Using WSRP with WebLogic Portal
|
|
Establishing WSRP Security
The WSRP standard does not enforce any specific security standard at this time; however, it does recommend that you follow security standards such as WS-Security and SAML when implementing WSRP-compliant portlets. The WSRP standard does emphasize using transport-level security standards, such as SSL/TLS, to address the security issues involved in Consumers invoking Producers on behalf of end-users. These security standards only require that a Producer's WSDL declare ports for an HTTPS service entry point. Consumers can only determine that secure transport is supported by parsing the URL for the service entry point access control.
This section describes some of the security measures we suggest you follow. It contains information on the following subjects:
- Access Control
- Security Recommendations
- Obtaining a Signed Certificate
- Configuring the Producer Keystore
Access Control
Both Producers and Consumers can control access by using the implemented security measures.
- Consumers can restrict end-users access to portlets and to specific operations on those portlets.
- Producers can implement access control programmatically through the use of facilities such as an authenticated user identity.
Security Recommendations
While the WSRP standard does not specify security requirements, the following recommendations serve as guidelines that will ensure secure implementation of your WSRP-compliant portlets:
Secure WSRP Messages
- Use SSL on any port through which the Producer will be offered.
- Configure the Producer to offer secure portlets by specifying
"true"for all secure attributes in the <service-config> element of the Producer project'sWEB-INF/wsrp-producer-config.xmlfile, as shown in Listing 2-1.
Listing 2-1 <service-config> Element Configured for Security
<service-config>
<registration required="true" secure="true"/>
<service-description secure="true"/>
<markup secure="true"rewrite-urls="true" transport="string"/>
<portlet-management required="true" secure="true"/>
</service-config>
Note: If you make any changes to wsrp-producer-config.xml, you will need to redeploy or bounce the server before the changes become active.
Manage User Identity
- Rely on single-sign-on (SSO), which is set up by default in WebLogic Portal.
- Let users login to the Consumer portal. WebLogic Portal will manage SSO automatically.
Secure the /producer Path
By default, the Producer servlet is not protected. In order to restrict access to a Producer, protect the path <webAppPath>/producer at the network or firewall level (where webAppPath is the URL of the web application).
Obtaining a Signed Certificate
Producers authenticate Consumers through the use of client certificates in conjunction with SSL/TLS. Therefore, if you are relying on SSO and allow users to log-in to the Consumer portal, as recommended, the Producer must trust that Consumer. To establish this trust, the Consumer needs a certificate of authentication signed by an approved certificate authority (CA), such as VeriSign, Inc. This section describes how to use the Java keytool utility to generate a self-signed certificate and then obtain a signed certificate from a CA. It contains information on the following subjects:
The Java keytool Utility
When you install WebLogic Platform, part of the installation process installs a Java runtime environment (JRE). Within the JRE you will find a utility call keytool.exe. keytool is a key and certificate management utility with which you can administer your own public/private key pairs and associated certificates to use in self-authentication (where the user authenticates himself/herself to other users/services) or data integrity and authentication services by using digital signatures.
keytool Concepts and Terminology
You should be familiar with the following terms when implementing security for WSRP-compliant portlets:
Also known as a public-key certificate—a digitally signed statement from one entity (the issuer), saying that the public key (and some other information) of another entity (the subject) has some specific value.
An organization, such as VeriSign, Inc. that will accept a CSR and return to the requestor a certificate or certificate chain.
A set of certificates used to establish trust back to a common certificate authority. The first certificate in the chain contains the public key corresponding to the private key.
A file that is sent to a certificate authority, who will authenticate the certificate requestor (usually offline) and return to the requestor a certificate or certificate chain, used to replace the existing certificate chain (which initially consists of a self-signed certificate) in the keystore.
A database of private keys and their associated X.509 certificate chains that are used to authenticate the corresponding public keys. A keystore file has the
.jksextension.
keytool Reference
keytool was created by Sun Microsystems. For complete information on this utility, please refer to keytool - Key and Certificate Management Tool at:
http://java.sun.com/j2se/1.4.2/docs/tooldocs/windows/keytool.html
Obtaining the Consumer Certificate
To obtain a signed certificate, use this procedure.
Note: Before you can actually create a keystore and generate a certificate, ensure the following has been completed:
keytool-genkey-keypass password1 -filefilename.pem -keystore C:\working\myWsrpKeystore.jks -storepass password2 -alias myAlias
- password1 is the password used to protect the private key of the generate key pair.
- /working/ is the directory into which you copied the renamed
.jksfile. - myWsrpKeystore is the new
.jksfile. - password2 is the password used to protect the integrity of the keystore.
myAliasis a name you specified as an alias, which is used to access an entity in the keystore.
Note: The options listed above are just a sample of the options you can use when generating a keystore. For a complete list of options, please refer to keytool - Key and Certificate Management Tool at:
http://java.sun.com/j2se/1.4.2/docs/tooldocs/windows/keytool.html
The keytool options are not required. If you choose not to specify them, defaults are used for those that have default values and you will be prompted for any required values.
