Chapter 7 Integrating an Existing User Data Store
This chapter contains detailed instructions for the following tasks:
7.1 Creating and Configuring a New User Data Store
In this deployment example, the new user data store is created within the same Directory Servers as the Access Manager configuration store. In most cases, the new data store would be created in a different Directory Server.
Figure 7–1 Directory Servers with User Data and Access Manager Configuration
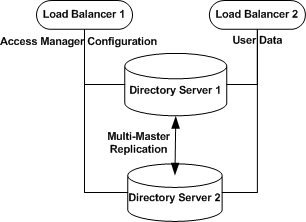
 To Create a User Data Store Instance on Directory
Server 1
To Create a User Data Store Instance on Directory
Server 1
-
As a root user log in to the Directory Server 1 host.
-
Run the netstat command to be sure the that the Directory Server administration port is open.
# cd /var/opt/mps/serverroot
# netstat —an | grep 1391
* 1390 *.* 0 0 49152 0 LISTEN
If the administration server is not running, start it now:
# ./start-admin
-
Start the Directory Server console.
# ./startconsole &
-
Log in to the Directory Server console using the following information:
- Username
-
cn=Directory Manager
- Password
-
d1rm4n4ger
- Administration URL
-
http://DirectoryServer-1.example.com:1391
-
Expand the example.com domain, the DirectoryServer-1.example.comnode, and the Server Group object.
You should see three Directory Server objects: an Administration Server, Directory Server (ds-config), and Directory Server (am-config).
-
Right-click the Server Group object, and choose “Create Instance Of.”
Choose Sun JavaTM System Directory Server.
-
In the Create New Instance dialog, provide the following information and then click OK:
- Server Identifier:
-
am-users
- Network port:
-
1489
- Base suffix:
-
dc=company,dc=com
- Directory Manager DN:
-
cn=Directory Manager
- Directory Manager Password:
-
d1rm4n4ger
- Confirm password:
-
d1rm4n4ger
- Server Runtime (UNIX) user ID:
-
nobody
In the navigation tree, the new instance Directory Server (am-users) is added to the Server Group list.
-
In the navigation tree, click the Directory Server (am-users) to open its console.
Verify that the Server status indicates “Started.”
-
Click Open, then click the Directory tab.
In the DirectoryServer-1.example.com:1489 node, you should see the new user data store base suffix dc=company,dc=com .
 To Create a User Data Store Instance on Directory
Server 2
To Create a User Data Store Instance on Directory
Server 2
-
As a root user log in to the Directory Server 2 host.
-
Run the netstat command to be sure the that the Directory Server administration port is open.
# cd /var/opt/mps/serverroot
# netstat —an | grep 1391
* 1390 *.* 0 0 49152 0 LISTEN
If the administration server is not running, start it now:
# ./start-admin
-
Start the Directory Server console.
# ./startconsole &
-
Log in to the Directory Server console using the following information:
- Username
-
cn=Directory Manager
- Password
-
d1rm4n4ger
- Administration URL
-
http://DirectoryServer-2.example.com:1391
-
Expand the example.com domain, the DirectoryServer-2.example.comnode, and the Server Group object.
You should see three Directory Server objects: an Administration Server, Directory Server (ds-config), and Directory Server (am-config).
-
Right-click the Server Group object, and choose “Create Instance Of.”
Choose Sun Java System Directory Server.
-
In the Create New Instance dialog, provide the following information and then click OK:
- Server Identifier:
-
am-users
- Network port:
-
1489
- Base suffix:
-
dc=company,dc=com
- Directory Manager DN:
-
cn=Directory Manager
- Directory Manager Password:
-
d1rm4n4ger
- Confirm password:
-
d1rm4n4ger
- Server Runtime (UNIX) user ID:
-
nobody
In the navigation tree, the new instance Directory Server (am-users) is added to the Server Group list.
-
In the navigation tree, click the Directory Server (am-users) to open its console.
Verify that the Server status indicates “Started.”
-
Click Open, then click the Directory tab.
In the DirectoryServer-2.example.com:1489 node, you should see the new user data store base suffix dc=company,dc=com .
