Introduction to Trusted Solaris Administration
Administration in the Trusted Solaris operating environment uses many of the same tools available in the Solaris operating environment and offers security-enhanced tools as well. The difference between the environments lies in how administration tools are accessed and how this access is restricted.
Accessing Tools in a Role Workspace
To use the Trusted Solaris administration tools, you must be in a role account with the assigned rights profiles that contain the desired trusted applications.The following procedure describes how to access a role workspace.
To Access a Role Workspace
-
Log in as a normal user.
-
Assume a role using the Trusted Path menu. If a role workspace already exists, click the role workspace button in the Front Panel.
-
Supply the role password.
Note that the default label for a role workspace is the role's minimum label, usually
ADMIN_LOW. If desired, you can switch labels by choosing Change Workspace Label from the Trusted Path menu while the pointer is over the role workspace button.
To leave a role workspace temporarily, click any other workspace button. To destroy the workspace, choose Delete from the Trusted Path menu while the pointer is over the role workspace button.
Within the role workspace, you can access four types of trusted applications:
-
Solaris Management Console tools - The Solaris Management Console (SMC) serves as a launcher for various administration tools and is available from: the Application Manager, the Tools subpanel in the Front Panel, or the command line by typing smc.
-
Commands - In the Trusted Solaris environment, administrative commands and other commands intended for restricted use are assigned to rights profiles. Opening a terminal in a role workspace launches a profile shell that gives you access to all commands assigned to the account's rights profiles. Any commands that you run are at the label of the current workspace.
-
CDE actions - The System_Admin folder in Application Manager provides actions for performing miscellaneous system administration tasks. Most of these actions apply a special version of the vi editor, adminvi(1M) to one of the configuration files. You can use the
dtpadeditor if you prefer. See "Changing the Default Admin Editor" for details.For security purposes, the editing actions cannot save a file to a different name, create a new file, or escape to a shell. All actions conform with mandatory access control and the local security policy. Any actions you launch are at the label of the current workspace, unless overridden by a rights profile.
-
Enhanced desktop tools - The Trusted Solaris operating environment provides desktop tools for administrators from the Front Panel. These tools have capabilities not available to normal users. For example, administrators can use the File Manager to set privileges and labels on executable files. Similarly, the Device Allocation Manager makes device administration capabalities available to roles. See "Understanding Device Allocation".
Remote Administration
You can perform remote administration in the Trusted Solaris operating environment using the Solaris Management Console. You can also log into a remote host from another Trusted Solaris host in the system. Depending on your site's security policy, you can make adjustments to log in from a non-Trusted Solaris system, although this will make your system somewhat less secure. See "Administering Remote Systems" under "Administering Systems in an Administrative Role" in Trusted Solaris Administrator's Procedures.
Solaris Management Console Tools
The Solaris Management Console (SMC) provides access to families of GUI-based administration tools. These tools enable you to edit items in various configuration databases.
SMC Toolboxes
The SMC tools are stored in sets referred to as toolboxes. For the security-related tools in the Trusted Solaris environment, you need to open the Trusted Solaris Management Console toolbox. Within the Trusted Solaris toolbox, you can access tools according to scope, that is, the name service for the administration files accessed by the tools: local host, NIS, or NIS+.
Organization of the Solaris Management Console
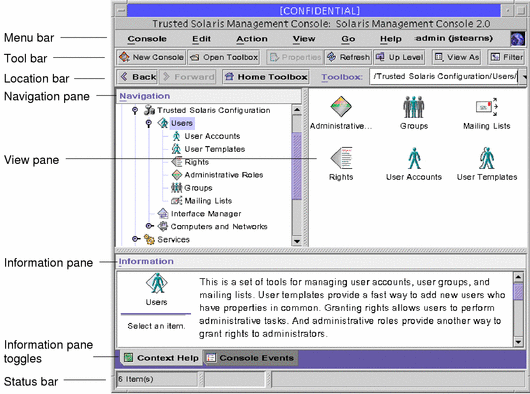
The SMC is shown in the following figure, with the Trusted Solaris toolbox loaded and the Users tool open.
Figure 2-1 Typical Trusted Solaris SMC
SMC Documentation
The main source of documentation for using the SMC and its tools is the online help system. There are two forms of online help: context-sensitive help and expanded help topics. The context-sensitive help is tied to the currently selected feature and is displayed in the information pane. The expanded help topics are available from the Help menu or by clicking cross reference links in the context-sensitive help. The help topics appear in a separate viewer.
