Overview of Portal Security
When you build portal applications, you secure them using authentication (Who are you?) and authorization (What can you access?). Think of authentication and authorization as getting into a house. Authentication is getting through the front door. Authorization is getting into any of the rooms in the house from there.
Authentication - When a user successfully logs in, the user is authenticated. The system knows who the user is. A user's username and password are stored in an authentication provider database that WebLogic Server knows about. WebLogic Server provides its own default authentication provider: an LDAP user store. Just by installing WebLogic and creating a new domain with the Configuration Wizard, you can begin adding and managing users and groups in this default LDAP user store.
You may also have one or more existing user stores, such as an OpenLDAP or RDBMS, that already store usernames and passwords. If they are supported by WebLogic Server, you can connect WebLogic Server to these authentication providers, and users with their usernames and passwords stored in those providers can log in as if they were stored in WebLogic Server.
Authorization - If successful authentication is getting through the front door of the metaphorical house, authorization determines which rooms in the house (or even which furniture or appliances) users can access and use.
WebLogic Portal has its own authorization framework that lets you define rules (roles) for who can access which portal resources. You can define delegated administration roles for your portal administrators, and you can define entitlement roles for visitors to your portals. When a portal administrator logs in to the WebLogic Administration portal, the administrator sees only the areas he can administer. When a visitor logs in to a portal, the visitor sees only the books, pages, and portlets to which he is entitled.

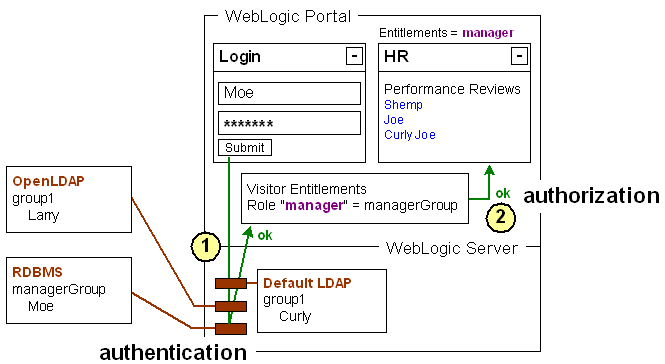
In this example, three authentication providers are being used by WebLogic Server: an OpenLDAP provider, an RDBMS (relational database) provider, and WebLogic Server's default LDAP provider. The two external authentication provider servers are running, and they have been added to WebLogic Server as authentication providers in the WebLogic Server Administration Console.
1 |
The user logging in is authenticated against all available authentication providers. Moe belongs to the RDBMS authentication provider and can log in successfully. |
2 |
On successful login to a portal, WebLogic Portal uses its DefaultRoleMapper to see if the user belongs to any delegated administration and visitor entitlement roles, and the user is granted access to only the resources he is allowed to access. The role called "manager" is defined so that anyone belonging to the group called "managerGroup" is part of that role. The HR portlet is set up so that only members of the "manager" role can view it. |
Other key factors in portal security are user credential management, network security, and WebLogic Server security.
As an administrator, you should have a clear understanding of how entitlements and Delegated Administration work. You should also be comfortable with role policies and security policies.
The WebLogic Administration Portal is a major factor in implementing security on top of WebLogic Server by provides the following functionality that can play a vital role in portal security:
Related Topics: