Compliance Violation Remediation and Mitigation
This section describes how to use Waveset Remediation to protect your critical assets.
The following topics discuss elements of the Waveset Remediation process:
About Remediation
When Waveset detects an unresolved (not mitigated) audit policy compliance violation, it creates a remediation request, which must be addressed by a remediator A remediator is a designated user who is allowed to evaluate and respond to audit policy violations.
Remediator Escalation
Waveset allows you to define three levels of remediator escalation. Remediation requests are initially sent to Level 1 remediators. If a Level 1 remediator does not act on a remediation request before the timeout period expires, Waveset escalates the violation to the Level 2 remediators and begins a new timeout period. If a Level 2 remediator does not respond before the timeout period expires, then the request is escalated once again to the Level 3 remediator.
To perform remediation, you must designate at least one remediator for your enterprise. Specifying more than one remediator for each level is optional, but recommended. Multiple remediators help ensure workflow is not delayed or halted.
These authorization options are for work items of authType RemediationWorkItem.
-
The remediation work item owner
-
A direct or indirect manager of the remediation work item owner
-
An administrator who controls an organization in which the remediation work item owner belongs
By default, the behavior for authorization checks is one of the following:
-
Owner is the user attempting the action
-
Owner is in an organization controlled by the user attempting the action
-
Owner is a subordinate of the user attempting the action
The second and third checks are independently configurable by modifying these options:
-
controlOrg. Valid values are true or false.
-
subordinate. Valid values are true or false.
-
lastLevel. The last subordinate level to include in the result; -1 means all levels. The integer value for lastLevel defaults to -1, meaning direct and indirect subordinates.
These options can be added or modified in the following:
UserForm: Remediation List
Remediation Workflow Process
Waveset provides the Standard Remediation Workflow to provide remediation processing for Audit Policy scans.
The Standard Remediation Workflow generates a remediation request (a review-type work item) containing information about the compliance violation and sends an email notification to each Level 1 remediator named in the audit policy. When a remediator mitigates the violation, the workflow changes the state of, and assigns an expiration to, the existing compliance violation object.
A compliance violation is uniquely identified by the combination of the user, policy name, and rule name. When an audit policy evaluates to true, a new compliance violation is created for each user/policy/rule combination, if an existing violation for this combination does not already exist. If a violation does exist for the combination, and the violation is in a mitigated state, then the workflow process takes no action. If the existing violation is not mitigated, then its recurrent count is incremented.
For more information about remediation workflows, see About Audit Policies.
Remediation Responses
By default, three response options are given to each remediator:
-
Remediate. A remediator indicates that something has been done to fix the problem on the resource.
When a compliance violation is modified, Waveset creates an audit event to log the remediation. In addition, Waveset stores the name of the remediator and any comments provided.
Note –After remediation, a violation is not deleted until the next audit scan. If an audit policy is configured to allow re-scans, then the user will be re-scanned as soon as the violation is remediated.
-
Mitigate. A remediator allows the violation and gives the user an exemption from the violation for a certain amount of time.
If the violation is deliberate (for example, there is a business case for belonging to two groups), you can mitigate the violation for an extended period of time. You can also mitigate the violation for a short period of time (for example, in cases where the resource’s system administrator is on vacation and you do not know how to fix the problem).
Waveset stores the name of the remediator that mitigated the violation along with the expiration date assigned to the exemption and any comments provided.
Note –When Waveset detects an expired exemption, it returns the violation from the mitigated state to a pending state.
-
Forward. A remediator reassigns the responsibility for resolving the violation to another individual.
As an example of remediation, suppose your enterprise establishes a rule in which a user cannot be responsible for both Accounts Payable and Accounts Receivable, and you receive notice that a user is violating this rule.
-
If the user is a supervisor who has responsibility for both roles until the company hires a second person for that position, you might mitigate the violation and issue an exemption for up to six months.
-
If the user is violating the rule, you might ask your Oracle ERP Administrator to correct the conflict, and then remediate the violation when the problem is fixed for that resource. Alternatively, you might forward the remediation request to the Oracle ERP Administrator.
