Specifying Security Attributes on Files and File Systems
Security attributes can be specified at the level of an individual file or directory, or at the level of the file system.
If a needed attribute is not obtained elsewhere, a set of defaults is used. For rules about how attributes are obtained, see "Trusted Solaris Attribute Precedence Rules".
Security Attributes on Files and Directories
The following attributes are present on objects in Solaris and Trusted Solaris file systems: User Id, Group Id, Permission Mode, and Access ACL (optional). Trusted Solaris files and directories have additional security attributes. The following table describes the extended security attributes provided in Trusted Solaris software.
Table 9-1 Trusted Solaris File and Directory Attributes| Extended Attributes | Description of Extended Trusted Solaris Attributes |
|---|---|
| Label | The label of the file or directory. |
| Forced Privileges | Optional. The set of privileges that an executable file is guaranteed to have available at start of execution. Must be a subset of the allowed privileges. |
| Allowed Privileges | Optional. The maximum set of privileges that an executable file is allowed to use during its execution. (Editing executable files causes them to lose all their privileges. Therefore, limiting the privileges that an executable can use to those in its allowed set provides a protection against Trojan Horses, since programs cannot use inheritable privileges if the programs have been edited.) Must be a superset of the forced privileges. |
| File Attribute Flag |
Optional. The only supported file attribute flag is |
| Directory Attribute Flag | Optional. Flag indicating that a directory is an MLD |
Specifying Security Attributes on Files and Directories
The Trusted Solaris File Manager enables users and administrators to change permissions on files and directories. It also enables authorized users and administrators to set privileges and labels on files and directories. Authorizations are required to change privileges and labels. Additional authorizations are required when the change is outside DAC or MAC policy.
Changing Labels and Privileges
The File Manager Selected menu has a Change Labels option to set the label. A user or role that has the setlabel(1) command in one of its profiles can also change labels. The File Manager Selected menu also has a Change Privileges option to set forced and allowed privileges on executable files. Changing forced and allowed privileges can also be done on the command line by any account that has the setfpriv(1) command in one of its profiles.
The following authorizations are required in order to set privileges and labels through the File Manager Selected menu options:
-
Setting privileges requires the Set File Privileges authorization.
-
Upgrading file and directory labels requires the Upgrade File Label authorization.
-
Downgrading file and directory labels requires the Downgrade File Label authorization.
The following figure shows the File Manager Selected menu when the account has the required authorizations. See "To Change Labels and Privileges With the File Manager" for how to change labels and privileges.
Figure 9-1 File Manager Selected Menu for an Authorized User
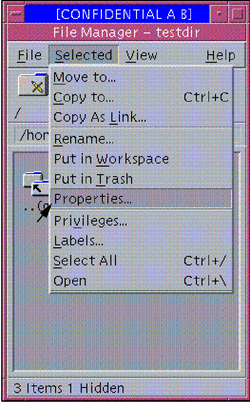
Changing File and Directory Attribute Flags
The getfattrflag(1) command gets the security attribute flags of a file or directory and the setfattrflag(1) command sets the public object flag on a file and sets the MLD flag on a directory.
Security Attributes on File Systems
File systems supported by Trusted Solaris software are characterized by whether their attributes can be changed or not. When the attributes can be changed, they are called variable attribute or variable file systems. File systems that do not support Trusted Solaris extended security attributes are called fixed because any attributes assigned to them (either at mount time or by default) cannot be altered.
Following are more details relevant for understanding and managing the various types of variable and fixed file system types:
-
All
ufs-type file systems are variable and therefore, all file systems installed with the Trusted Solaris software are variable.For example, if you connect a hard disk containing an unlabeled file system directly to a Trusted Solaris computer, when the file system is ufs-mounted the unlabeled file system becomes a variable file system, with a default set of attributes shown in Table 9-2.
-
An
nfs-type file system mounted from a Trusted Solaris or TSIX NFS server is variable. -
An
nfs-type file system mounted from an NFS server running another operating environment is fixed. -
tmpfsfile systems are variable. -
These file system types are always fixed:
fdfs,hsfs,pcfs. -
The
lofs-type file system's attributes are those of the underlying file system. See "Mounting File Systems in the Trusted Solaris Environment" for more information.
The following table shows the security attributes for variable-attribute file systems, with the default values that are used when none are specified.
