Chapter 3 Using the skiptool GUI
This chapter tells you:
-
How to start and use skiptool ("skiptool Overview")
-
How to configure SKIP ("Configuring SunScreen SKIP"
-
How to enable SKIP ("Enabling SKIP"
-
How to tell if SKIP is working ("Is SKIP Working?"
-
How to view statistics ("Viewing SunScreen SKIP Statistics "
-
How to manage keys ("Key Management with skiptool"
skiptool Overview
Once you install SunScreen SKIP and the local keys on your machine, you must set it up so that it can communicate with other systems using SKIP.
SunScreen SKIP provides two ways to configure and manage it: skiptool (the GUI) and skiphost (the command-line interface discussed in Chapter 4, Using the Command-Line Interface) The easiest way to set up your ACLs is through skiptool. Using skiptool you can:
-
Enable and disable access to your machine
-
Set the type of encryption used for hosts or network connections to your system (encrypted or unencrypted [clear])
-
Determine how to deal with unauthorized hosts that try to connect to your system.
-
View the following statistics including:
-
Network Interface Statistics
-
SKIP Header Statistics
-
Key Statistics
-
Encryption Statistics (for Versions 1 and 2)
-
Authentication Statistics
Note -If you are managing a large amount of certificates, you will probably find it easier to use the command line because the skiptool GUI displays a truncated MKID.
-
skiptool Requirements
To run skiptool, you must have root privileges on your system.
Note -
Enable access for any client to the X server for Solaris 2.x operating environments by entering the xhost + localhost command before you become root.
Starting skiptool
Use the following steps to start skiptool:
Become root, and type:
# skiptool & |
Note -
If you are configuring a system with multiple network interfaces, you can specify the interface following the command; for example, skiptool le1.
The main window of skiptool is shown in the following figure.
Figure 3-1 skiptool Main Window
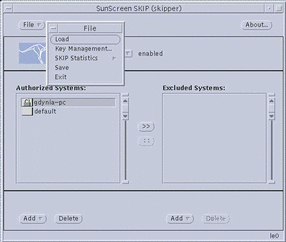
The skiptool Main Window
The skiptool main window has several important features:
-
The File button
-
The Access Control buttons
-
The Authorized and Excluded Systems lists
-
The Add and Delete (Management) buttons
Note -If you have other windows layered on top of the skiptool main window, you need to click on the Title Bar to bring the main window to the front.
File Menu
The file menu has five submenus:
Load--Loads the current address control list (ACL) from the kernel. This feature is useful if you have modified the ACL through other tools and want to update the configuration in skiptool.
Key Management--Defines the parameters for key usage, including when to delete an unused key (in seconds) and how much data to transmit per key (in Kbytes).
SKIP Statistics--Brings up one of six statistics windows: (Network Interface Stats, SKIP Header Stats, Encryption Stats (Version 1), Encryption Stats (Version 2), Key Stats, or Authentication Stats.
Save--Makes the configuration permanent. Before saving, it prompts you to add any systems that are in use, that have access, and that are not currently on the authorized list. The next time that you reboot this configuration is used. Quitting and restarting skiptool will not affect either saved or unsaved changes in the configuration.
Note -
If you do not save the changes in the configuration, they will only remain in effect until the next time you reboot your machine.
Exit--Closes all open windows and quits skiptool. The Statistics window does not close when you quit skiptool.
Access Control Buttons
Access Control button--This button toggles to enable or disable SKIP. When SKIP is enabled, the ACL rules apply.
For example, if you have only the default entry in the authorized systems list and some entries in the excluded systems list. In this case, any host except those that are in the excluded systems list can connect. When SKIP is disabled, any system can connect, if the default entry is configured in the clear.
Authorized Systems/Excluded Systems Lists
Authorized Systems--A list of systems that are authorized to access to host. System types are host, network, or nomadic. Secure systems appear with a padlock or the Sun Microsystems' logo next to the system name (depending on the type of security being used.)
Excluded Systems--A list of systems that are specifically denied access to your system. When you move or add a system to the excluded list, it is immediately excluded.
skiptool allows you to move systems from the list of authorized systems to the list of excluded systems and vice versa with the arrows between the two lists.
Management Buttons
These buttons enable you to add or delete a system from the access list. The buttons are available for both authorized and excluded systems.
Add--Brings up the Add pop-up menu where you select the system type to be added to the ACL:
Host--Adds an individual host, either with or without security.
Network--Adds a network, either with or without security.
Nomadic--Adds a nomadic identity, with SKIP Version 1 or SKIP Version 2 security.
Delete--Deletes the selected system from the list. When an item is deleted, the deletion occurs immediately and cannot be undone.
You may also move ACL entries from one list to another with the arrow buttons. These arrow buttons make it easy to add or delete systems when troubleshooting.
If you add, delete, or move ACL entries from one list to another, the action takes effect immediately.
