| Sun ONE Meta-Directory 5.1.1 Deployment Guide |
Chapter 1
Meta-Directory ConceptsThis chapter provides an overview of Meta-Directory and its components and describes why it is an essential application in today’s directory environment.
The chapter contains the following top-level sections:
The Importance of Meta-DirectoryA typical business enterprise today uses a myriad of directory system types. Often, the different systems collect information on the same entries (for example, information about a company employee), but each system will host different types of information for the entries. Think of the difference between the information contained in a Human Resource database as opposed to the employee information compiled by the Information Technologies (IT) department. As each of the systems gather data about a particular entity, there is an acute need for one product to integrate the various systems and link together their pertinent, authoritative information.
Meta-Directory joins dissimilar data repositories into a single LDAP database so you can effectively manage, modify, and search the information that is distributed among different directory and database systems. With Sun ONE Meta-Directory, you can create an “Enterprise LDAP Directory” that you can use as the central point for directory access and administration.
Historically, it has been extremely difficult to manage the data contained in differing data repositories due to dissimilar formats. Directory information stored in systems such as e-mail applications, human resources databases, various relational databases, and online directories makes it difficult to update and maintain the information for any one particular entity. The authoritative data source for a particular user attribute may exist in any one of many different user directories.
In a frequently repeated scenario, the Windows NT security accounts manager (SAM) stores account information for Windows users, the Network Information Server (NIS) stores user account information for UNIX users, a human resources database will likely store specific information for employees and contractors, the payroll database is maintained in SQL, the facilities database stores employee building information, and the PBX system is the definitive source for employee phone numbers.
The Sun ONE Meta-Directory Solution
Meta-Directory integrates the disparate directory systems within an enterprise so their joined information can be accessed and managed from a single location, the Meta View. The Meta View is contained in an LDAP directory that is hosted by an instance of Sun ONE Directory Server.
Meta-Directory creates an enterprise LDAP directory that contains a concentrated “view” of the external data repositories that it links. Since the Meta View is LDAPv3-compliant, the directory overcomes the limitations of system-specific directory name spaces. This integration provides functions and capabilities that give directory planners the flexibility they need to maintain and upgrade their existing enterprise directory structure.
The Meta View is a fully-functional Directory Server database. Using using the API built into LDAP, you can create applications to access the information stored in the Meta View. In fact, all features available in Sun ONE Directory Server (access control, data back-ups, and so on) are available in the Meta View.
The Meta-Directory’s Meta View combines diverse details about a data entity into a single LDAP directory entry. This provides a centralized system of gathering information on an entity that may have different details scattered throughout multiple data repositories. Meta-Directory can copy data from one data repository to another data repository. During this process, Meta-Directory controls information flow, including what to copy, and where and when to copy it. You can update all of the records for a single entity either through the Meta-Directory Meta View or through the individual data repositories.
In addition to unifying systems, you can use Meta-Directory to restructure the architecture of your enterprise directory system by combining and integrating legacy systems into state-of-the-art LDAP directories. By integrating these systems, you have greater control, flexibility, and access to the information stored in each directory.
An Example Application
Suppose an organization has information for one of its employees, Micki Guzman, in a number of different data repositories (for example, a human resource database, an e-mail system, and IS directory system). Not only would there be a lot of duplicate information on Micki between the systems, but the job of managing the changes rests with multiple administrators across the organization. Changing the telephone number or job title of Micki Guzman would require administrators to change records in each system on which Micki is registered. On top of this, finding the authoritative value for one of Micki’s attributes (an e-mail address, for example) can be time consuming and resource intensive.
With Meta-Directory, the details for Micki Guzman are stored in a single entry in the Meta View, which presents a single view of all her directory attributes. Using the Meta View, you can view and manage all of Micki Guzman’s attribute values from a single location. Modified details are propagated back to each of the data repositories. Likewise, changing attribute values in one system will propagate, through Meta-Directory, to all connected systems.
Synchronizing and Joining Entries
Through the process of synchronizing and joining, Meta-Directory integrates and unifies directory information maintained in the different directory systems implemented across an enterprise. With Meta-Directory, directory entries are unified into a single, common LDAP directory.
Figure 1-1 illustrates the difficulty of accessing data that is stored in several different data repositories. The figure is a simplified look at a problem that faces many organizations. In this simple scenario, there are three databases that store different information about a singe object, a person in the company. In this case, if a user wants to get the phone number, the location, and the email address of an employee, they must search though an assortment of different database systems.