- At this point, you've generated a self-signed certificate. Because a certificate is more likely to be trusted by others if it is signed by a Certification Authority (CA), you now need to generate a Certificate Signing Request (CSR) to gain that signature by doing the following:
-----BEGIN NEW CERTIFICATE REQUEST-----
MIICYzCCAiACAQAwXjELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAkNPMRAwDgYDVQQHEwdCb3VsZGVy
MRQwEgYDVQQKEwtCRUEgU3lzdGVtczENMAsGA1UECxMERG9jczELMAkGA1UEAxMCRWQwggG3MIIB
LAYHKoZIzjgEATCCAR8CgYEA/X9TgR11EilS30qcLuzk5/YRt1I870QAwx4/gLZRJmlFXUAiUftZ
PY1Y+r/F9bow9subVWzXgTuAHTRv8mZgt2uZUKWkn5/oBHsQIsJPu6nX/rfGG/g7V+fGqKYVDwT7
g/bTxR7DAjVUE1oWkTL2dfOuK2HXKu/yIgMZndFIAccCFQCXYFCPFSMLzLKSuYKi64QL8Fgc9QKB
gQD34aCF1ps93su8q1w2uFe5eZSvu/o66oL5V0wLPQeCZ1FZV4661FlP5nEHEIGAtEkWcSPoTCgW
E7fPCTKMyKbhPBZ6i1R8jSjgo64eK7OmdZFuo38L+iE1YvH7YnoBJDvMpPG+qFGQiaiD3+Fa5Z8G
kotmXoB7VSVkAUw7/s9JKgOBhAACgYBkQ10+BRJVVzMgZTQJiUDYdK+5WOI1EkvXbyZPmvYzAfch
vtR7WKJZMPcbAyq9mtrOXFY7TTEkupXlY4R8c5DdLW0db3YB1eV4gUGQOXn4Y+zE8Z4LxKNhkKLk
yEUQhv0JkyzIReV7sioJahf7AiOwqs2cW1r4dNt4y42duwrdsKAAMAsGByqGSM44BAMFAAMwADAt
AhRARh4iBbioO+Jn3qc/bXOpjr+cqgIVAI78/s8hMqhFkTJxt/qtE3L3F1aP
-----END NEW CERTIFICATE REQUEST-----
- Import the signed certificate by using the
-importcommand, specifying the appropriate options; for example:
keytool -import
http://java.sun.com/j2se/1.4.2/docs/tooldocs/windows/keytool.html#importCmd
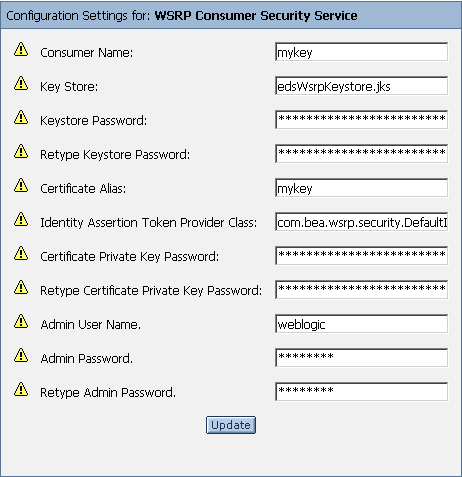
The Configuration Setting page appears (Figure 2-1).
Figure 2-1 Configuration Settings Page
The Configuration Settings for: dialog box appears in the right pane (Figure 2-2)
Figure 2-2 Configuration Settings for: WSRP Consumer Security Service Dialog Box
Configuring the Producer Keystore
For a Producer to trust a Consumer, it needs to recognize the Consumer's signed certificate. To ensure this, you need to provide the Producer with the Consumer's public key, which the Producer will add to its keystore.
To configure a keystore on the keystore side, you need to do the following:
- Update the WSRP Identity Asserter (on the WebLogic Server console).
- Set Up the Producer Keystore by importing the signed certificate that was returned to the Consumer.
Update the WSRP Identity Asserter
To update the WSRP identity asserter, use this procedure:
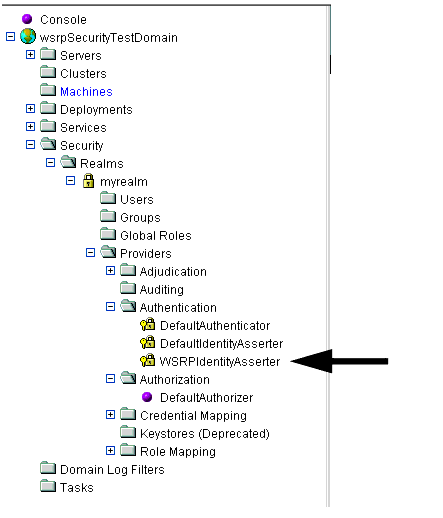
- In the left pane, drill down to the WSRP Identity Asserter node (Security>Realms>myRealm>Producers>Authentication>WSRPIndentityAsserter), as shown in Figure 2-3.
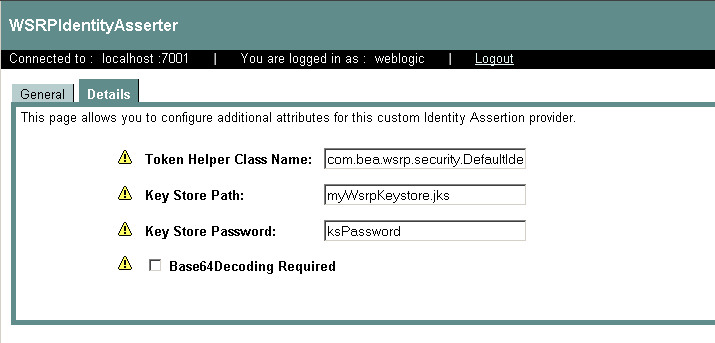
- Select the Detail tab to display WSRP identity detail information, as shown in Figure 2-4.
Figure 2-3 WSRP Identity Asserter Drill-down
Figure 2-4 WSRP Identity Asserter Detail
Note: If any of the yellow icons next to the field labels are blinking, you will need to reboot the server.
Set Up the Producer Keystore
To set up the Producer keystore, use the -import command on the Producer to import the signed certificate that was returned to the Consumer; for example:
keytool -import -filecert_file
where cert_file is the name of the .pem file that contains the signed certificate.