Chapter 9 SunScreen and Windows 2000 IKE Interoperability
This chapter provides some examples of how you can make a SunScreen firewall and a machine running Windows 2000 communicate with each other using IKE. SunScreen 3.2 and Windows 2000 each support the following IKE features:
-
Preshared Keys - These keys act like a password to authenticate the communicating endpoints during IKE negotiation.
-
Signed X.509 Certificates - These are certificates signed by a Certificate Authority (CA) as opposed to the self-signed Diffie-Hellman certificates supported by SunScreen (but not Windows 2000).
This chapter provides examples that illustrate the use of both interoperabilty features. You can find command line examples of using IKE in the IKE Policy Rule Syntax section of the Command Line Interface chapter of the SunScreen 3.2 Administrators Guide.
Network Example
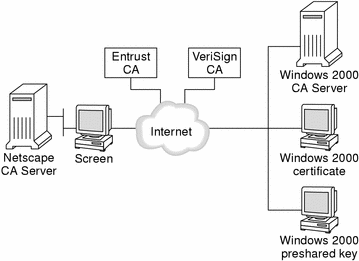
Figure 9-1 shows a SunScreen communicating with a Windows 2000 systems over the Internet. The Screen is using IKE preshared keys and also using signed certificates. Some of the CAs supported by Windows 2000 are also shown. SunScreen does not restrict the use of CAs to these authorities.
In this example, the Screen is communicating with one Windows 2000 system using an IKE preshared key and is also communicating with another system using CA signed certificates.
Figure 9-1 Windows 2000-SunScreen Interoperability
Using Preshared Keys
Preshared keys function as a type of password which authenticates each side of a communications channel during IKE negotiation. The actual preshared key (an ASCII text string) is not sent over the wire but a hash of it is used instead. Once the IKE parameters are successfully negotiated, regular secure communications can proceed. While this authentication method is simple to set up, it typically does not scale well.
Note -
Certain SunScreen features like remote administration require the use of certificates. So, you cannot use a Windows 2000 system to remotely administer a Screen using preshared keys.
Configuring the Screen to Use Preshared Keys
This sections describes how you set up SunScreen to use IKE preshared Keys.
Set Up the Screen
-
Select and edit the appropriate policy.
-
Define an IPsec Key Common Object.
Note -This is an optional step as you can also enter a preshared key directly into a field on the Rule Definition Action Details window.
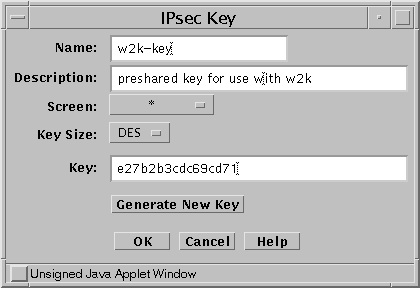
In the Common Object panel select IPsec Key and New; the IPsec Key dialog appears (see Figure 9-2).
Figure 9-2 IPsec Key Dialog Window
-
Fill in the required fields
Provide a Name and Description for the object as well as selecting the desired key size from the Key Size list. If you were using a preshared key generated by another system, you could type the key into the Key field. If you were using SunScreen to generate the key, you would click the Generate New Key button. The key does not have to be numeric, so you could for instance use a phrase.
-
Define the required Address objects.
In this example, you would define HOST type Address objects for the following systems: bos-host5, sf-w2kremote, and sf-w2k1.
-
Create a Packet Filtering rule that allows encrypted communication between the systems using the IKE preshared key.
In this example, telnet is the required service but it could be any service. The way you define the rule is similar to other IKE encryption rules except that the Authentication Method is PRE-SHARED (for more details on defining Packet Filtering IKE rules, see "Create Packet Filtering Rules with the ENCRYPT action".) See Figure 9-3 for an example of what the Rule Definition and Action Details windows would look like.
Figure 9-3 Rule Definition Windows for PreShared Key
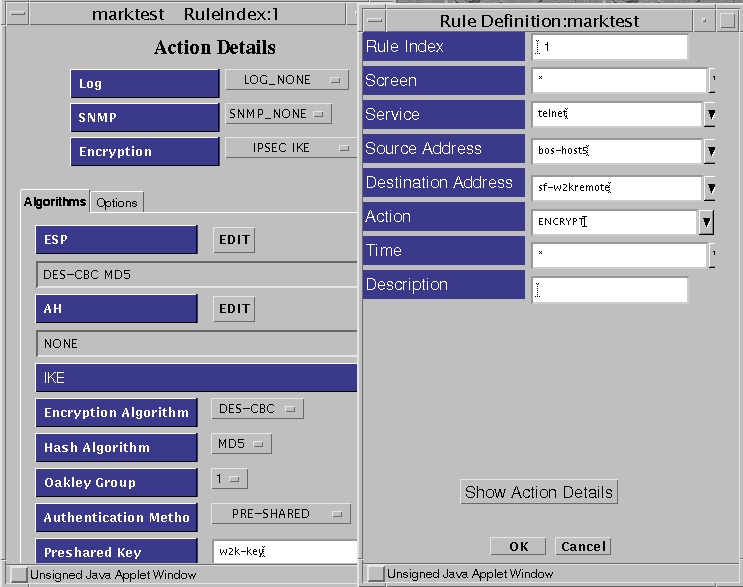
Note -The Oakley Group field on the Screen and the DH Group field on the Windows 2000 system must use the same value.
