Chapter 4 Preparing the SunWeb Deployment Specifications
The deployment specifications are a technical description of SunWeb that is more detailed than the deployment architecture. You derive the deployment specifications from the architecture by adding detailed information that is needed to install and configure the set of components identified in the architecture.
This chapter describes the deployment specifications for the SunWeb deployment in the following sections:
Preparing the Computer Hardware and Operating System Specification
The computer hardware and operating system specification describes the hardware and operating system configuration for each computer in the deployment. Your choice of hardware primarily depends on the level of performance you require from the components running on the computer.
The following table lists the computer hardware chosen for the SunWeb deployment. All of these computers run the Solaris 10 (x86) operating system with zones.
Table 4–1 Computer Hardware and Operating System Specification|
Computers |
Installed Components |
Service Description |
Hardware Model |
|---|---|---|---|
|
Portal Server SRA |
Gateway service for remote portal access |
Sun Fire V20z, 2 x Opteron |
|
|
Portal Server, Portal Server Mobile Access Pack, Access Manager SDK, Application Server, CMS Interface API |
SunWeb portal service |
Sun Fire V20z, 2 x Opteron |
|
|
Access Manager, Directory Server |
SunWeb Access Manager service, SunWeb directory service |
Sun Fire V20z, 2 x Opteron |
|
|
swAM3 through swAM8 |
Access Manager |
SunWeb Access Manager service |
Sun Fire V20z, 2 x Opteron |
Preparing the Network and Connectivity Specification
Before you install and configure the Java ES components that appear in your deployment architecture, the computers must be attached to the network and assigned IP addresses. Preparing the network for a Java ES deployment can be a complex task that requires you to create several subnets to implement the security zones described in the architecture. Before you begin to set up the network, prepare a network and connectivity specification that maps all of the network connections needed to implement the deployment architecture.
A network and connectivity specification is typically a graphical representation of the required network configuration. The following figure is a graphical representation of the network configuration required to implement the SunWeb architecture.
Note –
The IP addresses that appear in the following figure are not the addresses used in the actual SunWeb deployment. The IP addresses in the figure are used only to illustrate the concept of subnet configuration.
The network topology illustrated in the following figure implements the security strategies described in Choosing Security Strategies for the SunWeb Architecture. In particular, the following figure shows how the network and connectivity specification assigns private IP addresses to establish the secure network topology.
Figure 4–1 Network and Connectivity Specification
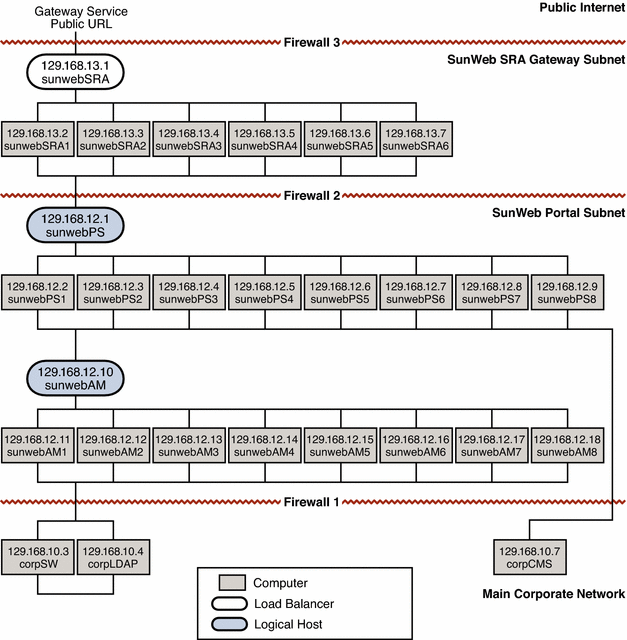
The computers running the gateway service and the computers running the portal service are on separate subnets. The existing corporate services are already deployed on the main corporate network, and appropriate security measures that allow the SunWeb portal controlled access to the information on the main corporate network are in place.
Access from the public Internet is restricted to HTTPS (SSL) access to the load balancer for the gateway service. Certificates are used.