Configuring SunScreen SKIP
You can configure only one network interface at a time using skiptool. If you have more than one network interface, you must configure each one separately.
Configuring SunScreen SKIP
Configuring SunScreen SKIP requires completing several simple steps:
-
Adding authorized systems
-
Adding any excluded systems
-
Setting up the behavior for unauthorized systems
-
Enabling SKIP
-
Verifying the installation and set up
Adding Authorized Systems
Any remote host with which you want to communicate must be configured using the Add pop-up window.
An authorized host may or may not be using encryption. The Add pop-up window provides three options:
-
Off (not using encryption)
-
Using SKIP encryption
-
Using SunScreen SKIP Version 1 encryption
You add hosts to the authorized systems list using the Add button. The valid types of remote hosts that you can add to your ACL are
-
Host
-
Network
-
Nomadic
 Caution -
Caution - When setting up SunScreen SKIP, be sure to include any NFS servers and NIS or DNS name servers on the authorized systems list, otherwise your system may hang. To avoid problems such as this, a safe approach at the beginning is to add the clear "default" entry. Once you become more comfortable with SKIP configuration, you can remove it.
To determine the servers your system communicates with, use the following commands:
-
For NFS servers, type mount
-
For NIS servers, type ypwhich
-
For DNS servers, consult your system administrator
-
Verify the current routing entries used by the local system. To verify the current routing entries, type netstat -rn and add specific network ACL entries.
If you do not specify a system that you currently have in use when you enable access control, a menu will come up and ask if you want to add the system. It also checks for multicast routers that are being used for others and adds them to the proposed list of systems to add.
Regardless of the type of system that you are adding to the ACL, you must implement the same policy on both your machine and the entity with which you wish to communicate securely. If you do not configure both systems properly, the packets are silently dropped and it appears as if that particular host does not exist. skiplog is useful in diagnosing this situation.
When you click on the Add button, the Add pop-up window appears. From the menu in this window, you select the type of connection: Host, Network, or Nomadic. Next, use the pull-right menu to set the security level. After you have selected the level of security, the appropriate Properties window becomes available. The Add System Properties window is used to set up the options for the type of encryption used by the host, network, or nomadic system being authorized. The procedures in the sections following the table detail how to set up each encryption option.
Adding a Host or Network with No Encryption
This procedure is used to allow a host or network access to your system without using any encryption.
-
Click and hold the Add button at the bottom of the authorized systems list on the skiptool main window.
-
Select the type of connection being authorized: Host or Network. (Nomadic does not offer this option.)
-
Pull right on the type of connection and select Off.
The Add Host properties or Add Network properties dialog box, shown in the following figure, in appears.
Figure 3-2 Add Host/Properties--No Encryption
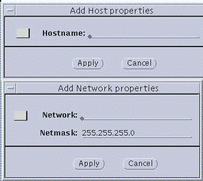
-
In the Add Host or Network properties window, enter the name or IP address of the host system to be added to your ACL.
In the case of a network, you must define the network with the IP address and the netmask.
-
Click the Apply button.
Setting Up Security for a Host, Network, or Nomadic System
The procedures in this section enable a host, network, or nomadic system access to your system according to the encryption rules you set up. Remember, both your system and the other system need to use the same rules in order to communicate.
Dialog Box Parameters
The following section provides some background on the choices available to you from the skiptool dialog boxes. This material will be useful to use the procedures that follow. The two encryption dialog boxes (SKIP and SKIP Version 1) use common set-up parameters, as you can see in Figure 3-3 through Figure 3-5. Explanations of the parameters follow the figures.