Remediation Email Template
Waveset provides a Policy Violation Notice email template (available by selecting the Configuration tab, then the Email Templates subtab. You can configure this template to notify remediators of pending violations. For more information, see Customizing Email Templates in Chapter 4, Configuring Business Administration Objects.
Working with the Remediations Page
Select Work Items -> Remediations to access the Remediations page.
You can use this page to:
-
View pending violations
-
Prioritize policy violations
-
Mitigate one or more policy violations
-
Remediate one or more policy violations
-
Forward one or more violations
-
Edit users from a remediation work item
Viewing Policy Violations
You can use the Remediations page to view details about violations before taking action on them.
Depending on your capabilities or place in the Waveset capabilities hierarchy, you may be able to view and take action on violations for other remediators.
The following topics are related to viewing violations:
Viewing Pending Requests
Pending requests assigned to you are, by default, displayed in the Remediation table.
You can use the List Remediations for option to view pending remediation requests for a different remediator:
-
Select My Direct Reports to view pending requests for users in your organization who report directly to you.
-
Select Search Users to enter or locate one or more users whose pending requests you want to view. Enter a user ID, and then click Apply to view pending requests for that user. Alternatively, click ... (More) to search for a user. After locating and selecting a user, click Dismiss to close the Search area.
The resulting table provides the following information about each request:
-
Remediator. Name of the assigned remediator. This column displays only when you view remediation requests for other remediators.
-
User. User for whom the request is made.
-
Audit Policy/Request. Action requested of the remediator.
-
Audit Rule/Description. Remediation comments for the request.
-
Violation State. Current state of the violation.
-
Severity. Severity assigned to the request (None, Low, Medium, High, or Critical).
-
Priority. Priority assigned to the request (None, Low, Medium, High, or Urgent).
-
Date of Request: Date and time the remediation request was issued.
Note –
Each user can choose a custom form that displays remediation data relevant to that particular remediator. To assign a custom form, select the Compliance tab on the user form.
Viewing Completed Requests
To view your completed remediation requests, click the My Work Items tab, and then click the History tab. A list of previously remediated work items displays.
The resulting table (which is generated by an AuditLog report) provides the following information about each remediation request:
-
Timestamp. Date and time the request was remediated
-
Subject. Name of the remediator who processed the request
-
Action. Whether the remediator mitigated or remediated the request
-
Type. ComplianceViolation or User Entitlement
-
Object Name. Name of the audit policy that was violated
-
Resource. Provides the remediator’s account ID (or may indicate N/A)
-
ID. Account ID related to the policy violation
-
Result. Always indicates Success
Clicking a timestamp in the table opens an Audit Events Details page.
The Audit Events Details page provides information about the completed request, including information about the remediation or mitigation, event parameters (if applicable), and auditable attributes.
Updating the Table
To update the information provided in the Remediations table, click Refresh. The Remediation page updates the table with any new remediation requests.
Prioritizing Policy Violations
You can prioritize policy violations by assigning them a priority, severity, or both. Prioritize violations from the Remediations page.
 To Edit the Priority or Severity for Violations
To Edit the Priority or Severity for Violations
-
Select one or more violations in the list.
-
Click Prioritize.
The Prioritize Policy Violations page appears.
-
Optionally set a severity for the violation. Selections are None, Low, Medium, High, or Critical.
-
Optionally set a priority for the violation. Selections are None, Low, Medium, High, or Urgent.
-
Click OK when you have finished making selections. Waveset returns to the list of remediations.
Note –Severity and priority values can be set only on remediations of type CV (Compliance Violation).
Mitigating Policy Violations
You can mitigate policy violations from the Remediations page.
-
Select rows in the table to specify which requests to mitigate.
-
Enable one or more individual options to specify requests to be mitigated.
-
Enable the option in the table header to mitigate all requests listed in the table.
Waveset allows you to enter only one set of comments to describe a mitigation action. You may not want to perform a bulk mitigation unless the violations are related and a single comment will suffice.
You can mitigate only those requests that include compliance violations. Other remediation requests cannot be mitigated.
-
-
Click Mitigate.