 To Create a New Branch in the User Data Store
To Create a New Branch in the User Data Store
You only have to perform these steps on Directory Server 1. With multi-master replication enabled, all changes to the directory are automatically replicated to Directory Server 2.
-
Log in to the Directory Server 1 console using the following information.
- Username
-
cn=Directory Manager
- Password
-
d1rm4n4ger
- Administration URL
-
http://DirectoryServer-1.example.com:1391
-
In the navigation pane, expand the example.com suffix, and expand the Server Group objects.
-
Under Server Group, click the am-usersinstance.
In the am-users console properties page, click Open.
-
Click the Directory tab,
-
Select New Instance, and then open the new instance.
-
Click the Directory tab.
-
Right click the dc=company, dc=com suffix, and choose “Create a new Organization Unit.”
-
In the Create New Organizational Unit dialog, in the Name field, enter users, and then click OK.
On the Directory tab, click the dc=company,dc=com suffix. You should see the new users instance in the list.
 To Import Users into the User Data Store
To Import Users into the User Data Store
In this procedure, you create four special accounts for the following users:
-
The user userdbadmin will be used by the AccessManager servers to connect to the user data store for data management purposes.
-
The user userdbauthadmin will be used by the AccessManager servers to authenticate users to the user data store.
-
The user testuser1 will be used to verify that the Policy Agent is configured properly.
-
The user testuser2 will be used to verify the working of the Policy Agent.
-
Create an LDIF file named /tmp/am-users.ldif.
The file should contain the following users:
dn: uid=userdbadmin,ou=users,dc=company,dc=com uid: userdbadmin givenName: UserDB objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetorgperson sn: Admin cn: UserDB Admin userPassword: 4serd84dmin dn: uid=userdbauthadmin,ou=users,dc=company,dc=com uid: userdbauthadmin givenName: UserDB objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetorgperson sn: AuthAdmin cn: UserDB AuthAdmin userPassword: 4serd84uth4dmin dn: uid=testuser1,ou=users,dc=company,dc=com uid: testuser1 givenName: Test objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetorgperson sn: User1 cn: Test User1 userPassword: password dn: uid=testuser2,ou=users,dc=company,dc=com uid: testuser2 givenName: Test objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetorgperson sn: User2 cn: Test User2 userPassword: password
-
Import the LDIF file into the Directory Server-1 server.
# cd /var/opt/mps/serverroot/shared/bin # ./ldapmodify -h DirectoryServer-1.example.com -p 1489 -D "cn=Directory Manager" -w d1rm4n4ger -a -f /tmp/am-users.ldif adding new entry uid=userdbadmin,ou=users,dc=company,dc=com adding new entry uid=userdbauthadmin,ou=users,dc=company,dc=com
-
Verify that the new users were imported to Directory Server 1 with no errors.
7.2 Enabling Multi-Master Replication
In this procedure you enable multi-master replication (MMR) between two directory masters. Then you use the data and schema from the first directory master to initialize the second directory master. When you're finished, you will have two Directory Servers, and each will contain two instances. The instance named ds-config stores Directory Server administration configuration. The instance named am-config stores the user data and Access Manager configuration.
On each Directory Server, the ds-config instance is a local configuration instance. Do not replicate this instance to other host systems. On each Directory Server, the am-config instance is the directory data instance. You enable the am-config instance for MMR with its counterpart on the other Directory Server host.
Use the following as your checklist for enabling multi-master replication:
 To Enable Multi-Master Replication on Directory
Server 1
To Enable Multi-Master Replication on Directory
Server 1
-
On Directory Server 1, start the Directory Server console.
# cd /var/opt/mps/serverroot/ # ./startconsole &
-
Log in to the Directory Server 1 console using the following information:
- Username
-
cn=Directory Manager
- Password
-
d1rm4n4ger
- Administration URL
-
http://DirectoryServer-1.example.com:1391
-
In the Directory Server console, under the Servers and Applications tab, expand the Server Administration domain list until you see the Server Group item.
-
Click to expand the Server Group.
You should see the following items: an Administration Server, a Directory Server (am-config), a Directory Server (ds-config), and a Directory Server (am-users).
-
Double-click the instance name Directory Server (am-users) to display the console for managing the instance am-users.
-
Click the Configuration tab and navigate to the Replication pane.
