Chapter 2 Auditing Setup
The focus of this chapter is on setting up auditing for a network of Trusted Solaris workstations. It also describes how to set up auditing for a non-networked Trusted Solaris workstation.
Planning Auditing at Your Site
When the system administrator and security administrator configure the first workstation for Trusted Solaris, auditing is enabled and a limited number of audit records are collected to a default audit location, workstation_name:/var/audit. The security administrator needs to plan what to audit and whether to customize site-specific event-to-class mappings. The system administrator plans disk space (local and remote) for the audit files, an audit administration server, and the order of installation.
Planning auditing for a non-networked workstation is a bit simpler. For a single workstation, customizing event-to-class mappings may not be worth the time. Your most important task is to ensure that auditing does not slow down your work. Planning the size and locations of auditing partitions can prevent work slowdown, and a regular maintenance schedule can automatically back up and free up the audit partition for more audit records.
Planning What to Audit
Trusted Solaris collects user actions and non-attributable (in the class na, non-attribute) events into audit classes. It is these audit classes, each of which holds a number of events, that are audited for success, for failure, or for both.
Before configuring auditing, understand the audit flags and the types of events they flag. Develop a philosophy of auditing for your organization that is based on the amount of security your site requires, and the types of users you administer.
Unless the process audit preselection mask is modified dynamically, the audit characteristics in place when a user logs in are inherited by all processes during the login session, and, unless the databases are modified, the process preselection mask applies in all subsequent login sessions.
See Appendix A, Event-to-Class Mappings for a list of provided audit classes. The list shows per audit class, each audit event's corresponding system call or user command, and points you to its audit record format.
The security administrator plans what to audit based on the site security policy. You can configure a system-wide setup and user exceptions/additions.
-
Decide if non-attributable events should be audited.
The audit flag na represents the non-attributable class of events. For example, accessing the PROM, booting, and remote mounting are non-attributable events. See "Events in Audit Class na " for a list of the events in the default non-attribute class.
When you audit a class, you audit all events in that class. If you want to customize the non-attributable class, see "Planning a Site-Specific Event-to-Class Mapping".
To audit non-attributable events, you will enter the na flag on the naflags: line of the audit_control file.
-
Decide whether to audit them for success, for failure, or for both.
To audit non-attributable events for success, the naflags: line of the audit_control file would look like:
naflags:+na
To audit non-attributable events for failure:
naflags:-na
To audit non-attributable events for both:
naflags:na
-
Decide if all events will be audited.
Note -The class all includes all auditable events in the Trusted Solaris software system. While unusual circumstances may dictate use of this class, typically you would avoid auditing all events.
-
If you are not going to audit all events, repeat Steps Step 1 and Step 2 for the other audit classes for the class na.
The decisions you have made in Steps Step 3 and Step 4 you will enter in the audit_control file when establishing auditing on the first workstation.
To audit these events, you will enter their flag on the flags: line of the audit_control file, just as you entered the na flag in the naflags: line.
-
Determine if there are particular users or roles that should be audited slightly differently than the system-wide setup.
You will enter user exceptions to the system setup in the audit_user file.
-
Be consistent.
All workstations in a Trusted Solaris network should have identical naflags: entries in their audit_control files.
All workstations in a Trusted Solaris network should have identical flags: entries in their audit_control files.
All workstations in a Trusted Solaris network should have identical audit_user files.
Considerations When Planning What to Audit
What is audited at your site is based on your site policy and the costs of auditing (time, efficiency, disk space). For a discussion of the costs, see "Controlling Audit Costs ". The following are factors to consider when using auditing as it is implemented in the Trusted Solaris environment.
-
Every audit record stands alone, so records can quickly fill up disk space.
Therefore, you might want to start with a small amount of auditing and see how the audit partitions fill. You can then make more educated estimates of disk requirements and an audit archiving schedule. You can refine audit classes as you get an estimate of the size of the audit trail.
-
The number of events in an audit class does not necessarily correlate to how many records are generated.
For example, the file read class contains about the same number of events as the login or logout class. Enabling the file read class for success is likely to generate many more records than enabling the login or logout class for success.
-
Auditing for failure locates abnormal events; auditing for success monitors system use.
If site policy requires monitoring of system use, you will want to set aside more space for the audit trail than if you are auditing for abnormal events.
-
Auditing for failure may generate many fewer records than auditing for success.
For example, auditing for failure of file read events in a Trusted Solaris system of sophisticated users can generate many fewer records than turning on the file read class for success.
-
Configuring the audit classes differently, or setting up new audit classes for audit events can more efficiently satisfy your site requirements. By excluding audit events that site policy does not require to be audited, the audit trail is smaller.
For example, you may want to create a class de for devices. When configuring devices, audit the class for success to generate a record of what devices have been set up and tested. When all devices have been configured, you may want to audit the class for failure.
-
Configuring some classes to be audited intermittently may satisfy your site requirements.
For example, you may want to audit the audit class you created, de, intermittently. A cron job, or the command auditconfig(1M), enable you to turn auditing on and off for particular classes and set other audit flags dynamically.
Planning a Site-Specific Event-to-Class Mapping
Optional: Skip this section if you are using the default event-to-class mappings provided by Trusted Solaris. Do not skip this section if you have decided to rearrange what events are assigned to what classes, or to create new classes or new events.
