The Remote Access Dialup User Service (RADIUS) protocol improves network security by providing a mechanism for authenticating remote users connecting to the network. It does this by carrying authentication, authorization and configuration information between a Network Access Server (NAS) and a RADIUS server.
A NAS, also known as a Remote Access Server (RAS), is a device that provides an access point to a network for remote users connecting through remote access protocols such as telnet, ftp or PPP.
Figure 1.1 Network Access Server.
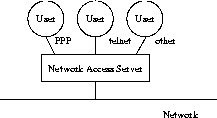
The configuration shown in Figure 1.1 relies on security mechanisms provided by the connection protocol in use, for example PPP, to prevent unauthorized access to the network. Using RADIUS, you can keep a single source of authentication information in a directory and use it to authenticate remote users. The security mechanism is the same regardless of the connection protocol.