How to Create a New Principal
An example of the corresponding command-line equivalent follows this procedure.
-
If neccessary, start the SEAM Tool.
See "How to Start the SEAM Tool" for details.
Note -If you are creating a new principal that may need a new policy, you should create the new policy before creating the new principal. Go to "How to Create a New Policy".
-
Click the Principals tab.
-
Click New.
The Principal Basics panel containing some of the attributes for a principal is displayed.
-
Specify a principal name and password.
Both the principal name and password are mandatory.
-
Specify values for the principal's attributes and continue to click Next to specify more attributes.
Three windows contain attribute information. Choose Context-Sensitive Help from the Help menu to get information about the various attributes in each window. Or, go to "SEAM Tool Panel Descriptions" for all the principal attribute descriptions.
-
Click Save to save the principal, or click Done on the last panel.
-
If needed, set up Kerberos administration privileges for the new principal in the /etc/krb5/kadm5.acl file.
See "How to Modify the Kerberos Administration Privileges" for more details.
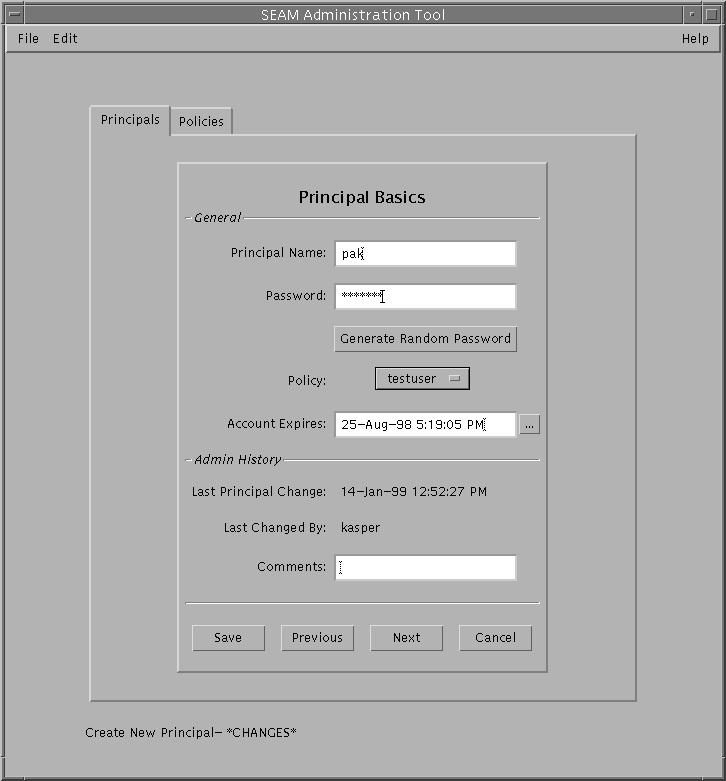
Example--Creating a New Principal
The following example shows the Principal Basics panel when creating a new principal called pak. So far, the policy has been set to testuser.
Example--Creating a New Principal (Command Line)
The following example uses the add_principal command of kadmin to create a new principal called pak. The principal's policy is set to testuser.
kadmin: add_principal -policy testuser pak Enter password for principal "pak@ACME.COM": <type the password> Re-enter password for principal "pak@ACME.COM": <type the password again> Principal "pak@ACME.COM" created. kadmin: quit |
- © 2010, Oracle Corporation and/or its affiliates