-
Click the “Enable replication” button to start the Replication Wizard.
-
Select Master Replica, and then click Next to continue.
-
Enter a Replica ID, and then click Next.
For this example, when enabling replication on DirectoryServer-1, assign the number 11.
-
If you have not already been prompted to select the change log file, you are prompted to select one now.
The default change log file is shown in the text field. If you do not wish to use the default, type in a filename for the change log, or click Browse to display a file selector. If the change log has already been enabled, the wizard will skip this step.
-
If you have not already been prompted to enter and confirm a password for the default replication manager, you are prompted now.
The replication manager is not used in the case of single-master replication, but you must still enter a password to proceed. For this example, enter replm4n4ger.
The Replication Wizard displays a status message while updating the replication configuration.
-
Click Close when replication is finished.
 To Enable Multi-Master Replication on Directory
Server 2
To Enable Multi-Master Replication on Directory
Server 2
-
On Directory Server 2, start the Directory Server console.
# cd /var/opt/mps/serverroot/ # ./startconsole &
-
Log in to the Directory Server 2 console using the following information:
- Username
-
cn=Directory Manager
- Password
-
d1rm4n4ger
- Administration URL
-
http://DirectoryServer-2.example.com:1391
-
In the Directory Server console, under the Servers and Applications tab, expand the Server Administration domain list until you see the Server Group item.
-
Click to expand the Server Group.
You should see the following items: an Administration Server, a Directory Server (am-config), a Directory Server (ds-config), and a Directory Server (am-users).
-
Double-click the instance name Directory Server (am-users) to display the console for managing the instance am-config.
-
Click the Configuration tab and navigate to the Replication pane.
-
Click the “Enable replication” button to start the Replication Wizard.
-
Select Master Replica, and then click Next to continue.
-
Enter a Replica ID, and then click Next.
For this example, when enabling replication on DirectoryServer-2, assign the number 22.
-
If you have not already been prompted to select the change log file, you are prompted to select one now.
The default change log file is shown in the text field. If you do not wish to use the default, type in a filename for the change log, or click Browse to display a file selector. If the change log has already been enabled, the wizard will skip this step.
-
If you have not already been prompted to enter and confirm a password for the default replication manager, you are prompted now.
The replication manager is not used in the case of single-master replication, but you must still enter a password to proceed. For this example, enter replm4n4ger.
The Replication Wizard displays a status message while updating the replication configuration.
-
Click Close when replication is finished.
 To Create Replication Agreements on Directory
Server 1
To Create Replication Agreements on Directory
Server 1
-
On DirectoryServer-1, in the Directory Server console, display the general properties for the Directory Server instance named am-users .
Navigate through the tree in the left panel to find the Directory Server instance named am-users, and click on the instance name to display its general properties.
-
Click the Open button to display the console for managing the am-users instance.
-
Click the Configuration tab and navigate to the Replication pane.
-
Click the New button.
-
In the Replication Agreement dialog box, click the Other button.
-
In the Remote Server dialog box, provide the following information, and then click OK.
- Host
-
DirectoryServer-2.example.com
- Port
-
1489
- Secure Port
-
Leave this box unmarked.
-
In the Replication Agreement dialog, for the distinguished name (DN) of the replication manager entry on the consumer server, accept the default value.
By default, the DN is that of the default replication manager.
-
For the password of the replication manager, enter replm4n4ger.
-
(Optional) Provide a description string for this agreement.
For this example, enter Replication from DirectoryServer-1 to DirectoryServer-2.
-
Click OK when done.
-
In the confirmation dialog, click Yes to test the connection to the server and port number.
Use the given replication manager and password replm4n4ger.
If the connection fails, you will still have the option of using this agreement. For example, the parameters are correct but the server is offline. When you have finished, the agreement appears in the list of replication agreements for this master replica.
 To Create Replication Agreements on Directory
Server 2
To Create Replication Agreements on Directory
Server 2
-
On DirectoryServer-2, in the Directory Server console, display the general properties for the Directory Server instance named am-users.
Navigate through the tree in the left panel to find the Directory Server instance named am-users, and click on the instance name to display its general properties.
-
Click the Open button to display the console for managing the am-users instance.
-
Click the Configuration tab and navigate to the Replication pane.