Figure 3-3 Host--Add SKIP Host Properties and SKIP Version 1 Properties

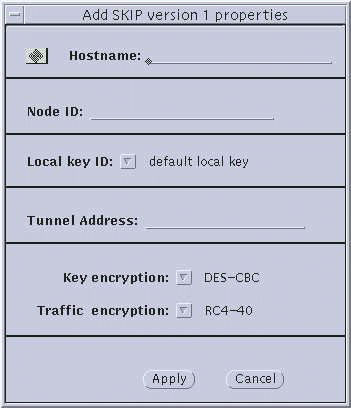
Figure 3-4 Network--Add SKIP Network Properties and SKIP Version 1 Properties
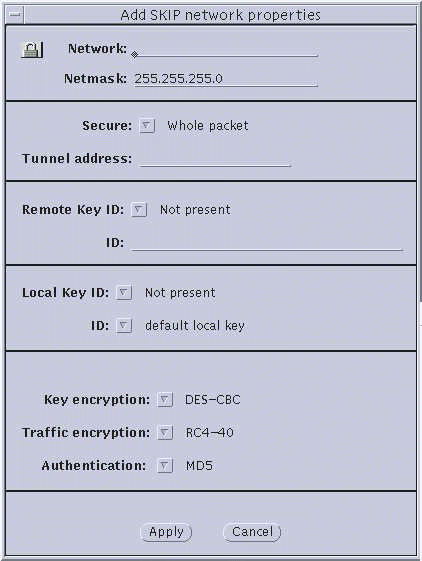
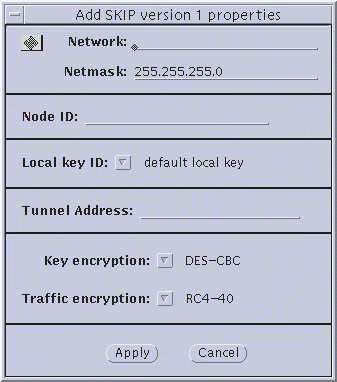
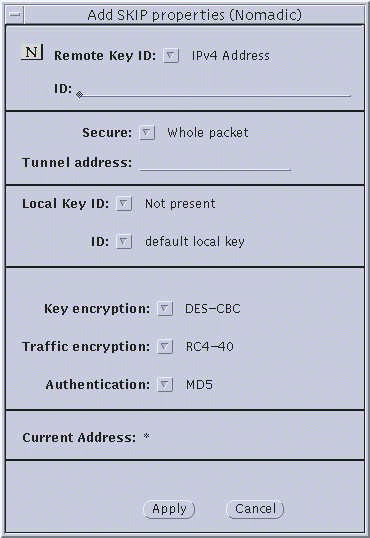
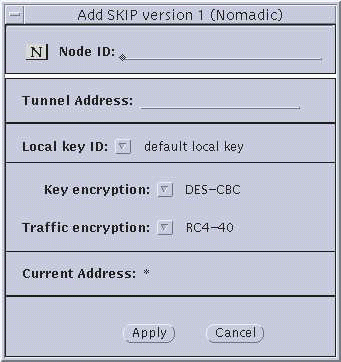
Figure 3-5 Nomadic--Add SKIP Properties and Add SKIP Version 1
Parameter Explanations
-
Hostname/Network/Node ID. Enter the name of the host or nomadic system, or the IP address of the host or network.
-
Netmask--(network only) Enter the netmask of the network. The default (255.255.255.0) is already entered.
-
Secure button--(SKIP only) Set to either Whole packet (tunnel mode) or Data only (transport mode). Whole packet is recommended because it offers a greater degree of security.
-
Node ID--(SKIP Version 1 only) This is the IPv4 key ID.
-
Tunnel Address--Use the tunnel address as the destination IP address. Tunnel address is generally used for clients of encrypted gateways where the IP address of the host entered here serves as the intermediary for any or all hosts on a network whose topography must remain unknown or hidden from the rest of the world. This is called topology hiding. This field is not available if you select Data only.
-
Remote Key ID button--(SKIP only) Select whether you want the remote system's key ID included in SKIP packets and, if so, the namespace that key ID occupies. Selecting Not Present means that the receiver key ID will not be sent.
The following name spaces are listed in this menu:
-
Not Present
-
IPv4 Address
-
MD5 (DH Public Value)
Not Present is the default. It uses the IP address of the remote system to identify its certificate. If a remote system has a key ID other than that identified by its IP address, set the namespace and indicate the remote system's key ID in the ID field.
Note -When you add a host by entering the hostname and you change the Remote key Id menu to IPV4 address from Not present the cursor does not appear in the ID field even if you click there. You must click on the Local key Id menu to move the cursor and regain focus.
-
Remote Key ID field--(SKIP only) The namespace indicated in the Remote Key ID field is determined by the type of certificate, shown in the following table, that you are using or have obtained for this system:
Table 3-1 Remote Key ID FieldCertificate Type
Remote Key ID Field
CA (Sun or other)
IPv4
Self-generated unsigned key
MD5 (DH Public Value)
If the Remote Key ID field has been set to other than Not Present, enter the key ID in hexadecimal format in the ID field (such as 0x0a000000). It must contain the appropriate key ID for the system being authorized based upon the selection made with the Remote Key ID button. Depending on the type of certificate, this information may be obtained from the master key ID on the diskette or from the local key ID field of the other host.
-
Local Key ID and ID buttons. Use the Local Key ID button to indicate whether you want your local system to send its key ID in the SKIP packet and, if so, the namespace that key occupies. If you select Not Present, the sender's key ID is not sent in the packet and the remote system uses the local system's IP address to decide what key to use.
Note -If you have installed new local keys after you have started skiptool, skiptool will not list them. You must restart the key manager with the skipd_restart command to list them and rerun skiptool.
All the local-key times installed for this host are listed. Select the namespace for the local key that is to be used for communication with the above host. Once you have selected the namespace, click on the ID field to select the key to be used, in hexadecimal, for communication with this host.
-
Key Encryption button--Selecting this button lists the available key encryption algorithms. The algorithms available are determined by the system type and the selected encryption method selected.
