Chapter5 Desktop Components - Linux
To access the configuration data from the Configuration Manager, a desktop client requires the Sun JavaTM Desktop System Configuration Agent. The Configuration Agent communicates with the remote configuration data repository and the adapters as well as integrates data into specific configuration systems. The configuration systems that are currently supported are GConf, Mozilla Preferences, and StarOffice Registry.
All of these components are shipped and installed as part of the Java Desktop System.
Data Access/User Authentication
The Configuration Agent retrieves information from the LDAP server based on the login ID of a desktop user. The User/UniqueIdAttribute setting of the organizational mapping file maps the login ID to a user entity in the LDAP server. The Configuration Agent also retrieves information about the host, such as the name or the IP address of the host. This information is mapped to a host entity in the LDAP server through the Host/UniqueIdAttribute setting of the organizational mapping file.
There are two methods to access the LDAP server, namely anonymously or with GSSAPI. For anonymous access, no action is required on the desktop. For the GSSAPI method, Kerberos credentials must be acquired on the desktop. To integrate Kerberos credential acquisition with the user login, the pam_krb5() module must be installed and configured on the Java Desktop System host. You can find example configurations for the pam() module in the /usr/share/doc/packages/pam_krb5/README.SuSE directory on the Java Desktop System CD. You can also use gdm to integrate Kerberos with the user login, for example, by using the following /etc/pam.d/gdm file:
#%PAM-1.0 auth required pam_unix2.so nullok #set_secrpc auth optional pam_krb5.so use_first_pass missing_keytab_ok ccache=SAFE putenv_direct account required pam_unix2.so password required pam_unix2.so #strict=false session required pam_unix2.so # trace or none session required pam_devperm.so session optional pam_console.so |
Configuration Agent
The Configuration Agent is part of the apoc package. When you install the corresponding RPM, the files that are required for this API are installed and registered with inetd. You can install the RPM manually or through the Java Desktop System installation.
Bootstrap Information
To access the remote configuration data, the Configuration Agent must be provided with the location of the LDAP server. You can add this location through the YaST2 configuration tool, autoYaST, or by manually editing the policymgr.properties properties file in the /opt/apoc/lib directory. In YaST2, you can add this data in the Network/Advanced section.
Figure 51 Java Desktop System Configuration Agent in YaST
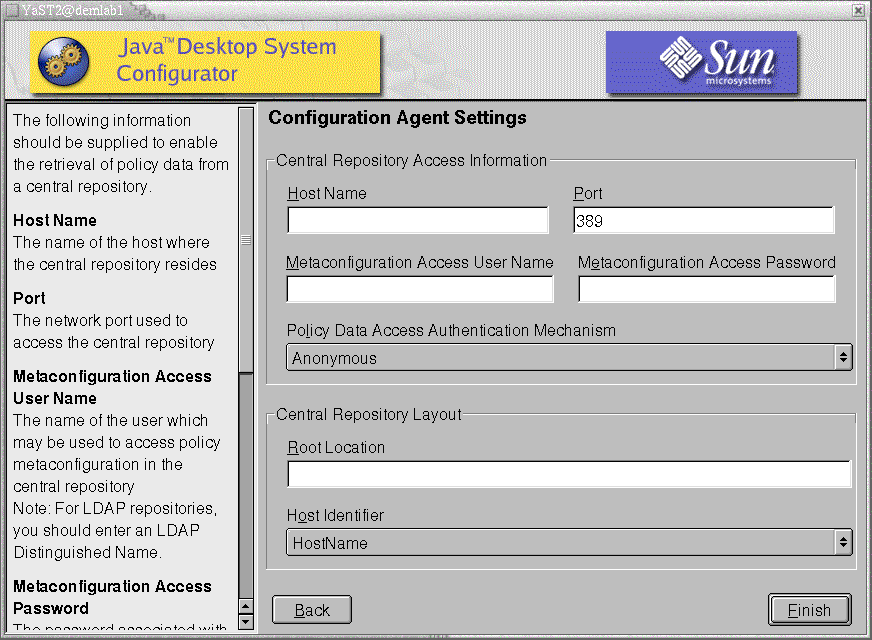
The following information is required to run the Configuration Agent:
Note
Associated property file keys are indicated in parentheses, where appropriate.
-
Host Name (Server): host name of the LDAP server.
-
Port (Port): port number of the LDAP server.
-
Metaconfiguration Access User Name (AuthDn): full DN of a user with read and search access rights on the repository.
NoteIf anonymous access is enabled in the directory, this setting can be left blank.