The Mitigate Policy Violation page (or Mitigate Multiple Policy Violations page) appears.
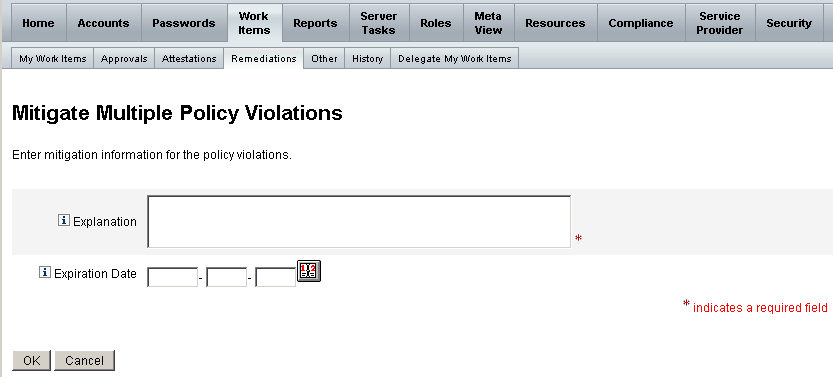
-
Enter comments about the mitigation into the Explanation field. (required)
Your comments provide an audit trail for this action, so be sure to enter complete and meaningful information. For example, explain why you are mitigating the policy violation, the date, and why you chose the exemption period.
-
Provide an expiration date for the exemption by typing the date (in the format YYYY-MM-DD) directly into the Expiration Date field, or by clicking the date button and selecting a date from the calendar.
Note –If you do not provide a date, the exemption is valid indefinitely.
-
Click OK to save your changes and return to the Remediations page.
To mitigate pending policy violations from the Remediations page:
Remediating Policy Violations
 To Remediate One or More Policy Violations
To Remediate One or More Policy Violations
-
Use the check boxes in the table to specify which requests to remediate.
-
Enable one or more individual check boxes in the table to specify requests to remediate.
-
Enable the check box in the table header to remediate all requests listed in the table.
If selecting more than one request, keep in mind that Waveset allows you to enter only one set of comments to describe a remediation action. You may not want to perform a bulk remediation unless the violations are related and a single comment will suffice.
-
-
Click Remediate.
-
The Remediate Policy Violation page (or Remediate Multiple Policy Violations page) displays.
-
Enter your comments about the remediation into the Comments field.
-
Click OK to save your changes and return to the Remediations page.
Note –Audit policies that are directly assigned to a user (who is assigned through a user account or an organization assignment) are always re-evaluated when a violation for that user is remediated.
Forwarding Remediation Requests
You can forward one or more remediation requests to another remediator.
 To Forward Remediation Requests
To Forward Remediation Requests
-
Use the check boxes in the table to specify which requests to forward.
-
Enable the check box in the table header to forward all requests listed in the table.
-
Enable individual check boxes in the table to forward one or more requests.
-
-
Click Forward.
The Select and Confirm Forwarding page appears.
Figure 15–3 Select and Confirm Forwarding Page

-
Enter a remediator name in the Forward to field, and then click OK. Alternatively, you can click ... (More) to search for a remediator name. Select a name from the search list, and then click Set to enter that name in the Forward to field. Click Dismiss to close the search area.
When the Remediations page reappears, the new remediator’s name displays in the Remediator column of the table.
Editing a User from a Remediation Work Item
From a remediation work item, you can (with appropriate user editing capabilities) edit a user to remediate problems (as described in the associated entitlement history).
-
Click Edit User from the Review Remediation Request page.
The displayed Edit User page shows:
-
Entitlement history associated with the user, for this work item
-
Attributes for the user
The options that appear here are the same as on the Edit User form available from the Accounts area.
-
-
After making changes to the user, click Save.
Note –Saving user edits causes the Update User workflow to run. Because this workflow may have approvals, it is possible that the changes to the user accounts are not in effect for a period of time after the save. If the audit policy allows re-scans, and the Update User workflow has not completed, then the subsequent policy scan may detect the same violation.
To edit a user, perform the following steps:
- © 2010, Oracle Corporation and/or its affiliates