Trusted Solaris allows 32 audit classes, including the class all. Your site may add classes until the total number is 32.
The security administrator plans site-specific mappings. To plan site-specific mappings:
-
Decide what classes are needed.
-
Decide what events belong in what classes.
-
Decide what events should be copied to another class or classes.
An audit event can belong to more than one class. For example, the audit event AUE_RENAME belongs to the classes file create and file delete in the default event-to-class mapping.
-
Decide what events should be moved to another class or classes.
-
Decide what events should be added to a class or classes.
-
-
For each class, decide whether to audit it for success, for failure, or for both.
When new software programs include audit events not provided by Trusted Solaris 2.5.1 software, add the events to existing classes or create a new classes for the new events.
Considerations When Changing Event-to-Class Mappings
The following are factors to consider when changing the contents of default audit classes and creating new ones in the Trusted Solaris environment.
-
This document, Trusted Solaris Audit Administration, reports the default auditing configuration.
Document your site's modifications to the auditing defaults, and make the document available to the administrators handling audit administration.
-
If you are networked, you must change the auditing configuration files on all the workstations when you change the files on one workstation.
A network of Trusted Solaris workstations behaves like one workstation. When auditing is enabled, it is enabled on every workstation, and every workstation is audited for the same classes, has the same defaults, has the same user exceptions, and has the same event-to-class mappings as every other Trusted Solaris workstation in the network.
Planning Space for Audit Records
Storing audit records on a non-networked workstation involves setting up at least two local partitions dedicated to audit records, one primary and one backup, and planning a maintenance schedule.
Storing audit records for a network of workstations involves setting up a local (backup) partition dedicated to audit records, plus a network of audit servers with partitions for remote (primary) audit storage, and plus an audit administration server from which the entire audit trail can be monitored. The audit trail is every audit file (audit files hold audit records generated on a workstation) created by every workstation on the network.
Planning Space on a Non-Networked Workstation
On a non-networked workstation, plan the size of a disk partition to hold audit records. For efficiency, it is best to place the audit records on a separate disk. For safety, you may want to create two audit partitions on that disk, one as the primary storage area and the other as a backup if the first partition gets full. Set filesystem security attributes to set on the audit directory to prevent snooping on the audit trail.
-
Estimate the volume of auditing between audit record backups.
Balance your security needs against the availability of disk space for audit trail storage.
A rule of thumb is to assign 200 MB of space per workstation. However, the disk space requirements for the workstation are based on how much auditing you perform and may be far greater than this figure.
"Controlling Audit Costs "and "Auditing Efficiently" provide guidance on how to reduce storage requirements.
-
Decide at what point the audit file system sends a warning that it is filling up.
You will specify what is called the minfree limit for audit partitions in the audit_control file. This is the percentage of disk space remaining when the audit administrator is sent an email message (by the audit_warn alias) that the disk is getting full. The default is to send the warning when there is 20% disk space remaining. This percentage is tunable.
Planning Space on a Network of Workstations
A networked system should include audit servers to store audit files for users' workstations, an audit administration server for central audit analysis and backup, and a local audit partition on every workstation. You may want to set filesystem security attributes on the directories and mount points to prevent snooping on the audit trail. Create a worksheet to record your auditing plan, or use another mechanism that helps you track the auditing network that you set up.
-
Determine how much auditing your site needs to do.
Balance your site's security needs against the availability of disk space for audit trail storage.
A rule of thumb is to assign 200 MB of space for each workstation that will be on the distributed system, but remember that the disk space requirements at your site is based on how much auditing you perform and may be far greater than this figure per workstation. If you are able to dedicate a local and a remote disk for auditing, one way to set up audit partitions is to divide each disk into two partitions.
"Controlling Audit Costs "and "Auditing Efficiently" provide guidance on how to reduce storage requirements while still maintaining site security.
-
Decide at what point each audit file system for the workstation sends a warning that it is filling up.
You will specify what is called the minfree limit for audit partitions in the audit_control file. This is the percentage of disk space remaining when the audit administrator is sent an email message (by the audit_warn alias) that the disk is getting full. The default is to send the warning when there is 20% disk space remaining. This percentage is tunable.
-
Determine which workstations will be audit servers.
The system administrator and you will install these workstations before installing the audit client workstations.
-
Plan a local audit partition for each workstation.
The local partition provides a backup in cases where the audit server's partitions are full or when the network is unreachable.
-
Determine which clients will use which audit file systems on which audit server.
Lay out the auditing network. The following figure shows an audit server, egret, with file systems /etc/security/audit/egret[.n]/files available to store remote hosts' audit records.
Figure 2-1 Audit Server egret's Audit File Systems
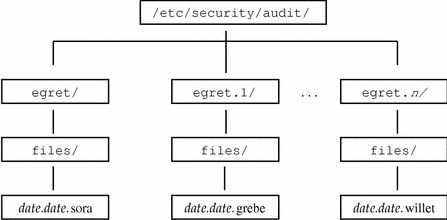
-
Follow the naming conventions for audit file systems.
As illustrated in the figure, the convention for naming the audit file systems on a workstation is:
/etc/security/audit/workstationname/files /etc/security/audit/workstationname.1/files /etc/security/audit/workstationname.2/files /etc/security/audit/workstationname.3/files ...
For an explanation of the naming scheme, see "Audit Storage".