Trusted CDE Actions
This section presents the CDE actions available to roles and describes how to use or change the restricted editor used in these actions.
To Access Trusted CDE Actions
-
Right-click the background to bring up the Workspace Menu.
-
Press Applications, then click Application Manager.
-
In the Application Manager, double-click the System_Admin icon.
The CDE action icons display in the Application Manager window.
-
Invoke the desired action by double-clicking its icon.
A window or dialog box for the appropriate action appears.
The trusted CDE actions are listed in the following table.
Table 2-1 Administrative Actions, Purposes, and Default Roles| Action Name | Purpose of Action | Default Rights Profile |
|---|---|---|
|
Creates devices by putting entries in device_allocate(4), and device_maps(4). See add_allocatable(1M). |
Device Security |
|
|
Edits any specified file |
Object Access Management |
|
|
Edits audit_class(4) |
Audit Control |
|
|
Edits audit_control(4) |
Audit Control |
|
|
Edits audit_event(4) |
Audit Control |
|
|
Edits the audit_startup.sh script. See audit_startup(1M). |
Audit Control |
|
|
Runs chk_encodings(1M) on specified encodings file |
Object Label Management |
|
|
Runs tnchkdb(1M) on local tnidb(4), tnrhdb(4), and tnrhtp(4) files |
Network Security |
|
| Check TN NIS+ Tables |
Runs tnchkdb(1M) on tnrhdb(4), and tnrhtp(4) NIS+ trusted network maps | Network Management |
|
Edits /usr/dt/config/sel_config. See sel_config(4). |
Object Label Management |
|
|
Runs ypinit(1M), using both the specified hostname for the NIS master and the specified domain name |
Name Server Security |
|
|
Runs nisclient(1M), using both the specified hostname for the NIS+ master and the specified domain name |
Name Server Security |
|
|
Runs ypinit(1M) using the specified domain name |
Name Server Security |
|
|
Runs nisserver(1M) using the specified domain name |
Name Server Security |
|
|
Edits specified label_encodings(4) file and runs chk_encodings(1M) |
Object Label Management |
|
|
Edits nsswitch.conf(4) |
Network Management |
|
|
Runs nispopulate(1M) from the specified directory |
Name Service Security |
|
|
Network Management |
||
|
Edits /etc/defaultrouter. See route(1M). |
Network Management |
|
|
Edits resolv.conf(4) |
Network Management |
|
|
Edits /etc/mail/sendmail.cf. See sendmail(1M). |
Mail Management |
|
|
Edits vfstab_adjunct(4) |
File System Security |
|
|
Edits vfstab(4) |
File System Management |
|
|
Edits tsolgateways(4) |
Network Management |
|
|
File System Management |
||
|
Runs niscat(1) with the -o option on the specified NIS+ trusted network database to display the table's attributes. |
Name Service Management |
|
|
Runs niscat(1) on the specified NIS+ trusted network database to display the table's contents. |
Name Service Management |
Admin Editor
The Admin Editor action, which can also be accessed from the command adminvi(1M), is a modified version of the vi(1) command. It restricts the user from executing shell commands and from writing to (saving to) any file other than the original file being edited. The Admin Editor action, which is assigned to the security administrator role by default, should be used in most cases instead of adminvi on the command line to edit or create administrative files. This is due to the fact that the Admin Editor is a wrapper for adminvi that incorporates auditing and allows an editor preference. You can assign the adminvi command to any users with the profile shell as their default if you need to provide them a text editor with the restrictions of adminvi.
Changing the Default Admin Editor
The Admin Editor is launched through the /usr/dt/bin/trusted_edit shell script, which brings up the editor specified in the EDITOR environment variable for the role account, restricts saves, and audits any changes made at the time the file is saved. The variable is set to adminvi(1M) by default, but the security administrator role can redefine the EDITOR variable to /usr/dt/bin/dtpad. When adminvi is specified, /bin/adminvi is invoked as root to edit the file. The adminvi command prevents the saving of the file with any other name. If dtpad(1) is specified, the New, Save, and Open options in the File menu are disabled when the action runs so that the file cannot be renamed.
- © 2010, Oracle Corporation and/or its affiliates