-
Click the New button.
-
In the Replication Agreement dialog box, click the Other button.
-
In the Remote Server dialog box, provide the following information, and then click OK.
- Host
-
DirectoryServer-1.example.com
- Port
-
1489
- Secure Port
-
Leave this box unmarked.
-
In the Replication Agreement dialog, for the distinguished name (DN) of the replication manager entry on the consumer server, accept the default value.
By default, the DN is that of the default replication manager.
-
For the password of the replication manager, enter replm4n4ger.
-
(Optional) Provide a description string for this agreement.
For this example, enter Replication from DirectoryServer-2 to DirectoryServer-1.
-
Click OK when done.
-
In the confirmation dialog, click Yes to test the connection to the server and port number.
Use the given replication manager and password.
If the connection fails, you will still have the option of using this agreement. For example, the parameters are correct but the server is offline. When you have finished, the agreement appears in the list of replication agreements for this master replica.
 To Initialize the Master Replica
To Initialize the Master Replica
-
On DirectoryServer–1, in the Directory Server console, navigate through the tree in the left panel to find the Directory Server instance named am-users, and click on the instance name to display its general properties.
-
Double-click the instance name Directory Server (am-users) in the tree to display the console for managing the data.
-
Click the Configuration tab and navigate to the Replication pane.
-
In the list of defined agreements, select the replication agreement corresponding to DirectoryServer-2, the consumer you want to initialize.
-
Click Action > Initialize remote replica.
A confirmation message warns you that any information already stored in the replica on the consumer will be removed.
-
In the Confirmation dialog, click Yes.
Online consumer initialization begins immediately. The icon of the replication agreement shows a red gear to indicate the status of the initialization process.
-
Click Refresh > Continuous Refresh to follow the status of the consumer initialization.
Any messages for the highlighted agreement will appear in the text box below the list.
-
Verify that replication is working properly.
-
Log in to both Directory Server hosts as a root user, and start both Directory Server consoles.
-
Log in to each Directory Server console.
-
In each Directory Server console, enable the audit log on both Directory Server instances.
Go to Configuration > Logs > Audit Log. Check Enable Logging, and then click Save.
-
In separate terminal windows , use the tail -f command to watch the audit log files change.
-
On DirectoryServer-1, in the Directory Server console, create a new user entry.
-
Go to the Directory tab, and expand the suffix dc=company,dc=com.
-
Right-click users, and then choose New > User.
-
In the Create New User dialog, enter a first name and last name, an then click OK.
Note the user entry is created in the instance audit log. Check to be sure the same entry is also created in on DirectoryServer-2 in the Directory Server instance audit log
-
-
On DirectoryServer-2, in the Directory Server console, create a new user entry.
-
Go to the Directory tab, and expand the suffix dc=company,dc=com.
-
Right-click users, and then choose New > User.
-
In the Create New User dialog, enter a first name and last name, an then click OK.
Note the user entry is created in the instance audit log. Check to be sure the same entry is also created in on DirectoryServer-1 in the Directory Server instance audit log
-
-
Delete both new user entries in the Directory Server 2 console.
Look in the Directory Server 1 console to verify that both users have been deleted.
-
7.3 Configuring the User Data Stores Load Balancer
-
Contact your network administrator to obtain an available virtual IP address for the load balancer you want to configure.
You must also know the IP address of the load balancer hardware, the URL for the load balancer login page, and a username and password for logging in to the load balancer application.
Note –The load balancer hardware and software used in the lab facility for this deployment is BIG-IP® manufactured by F5 Networks. If you are using different load balancer software, see the documentation that comes with that product for detailed settings information.
-
You must also have ready the IP addresses for Directory Server 1 and Directory Server 2.
To obtain these IP addresses, on each Directory Server host, run the following command:
ifconfig —a
 To Configure the User Data Stores Load Balancer
To Configure the User Data Stores Load Balancer
-
Create a Pool.
A pool contains all the backend server instances.
-
Go to URL for the Big IP load balancer login page.
-
Open the Configuration Utility.
Click “Configure your BIG-IP (R) using the Configuration Utility.”
-
In the left pane, click Pools.
-
On the Pools tab, click the Add button.
