Chapter 2 Overview of AS2 PM
This chapter provides a general overview of AS2 PM as it functions in the context of Java CAPS and the Sun B2B Suite. The chapter includes system descriptions, AS2 PM information, general operation, and basic features.
This chapter covers the following topics:
-
Note –For more information about eGate, eInsight, and eXchange, see the appropriate user’s guides.
AS2 PM: Introduction
AS2 PM works primarily with eGate, eInsight, and eXchange. You can use AS2 PM to design Java CAPS Projects to process and validate messages using AS2 messaging protocol.
AS2 PM is designed to work with the eXchange B2B framework to expose all of its Projects’ components. This feature allows you to easily expand and customize your Projects.
AS2 PM performs the following basic operations:
-
Uses a Messaging Service (also called a business service), that is, a sequence of events incorporating rules set by the protocol specifications.
-
Uses information in the message itself and in the eXchange Trading Partner (TP) to prepare messages according to AS2 standards.
-
Works with common eXchange Services to prepare and deliver messages, employing the following features:
-
Visibility of the business logic implemented, using eXchange Business Processes (BPs).
-
Error handling
-
Message tracking
-
TP database lookup
-
PKI cryptographic services, such as encryption and signature creation and verification
For complete instructions on how to use AS2 PM see the following books or chapters in this book:
-
Installation, operating system (OS) compatibility, dependencies, and related information, eXchange Integrator Release Notes.
-
Configuration and an explanation of the configuration parameters in eXchange Partner Manager (ePM), a feature of eXchange, Chapter 4, Configuring AS2 PM.
-
General summary of how to get started and use AS2 PM,Chapter 5, Quick Start for AS2 PM .
-
Complete explanation of a sample AS2 PM scenario with operation procedures, Chapter 6, AS2 PM Sample Scenario Tutorial.
Business Problem-Solving With AS2 PM
This book provides instructions and background information for all users of AS2. The book also gives the following types of information about AS2 PM and AS2, to assist in solving your business problems:
-
The relationship of AS2 PM to other components of the Java CAPS, including eGate, eInsight, and eXchange, as well as the appropriate eWays .
-
The AS2 PM components and editors and how to use them in your system environment.
-
How to use the AS2-related features employed by AS2 PM.
-
Importing and implementing an AS2 PM sample scenario provided with the product.
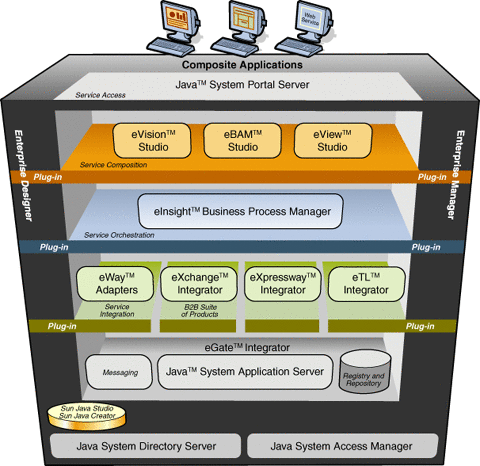
Figure 2–1 shows a diagram of howAS2 PM operates in the context of eXchange and the Sun B2B Suite.
Figure 2–1 AS2 PM/eXchange Operation With Sun B2B Suite
Installing AS2 PM
Open and review the README file for the Java CAPS to gain current information you may need, for example for eGate or eInsight, before installing AS2 PM. You can find this file in the root directory of the Java CAPS installation’s Repository CD-ROM.
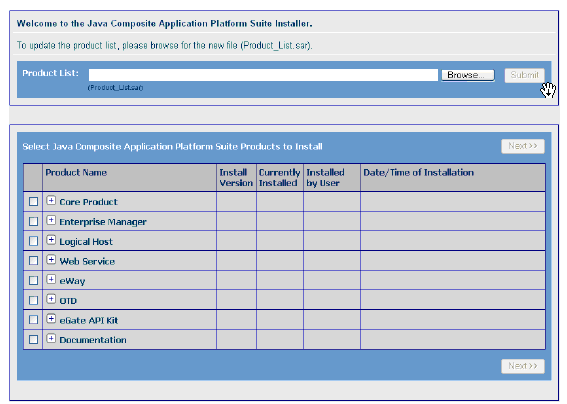
Install AS2 PM, using Java CAPS Installer. Figure 2–2 shows an example of this user interface.
Figure 2–2 Java CAPS Installer Example
Version Information
Note –
See the Sun Java Composite Application Platform Installation Guide for details on how to obtain the README and documentation files for the suite.
This version of AS2 PM is compatible with Java CAPS version 5.1.2 (eGate and eInsight).
Configuring eGate Projects for Large Messages
If an eGate Project uses Sun SeeBeyond JMS (Java Messaging Service) IQ Manager and is estimated to process messages or transactions over 8 megabytes for Windows, or 16 megabytes for UNIX, you must increase the Segment Size property of JMS IQ Manager as explained in the eGate Integrator JMS Reference Guide.