Planning the Rollout
Rolling out the auditing plan to the workstations is a job coordinated by the system administrator, who sets up the disks and the network of audit storage, and the security administrator, who decides what is to be audited and enters the information in the audit configuration files. Together, you want to set up an audited network of workstations where:
-
From one workstation, the audit analyst is able to read every audit file on every workstation in the network, and the system operator is able to back up every audit file on every workstation on the network.
How: Create an administration server, and mount all audit directories on the server.
-
The audit trail is not available for snooping.
How: Protect audit directories with appropriate discretionary access controls and mandatory access controls. You may want to audit directory access.
-
Each workstation in a Trusted Solaris system is writing records to the audit trail from the first time it is in multiuser mode, and thereafter.
How: Create audit servers before you create user workstations. On all workstations, create a dedicated audit partition during installation.
-
Every workstation is audited identically.
How: Create a central location for all audit configuration files: audit_event, audit_class, audit_control, audit_startup, audit_user, and audit_warn. The examples use the directory /export/home/tmp on the NIS+ master. Copy these files to a tape or diskette that is copied to every workstation.
-
When an end user's workstation is configured, it is able to immediately send its audit records to an audit server.
How: Create the audit servers and configure them for receiving audit records before the end user workstations are set up. Create a procedure to copy the system-wide audit configuration files to each workstation and to modify the audit_control file for the audit storage locations for that workstation.
-
End user's workstations are not slowed down by writing audit records.
How: Regular archiving of the audit trail frees up audit server disk space. Placing the local audit storage on a separate or little-used disk will enable the end user to work quickly when audit records are stored locally.
Rolling Out Auditing at Your Site
To roll out auditing, the system administrator sets up the audit administration server, the audit file servers, the local audit partitions, and what usernames are warned of audit trouble. The security administrator edits the audit_control(4) file on the NIS+ root master, and edits other audit configuration files before copying them to a central directory for distribution by tape or floppy. The audit configuration files are copied from the tape to each workstation as it is configured by the install team. The security administrator edits the dir: lines in the audit_control file on each workstation before the system is rebooted.
Note -
Administrators should understand that Trusted Solaris only records the security-relevant events that it is configured to record (that is, by preselection). Therefore any subsequent audit can only consider the events recorded. If auditing is not configured to record the security-relevant events for the particular system environment in which it operates, it will not be possible to audit. This may mean that attempts to breach the security of the system go undetected, or that the administrator is unable to detect the user responsible for an attempted breach of security. Administrators should regularly analyze audit trails to check for breaches of security.
System Administrator's Audit Setup Tasks
Table 2-1 Basic Auditing Setup by the System Administrator|
Task |
For the procedure, see... |
|---|---|
|
Create audit partitions | |
|
Create audit administration server |
Trusted Solaris Installation and Configuration or Trusted Solaris Administrator's Procedures |
|
Install audit file servers |
Plan to install them before audit clients |
|
Create files directory | |
|
Export audit partitions (networks only) | |
|
Edit Aliases database | |
|
Mount audit partitions (networks only) |
Security Administrator's Audit Setup Tasks - Basic
Table 2-2 Basic Auditing Setup by the Security Administrator|
Task |
For the procedure, see... |
|---|---|
|
On first workstation |
|
|
Edit audit_control file | |
|
| |
|
Set Solaris security attributes | |
|
Edit audit_user file | |
|
Edit audit_startup file | |
|
Copy for distribution (networks only) |
"To Distribute Audit Configuration Files to a Network of Workstations" |
|
Set security attributes |
Security Administrator's Audit Setup Tasks - Advanced
Table 2-3 Advanced Auditing Setup by the Security Administrator|
Task |
For the procedure, see... |
|---|---|
|
On first workstation |
|
|
Edit audit_event file
| |
|
Edit audit_class file | |
|
Copy for distribution (networks only) |
"To Distribute Audit Configuration Files to a Network of Workstations" |
Audit Shutdown and Startup Procedures
The following procedures describe how to enable and disable auditing for one or more workstations. The commands should be run only on a diskfull workstation, and never on a diskless client.
Auditing tasks require commands and actions that are limited to particular roles and particular labels. Read each task for the administrative role that can perform it, and the label required. See "To Execute Commands that Require Privilege" for how to assume a role and open a privileged shell.
To Disable Auditing
-
As role secadmin, at label
admin_low, open the script /etc/init.d/audit using the Admin Editor.
Note -This should be done only if auditing is not a site security requirement, or in cases of audit file overflow. The security administrator is responsible.
-
Comment out the start script:
... # Start the audit daemon # if [ -f /etc/security/audit_startup ] ; then # echo "starting audit daemon" # /etc/security/audit_startup # /usr/sbin/auditd & # fi ...
-
Write and quit the file.
-
Open the script /etc/init.d/drvconfig using the Admin Editor.
-
Add the following lines to the end of the file:
# Disable auditing # /usr/bin/adb -wk /dev/ksyms /dev/mem > /dev/null <<end audit_active/W 0 end
-
Prevent spurious messages about the audit daemon at shutdown by commenting out the stop script in /etc/init.d/audit:
... # Stop the audit daemon # if [ -f /etc/security/audit_startup ] ; then # /usr/sbin/audit -t # fi
-
Write and quit the file.