-
In the Add Pool dialog, provide the following information:
- Pool Name
-
Example: DirectoryServer-UserData-Pool
- Load Balancing Method
-
Round Robin
- Resources
-
Add the IP address of both Directory Server hosts. In this case, add the IP address and port number for DirectoryServer-1:1489 and for DirectoryServer-2:1489.
-
Click the Done button.
-
-
Add a Virtual Server.
If you encounter Javascript errors or otherwise cannot proceed to create a virtual server, try using Microsoft Internet Explorer for this step.
-
In the left frame, Click Virtual Servers.
-
On the Virtual Servers tab, click the Add button.
-
In the Add a Virtual Server dialog box, provide the following information:
- Address
-
xxx.xx.69.14 (for LoadBalancer-2.example.com)
- Service
-
489
- Pool
-
DirectoryServer-UserData-Pool
-
Continue to click Next until you reach the Pool Selection dialog box.
-
In the Pool Selection dialog box, assign the Pool (DirectoryServer-POOL) that you have just created.
-
Click the Done button.
-
-
Add Monitors
Monitors are required for the load balancer to detect the backend server failures.
-
In the left frame, click Monitors.
-
Click the Basic Associations tab.
-
Add an LDAP monitor for the Directory Server 1 node.
Three columns exist on this page: Node, Node Address, and Service. In the Node column, locate the IP address and port number DirectoryServer-1:1489 . Select the Add checkbox.
-
Add an LDAP monitor for the Directory Server 2 node.
In the Node column, locate the IP address and port number for DirectoryServer–2:1489. Select the Add checkbox.
-
At the top of the Node column, in the drop-down list, choose ldap-tcp.
-
Click Apply.
-
-
Configure the load balancer for persistence.
-
Verify the Directory Server load balancer configuration.
-
Log in as a root user to the host of each Directory Server.
-
On each Directory Server host, use the tail command to monitor the Directory Server access log.
# cd /var/opt/mps/serverroot/slapd-am-users/logs
# tail -f access
You should see connections to the load balancer IP address opening and closing. Example:
[12/Oct/2006:13:10:20-0700] conn=54 op=-1 msgId=-1 — fd=22 slot=22 LDAP connection from xxx.xx.69.18 to xxx.xx.72.33
[12/Oct/2006:13:10:20-0700] conn=54 op=-1 msgId=-1 — closing — B1
[12/Oct/2006:13:10:20-0700] conn=54 op=-1 msgId=-1 — closed.
-
Execute the following LDAP search against the Directory Server load balancer:
# cd /var/opt/mps/serverroot/shared/bin/ # ./ldapsearch -h LoadBalancer-2.example.com -p 1489 -b "dc=company,dc=com" -D "cn=directory manager" -w d1rm4n4ger "(objectclass=*)"
The ldapsearch operation should return entries. Make sure the directory access entries display in only one Directory Server access log.
-
Stop Directory Server 1, and again perform the following LDAP search against the Directory Server load balancer:
# cd /var/opt/mps/serverroot/slapd-am-config # ./stop # cd /var/opt/mps/serverroot/shared/bin/ # ./ldapsearch -h LoadBalancer-2.example.com -p 1489 -b "dc=company,dc=com" -D "cn=directory manager" -w d1rm4n4ger "(objectclass=*)"
The ldapsearch operation should return entries. Verify that the Directory Server access entries display in only one Directory Server access log.
You may encounter the following error message:
ldap_simple_bind: Cant' connect to the LDAP server — Connection refused
In the Load Balancer configuration page, reset the timeout properties to lower values.
-
Click the Monitors tab, and click the ldap-tcp monitor name.
-
In the Interval field, set the value to 5.
-
In the Timeout field, set the value to 16.
The default is 16 seconds. You can change this number to any value. In this deployment example, the BigIP documentation recommends the value should be at least three times the interval number of seconds plus one second.
-
Click Apply.
Repeat the LDAP search.
-
-
Restart the stopped Directory Server 1, and then stop Directory Server 2.
Confirm that the requests are forwarded to the running Directory Server 1.
-
Perform the following LDAP search against the Directory Server load balancer.