For employees accessing the portal service over the public Internet only the load balancer in the DMZ (subnet 129.168.13.x) is actually exposed as shown in Figure 4–1. Everything else, according to the philosophy of minimizing the surface of attack, is hidden through use of private IP addresses.
Since the DMZ contains the SRA service that is accessed by Sun employees over the public internet, the IP address for the load balancer sunwebSRA is a normal IP address, which is accessible from the Internet. The IP address shown for this load balancer in Figure 4–1 is 129.168.13.1. When this load balancer is configured, however, this address is replaced with the real, publicly accessible address for the gateway service.
All of the other hardware in this zone is assigned 129.168.13.xx IP addresses, which are private addresses. These private addresses are not recognized by the Internet and are not routed outside the corporate network.
The only bridge between the DMZ and the portal service subnet is the load balancer, which controls the traffic between the subnets. Therefore, if the DMZ is compromised there is no direct route to the portal service subnet.
Preparing the User Management Specification
The process of installing and configuring a Java ES deployment establishes both the LDAP schema and the basic tree structure of the LDAP directory. Before beginning the installation and configuration process, you must analyze your directory needs and develop specifications for a schema and a directory tree structure that support your Java ES deployment. At installation and configuration time, the specification ensures that the correct values are input.
This section specifies the LDAP schema and the directory tree specifications for the SunWeb deployment. It also describes how the installation and configuration process establishes the directory schema and the directory tree structure for the deployment.
The LDAP Schema
The Java ES installation and configuration process establishes an LDAP schema for the deployment. The LDAP schema is constructed in stages. Depending on the components in the deployment, the schema can be constructed by the Java ES installer, several of the configuration tools, and the LDAP commands.
With Java ES deployments in general, you need to specify the LDAP schema before you install and configure so that you can select the correct installation and configuration parameters. This section describes the LDAP schema for the SunWeb deployment and the installation parameters that you input to construct the schema.
The first step in specifying the schema for a deployment is to identify the services that the directory service must support. For the SunWeb deployment, the directory service must support the following basic services:
-
Access Manager authentication and single sign-on for SunWeb portal users
-
Proxy authentication for Sun employees who access the corporate mail and calendar services through their portal desktops
-
Control of employee access to portal content
These requirements lead to a relatively simple schema for the SunWeb LDAP directory. To support Access Manager, the schema must be brought up to Schema 2.
Note –
Java ES solutions that use Directory Server can use either of two versions of a Sun standard LDAP schema for messaging and calendaring, which are known as Schema 1 and Schema 2. Schema 2 natively supports Access Manager and Access Manager’s single sign-on feature.
To support control of employee access to portal content, a number of object classes and attributes that correspond to the different types of portal content must be added to the schema. Access Manager uses these object classes and attributes to determine which types of content each user is allowed to view.
The installation and configuration process constructs the schema for the SunWeb deployment as follows:
-
Installing Directory Server creates the basic schema.
-
Installing Access Manager applies Schema 2 to the directory.
Directory Server must be installed before Access Manager, and the Directory Server instances must be running while the Access Manager instances are installed.
-
Adding the object classes and attributes that identify portal services and portal desktop configuration prepares the directory for use in the SunWeb deployment.
Some of the attributes used in the SunWeb schema make use of Directory Server's filtered role feature. The roles are associated with portal display profiles that specify the personalized content for a portal user based on several attributes.
The Directory Tree Structure
The LDAP directory for a Java ES deployment can be simple or complex, depending on the organization’s needs for organizing user data. The LDAP directory for the SunWeb deployment is primarily used to support employees who use the portal service. The SunWeb directory does not need a complex tree structure to classify employee records. That type of classification is maintained in the main corporate LDAP directory.
The directory structure developed to support the SunWeb requirements is illustrated in the following figure.
Figure 4–2 LDAP Directory Tree for the SunWeb Deployment

The root of the SunWeb directory tree is dc=sun,dc=com. The data for SunWeb portal users is stored in ou=people,dc=sun,dc=com.
- © 2010, Oracle Corporation and/or its affiliates
