User's Guide
|
|
Get Adobe Reader |
User Certificates and Private Keys
The following sections describe how to work with certificates and private keys:
- About user certificates and private keys
- About the certificate builder
- Generating certificates and private keys
About user certificates and private keys
An application using network services through an OSA/Parlay gateway acts as an OSA/Parlay client towards the OSA/Parlay gateway. The OSA/Parlay client and the OSA/Parlay gateway's framework authenticate using user certificates and private keys.
When an application account is registered, an OSA/Parlay client for the application is created. This OSA/Parlay client imports the OSA/Parlay gateway's user certificate and provides its user certificate to the OSA/Parlay gateway. A part of creating the OSA/Parlay client is to generate the OSA/Parlay client's user certificate and private key.
About the certificate builder
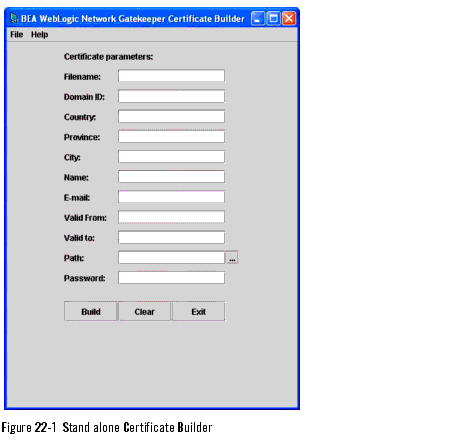
The certificate builder is a tool for generating user certificates and private keys. It can be used stand alone and through an Network Gatekeeper Management Tool. The same functions are provided in both cases. The stand alone version of the certificate builder is shown in Figure 22-1.
Some fields in the certificate builder are used differently depending on what function the user certificate and private key is generated for. The specific usage of all fields are described in Table 22-3.
Table 22-3 Description of the Fields in the Certificate Builder
Generating certificates and private keys
Follow the instruction below to generate a user certificate and private key pair.
If you perform the task through an Network Gatekeeper Management Tool, remember that the user certificate and private key will be stored on the server the Network Gatekeeper Management Tool is connected to. That is, where the SLEE runs.
Using the certificate builder stand alone
- Enter the user certificate and private key data according to Table 22-3 on page 4.
Using the certificate builder through an Network Gatekeeper Management Tool
- Enter the user certificate and private key data according to Table 22-3 on page 4.