# cd /var/opt/mps/serverroot/shared/bin/ # ./ldapsearch -h LoadBalancer-2.example.com -p 1489 -b "dc=company,dc=com" -D "cn=Directory Manager" - w d1rm4n4ger "(objectclass=*)"
The ldapsearch operation should return entries. Make sure the directory access entries display in only the one Directory Server access log.
-
7.4 Configuring a User Realm
Create a new realm that you can use to authenticate against only the existing Directory Server. The two Access Manager servers share configuration, so you configure the new realm on just one Access Manager server.
Use the following as your checklist for creating a user realm:
 To Create a New Realm
To Create a New Realm
-
Start a new browser and log in to the first Access Manager server.
Go to the URL http://AccessManager-1.example.com:1080/amserver/console
-
Log in as a root user to the Access Manager console using the following information:
- User Name:
-
amadmin
- Password:
-
4m4dmin1
-
Click the Access Control tab, and then click New.
-
In the New Realm page, in the Name field, enter users .
-
Click OK.
 To Configure a Realm Alias
To Configure a Realm Alias
-
On the Access Control tab, under Realms, click the Realm Name users.
-
On the General tab for users-Properties, add users to the Realm/DNS/Aliases list.
In the Add field enter users, and then click Add.
-
Click Save.
 To Configure the Realm Authentication
To Configure the Realm Authentication
-
Modify the User Profile.
-
Click Realms.
-
On the Access Control tab, under Realms, select the new realm users.
-
Click the Authentication tab.
-
In the General section, click Advanced Properties.
-
In the Core page, in the Realm Attributes section, change the User Profile attribute to Ignored.
Access Manager is configured to use only the existing Directory Server for authentication, and a full User Profile may not exist. That's why the attribute is set to Ignored in this example.
-
Click Save.
The changes are saved, and the Core > Realm Attributes page is displayed.
-
-
Create a new authentication module.
-
Configure the new realm.
-
In the users — Authentication page, in the New Module Instances section, click the New Instance named usersLDAP.
-
In the LDAP > Realm Attributes page, set the following attributes:
- Primary LDAP Server
-
-
In the Add field, enter the hostname and port number for the load balancer for the user data store:LoadBalancer-2.example.com:489 .
-
In the server listbox, select the default server, then click Remove.
-
- DN to Start User Search
-
-
In the Add field, enter dc=company,dc=com and then click Add.
-
Select the default entry o=example.com, and then click Remove.
-
- DN for Root User Bind
-
uid=userdbauthadmin,ou=users,dc=company,dc=com
- Password for Root User Bind
-
4serd84uth4dmin
- Password for Root User Bind (confirm)
-
4serd84uth4dmin
These values were imported into the user data store in a previous task. See To Import Users into the User Data Store.
-
Click Save.
The changes are saved, and the users — Authentication page is displayed.
-
-
Configure the default ldapService chain to use the new authentication module.
-
Remove the LDAP authentication module.
This module is automatically inherited from the default realm and it authenticates against the Access Manager configuration directory. The module is no longer needed now that the usersLDAP module will be used for authentication.
-
On the users — Authentication page, click Save.
Changes you made in the previous steps are saved.
 To Configure Access Manager to Use Roles from
the User Data Store
To Configure Access Manager to Use Roles from
the User Data Store
This procedure is not required to make Access Manager work in all scenarios because not all scenarios require role support. The procedure is required in this deployment example because policies are created in later procedures, and the policies will refer to roles.
-
On the Access Control tab, under Realms, click the users link.
-
Click the Data Stores tab, and then click the usersLDAP link.
-
On the Edit Data Store page, in the section “LDAPv3 Plugin Supported Types and Operations,” in the Add field, enter role=read,create,edit,delete, and then click Add.
-
In the section, “LDAP User Attributes,” in the Add field, enter nsrole, and then click Add.
-
In the Add field, enter nsroledn, and then click Add.
-
Click Save.
-
Edit the Top-Level Realm.
Click Edit Realm.
-
Click Subjects > Role.
Two roles employee and manager are in the Roles list.
-
Click the Users tab, and then click the testuser1 link.
-
Click on the Role tab.
Verify that testuser1 is added to the manager role. The role manager is displayed in the list of selected roles.
-
Click Edit Realm —users, and then click the testuser2 link.
-
Click on the Role tab.
Verify that testuser2 is added to the employee role. The role employee is displayed in the list of selected roles.
-
Click Edit Realm —users, and then click the testuser2 link.
-
 To Configure the User Data Stores
To Configure the User Data Stores
-
Delete the default data store.
-
Create a new data store.
-
Click New .
-
In the “Step 1 of 2: Select Type of Data Store” page, set the following attributes:
- Name
-
Enter usersLDAP.
- Type
-
Choose “LDAPv3 Repository Plug-In.”
-
Click Next.
-
In the “Step 2 of 2: New Data Store” page, set the following attributes:
- Primary LDAP Server
-
-
In the Add field, enter the hostname and port number for the existing directory. Use the form LoadBalancer-2.example.com:489
-
Select the default DirectoryServer-1.example.com:1389 , and then click Remove.
-
- LDAP Bind DN
-
Enter uid=userdbadmin,ou=users,dc=company,dc=com .
- Password for Root User Bind
-
4serd84dmin
- Password for Root User Bind (confirm)
-
4serd84dmin
- LDAP Organization DN
-
Enter dc=company,dc=com.
- LDAP People Container Value
-
users
When this field is empty, the search for users will start from the root suffix.
- Persistent Search Base DN
-
Enter dc=company,dc=com.
These values were imported into the user data store in a previous task. See To Import Users into the User Data Store.
-
Click Finish and log out of the Access Manager console.
-
-
Restart each Access Manager server for the changes to take place.
Log in to each Access Manager host system, and restart the Web Server on each host system.
-
Verify that in the Access Manager console you can see the users in the external user data store.
-
Go to the Access Manager URL.
http://AccessManager-1.example.com:1080/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
-
Click on Users Realm.
-
Click on Subjects tab.
You should see three new users: authuiadmin, userdbadmin, and userdbauthadmin.
-
-
Verify that a user can successfully authenticate against the new realm.
-
Start a new browser session and log in to Access Manager.
Go to the following URL:
http://AccessManager-1.example.com:1080/amserver/UI/Login?realm=users
The parameter realm=users specifies the new realm to use for authentication. Without the parameter, the default realm is used.
-
On the login page, provide a user login and password from the existing directory.
- User Name:
-
authuiadmin
- Password:
-
4uthu14dmin
You should be able to log in successfully.
If the login is not successful, watch the existing Directory Server access log to troubleshoot the problem.
At this point, a user can log in against the existing Directory Server if he invokes the realm=users parameter. If such a parameter is absent, the default realm is used.
Administrators who want to access the Access Manager console should log in to the default realm.
-
7.5 (Optional) Enabling Access Manager to Manage Users in the Existing User Data Store
You can user the Access Manager console to create, edit, and delete user profiles in your existing data store. The procedures in this section are optional.
Access Manager typically is used more for policy management than for user management. In most cases, the user repository is a different repository than the one used by Access Manager to store its configuration. Administrators usually prefer to manage the user repository separately or differently from the Access Manager repository. However, at some times administrators find it necessary to manage the assignment of Access Manager services to users or roles. For convenience, administrators can to do this through the Access Manager console. The relevant AM objectclasses must be imported into the user repository so that Access Manager can read and write Access Manager service properties into the relevant entries in the user repository.
Use the following as your checklist for enabling Access Manager to manage users in the existing data store:
-
Configure Access Manager to manage users in an existing user data store.
-
Verify that user management with the existing data store works properly.
 To Configure Access Manager to Manage Users
in an Existing User Data Store
To Configure Access Manager to Manage Users
in an Existing User Data Store
-
Copy Access Manager schema to Directory Server 1.
-
Copy Access Manager schema to Directory Server 2.
-
Start the Directory Server 1 console.
# cd /var/opt/mps/serverroot # ./startconsole &
-
Log in to the Directory Server 1 console using the following information:
- Username
-
cn=Directory Manager
- Password
-
d1rm4n4ger
- Administration URL
-
http://DirectoryServer-1.example.com:1391
-
Create a new Access Control Instruction (ACI).
-
In the Directory Server console, in the navigation tree, expand the Server Group object and then click on the am-users instance.
-
On the Directory Server page for am-users, click Open.
-
Click the Directory tab.
-
In the navigation tree, click the dc=company, dc=com suffix.