-
For the changes to take effect, reboot.
Note -A user or role requires authorization to reboot the workstation.
To Enable Auditing
By default, auditing is enabled. If you have disabled auditing, enable it by reversing the above procedure.
-
As role secadmin, at label
admin_low, open the script /etc/init.d/audit using the Admin Editor. -
Remove the comments from the audit start script:
... # Start the audit daemon if [ -f /etc/security/audit_startup ] ; then echo "starting audit daemon" /etc/security/audit_startup /usr/sbin/auditd & fi ...
-
Write and quit the file.
-
Enable the audit daemon to exit gracefully at shutdown by removing the comments in the stop script in /etc/init.d/audit:
... # Stop the audit daemon if [ -f /etc/security/audit_startup ] ; then /usr/sbin/audit -t fi
-
Write and quit the file.
-
Open the script /etc/init.d/drvconfig using the Admin Editor.
-
Comment out the Disable auditing lines:
# Disable auditing # # /usr/bin/adb -wk /dev/ksyms /dev/mem > /dev/null <<end # audit_active/W 0 # end
-
Write and quit the file.
-
For the changes to take effect, reboot using the Shut Down menu item from the TP (Trusted Path) menu.
Basic Audit Setup Procedures
The following procedures describe how to set up auditing for one or more workstations.
To Create Dedicated Audit Partitions
During installation, the install team creates dedicated audit partition(s) when formatting the disks.
Use the naming convention /etc/security/audit/workstation_name(.n)
A diskfull workstation should have at least one local audit directory, which it can use as a directory of last resort, if unable to communicate with the audit server.
See "Audit Storage" for an explanation of the naming convention.
On an audit file server, most partitions hold audit files, as is shown in the following example of the egret audit file server:
|
Disk |
Slice |
Mount point |
Size |
|---|---|---|---|
|
c0t2d0 |
s0 |
/etc/security/audit/egret |
1.0 GB |
|
|
s1 |
/etc/security/audit/egret.1 |
.98 GB |
|
|
s2 |
entire disk |
1.98 GB |
|
c0t2d1 |
s0 |
/etc/security/audit/egret.2 |
502 MB |
|
|
s1 |
/etc/security/audit/egret.3 |
500 MB |
|
|
s2 |
entire disk |
1002 MB |
Note -
Another disk holds egret's / (root) and /swap partitions.
On a diskfull workstation, including the audit administration server, at least one partition should be dedicated to local audit files, as is shown in the following example of the workstation willet:
|
Disk |
Slice |
Mount point |
Size (MB) |
|---|---|---|---|
|
c0t3d0 |
s0 |
/ |
70 |
|
|
s1 |
swap |
180 |
|
|
s2 |
entire disk |
1002 |
|
|
s3 |
/usr |
350 |
|
|
s4 |
/etc/security/audit/willet |
202 |
|
|
s7 |
/export/home |
200 |
Hints
A rule of thumb is to assign 200 MB of space for each workstation. However, the disk space requirements at your site will be based on how much auditing you perform and may be far greater than this figure.
Fewer and large partitions are more efficient than more and smaller ones.
Note -
To add a disk to hold audit partitions after installing the workstation, see the Solaris 7 System Administration Guide, Volume II. To protect the disks with Trusted Solaris security attributes, see Trusted Solaris Administrator's Procedures.
To Execute Commands that Require Privilege
Most commands for setting up auditing require the use of a profile shell, where commands can run with privilege. Auditing also requires the use of actions in the System_Admin and Solstice_Apps folders of Application Manager.
Log In and Assume an Administrative Role
-
Log in to the workstation as yourself.
-
Enter your user name and press the Return key.
If the workstation is protected against anyone logging in, the Enable Logins dialog is displayed.
-
If you are allowed to enable logins, click the Yes button after Login:.
If you are not allowed to enable logins, ask the administrator to enable logins.
-
Enter your password.
-
Click OK to dismiss the dialog.
You are presented with the message of the day and a label builder screen. In a single-label system, the screen describes your session label. In a multilabel system, it presents you with a label builder to choose your session clearance.
-
Accept the default unless you have a reason not to.
Press the Return key or click the OK button and be logged in.
-
-
Assume an administrative role that you have been assigned.
Open a Profile Shell
-
As an administrative role, in a workspace at the label required by the task, launch a terminal by right-clicking the background and selecting Tools > Terminal from the menu.
-
Enter the clist command.
# clist
If a list of commands prints, you are in a profile shell.
To Remove Free Space (Optional)
-
As role admin, at label
admin_low, unmount the audit partitions from the workstation by running the umount(1M) command.For example, on the audit file server egret:
egret$ umount /etc/security/audit/egret egret$ umount /etc/security/audit/egret.1 egret$ umount /etc/security/audit/egret.2 egret$ umount /etc/security/audit/egret.3
-
Reduce reserved filesystem space on each partition to 0% with the command tunefs -m 0.
The security administrator sets the reserved filesystem space (called the minfree limit) in the audit_control(4) file.
For example, on the audit file server egret:
egret$ tunefs -m 0 /etc/security/audit/egret egret$ tunefs -m 0 /etc/security/audit/egret.1 egret$ tunefs -m 0 /etc/security/audit/egret.2 egret$ tunefs -m 0 /etc/security/audit/egret.3
Similarly, on the workstation willet:
willet$ umount /etc/security/audit/willet willet$ tunefs -m 0 /etc/security/audit/willet
See the tunefs(1M) man page for more information on the advantages and disadvantages of tuning a file system.
To Protect an Audit File System
-
As role secadmin, at label
admin_low, set the appropriate file permissions on every audit file system while the file system is unmounted.For example, on the audit file server egret:
egret$ chmod -R 750 /etc/security/audit/egret egret$ chmod -R 750 /etc/security/audit/egret.1 egret$ chmod -R 750 /etc/security/audit/egret.2 egret$ chmod -R 750 /etc/security/audit/egret.3
On the workstation willet:
willet$ chmod -R 750 /etc/security/audit/willet
-
As role secadmin, at label
admin_high, set any Trusted Solaris security attribute defaults required by your site security policy on every audit file system while the file system is unmounted.To run the command at the label
admin_high, you must create anadmin_highworkspace. Follow the procedure in "To Create an Admin_High Workspace".For example, the following command on the audit file server egret should be repeated for all of its audit partitions:
egret$ setfsattr -l "admin_high;admin_high" -s "[admin_high]" \ /etc/security/audit/egret
On the workstation willet:
willet$ setfsattr -l "admin_high;admin_high" -s "[admin_high]" \ /etc/security/audit/willet
The -l option ensures that all files created in the file system are labeled
admin_high, and the -s option sets the partition's default sensitivity label for the audit files. See the setfsattr(1M) man page for more information.
Note -The local audit file systems must already be in the host's /etc/vfstab file.
To Create an Audit Directory
-
As admin, at label
admin_high, remount the local audit file systems.Follow the procedure in "To Create an Admin_High Workspace" to get an
admin_highprocess.For example, on the audit file server egret:
egret$ mount /etc/security/audit/egret egret$ mount /etc/security/audit/egret.1 egret$ mount /etc/security/audit/egret.2 egret$ mount /etc/security/audit/egret.3
Similarly, on the workstation willet:
willet$ mount /etc/security/audit/willet
-
Create a directory named files at the top of each mounted audit partition.
For example, on the audit file server egret:
egret$ mkdir /etc/security/audit/egret/files egret$ mkdir /etc/security/audit/egret.1/files egret$ mkdir /etc/security/audit/egret.2/files egret$ mkdir /etc/security/audit/egret.3/files
On the workstation willet:
willet$ mkdir /etc/security/audit/willet/files
To Share an Audit File System
-
As role admin, at label
admin_low, enter every local audit file system in the local host's dfstab(4) file.-
Click the Application Manager, double-click the System_Admin folder, and double-click the Share Filesystems action.
-
Enter and protect each local audit directory in the dfstab file.
For example, the audit file server egret has the following entries:
share -F nfs -o ro -d "local audit files" /etc/security/audit/egret share -F nfs -o rw=willet:audubon -d "audit willet" /etc/security/audit/egret.1 share -F nfs -o rw=grebe:audubon -d "audit grebe" /etc/security/audit/egret.2 share -F nfs -o rw=sora:audubon -d "audit sora" /etc/security/audit/egret.3
The workstation willet has the following entry:
share -F nfs -o ro -d "local audit files" /etc/security/audit/willet
-
-
Reboot the workstation by choosing Shut Down from the TP menu.
To Mount an Audit File System
-
As role admin at label
admin_low, on audubon, the audit administration server, create a mount point for every audit directory in the Trusted Solaris network.For example, on the audit administration server audubon:
audubon$ mkdir /etc/security/audit/willet audubon$ mkdir /etc/security/audit/egret audubon$ mkdir /etc/security/audit/egret.1 ...
-
As role admin, at label
admin_low, enter every audit partition on the network in the audit administration server's vfstab(4) file.Mount audit directories with the read-write (rw) option. Mount remote partitions using the soft option.
-
Click the Application Manager, double-click the System_Admin folder, and double-click the Set Mount Points action.
-
Enter the mount points in the vfstab(4) file.
The following shows part of the vfstab file on audubon:
egret:/etc/security/audit/egret - /etc/security/audit/egret nfs - yes bg,soft,nopriv egret:/etc/security/audit/egret.1 - /etc/security/audit/egret.1 nfs - yes bg,soft,nopriv egret:/etc/security/audit/egret.2 - /etc/security/audit/egret.2 nfs - yes bg,soft,nopriv egret:/etc/security/audit/egret.3 - /etc/security/audit/egret.3 nfs - yes bg,soft,nopriv willet:/etc/security/audit/willet - /etc/security/audit/willet nfs - yes bg,soft,nopriv ...
-
-
On each workstation, create the mount points for the remote audit file servers' partitions that are used by the workstation, and enter them in the vfstab(4) file. Do this as role admin, at label
admin_low.For example, to create the mount points on the workstation willet:
willet$ mkdir /etc/security/audit/egret willet$ mkdir /etc/security/audit/audubon.2
-
Click the Application Manager, double-click the System_Admin folder, and double-click the Set Mount Points action.
-
Enter the mount points in the vfstab(4) file.
The following shows part of the vfstab file on willet:
egret:/etc/security/audit/egret - /etc/security/audit/egret nfs - yes bg,soft,nopriv audubon:/etc/security/audit/audubon.2 - /etc/security/audit/audubon.2 nfs - yes nopriv
-
To Reserve Free Space on an Audit File System
-
As role secadmin, at label
admin_low, enter reserve free space in the audit_control(4) file. -
Enter a value between 10 and 20 on the minfree: line.
dir:/var/audit flags: minfree:20 naflags:
-
Write the file and quit the editor.
To Specify the Audit File Storage Locations
-
As role secadmin, at label
admin_low, enter audit storage locations in the audit_control file. -
On the first workstation installed, enter its local audit file system as the value of the dir: line.
The following shows the audit_control file for grebe, the NIS+ root master.
dir:/etc/security/audit/grebe/files flags: minfree:20 naflags:
-
When the audit file servers have been installed and configured, add their (mounted) filesystem names plus their top-level directory, files to the dir: entry.
The mounted file systems are listed before the workstation's local file system, as in:
dir:/etc/security/audit/egret/files dir:/etc/security/audit/egret.1/files dir:/etc/security/audit/grebe/files flags: minfree:20 naflags:
-
Write the file and exit the editor.
-
As role secadmin in an
admin_highprofile shell, execute the audit -s command to have the audit daemon re-read the audit_control file and write audit records to the designated directory.:
$ audit -s
By default, the audit records have been stored in /var/audit. The audit records will now be stored in the first directory in the audit_control file.
To Set Audit Flags
-
As role secadmin, at label
admin_low, enter system-wide audit flags in the audit_control(4) file. -
Enter the na class in the naflags: line if your site is auditing non-attributable events.
dir:/etc/security/audit/egret/files dir:/etc/security/audit/egret.1/files dir:/etc/security/audit/grebe/files flags: minfree:20 naflags:na
-
Enter other classes in the flags: line if your workstation is auditing user-level events.
dir:/etc/security/audit/egret/files dir:/etc/security/audit/egret.1/files dir:/etc/security/audit/grebe/files flags:lo,ad,-all,^-fc minfree:20 naflags:na
See "Sample audit_control File" for an explanation of the syntax of the audit flags' fields.
-
Write the file and exit the editor.
Note -On a distributed system, the audit flags in the audit_control file must be identical on every workstation on the network. See "To Distribute Audit Configuration Files to a Network of Workstations" for a process to distribute master copies of files to all workstations on the network.
To Set User Exceptions to the Audit Flags
As role secadmin, at label admin_low, enter user exceptions to system-wide audit flags in the audit_user(4) file.
-
Open the System_Admin folder from the Application Manager.
-
Double-click the Audit Users action.
-
Enter the user exceptions, write the file, and exit the editor.
For example, the following entry audits the role root for logins and logouts, and never audits the fc class, even if it is being audited for the workstation. The jane entry audits her for all flags specified in the audit_control file except for successful file_read events. Null events, no, are never audited.
# User Level Audit User File # # File Format # # username:always:never # root:lo:no,fc jane:all,^+fr:no
To Warn of Audit Trouble
-
As role admin, at label
admin_low, enter mail alias to warn of audit trouble in the Aliases database. -
Add an alias called audit_warn(1M) for notifying its members of audit trouble.
For example, this audit_warn alias emails the security administrator and the system administrator when the auditing subsystem needs attention.
Alias: audit_warn Expansion: secadmin@grebe,admin@grebe
To Set Audit Policy Permanently
-
As role secadmin, at label
admin_low, enter permanent audit policy in the audit_startup(1M) file. -
Create a script that calls the auditconfig(1M) command with policy options.
The sample audit_startup(1M) script below adds ACLs to audit records, halts the workstation when its audit file systems are full, and at startup, prints the current audit policy to standard i/o.
#!/bin/sh auditconfig -setpolicy +slabel,+acl auditconfig -setpolicy +ahlt auditconfig -getpolicy
-
Write the file and exit the editor
 Caution -
Caution - To run auditing in an evaluated configuration, the cnt policy cannot be turned on; the ahlt policy (the default) cannot be turned off.
To Distribute Audit Configuration Files to a Network of Workstations
-
During installation, as root, at label
admin_low, create a directory on the first installed workstation to hold copies of the audit configuration files customized for your site.The directory would include your customized versions of audit_control, audit_user, audit_startup, and audit_warn. If you have modified event-to-class mappings, it would include audit_event and audit_class. It would not include audit_data.
For example, on grebe, the first workstation in a network:
# mkdir /export/home/tmp
-
Copy the modified files from the /etc/security directory to the /export/home/tmp directory.
# cp /etc/security/audit_control /export/home/tmp/audit_control # cp /etc/security/audit_user /export/home/tmp/audit_user # cp /etc/security/audit_startup /export/home/tmp/audit_startup # cp /etc/security/audit_event /export/home/tmp/audit_event
-
Allocate the tape or diskette device.
Follow the procedure in "To Allocate and Deallocate Devices".
-
Run the tar(1) command to copy the contents of the /export/home/tmp directory to tape or to diskette.
-
Deallocate the tape or diskette device and follow the instructions.
Follow the procedure in "To Deallocate a Device".
-
As root, at label
admin_low, as each new workstation is configured, copy the files from the tape or diskette to the correct directory on the new workstation.-
Prepare the directory for the new files.