Table 3-2 Available Key and Traffic Encryption Algorithms512 bit
1024 bit
2048 and 4096 bit
Key Encryption DES-CBC
DES-CBC
DES-CBC
RC2-40 (32-bit mode only)
RC2-40 (32-bit mode only)
RC2-40 (32-bit mode only)
3DES
SAFER
Traffic Encryption RC2-40 (32-bit mode only)
RC2-40 (32-bit mode only)
RC2-40 (32-bit mode only)
RC4-40
RC4-40
RC4-40
3DES
3DES
SAFER
RC4-128
Note -The RC2 cryptor is supported in 32-bit mode only. If you inadvertently select this cryptor while in 64-bit mode, the console reports an error message and communication with the system using this cryptor stops (no information is transferred in the clear).
-
Traffic Encryption button--Select the algorithm for encrypting the traffic between your system and the remote system. The algorithms available are determined by the system type, the version of SunScreen SKIP, and the method of encryption selected. Please see the previous table for complete information.
-
Authentication button--Use the authentication button to select the type of authentication for the packets. Currently, SunScreen SKIP supports two types of authentication--MD5 and MD5-NAT. You can also select None for no authentication.
Adding Authorized Systems with Encryption
Note -
While using any of the Add functions of skiptool, if you generate an error msg, clicking the apply button will not close the window. You must close the Add window manually. The normal behavior is for the window to close automatically after you click the apply button.
-
Click and hold on the Add button at the bottom of the authorized systems list on skiptool's Main Window.
-
Select the type of connection being authorized: Host, Network, or Nomadic.
-
Pull right on the type of connection and select the type of encryption that you want to use.
-
If the remote host system also uses SKIP and the traffic between your systems is to be encrypted, select SKIP.
-
For systems using Sun Microsystems' SunScreen SPF-100, select SKIP Version 1.
-
-
On the Add properties window, enter the name or IP address of the host system to be added to your ACL.
-
Determine whether Whole packet (tunnel mode) or Data only (transport mode) is secure by clicking on the appropriate selection for the Secure button.
-
Each type of encryption requires that certain options be set.
The parameters selected are determined by the type of system being authorized and your security policies. The options to be considered are based on the method of encryption selected. They are
-
For systems using SKIP: Tunnel address, Remote Key ID, Local Key ID. If you leave the tunnel address blank, it will default to the peer's address.
-
For SKIP Version 1: Key ID, Tunnel address.
-
-
Select the appropriate algorithms buttons for Key encryption, Traffic encryption, and Authentication.
The options available for each system are based upon the method of encryption selected from the Security pop-up menu:
-
Key Encryption button: Selecting this button lists the available key encryption algorithms. The algorithm available is determined by the type of system and selected method of encryption. Please Table 3-2.
-
Traffic Encryption button: Selecting this button lists the algorithms available for encryption between your system and the remote system. The algorithms that are available for key and traffic encryption depend on the packages that were installed on the system, such as core product and key upgrades. The algorithms available determine the type of system and the method of encryption selected. Please see Table 3-2.
-
Authentication button: Use this button to select the type of authentication for the packets.
-
-
Click Apply to add the host to the authorized systems list.
Refer to the previous section for descriptions of the fields and buttons.
Repeat Steps 1 though 8 for all encrypted hosts. Remember that your policy options for each system entered on your ACL must be the same as those entered on the system entity with which you wish to communicate through encrypted channels. If the configuration on your system does not match that of the party with which you wish to communicate, the packets are silently dropped. It will simply appear as though that host no longer exists.
Using Default System Entry
The default system entry is used when no other more specific ACL entry matches a host. Often, this entry is set to clear to allow hosts that are not listed in the ACL to communicate in the clear. It may, however, be used to create a default encryption rule.
Communicating In the Clear (Off)
Typically, the NIS and DNS servers to which your systems have access are set up as communicating with your system in the clear or unencrypted. In addition, any host that does not use an encryption package must be set up to communicate with you in the clear.
Communicating Using SKIP Version 1
Complete the following steps to set these fields for encrypted traffic between your server and the system to be authorized.
-
After selecting the type of system and setting the security to SKIP, enter the Hostname.
-
Enter the Node ID.
This is the IPv4 key ID.
-
Local Key ID and ID buttons.
Use the Local Key ID button to indicate whether you want your local system to send its key ID in the SKIP packet.
-
Set the Tunnel Address, if you are using topology hiding.
Tunnel addressing is generally used for clients of encrypted gateways where the IP address of the host entered here serves as the intermediary for any or all hosts on a network whose topography is to remain unknown or hidden from the rest of the world.
-
Select the appropriate key and traffic algorithms for the Key and Traffic encryption buttons.
The available key and traffic encryption algorithms depend on the which version of SKIP you are using: 512 bit, 1024 bit, 2048 bit, 4096 bit. To see which options are available, please see Table 3-2.