Table 9-2 Variable File System Security Attributes with Defined Settings|
Attribute |
Description |
Defaults |
|---|---|---|
|
MLD prefix |
The characters to use for the MLD prefix for MLDs on this file system |
.MLD. |
|
Label Range |
The minimum and maximum sensitivity level for files and directories created on this file system |
ADMIN_LOW to ADMIN_HIGH |
|
Label |
Label to infer for all files and directories on this file system that do not have an explicit label |
None. NOTE: Files and directories in a fixed file system are assigned a default label when they are UFS-mounted, if the administrator has not assigned one. |
|
Forced Privilege Set |
Set of forced privileges to infer for all executable files on this file system that do not have explicit forced privileges |
None. |
|
Allowed Privilege Set |
Set of allowed privileges to infer for all executable files on this file system that do not have explicit allowed privileges |
None. |
The Label Attribute
In variable file systems the label of each object is set when it is created and can be changed by an authorized user. In fixed file systems, a single label is assigned when the file system is mounted. The label can be changed only if an object is moved from the fixed file system. Because they are configured to have a single label when mounted on Trusted Solaris hosts, fixed attribute file systems are also referred to as single-label file systems.
The label is obtained differently when a fixed-attribute file system is NFS-mounted than when it is PCFS-mounted from a floppy disk or HSFS-mounted from a CDROM.
-
An NFS-mounted file system is assigned the label that is specified in the Default Label setting in the Security Families template assigned to the remote computer from which the file system is NFS-mounted.
-
For a PCFS- or HSFS-mounted fixed-attribute file system, the label is specified at mount time. either on the mount command line or in an entry in the vfstab_adjunct(4) file.
Specifying Security Attributes on Variable File Systems
(See "To Set Security Attributes on a File System ". The Security Administrator role uses the getfsattr(1M) command to get the security attributes of a file system. The setfsattr(1M) command tunes the attributes set on an already-existing file system ).
Do not change or explicitly set the security attributes of the /, /usr, or /var file systems on a Trusted Solaris host. The results are unpredictable.
Specifying Security Attributes on Fixed File Systems
When mounting a fixed-attribute file system, the Security Administrator role can specify security attributes on the command line with the mount(1M) command, in the vfstab_adjunct(4) file, or in the /etc/auto_master file other autofs maps (see automount(1M)).
Note -
In the mount command, most of the keyword=value pairs used to specify security attributes with the -S can be specified with the -o option. If a keyword is followed by multiple values separated by commas, the keyword must be specified with the-S option becauses comma-separated values are not allowed after -o. Use of the -o option is preferable. For more about the security-related mount options that can be specified with the -o option, see "Mount Options Used for Protection ".
Any attributes specified at mount time are applied to all the files and directories in the mounted file system, if the files or directories themselves do not have the attribute. Any attributes on the file or directory are used. If the file or directory does not have an attribute and none is specified at mount-time, the defaults shown in Table 9-3 apply.
In fixed attribute file systems, the security attributes cannot change on an object as long as the object resides in the file system.
If, for example, the mounted file system /spare contains a file called test, no one can change the label of /spare/test. However, if /spare/test is copied into another directory such as /tmp or /export/home/secadmin, its label can be changed.
The following table shows the attributes that can be specified for a fixed attribute file system when the file system does not support the attribute, and the default vales that apply if no value for the attribute is supplied.
Table 9-3 Attributes Assignable to Fixed File Systems|
Attribute |
-S or -o Option Keyword to Use When Mounting |
Default Values |
|---|---|---|
|
MLD prefix |
mld_prefix |
.MLD. |
|
Label Range |
low_range, high_range |
|
|
Label |
slabel= |
Mounted from a CD-ROM or floppy disk - the label of the mounting process Mounted from an NFS server - the default label of the server in the tnrhdb database |
|
Forced Privilege Set |
forced= |
None |
|
Allowed Privilege Set |
allowed= |
None |
The following example shows a command line to NFS-mount a fixed attribute file system called /spare from an NFS server running the Solaris operating environment. The server is called outside. /spare is mounted with a label of INTERNAL_USE_ONLY using mount with the -S option on the command line as shown here:
$ mount -F nfs -S "slabel=INTERNAL_USE_ONLY" outside:/spare /spare |
- © 2010, Oracle Corporation and/or its affiliates