-
Metaconfigurator Access Password (Password): password of a registered LDAP user.
NoteIf anonymous access is enabled in the directory, this setting can be left blank.
-
Policy Data Access Authentication Mechanism (AuthType): can be anonymous or GSSAPI, depending on how the LDAP server authenticates users.
-
Root Location (BaseDn): base DN of the LDAP repository.
-
Host Identifier (HostIdentifier): can be HostName or IPAddress and must be set to match the contents of the LDAP attribute that is used to identify hosts. This attribute is defined in the mapping files as Host/UniqueIdAttribute.
-
Connect Timeout (Connect Timeout): this indicates the number of seconds, after which attempts to connect to the LDAP server will time out. The default value is 1 second.
Note
Whenever you change the bootstrap and operational settings, the Configuration Agent must be restarted.
To restart the Configuration Agent on the Desktop, ensure that none of the related client applications are running, log in as root, and type the command /opt/apoc/bin/apocd restart.
Operational Settings
You can configure the operational settings of the Configuration Agent locally or remotely. To configure the settings locally, edit the apocd.properties file in the /opt/apoc/lib directory. To configure the settings remotely, use the Configuration Agent policy in the Configuration Manager. The following settings can be configured in the properties file:
-
DaemonPort: port where the Configuration Agent listens for communication from its clients on the desktop
-
MaxClientThreads: maximum number of client requests that can be simultaneously processed
-
MaxClientConnections: maximum number of client connections
-
MaxRequestSize: maximum size of client requests
-
DaemonChangeDetectionInterval: interval in minutes between the change detection cycles for this list of configuration settings
-
ChangeDetectionInterval: interval in minutes between the change detection cycles for the client configuration data
-
GarbageCollectionInterval: interval in minutes between the garbage collection cycles in the local configuration database
-
TimeToLive: interval in minutes that non-offline configuration data remains in the local database
-
LogLevel: level of detail in the agent log files
The DaemonPort setting can only be modified locally and requires a restart of the agent for the changes to take effect. All other settings take effect at the next change detection cycle for the agent configuration. The logging level that is specified in LogLevel must be a value that is consistent with the Java Logger levels. In order of decreasing severity, these levels are: SEVERE, WARNING, INFO, CONFIG, FINE, FINER and FINEST.
Propagating Configuration Data Changes
You can use the ChangeDetectionInterval setting that is described in Operational Settings to tune the propagation of remote configuration data changes to client side applications. The value that you provide for this setting is the maximum length of time in minutes that elapses before changes that are made remotely are reflected in the client applications. Smaller values for the ChangeDetectionInterval result in increased Configuration Agent and LDAP server activity. As a result, use caution when you adjust the value of the setting. For example, in an initial deployment phase, you can set this value to one minute so that you can easily test the impact of remote configuration on client applications. After you complete the testing, return this setting to the initial value.
Configuration Agent Port Information
The Configuration Agent uses two ports:
-
The daemon port (default is 38900), which is used by the daemon to communicate with client applications.
-
The daemon admin port (default is 38901), which is used by the daemon controller program, apocdct1, when communicating with the daemon.
Changing the daemon port:
To change the daemon port, you must modify the DaemonPort property in the daemon's apocd.properties file and the apocd entries in /etc/services and /etc/inetd.conf. Afterward, restart the daemon and reload inetd.
Changing the daemon admin port:
To change the daemon admin port, you must modify the DaemonAdminPort property in the daemon's apocd.properties file. Afterward, restart the daemon.
GConf Adapter
The GConf adapter is part of the apoc-adapter-gconf package. When you install the adapter from the corresponding RPM, the GConf data sources path in /etc/gconf/2/path is updated to include the Configuration Manager sources. A backup of the old path is stored in /etc/gconf/2/path.apocBackup. If the old path refers to custom data sources, you will need to update the path by merging the changes from the default path to the newly installed Manager path. The two data sources that are provided by the adapter are:
-
"apoc:readonly:": provides access to non-protected settings from the policies. Insert this data source after the user settings and before the local defaults.
-
"apoc:readonly:mandatory@": provides access to protected settings from the policies. Insert this data source after the local mandatory settings and before the user settings.
Mozilla Adapter
The Mozilla adapter is part of the mozilla-apoc-integration package. When you install the adapter from the corresponding RPM, the required files are added to an existing installation of Mozilla and are automatically registered.
StarOffice Adapter
The StarOffice adapter is included in a standard StarOffice installation and allows you to access the policy configuration data without any special modifications.
- © 2010, Oracle Corporation and/or its affiliates