Communicating Using SKIP
Complete the following steps to set these fields for encrypted traffic between your server and the system to be authorized.
-
After selecting the type of system and setting the security to SKIP, enter the Hostname.
-
Set the Secure button to either Whole packet (tunnel mode) or Data only (transport mode).
Whole packet is recommended because it offers a greater degree of security.
-
Set the Tunnel address, if you are using topology hiding.
Tunnel addressing is generally used for clients of encrypted gateways where the IP address of the host entered here serves as the intermediary for any or all hosts on a network whose topography is to remain unknown or hidden from the rest of the world.
-
Use the Remote Key ID button to select whether you would like the remote system's keyID included in SKIP packets.
If so, what namespace does that key occupy. By selecting Not Present, the receiver key ID is not sent.
Not Present is the default. It uses the IP address of the remote system to identify its certificate. If a remote system has a key ID other than identified by its IP address, set the name spaces and indicate the remote system's key ID in the ID Field. The namespace indicated in the Remote Key ID field is determined by the type of certificate that is used or obtained for this system. The type of certificate and the Remote Key ID field for that certificate is shown in the following table:
Table 3-3 Type of Certificate and Remote Key ID FieldCertificate Type
Remote Key ID Field
CA (Sun or other)
IPv4
Self-generated unsigned key
MD5 (DH Public Value)
-
The following name spaces are used in this menu:
Not present
IPv4 Address
MD5 (DH public Value)
-
If the Remote Key ID field has been set to something other than Not Present, enter the key ID in hexadecimal format in the ID field (0x0a000000).
It must contain the appropriate key ID for the system that is being authorized based upon the selection made in the Remote Key ID field. Depending on the type of certificate, this information may be obtained from the master keyID on the diskette or from the Local key ID field of the other host.
-
Select the appropriate key and traffic algorithms for the Key and Traffic encryption buttons.
The available options that appear depend on which version of SKIP you are using. versions Available options include: 512 bit, 1024 bit, 2048 bit, or 4096 bit. Please see Table 3-2.
-
Authentication button.
Use the authentication button to select the type of authentication for the packets. Currently, SunScreen SKIP supports MD5 and MD5-NAT. You can also select None for no authentication.
Excluding Systems
If the D entry remains on the authorized systems list, any remote host with which you want to exclude must be configured using the Add button located under the excluded systems list. When setting up an excluded system, you only need to enter the hostname for hosts and network number for networks. For nomadic systems you need to specify the key IDs.
If the state of the host or network changes to an authorized system, you must delete the system from the excluded systems list and add it to the authorized systems list.
The easiest way to exclude a system is to move it from the authorized systems list with the arrow button to the excluded systems list. The arrow buttons make it easy to add or delete systems when troubleshooting and the host is already present in the authorized systems list. If the host does not already exist on one of the lists, it is simpler to add it directly on the excluded systems list so that you can move it easily with the arrow button when you wish to add it to the authorized systems list.
Note -
If you move an encrypted host from the authorized systems list to the excluded systems list with the arrow button, SunScreen SKIP retains the encryption parameters so that if you later move this host back to the authorized systems list, its parameters are restored.
Adding Excluded Systems
Complete the following steps to exclude a system:
-
Click on the Add button at the bottom of the excluded systems list on skiptool's main window.
-
Select the system type: Host, Network, or Nomadic.
-
In the Hostname field on the Exclude System window, enter the name or IP address of the host system that you want to deny access to your system.
If you are excluding a nomadic system, also enter the key ID.
-
Click Apply on the Exclude System window.
 Caution -
Caution - If you add or delete ACL entries from one list to another, the addition or deletion takes effect immediately.
Enabling SKIP
The last step in setting up SunScreen SKIP is to enable access control for the system. You may also wish to understand the different symbols in the Authorized Systems list and know how to iconify skiptool.
Enabling Access Control
-
Enable SunScreen SKIP by selecting enabled from the Access Control button on the main window.
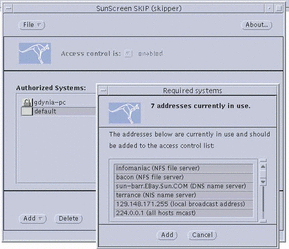
When SKIP is enabled for the first time, it checks for all systems with which you are talking in the clear. It detects the NFS, X Windows, NIS, and DNS servers with which you are communicating and offers the possibility of adding the systems automatically to the ACL when you select Add from the Required Systems window, shown in the following figure. Choosing Cancel can hang your system or prevent your access to the system or network the next time you try to log in because certain necessary servers may not have been added. To prevent this, select disable after canceling.
Figure 3-6 Enabling SKIP
Understanding the Symbols in the Authorized Systems List
The authorized systems area lists all the hosts that are allowed access. The excluded systems area shows all those known hosts that are explicitly denied access. The graphic preceding the host name or IP address depicts what type of security is being used with that host.