-
Double-click the Directory Administrators group.
-
On the Edit Entry page for Directory Administrators, click Members.
-
On the Static Group page, click Add.
-
In the Search dialog, click Search.
-
In the results list, click the User ID userdbadmin.
The Member User ID userdbadmin is now added to the Static Group list.
Click OK.
-
-
Set access permissions.
-
On the Directory tab, in the navigation tree, right— click the dc=company, dc=com suffix, and the select Set Access Permissions.
-
In the Manage Access Control dialog, click New.
-
In the Edit ACI dialog, in the ACI name field, enter Directory Administrators.
-
In the list of Users/Groups, select All Users, and then click Remove.
-
Click Add.
-
In the Add Users and Groups, click Search.
-
In the Search results list, select Directory Administrators, and then click Add.
-
Click OK.
The group Directory Administrators group is now displayed in the list of Users/Groups who have access permission.
-
Click the Target tab.
-
In the “Target directory entry,” click This Entry.
The dc=company,dc=com suffix is displayed.
-
Click OK.
The Directory Administrators group is displayed in the Manage Access Control dialog.
-
Click OK, and then log out of Directory Server 1.
-
-
Restart both Directory Server 1 and Directory Server 2.
-
Log in as a root user to the Directory Server 1 host.
# cd /var/opt/mps/serverroot # ./restart
-
Log in as a root user to the Directory Server 2 host.
# cd /var/opt/mps/serverroot # ./restart
Tip –If you see errors such as the following on the command line:
[13/Oct/2006:12:43:39 -0700] - ERROR<5895> - Schema - conn=-1 op=-1 msgId=-1 - User error: Entry "cn=schema", single-valued attribute "modifyTimestamp" has multiple values
then run the following commands:
# cd config/schema # edit file 98am-schema.ldif # remove the entries: modifiersName: cn=directory manager modifyTimestamp: 20060913190551Z # cd ../.. # ./restart-slapd
-
-
Restart both Access Manager 1 and Access Manager 2.
 To Verify that User Management with the Existing
Data Store Works Properly
To Verify that User Management with the Existing
Data Store Works Properly
-
In a browser, go to the following Access Manager URL:
https://loadbalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
-
Add a new user.
-
On the Realms page, click the users link.
-
Click the Subjects tab.
-
On the User page, under User, click New.
-
On the New User page, provide the following information, and then click Create:
- ID:
-
johndoe
- First Name:
-
John
- Last Name:
-
Doe
- Full Name:
-
John Doe
- Password:
-
password
- Password Confirm:
-
password
John Doe is now displayed in the list of Users. This indicates the user created in Access Manager was also created in Directory Server. Changes to the user profile were updated in Directory Server.
-
Modify the John Doe entry.
-
-
Log in as a root user to the host DirectoryServer-1.
-
Start the Directory Server console:
# cd /var/opt/mps/serverroot # ./startconsole &
-
Log in to the Directory Server console using the following information:
- Username
-
cn=Directory Manager
- Password
-
d1rm4n4ger
- Administration URL
-
http://DirectoryServer-1.example.com:1391
-
In the navigation tree, expand the DirectoryServer-1 node, and expand the Server Group.
-
Click the am-users instance.
-
On the Directory Server page for am-users , click Open.
-
Click the Directory tab.
-
Click the dc=company,dc=com suffix, and then click the users group.
-
In the list of users, double-click the johndoeentry.
In the Edit User page, verify that the information is the same as the information you entered through the Access Manager console in the previous steps.
Leave the Directory Server console open.
-
-
In the Access Manager console, create a new role and add John Doe to the role.
-
In the Realms page for users, click the Subjects tab.
-
Click the Role tab.
-
Under Roles, click New Role.
-
In the Role page, in the Name field, enter testRole.
-
Click Create.
The new role testRole is now displayed in the list of roles.
-
Click the testRole link.
-
Click the User tab.
-
In the Edit Role page for testRole, in the Available list, select johndoe.
-
Click Add.
The user johndoe is added to the Selected list.
-
Click Save.
John Doe is now added to the testRole role.
-
-
Verify that the new user and role are created in Directory Server.
- © 2010, Oracle Corporation and/or its affiliates