# cd /etc/security # mv audit_control audit_control.orig # mv audit_startup audit_startup.orig # mv audit_warn audit_user.orig # mv audit_event audit_event.orig
-
Allocate the appropriate device at the label
admin_low.Follow the procedure in "To Allocate and Deallocate Devices".
-
Deallocate the device.
Follow the procedure in "To Deallocate a Device".
-
-
As role secadmin, at label
admin_low, modify the audit_control file on each new workstation with that workstation's remote and local audit file systems.
To Allocate and Deallocate Devices
The Device Manager allocates and deallocates devices.
-
In the role and in a workspace at the label required, click the left mouse button on the triangle above the Style Manager icon on the Front Panel.
The Trusted Desktop subpanel is displayed.
-
Click the Device Manager icon once.
-
Double-click the device to be allocated.
mag_tape_0 allocates a tape device. floppy_0 allocates a diskette.
-
Click OK in the label builder that appears.
The file you load will be labeled
admin_low. -
Follow the directions in the window that is displayed.
To Deallocate a Device
-
Go to the workspace where the Device Manager was allocated.
-
Double-click the device to deallocate itis .
A window appears listing devices being deallocated.
-
When prompted, remove the tape or diskette from the drive and label it appropriately.
-
Press the Return key to dismiss the window.
-
Click the top left button and select Close to close the Device Allocation Manager window.
Advanced Audit Setup Procedures
The following procedures describe how to modify the default audit classes and audit events, and to set a public object bit on files and folders to reduce unnecessary auditing.
To Add Audit Classes
-
As role secadmin, at label
admin_low, add audit classes in the audit_classes file. -
Add the classes you planned in "Planning a Site-Specific Event-to-Class Mapping", write the file, and exit the editor.
 Caution -
Caution - Do not reassign the hexadecimal numbers already in use.
-
As role secadmin, at label
admin_low, open the Audit Events action to add the new class to each event in the new class.For events in more than one class, use a comma (no space) to delimit the classes.
-
Write the file and exit the editor.
-
Make any changes to audit_control(4) and audit_user(4) to audit the events in the new classes.
See "To Set Audit Flags" and "To Set User Exceptions to the Audit Flags" for details of the procedures.
Note -On a distributed system, the audit_class, audit_event, audit_startup, and audit_user files must be identical on every workstation on the network. See "To Distribute Audit Configuration Files to a Network of Workstations" for a process to distribute master copies of files to all workstations on the network.
-
Reboot, or as secadmin in an
admin_lowprofile shell, run the auditconfig(1M) command with appropriate options.In the following example, the audit session ID is 159, and the new classes are gr(for graphic applications) and db (for databases applications).
$ auditconfig -setsmask 159 gr,db
To Add Audit Events
-
As role secadmin, at label
admin_low, add audit events in the audit_event(4) file. -
Add the events you planned in "Planning a Site-Specific Event-to-Class Mapping", write the file, and exit the editor.
For events in more than one class, use a comma (no space) to delimit the classes.
Note -Third-party applications can use the event numbers 32768 through 65536 only. See Table 1-1 for more information.
-
Make any changes to audit_control(4) and audit_user(4) to audit the events in the new classes.
See "To Set Audit Flags" and "To Set User Exceptions to the Audit Flags" for details of the procedures.
Note -On a distributed system, the audit_class, audit_event, audit_startup, and audit_user files must be identical on every workstation on the network. See "To Distribute Audit Configuration Files to a Network of Workstations" for a process to distribute master copies of files to all workstations on the network.
-
Reboot, or as secadmin in an
admin_lowprofile shell, run the auditconfig(1M) command with appropriate options.In the following example, the audit session ID is 159, and the new events are in the classes gr (for graphic applications) and db (for databases applications).
$ auditconfig -setsmask 159 gr,db
To Change Event-Class Mappings
-
Change event-class mappings in the audit_control(4) file.
-
Edit the file to change the class mapping for each event to be changed, write the file, and exit the editor.
If you are changing events above number 2048, this is all you need to do.
Note -On a distributed system, the audit_class, audit_event, audit_startup, and audit_user files must be identical on every workstation on the network. See "To Distribute Audit Configuration Files to a Network of Workstations" for a process to distribute master copies of files to all workstations on the network.
-
If you modify a kernel event mapping (numbers 1 to 2047):
To Set Public Object Bit on Publicly Accessible Files
Setting the public object bit can reduce the size of the audit trail when the audit record includes successful accesses of files or directories. Successful viewing, listing, or listing of a file or directory's attributes will not be written to the audit record when the file's public object bit is set.
As role secadmin, at label admin_low, set the public object bit on a local directory of publicly accessible files using the setfattrflag(1) command with the -p 1 option.
The following command sets the public object bit on the /etc directory. A search of the /etc directory, or a read of files in the /etc directory will not result in an audit record.
$ setfattrflag -p 1 /etc
$ getfattrflag /etc
Multilevel directory: no
Single level directory: no
Public object: yes
|
As secadmin, at label admin_low, set the public object bit on a mounted file system of publicly accessible files using the attr_flag security attribute.
For example, the following entry in the vfstab_adjunct(4) file for the mounted file system /spublic sets the public object flag for all files in the file system.
# Modified template. # /spublic; \ acc_acl=; \ mode=; \ attr_flag=public; \ gid=; \ uid=; \ slabel=; \ forced=; \ allowed=; \ low_range=; \ hi_range=; \ mld_prefix=mldroot; #
See the man page for mount(1M) and "Managing Files and File Systems" in the Trusted Solaris Administrator's Procedures for more details.