After You Install
Once AS2 PM is installed and configured, it must then operate in conjunction with an eGate Project before it can perform its intended functions. You must create these Projects specifically for AS2 PM, or you must import one or more AS2 PM Projects.
See the eXchange Integrator User’s Guide for detailed information on incorporating these types of Projects into eGate, as well as for more detailed information on PM installation. Also, see the eGate Integrator User’s Guide for information on eGate Projects and their architecture.
Also, see Chapter Chapter 6, AS2 PM Sample Scenario Tutorial for detailed information on a sample business scenario with Projects already created, using eXchange and AS2 PM.
Database Scripts
eXchange allows you to collect database information and persist data about your TPs and their operation. eXchange provides database scripts to create and upgrade this database feature for eXchange. For more information, see the eXchange Integrator User’s Guide.
Configuring Cryptographic Features
Your use of the AS2 protocol assumes you are also using its cryptographic features (encryption, decryption, signatures, and verifications). Additional configuration steps are required in setting up the eXchange Service to use these features. The eXchange Secure Messaging Extension With Keystore (SME/KS) feature enables protected transmission of messages over public domains by providing message encryption, decryption, digital signing, and signature verification.
Note –
For more information on this feature, see Chapter 3, Using SME/KS With AS2 PM.
You must associate encryption information with each XDC eXchange Service. For complete information on setting up an eXchange Service with cryptographic features for protocol managers, see the eXchange Integrator User’s Guide.
Note –
For specific examples of this operation, see the encryption setup used in the sample scenario explained in Chapter 6, AS2 PM Sample Scenario Tutorial.
The rest of this section describes and explains how to install necessary files that allow SME/KS to operate with your AS2 PM system.
Java Cryptography Extension Framework
The Java Cryptography Extension (JCE) framework includes the ability to enforce restrictions on the cryptographic algorithms and strengths. These restrictions are specified in jurisdiction policy files. These files are necessary to enable operation of SME/KS features.
Import control restrictions imposed by some governments require that the default jurisdiction policy files packaged with the Java Run-time Environment (JRE) specify that only strong but limited cryptography may be used. An unlimited strength policy file with no restrictions on cryptographic strength is available for most countries. However, only the strong but limited version can be readily imported into those countries where the governments restrict cryptography. In your JRE environment, the strong but limited default policy files are located as follows:
-
<java-home>/lib/security/local_policy.jar
-
<java-home>/lib/security/US_export_policy.jar
Where, <java-home> is the JRE directory within your Java Development Kit (JDK) environment, or the top-level directory of the JRE. The unlimited strength version of these policy files are downloaded from a Java Download web page (see To Download and Install the Policy Files).
The JCE framework has been through the U.S. export review process and is certified for export. Consult with your export/import control authority to determine your policy requirements.
Installing Policy JAR Files for SME/KS
Before you can implement security using SME/KS, you must replace the existing policy files. You will download different files based on the version of your JRE and your operating system. See Table 2–1 to determine which JRE is running on your logical hosts.
Table 2–1 JRE Versions Listed by Operating System|
Operating System |
JRE |
URL |
|---|---|---|
|
Solaris, Windows, Linux, HP-UX, Tru64 |
1.5.0 |
http://java.sun.com/j2se/1.5.0/download.html |
|
AIX |
1.4.1 |
http://java.sun.com/products/archive/j2se/1.4.1_07/index.html |
To download the files, go to the appropriate URL for your operating system and follow the instructions under To Download and Install the Policy Files.
Note –
Some governments may allow certain applications to be exempt from cryptographic restrictions, that is, exempt applications may implement stronger encryption than nonexempt applications. For an application to be recognized as exempt at run time, it must meet the following criteria:
-
The application must have its policy file bundled with it in a .jar file.
-
The .jar file containing the application and the policy file must be signed using a code-signing certificate issued after the application was designated exempt.
 To Download and Install the Policy Files
To Download and Install the Policy Files
-
Open your browser.
-
Based on your operating system, do one of the following actions:
-
For Solaris, Windows, Linux, HP-UX, or Tru64, do the following operation:
-
On the JSE 1.5.0 web page, scroll down to Other Downloads.
-
Click Download for Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 5.0 and download jse_policy-1_5_0.zip (8.64 kilobytes, including two .jar files each somewhat less than 2500 bytes).
-
After downloading the archive file, extract the following .jar files:
-
local.policy.jar
-
US_export_policy.jar
-
-
For each of your Logical Hosts, replace the existing policy file in the following directory:
Logical Host/jre/lib/security/
-
-
For AIX, do the following operation:
-
On the Archive-Java Technology Products Download page, scroll down to Other Downloads.
-
Click the Download link for Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 1.4.1 and download jce_policy-1.4.1.zip (9.48 kilobytes, contains two files approximately 4300 bytes each).
-
After downloading the archive file, extract the following .jar files:
-
local.policy.jar
-
US_export_policy.jar
-
-
For each of your logical hosts, replace the existing policy files in the following directories:
-
- © 2010, Oracle Corporation and/or its affiliates
