Chapter 2 Setting Up Remote Administration in Routing Mode
Typically, you use SunScreen in routing mode if you need a machine to act as both a router and a firewall. In this mode, the interfaces have IP addresses and perform IP routing functions, while the SunScreen software restricts the packet flow between those interfaces. This example shows how you would set up a routing mode Screen and connect it to a remote Administration Station.
Network Example
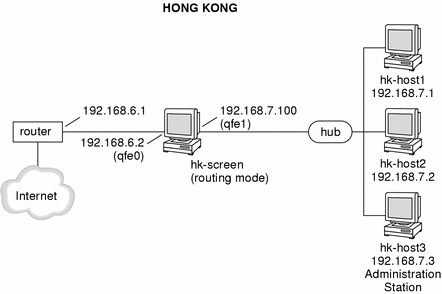
The example in Figure 2-1 shows the Hong Kong segment of the network. A remotely administered Screen, hk-screen, is set up in routing mode with two interfaces (configured with IP addresses on separate subnets). In this example, traffic between the Screen and the Administration Station is encrypted using SKIP. You can find information about using IKE for encryption in Chapter 5, Creating a VPN and in the SunScreen 3.2 Administrators Overview.
Figure 2-1 Hong Kong Segment of the Sample Company Network
Routing Prerequisites
Before you install SunScreen, make sure the machine can route traffic properly:
-
Each interface connects to a different subnet
-
Network traffic routes correctly between the individual subnets
-
System can forward packets between interfaces
-
Kernel global variable ip_forwarding is set to 1
To set this variable to 1, type:
# ndd -set /dev/ip ip_forwarding 1 |
See the ip(7P) Solaris man page for more details.
Note -
If you are using SunScreen 3.2 Lite, you must set this variable to 0, or your Screen will be limited to two routing interfaces.
Setting Up Remote Administration with SKIP
Before you begin, verify that the Administration Station can communicate with the Screen. After logging on as root, perform the following procedures:
Install the Administration Station Software
-
On the Administration Station, install the SunScreen Administration Station software.
See the SunScreen 3.2 Installation Guide for complete information including command line installation. Also check the SunScreen 3.2 Release Notes, which may show additional installation issues.
-
On Administration Station, generate a local certificate ID and set up SunScreen SKIP as follows:
-
Initialize the SunScreen SKIP directories by typing:
# skiplocal -i
-
Generate the certificate ID by typing:
# skiplocal -k
Because the output of skiplocal -k is verbose, use the command shown in the next step, skiplocal -l, to list the certificate ID you just created in a more clearly understood format.
-
List the certificate ID you just created by typing:
# skiplocal -l
-
Write down the certificate ID for use when installing the SunScreen software on the Screen, for example:
c590723af78f869118cd35dee50680a6
-
Add SunScreen SKIP to all the interfaces by typing:
# skipif -a
-
Reboot the system.
-
Install the Screen Software
-
On the Screen, install the SunScreen Screen software.
Install the Screen with remote administration. If you use the command line to install the Screen software, make sure that you do not install End System SKIP (SUNWes and SUNWesx) on the Screen.
-
Use the Administration Station's certificate ID, when prompted.
-
Write down the Screen's certificate ID for use in the next section.
-
Reboot the Screen upon completion.
Enable Communication Between the Administration Station and the Screen
Return to the Administration Station and add an ACL using the skiptool GUI.
This action allows all hosts not specified by other ACL entries to communicate with the Administration Station system in the clear. Then, the only encrypted traffic will be between this system and the Screen.
Note -
These steps can also be accomplished using the skiphost command as described in the file /etc/opt/SUNWicg/SunScreen/AdminSetup.readme.
-
Launch the skiptool GUI by typing:
# skiptool
-
Click the Add button under Host and choose Off.
-
Type `default' as the hostname and click Apply.
-
Click the Add button under Host and choose SKIP.
-
Type the following information:
screenname as hostname ( hk-screen in this example), MD5 for Remote Key ID, the Screen's certificate ID for Local Key ID. Use the Administration Station's certificate ID for the local Key ID and the default values for key, traffic, and authentication algorithms
-
Verify that Access Control is set to Enabled.
-
Choose Save from the File menu to make your changes permanent.
Enabling SunScreen SKIP allows the Administration Station to begin encrypted communication with the Screen.
-
Continuing on the Administration Station, start a browser and verify that remote administration to the Screen is working by typing a URL like this one:
http://hk-screen:3852
The SunScreen log-in screen for Screen hk-screen appears. For your own configuration, replace hk-screen with the name of you Screen.
Setting Up Remote Administration with IKE
The following section describes how you would set up a remote administration station using IKE instead of SKIP.
Installing a Remote Administration Station
These instruction apply to using SunScreen on a Solaris--based system only. Because the Solaris operating environment does not yet support IKE, there is no built-in facility for generating IKE certificates on a remote Administration Station. So, you must install the Screen packages as well as the administration packages on your system.
On the Screen
-
Install the full Screen software. Create a self-signed Screen certificate using the GUI, or use the command line editor, as follows:
# ssadm certlocal -Iks -m 1024 -t rsa-sha1 -D "C=US, O=Your_Org, CN=screen_name"
-
Export the Screen certificate to a file using the GUI, or the command line editor:
# ssadm certdb -Ie "C=US, O=Your_Org, CN=screen_name" > /tmp/screen_cert
-
Import Administration Station certificate using the GUI, or the command line editor and add the Certificate objects into the SunScreen configuration:
# ssadm certdb -Ia < /tmp/admin_cert
-
Edit the SunScreen policy for certificates.
# ssadm edit policyname edit> add certificate admin_cert SINGLE IKE "C=US, O=YourOrg, CN=admin_name" edit> add certificate screen_cert SINGLE IKE "C=US, O=YourOrg,CN=screen_name" edit> add address admin_addr HOST ip.address edit> add accessremote screen "screen_name" USER "admin" "admin_addr" IPSEC ESP ("DES-CBC", "MD5") AH ("SHA1") IKE("DES-CBC", "MD5", 1, RSA-SIGNATURES, "screen_cert") PERMISSION ALL SCREEN "screen_name" edit> add screen "screen_name" ADMIN_IP "admin_addr" IKE(screen_cert) RIP
Note -The DN must be entered correctly including the space after the commas. Also, no packet filtering rule is required on the Screen.
-
Save and activate policy.
On the Remote Administration Station
-
Install the full Screen software
-
Create a self-signed Screen Certificate:
# ssadm certlocal -Iks -m 1024 -t rsa-sha1 -D "C=US, O=Your_Org, CN=admin_name"
-
Export the Administration Certificate to a file using the GUI or use the command line editor as follows:
# ssadm certdb -Ie "C=US, O=YOUR_ORG, CN=admin_name" > /tmp/admin_cert
-
Import Screen Certificate using the GUI or command line editor:
# ssadm certdb -I -a < /tmp/screen_cert
-
Edit the SunScreen policy for certificates:
# ssadm edit policyname edit > add certificate admin_cert SINGLE IKE "C=US, O=YourOrg, CN=admin_name" edit > add certificate screen_cert SINGLE IKE "C=US,O=YourOrg, CN=screen_name" edit > add address admin_addr HOST ip.address edit > add address screen_addr HOST ip.address
-
Add a packet filter rule like the following:
edit > add rule "remote administration" "admin_addr" "screen_addr" IPSEC ESP("DES-CBC", "MD5") AH("SHA1") IKE("DES-CBC", "MD5", 1, RSA-SIGNATURES, "admin_cert", "screen_cert") ALLOW
- © 2010, Oracle Corporation and/or its affiliates