Dynamic Procedures
Dynamic controls apply to one workstation at a time, since the audit command only applies to the current workstation where you are logged in. Use dynamic controls to test auditing on a workstation (estimate volume of records, for example), or to add an auditing flag without having to reboot the workstation. However, if you make dynamic changes on one workstation for other than testing purposes, you should make the changes on all workstations.
Note -
The following procedures work only when auditing is enabled.
To Determine Current Audit Policy
The auditconfig(1M) command enables an appropriately configured role to determine
audit policy and to see what policies can be set. If your role is not configured to determine the policy, or if auditing is turned off, the command auditconfig -getpolicy returns an error. The following example was
run by the role secadmin, at label admin_low:
$ auditconfig -getpolicy audit policies = none $ auditconfig -lspolicy policy string description: arge include exec environment args in audit recs argv include exec args in audit recs cnt when no more space, drop recs and keep a count group include supplementary groups in audit recs seq include a sequence number in audit recs trail include trailer tokens in audit recs path allow multiple paths per event acl include ACL information in audit recs ahlt halt machine if we can't record an async event slabel include sensitivity labels in audit recs passwd include cleartext passwords in audit recs windata_down include downgraded information in audit recs windata_up include upgraded information in audit recs all all policies none no policies |
To Create an Admin_High Workspace
To label files admin_high or to move them to an admin_high directory, to reset the audit daemon, and to make other changes in auditing requires an admin_high process. An admin_high process starts from an admin_high workspace.
-
Click the right button on the Front Panel and choose Assume secadmin Role from the menu.
A secadmin role workspace becomes the current workspace.
-
In the current workspace, click the right button on the workspace name (secadmin) button and choose Change Workspace SL from the menu.
-
In the label builder, click the ADMIN_HIGH button.
-
Click OK at the bottom of the label builder.
The color of the workspace button turns to black, indicating an
admin_highworkspace. Anadmin_highworkspace is available only to an administrative role.
To Set Audit Policy Temporarily
The auditconfig command enables you to change audit policy, such as whether to include acl information in the audit record. Since the policy variable is a dynamic kernel variable, the policy that you set is in effect until the workstation next boots. See the auditconfig(1M) man page for a list of policy parameters.
To set policies in one invocation of the command, or to override all current policies, as role secadmin at label admin_low,
separate the policies with commas (no spaces):
$ auditconfig -setpolicy trail,seq $ auditconfig -getpolicy audit policies = trail,seq $ auditconfig -setpolicy argv,acl $ auditconfig -getpolicy audit policies = argv,acl |
To add policies to the current policies, as role secadmin at label admin_low, preface each added policy with a plus (+):
$ auditconfig -setpolicy trail,seq $ auditconfig -getpolicy audit policies = trail,seq $ auditconfig -setpolicy +argv $ auditconfig -setpolicy +acl $ auditconfig -getpolicy audit policies = seq,trail,argv,acl |
To remove policies from the current policies, as role secadmin at label admin_low, preface each policy to be removed with
a minus (-):
$ auditconfig -setpolicy trail,seq $ auditconfig -getpolicy audit policies = trail,seq $ auditconfig -setpolicy -seq $ auditconfig -getpolicy audit policies = trail |
In the examples above, the trail and seq tokens are added to debug audit trail discrepancies. To set policies permanently, enter the auditconfig command in the audit_startup(1M) script. See "To Set Audit Policy Permanently" for how to edit the script.
To run auditing in an evaluated configuration, the cnt policy cannot be turned on; the ahlt policy (the default) cannot be turned off.
To Change Audit Flags Dynamically
The auditconfig(1M) command enables you to change audit flags dynamically, such as adding extra flags to a user, a session, or a process while the user, session, or process is active. Since the flags are added dynamically, they are in effect until the user logs out, the session ends, or the process ends.
To set a particular user to be additionally audited for successful file reads, as role secadmin at label admin_low:
$ auditconfig -setumask audit_user_id +fr |
To set a particular session to be additionally audited for failed file attribute access, as role secadmin at label admin_low:
$ auditconfig -setsmask audit_session_id -fa |
To set a particular process to be additionally audited for successful and unsuccessful file attribute modifications, as role secadmin at label admin_low:
$ ps -ef | grep application-to-be-monitored $ auditconfig -setpmask process_id fm |
To Stop the Audit Daemon
Only one audit daemon may run at a time. An attempt to start a second one will result in an error message, and the new one will exit. If there is a problem with the audit daemon, terminate the audit daemon gracefully, then restart it manually.
To stop the audit daemon in event of trouble, as role secadmin, at label admin_high:
$ audit -t |
This is not recommended. Audit records may be lost.
To Start the Audit Daemon
The audit daemon starts when the workstation is brought up to multiuser mode, and restarts when the audit daemon is instructed by the audit -s command to reread an audit configuration file.
To restart the audit daemon in event of trouble or a change to an audit configuration file, as role secadmin, at label admin_high:
$ audit -s |
The pointer may be reset to the beginning of the list of audit directories when the administrator enters the audit -s command.
To Send Audit Records to a New Audit File
- © 2010, Oracle Corporation and/or its affiliates