-
A blank box preceding the host name indicates no encryption (Security = Off).
-
A box with a lock in it indicates that the system is using SKIP as the encryption method (Security = SKIP).
-
A box with the Sun Microsystems' logo in it indicates that the system is using SKIP Version 1 (Security = SKIP version 1).
-
A box with an N indicates a system that is Nomadic (that is, it is identified by its key ID not its IP address) and that it is using either SKIP or SKIP Version 1 as the security method.
Iconify SunScreen SKIP
Once you have enabled SunScreen SKIP, it is no longer necessary to keep the window open. At this time, you can iconify the main window. The skiptool icon, which is shown in the following figure, shows SKIP's status. If you have set unauthorized systems to No Access, you can quit skiptool.
Figure 3-7 SKIP Icon Showing Both the Enabled and Disabled States
If you quit the application, SKIP stays in whatever mode it was last in (enabled or disabled).
Unauthorized Systems automatically changes to No Access, since there is no longer any way to notify you if an unauthorized system attempts to gain access.
Is SKIP Working?
Once you have configured and enabled SKIP, you cab determine that it is working properly. If the configurations on the systems do not match (that is, the encryption algorithms used), it will appear as if the other part of the communication equation does not exist. SKIP silently drops the packets. skiplog will log this event.
To verify that SunScreen SKIP is operating properly on your system, complete one or more of the following procedures:
-
Ping the remote system.
The remote system must have SunScreen SKIP enabled and be using the same key and traffic encryption algorithms as your system.
If you have the remote site's certificate, you can immediately start sending encrypted IP. Otherwise, SKIP will need to fetch the remote machine's certificate. By default, this is done by asking the remote site for its certificate over a clear channel. If you have configured other hosts to act as key servers, they will be asked for the certificate. See the D pages for skipd and skipd.conf for details. If there are no problems at the remote site, you receive replies when you ping.
Note -The initial ping can fail because the key manager's computation may exceed the time-out value of some of the IP protocols, such as ping.
-
Run snoop on your local system or a sniffer to see that packets are being encrypted.
If encryption is not taking place between your system and a system on your authorized systems list or you cannot connect to that system, check the following items.
-
Is SKIP enabled? Check the Access Control button. Set it to enabled.
-
Verify that a certificate exists for each system you wish to communicate with on your authorized systems list. Use the skipdb command to check for the certificate of the remote system by dumping the database to the screen. Try to restart the key manager by using the skipd_restart command.
-
Verify that SKIP is installed, configured, enabled, and has the certificate of the remote system.
-
Verify the key ID of the remote system in the log file /var/log/skipd.log to see if the key manager has set the key ID to what you think it should be. If it is not the correct key ID, get certificates for the correct key ID.
-
Verify that both machines have the same key encryption, traffic encryption, and authentication algorithms. You can check which ACL entry will be used when communicating with a remote host by using skiphost hostname/IP address command. This command will check default entries, as well as network entries.
-
Certificate discovery protocol (CDP) works by sending UDP requests to port 1640 of the server. If you are connecting through a firewall, check with your system administrator that UDP messages are allowed to pass on port 1640. These ports are required for CDP. As a workaround, you can manually distribute keys. Also, make sure that the SKIP protocol 57 (decimal number) and the SKIP Version 1 protocol 79 (decimal number) are permitted to pass through the firewall.
-
Some routers also filter packets. Check on the router and its configuration.
-
Verify that the CDP server specified in skipd.conf is correct and has been authorized in skiptool. If the cdp_server entry is = or @, it is specifying the tunnel address or host address, respectively.
-
SKIP requires that machine clocks be synchronized within one hour. Marke sure they are sysnchronized. Messages in /var/log/skipd.log will indicate this situation. You can use the UNIX command rdate(1M) to synchronize the clocks.
-
If the skiplocal -x command has been used to communicate key IDs when one or both of the systems have multiple keys or multiple network interfaces, the key ID may have been bound to the wrong network interface or local key ID. Use skiptool or skiphost to add the remote host after verifying key IDs over the telephone.
-
Use skiplog to verify configuration mismatches.
Viewing SunScreen SKIP Statistics
SunScreen SKIP provides two methods of viewing statistics: skiptool and skipstat (the command-line interface for viewing SKIP statistics and is discussed in Chapter 4, Using the Command-Line Interface.) The method you choose is a matter of personal preference since both interfaces provide the same data. The skiptool display has the word UPDATED in front of fields whose values have changed since the last "sampling." This feature is not available through skipstat.
The following statistics are available in SunScreen SKIP:
-
Network Interface Statistics
-
SKIP Header Statistics
-
Key Statistics
-
Encryption Statistics (for Versions 1 and 2)
-
Authentication Statistics
The Statistics Window
You can view the Network Interface, SKIP Header, Key, Encryption (Versions 1 and 2), and Authentication statistics in real-time by selecting SKIP Statistics from the File menu (File --> SKIP Statistics) on the skiptool main window, shown in the following figure.