-
Click the Options tab and select the IKE mode.
Your choices are Tunnel or Transport mode. Tunnel mode encapsulates and encrypts the entire packet including the IP header for maximum security. Transport mode encapsulates and encrypts only the data portion of the IP packet resulting in smaller packets and potentially better throughput as the Screen is relieved of the overhead of decrypting the IP header. SunScreen and Windows 2000 both support IKE Transport and Tunnel modes.
If you choose Tunnel mode, you can supply the Source and Destination Tunnel addresses. You can also supply Source and Destination Screens. If you choose Transport mode, you can only specify Source and Destination Screens.
If the Source Address is the Screen, specify the Screen object in the Source Screen field. If the Destination Address is the Screen, specify the Screen object in the Destination Screen field.
-
Save and activate the policy.
Configuring the Windows 2000 System to Use Preshared Keys
See the Windows 2000 online help for specific instructions on how to create a Security Policy with an IKE filter that uses preshared keys. You can also refer to the Microsoft White Paper How to Configure IPSec Tunneling in Windows 2000 which is available from their web site.
When you create the Security Policy, make sure all the IKE parameters on the Windows system match the IKE parameters on the Screen, including:
-
ESP and/or AH
-
Encryption Algorithm
-
Hash Algorithm
-
Authentication Method
Make sure he the DH Group value is the same as the Oakley Group value on the Screen. Lastly, use the same preshared key as the key used on the Screen.
Note -
Windows 2000 uses an ACSII character string to specify the preshared key. SunScreen uses an ASCII hexidecimal string for the same purpose. For example, if you specified the preshared key as ABC on the Windows 2000 system, you would specify the same key as 414243 on the SunScreen system.
Using CA Signed Certificates
A more secure method than using preshared keys is using CA signed X.509 certificates. These certificates must be digitally signed by a Certificate Authority (CA) supported by both the Windows 2000 system and the SunScreen system. Currently, Microsoft supports certificates signed by its own Windows 2000 Server CA as well as a number of public CA authorities (see the Trusted CA Authorities list on Windows 2000, all of these vendors qualify as Root CAs). You can also use non-public CA's like Netscape Certificate server, if you import the CA's root Ccertificate into the Windows 2000 Trusted Root Certificate store. Self signed certificates are not supported by Microsoft
Each side must be able to follow each signed certificate up its certificate chain to the Root CA. They accomplish verification by having the Root CA's certificate in a special certificate store (the IKE root CA certificates GROUP certificate object on the Screen and the Trusted Root Certificate store on the Windows 2000 system). Because both systems must use certificates signed by a CA common to both systems, you cannot use self signed DH certificates to interoperate with Windows 2000.
Note -
Certificates are necessary in order to have a Windows 2000 system act as a remote Administration Station managing a Screen.
Configuring the Screen to Use CA Signed Certificates
The following sections describe how you would set up the Screen and the Windows 2000 system to interoperate.
Set Up the Screen
-
Generate a Certificate Signing Request
-
From the Common Objects panel, select Generate IKE Certificate
-
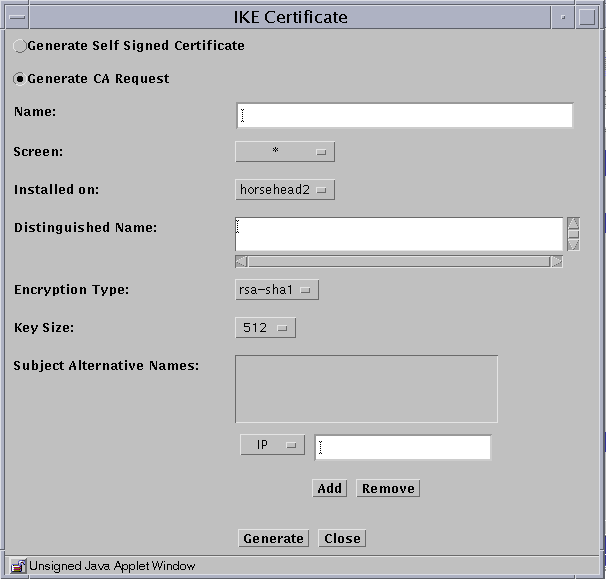
When the IKE Certificate dialog appears, click the Generate CA Request button; see Figure 9-4
Figure 9-4 Generate CA Signing Request
-
Fill in the required fields.
