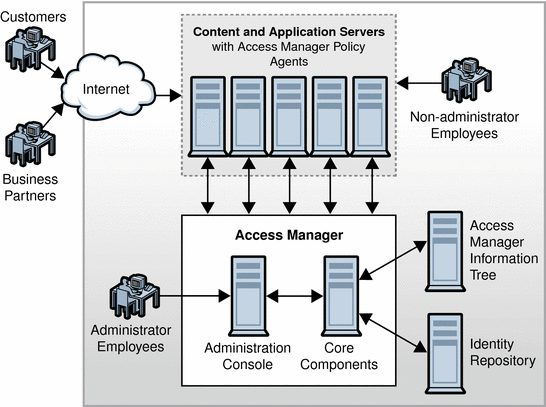
What Access Manager Does
When an enterprise user or an external application tries to access content stored on a company’s web server, the Access Manager policy agent intercepts the request and directs it to the Access Manager server. Access Manager asks the user to present credentials such as a username and password. If the credentials match those stored in the appropriate identity repository, Access Manager determines that the user’s credentials are authentic.
Next, Access Manager evaluates the policies associated with the user’s identity. Policies identify which users or groups of users are authorized to access a resource, and specify conditions under which authorization is valid. Finally, based upon policy evaluation results, Access Manager either grants or denies the user access to the information. What Access Manager Does illustrates one way Access Manager can be configured to act as the gatekeeper to a company’s information resources.
Figure 1–1 Access Manager as the Gateway to a Company's Enterprise Resources
Access Manager integrates the following features into a single product that can be viewed in a single administration console:
Authentication Service
Authentication is the first step in determining whether a user is allowed to access a resource protected by Access Manager. The Access Manager Authentication service verifies that a user really is the person he claims to be. Authentication service consists of the following components: plug-in modules, a framework for connecting plug-in modules, a core authentication component, a web service interface, and client APIs. Authentication Service interacts with the Authentication database to validate user credentials, and interacts with Identity Repository Management plug-ins to retrieve user profile attributes. When Authentication Service determines that a user’s credentials are genuine, a valid user session token is issued, and the user is said to be authenticated.
Policy Service
Authorization is the process by which Access Manager evaluates policies associated with a user’s identity, and determines whether an authenticated user has permission to access a protected resource. Access Manager Policy service enables authorization to take place. Policy service consists of the following components: policy plug-ins, a framework for connecting policy plug-ins, a core policy component, a web service interface, and client APIs. Policy service interacts with Access Manager service configurations, delegation service, and identity repository plug-ins to verify that the user has access privileges from a recognized authority.
User Session Management
An Access Manager user session is the interval between the moment a user logs in to a network resource protected by Access Manager, and the moment the user logs out of the resource. During the user session, Access Manager session service maintains information about the user’s interaction with various applications the user accesses. Access Manager uses this information to enforce time-dependent rules such as timeout limits. Also during the user session, Access Manager provides continuous proof of the user’s identity. This continued proof of identity enables the user to access multiple enterprise resources without having to provide credentials each time.
The Access Manager Session Service enables the following types of user sessions:
-
Basic user session. The user provides credentials to log in to one application, and then logs out of the same application.
-
Single sign-on (SSO) session. The user provides credentials once, and can then access multiple applications within the same DNS domain.
-
Cross-domain SSO session. The user provides credentials once, and can then access applications among multiple DNS domains.
SAML Service
Access Manager uses the Security Assertion Markup Language (SAML), an XML based framework for exchanging security information. While Access Manager User Session service enables single sign-on sessions among different DNS domains within the same intranet, SAML service enables cross-domain sign-on (CDSSO) sessions among different business domains. Using the SAML protocol, business partners can securely exchange authentication and authorization information over the Internet. Access Manager SAML service consists of a web service interface, a SAML core component, and a SAML framework that web services can connect to.
Identity Federation Service
Identity federation allows a user to consolidate the many local identities he has configured among multiple service providers. With one federated identity, the user can log in at one service provider’s site and move to an affiliated service provider site without having to re-authenticate or re-establish his identity. Identity Federation service works with SAML service to enable single sign-on sessions among business partners over the Internet. Identity Federation services consists of a web service interface, a core Identity Federation component, and an Identity Federation Framework that complies with the Liberty Alliance Project specifications.
Logging
When a user logs in to a resource protected by Access Manager, the Logging component logs information about the user's activity. You can write custom log operations and customize log plug-ins to generate log reports for auditing purposes.
- © 2010, Oracle Corporation and/or its affiliates