Figure 3-8 Bringing Up a Statistics Window
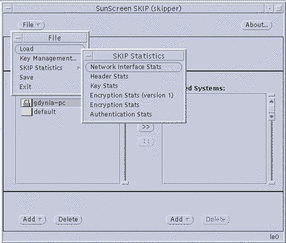
Each of the statistics available for SunScreen SKIP is described on the following pages. Sample data with field descriptions illustrate the information available for monitoring SunScreen SKIP's performance. The fields on the statistics screens are updated approximately every 3 seconds. A status change is indicated with the word UPDATED next to the field name.
SKIP Statistics
SKIP Interface Statistics
Selecting File --> SKIP Statistics --> Network Interface Stats displays the SKIP Interface Statistics window, shown in the following figure.
.
Figure 3-9 SKIP Interface Statistics Window
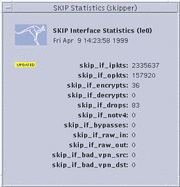
A brief description of each field is given below:
|
skip_if_ipkts |
Packets received by the interface. |
|
skip_if_opkts |
Packets sent by the interface. |
|
skip_if_encrypts |
Packets encrypted. |
|
skip_if_decrypts |
Packets decrypted. |
|
skip_if_drops |
Packets dropped. |
|
skip_if_notv4 |
Packets that are not IPv4 packets. |
|
skip_if_bypasses |
Number of certificate packets. |
|
skip_raw_in |
Number of non-SKIP IPSEC packets received. |
|
skip_raw_out |
Number of non-SKIP IPSEC packets sent. |
|
skip_if_bad_vpn_src |
Number of incorrect source tunnel addresses. |
|
skip_if_bad_vpn_dst |
Number of incorrect destination tunnel addresses. |
SKIP Header Statistics
Selecting File --> SKIP Statistics --> Header Stats displays the Header Statistics window, shown in the following figure. In the field descriptions below, V1 refers to SKIP Version 1.
Figure 3-10 SKIP Header Statistics Window
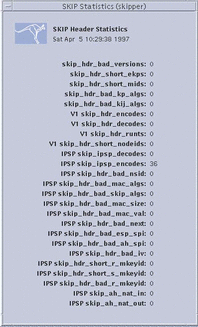
A brief description of each field in SKIP Header Statistics window is given below:
|
skip_hdr_bad_versions |
The number of headers with invalid protocol versions. |
|
skip_hdr_short_ekps |
The number of headers with short ekp fields. |
|
skip_hdr_short_mids |
The number of headers with short MID fields. |
|
skip_hdr_bad_kp_algs |
The number of headers with unknown cryptographic algorithms. |
|
skip_hdr_bad_kij_algs |
The number of headers with unknown key encryption algorithms |
|
V1 skip_hdr_encodes |
The number of SKIP V1 headers encoded. |
|
V1 skip_hdr_decodes |
The number of SKIP V1 headers decoded. |
|
V1 skip_hdr_runts |
The number of headers with short SKIP V1 packets. |
|
V1 skip_hdr_short_nodeids |
The number of headers with short SKIP V1 key ID. |
|
IPSP skip_ipsp_decodes |
The number of SKIP headers decoded. |
|
IPSP skip_ipsp_encodes |
The number of SKIP headers encoded. |
|
IPSP skip_hdr_bad_nsid |
The number of headers with a bad SKIP name- space ID. |
|
IPSP skip_hdr_bad_mac_algs |
The number of headers with unknown or bad authentication algorithms. |
|
IPSP skip_hdr_bad_skip_algs |
The number of bad SKIP algorithms. |
|
IPSP skip_hdr_bad_mac_size |
The number of headers with an authentication error in the MAC size. |
|
IPSP skip_hdr_bad_mac_val |
The number of headers with an authentication error in the MAC value. |
|
IPSP skip_hdr_bad_next |
The number of headers with a bad SKIP next protocol field. |
|
IPSP skip_hdr_bad_esp_spi |
The number of headers with a bad SKIP SPI field. |
|
IPSP skip_hdr_bad_ah_spi_ |
The number of bad AH/SPI headers (manual keying). |
|
IPSP skip_hdr_bad_iv |
The number of headers with a bad SKIP initialization vector. |
|
IPSP skip_hdr_short_r_mkeyid |
The number of headers with a short SKIP receiver key ID. |
|
IPSP skip_hdr_short_s_mkeyid |
The number of headers with a short SKIP sender key ID. |
|
IPSP skip_hdr_bad_r_mkeyid |
The number of headers with a bad SKIP receiver key ID. |
|
skip_ah_nat_in |
MD5-NAT packets received. |
|
skip_ah_nat_out |
MD5-NAT packets sent. |
Key Statistics
Selecting File --> SKIP Statistics --> Key Stats displays the Key Statistics window, shown in the following figure.