Type in a Distinguished Name and make sure that the Encryption Type and Key Size match the related parameters used by the Windows 2000 system for its own certificate.
-
Click the Generate button.
SunScreen generates a Certificate Signing Request (CSR) and also creates and stores a private key. The following figure shows the CSR.
Figure 9-5 IKE CA Certificate Signing Request
You can copy the text or save into a file for use in your signing request.
-
-
Present the CSR to the CA.
Have the certificate signed and acquire the new certificate.
-
Import the CA signed certificate into the Screen
-
From the common Objects panel, choose Import IKE Certificate. The Import IKE Certificate screen appears
-
Specify a name and description.
-
Choose an import method
Click the appropriate button and then either specify a file to import or paste the signed certificate into the text area.
-
Click the Install Certificate button.
-
-
Add the IKE Root CA Certificate to the Screen.
You accomplish this task by adding the Root CA certificate to the IKE root CA Certificates GROUP object.
-
Acquire the Root CA certificate and import it into the Screen's certificate store.
-
After you finish the import, in the Common Objects panel, search for the IKE root CA certificates object.
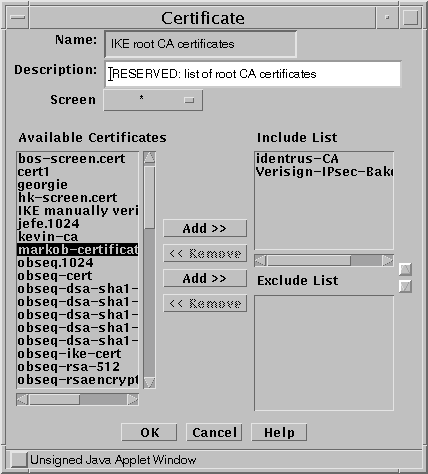
When you find the object, select it and click the edit button. The Certificates object dialog appears. See Figure 9-6.
Figure 9-6 Import Root CA
-
Select the Root CA certificate you want and add it to the Include List.
-
Click OK to finish the task.
-
-
Edit the Root CA certificate object.
A requirement of Windows 2000 for IKE interoperability is that you must specify the Root CA certificate by its ISSUER Distinguished Name.
Configuring Windows 2000 to Use CA Signed Certificates
The following section describes in general terms how you would set up a Windows 2000 system to interoperate with a Screen. This section only provides general steps. For specific instructions on setting up the Windows 2000 system see the Windows 2000 online help and also refer to these White Papers which are available on the Microsoft web site.
-
How to Configure IPSec Tunneling in Windows 2000
-
How to Install a Certificate for Use with IP Security
-
Step-by-Step Guide to Internet Protocol Security IPSec
Set Up the Windows 2000 System
-
Obtain a private key and certificate signed by the same CA used by the Screen with whom you wish to communicate.
-
Make sure that the CA Root certificate is in the Trusted Root CA Certificate store.
-
Create an IPSec security policy.
Create an IKE rule that allows communication between the Screen and the Windows 2000 system.
-
Be aware of the following interoperability requirements:
-
The Authentication Method should be Certificate Authority and the Root CA list must contain the common Root CA certificate.
-
The filter action should be Negotiate Security and it should only specify one security method.
-
Using the Encryption Action on the Screen
To set up a packet filtering rule on the Screen use the same procedure as would be used with any IKE encryption rule. However, you must be aware of the following interoperability requirements:
-
The ESP and AH values must match those specified in the Filter Action on the Windows 2000 system.
-
The encryption Algorithm must be either DES or 3DES.
-
The Authentication Method must be RSA-SIGNATURES
-
The Oakley group must be consistent with the DH values used by the Windows 2000 system during IKE negotiation. You are restricted to those values supported by the Windows 2000 system. For example, Windows 2000 does not support Oakley group 5. The following table shows the default Oakley Group values used by Windows 2000. If someone on the Windows 2000 side changes these default values (unlikely based on how far down they are buried in the GUI) , you would have to use a value that matches their new value.
Encryption Algorithm
Hash Algorithm
Oakley Group Value
3DES
SHA1
2
3DES
MD5
2
DES
SHA1
1
DES
MD5
1
-
If the rule permits traffic from the Windows 2000 system to the Screen, the Source Certificate must be the Root CA certificate and the Destination Screen is the Screen object.
-
If the rule permits traffic from the Screen to the Windows 2000 system, the Destination Certificate must be the Root CA certificate and the Source Screen is the Screen object.
- © 2010, Oracle Corporation and/or its affiliates
