
Configuring Security for Web Service Clients Using NetBeans IDE
To use the IDE to configure security for a web service client, perform the following tasks:
- Create a client for a web service. If you need an example of how to do this, see Creating a Client to Consume a WSIT-Enabled Web Service for steps for creating a JSR-109-compliant client and refer to the steps in Securing the Example Web Service Client Application (SA) for an example that creates a non-JSR-109-compliant client. The following are changes to the basic application that might be needed depending on the security mechanism selected for the web service:
- If you are creating a client for a mechanism that will use SSL, specify the secure port for running the client when completing the New Web Service Client step. To do this, enter
https://localhost:8181/<rest_of_url>in the WSDL URL field of the New Web Service Client wizard. For the example, this is the way to specify the secure URL for Calculator web service:https://localhost:8181/CalculatorApplication/CalculatorService?wsdl- If you are creating a client for a service that is secured using one of the SAML mechanisms, follow the example for creating a non-JSR-109 client, as described in Securing the Example Web Service Client Application (SA).
- In the Projects window, expand the client node.
- Expand the Web Service References node.
- Right-click the node for the web service reference for which you want to configure security options.
- Select Edit Web Service Attributes.
When the Web Service References Attributes Editor is opened, select the WSIT tab to display the WSIT options (see Figure 7-1).
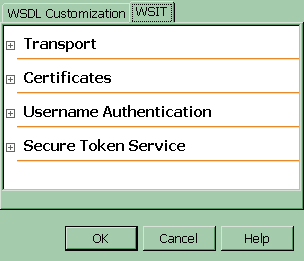
Figure 7-1 Web Service References Attributes Editor Page for Web Service Clients
- In the Transport section, optionally, select an option to automatically select optimal encoding or optimal transport. This is not a security feature, but it is covered in this section because it is on the WSIT tab with the security options. For more description of these options, read Configuring Transport Options.
- In the Certificates section, specify the information about the client keystore and truststore files, if necessary for the type of security mechanism configured for the service. For more description of these options, read Configuring Certificates Options.
- In the Username Authentication section, you can specify a Username and a Password Callback Handler, a default user name and password that can be used for development purposes, or a SAML Callback Handler to be used with non-JSR-109 web service clients. For more description of these options, read Configuring Username Authentication Options.
- In the Secure Token Service section, specify the information needed to contact the Secure Token Service, if the selected security mechanism of the service requires this. For more description of these options, read Configuring Secure Token Service Options.
- Click OK to save your changes. This information is saved in a WSDL file under Source Packages
META-INF.
- You may want to view the WSDL file and verify that the information you specified is contained therein. To do this, in the tree, drill down from the project to Source Packages
META-INF. Double-click on <service>Service.wsdl. For example, if the web service was secured using the Username Authentication with Symmetric Keys mechanism, the client WSDL should resemble the following:
<wsp:All> <wsaws:UsingAddressing xmlns:wsaws="http://www.w3.org/ 2006/05/addressing/ wsdl"/> <sc:CallbackHandlerConfiguration wspp:visibility="private"> <sc:CallbackHandler default="user_name" name="usernameHandler"/> <sc:CallbackHandler default="user_password" name="passwordHandler"/> </sc:CallbackHandlerConfiguration> <sc:TrustStore wspp:visibility="private" location="C:\Sun\glassfish\domains\domain1\config\cacerts.jks" storepass="changeit" peeralias="xws-security-server"/> </wsp:All>The following section provides a summary of what options are required on the client side for a specific mechanism specified on the server side.
Summary of Client-Side Configuration Requirements
Table 7-1 summarizes the options that need to be configured for each of the security mechanisms on the client-side. Each of the columns is briefly discussed after the table. A summary of the server-side configuration options is available at Summary of Configuration Options.
- Keystore--If this column indicates YES, configure the keystore to point to the alias for the client certificate. For the GlassFish keystores, the keystore file is
keystore.jksand the alias isxws-security-client, assuming that you've updated the GlassFish default certificate stores as described in Updating GlassFish Certificates.- Truststore--If this column indicates YES, configure the truststore that contains the certificate and trusted roots of the server. For the GlassFish keystores, the file is
cacerts.jksand the alias isxws-security-server, assuming that you've updated the GlassFish default certificate stores as described in Updating GlassFish Certificates.When using an STS mechanism, the client specifies the truststore and certificate alias for the STS, not the service. For the GlassFish stores, the file is
cacerts.jksand the alias iswssip.- Default User--When this column indicates YES, you must configure either a default username and password, a UsernameCallbackHandler, or leave these options blank and specify a user at runtime. More information on these options can be found at Configuring Username Authentication Options.
- SAML Callback Handler--When this column indicates YES, you must specify a SAML Callback Handler. Examples of SAML Callback Handlers are described in Example SAML Callback Handlers.
- Non-109 Client--When this column indicates YES, you must create a non-JSR-109 client. For more description of what constitutes a JSR-109 client, read What is the difference between JSR-109 and Non-JSR-109 Clients?. For an example that uses a non-JSR-109 client, read Securing the Example Web Service Client Application (SA).
- STS--If this column indicates YES, you must have a Security Token Service that can be referenced by the service. An example of an STS can be found in the section Creating and Securing the STS (STS). The STS is secured using a separate (non-STS) security mechanism. The security configuration for the client-side of this application is dependent upon the security mechanism selected for the STS, and not on the security mechanism selected for the application.
- SSL--To use a mechanism that uses secure transport (SSL), you must configure the system to point to the client and server keystore and truststore files. Steps for doing this are described in Configuring SSL For Your Applications.
- User in Glassfish--To use a mechanism that requires a user database for authentication, you can add a user to the file realm of GlassFish. Instructions for doing this can be found at Adding Users to GlassFish.