Figure 3-11 SKIP Key Statistics Window
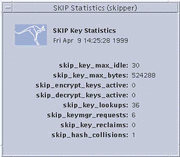
A brief description of each field on the Key Statistics window is given below:
|
skip_key_max_idle |
The time, in seconds, until an unused key is reclaimed. |
|
skip_key_max_bytes |
Maximum number of bytes to encrypt before discarding a key. |
|
skip_encrypt_keys_active |
Number of encryption keys in the cache. |
|
skip_decrypt_keys_active |
Number of decryption keys in the cache. |
|
skip_key_lookups |
The total number of key cache lookups. |
|
skip_keymgr_requests |
The total number of key cache misses (key not found). |
|
skip_key_reclaims |
The total number of key entries reclaimed. |
|
skip_hash_collisions |
The total number of table collisions. |
Algorithm Statistics
Selecting File --> SKIP Statistics --> Encryption Stats (Version 1) displays the Algorithm Statistics window for SKIP Version 1 as is shown in the following figure.
Selecting File --> SKIP Statistics --> Encryption Stats displays the standard Algorithm Statistics window, as is shown in the following figure.
Figure 3-12 Encryption Statistics Window--SKIP Version 1 and Standard SKIP
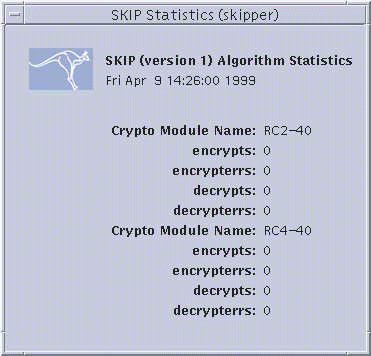
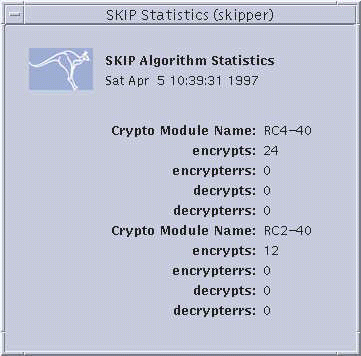
One set of statistics is displayed for each different traffic and key encryption module. A brief description of each field is give below:
|
Crypto Module Name |
The name of the cryptographic module for which the statistics are being displayed. |
|
encrypts |
Number of successful encryptions. |
|
encrypterrs |
Number of failed encryptions. |
|
decrypts |
Number of successful decryptions. |
|
decrypterrs |
Number of failed decryptions. |
Authentication Statistics
Selecting File --> SKIP Statistics --> Authentication Stats displays the Authentication Statistics window, shown in the following figure, which provides information on MACs (Message Authentication Code).
Figure 3-13 Authentication Statistics Window
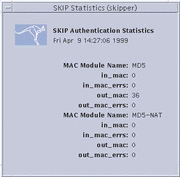
A brief description of each field on the Authentication Stats window is given below:
|
MAC_Module_Name |
MAC method used for authentication. |
|
in_mac |
Number of received MAC calculations that succeeded. |
|
in_mac_errs |
Number of received MAC calculations that failed. |
|
out_mac |
Number of sent MAC calculations that succeeded. |
|
out_mac_errs |
Number of sent MAC calculations that failed. |
Key Management with skiptool
The Key Management Parameters window, The following figure is displayed by selecting File --> Key Management. Key management parameters are global; that is, one set of key management parameters governs the activity of all keys on a particular system. They determine when a key is deleted based upon use and the maximum number of bytes transmitted per encrypt key.
Figure 3-14 Key Management Parameters Window
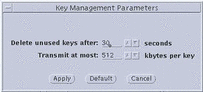
The Key Management Parameters window has four major components.
Change transmit keys every: The system uses the delete unused key parameter to decide when to change active encrypt keys.
Delete unused keys after--This button sets the number of seconds an unused traffic key is kept before it is deleted. The number may be changed by either typing in a new number or clicking on the up and down arrows until the desired number is reached. Default value = 30 seconds. Valid range: 5 seconds to 10,000 seconds.
Transmit at most--This button sets the maximum amount of information that can be transmitted using a particular key. When the set amount is reached, the key is changed. The number can be changed by either typing in a new number or clicking on the up and down arrows until the desired number is reached. Default value = 512 Kbytes per key. Valid range: 1 Kbyte per key to 10,000 Kbytes per key.
Management Buttons--These three buttons enable you to apply the new values, return to the default values, or dismiss the window without changes:
-
Apply--Makes the changes made in the window active.
-
Default--Returns the values in the window to the default values (30 seconds and 512 Kbytes).
-
Cancel--Dismisses the window without changing anything.
- © 2010, Oracle Corporation and/or its affiliates