Figure 1-1 Manual Data Synchronization Without Meta-Directory
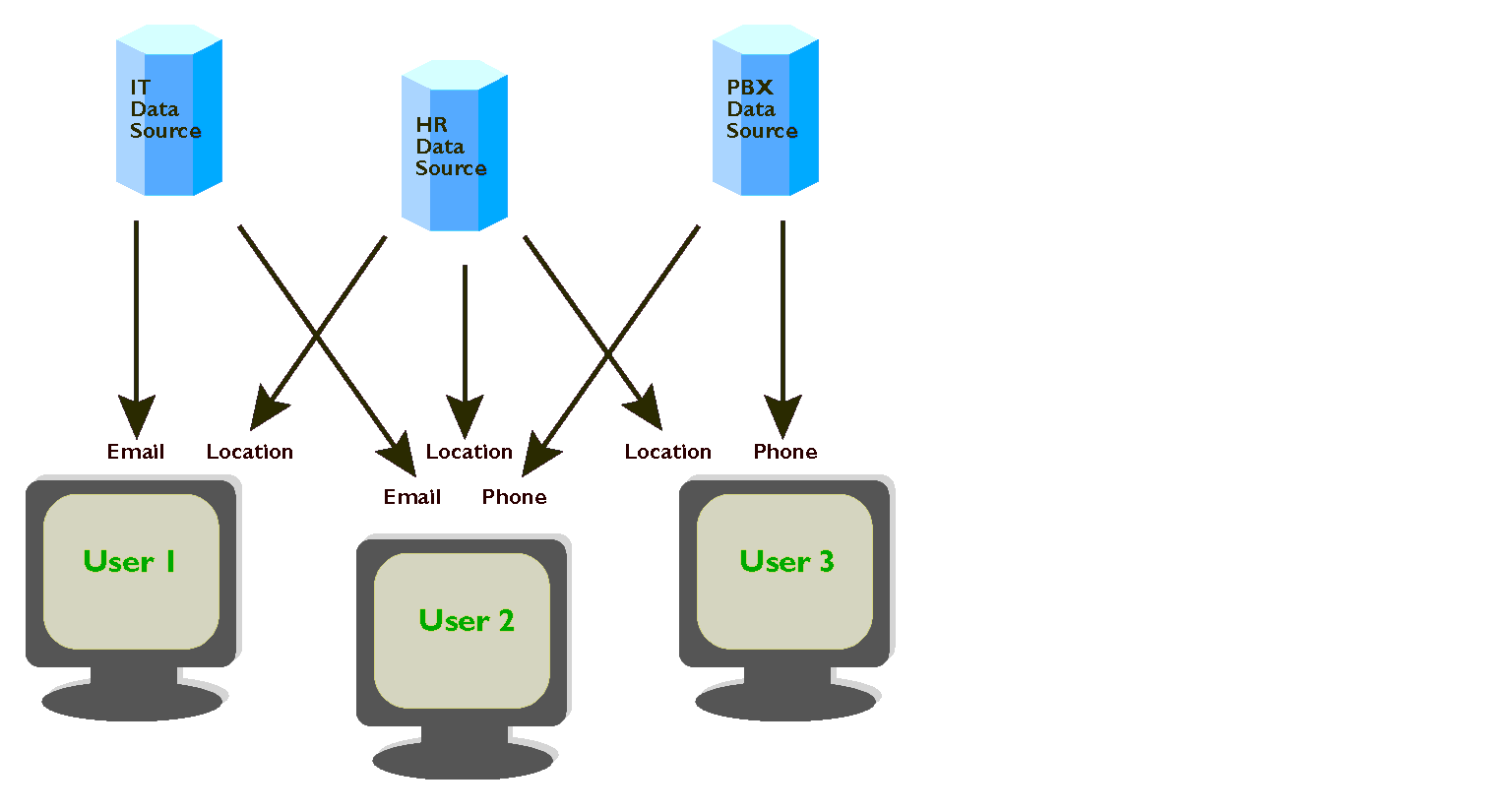
Figure 1-2 shows the highly automated data flow implemented in the Meta-Directory join process. Meta-Directory serves as the central repository and propagation facility for commonly updated user attributes. Here, users are able to query a single LDAP database (the Meta View) to obtain information associated with a user. With Meta-Directory, users are assured that the information they are retrieving is the “authoritative” information for that user. Without Meta-Directory, a user would have to query several different databases, possibly retrieving several pieces of conflicting information.
Figure 1-2 Automatic Data Synchronization Provided by Meta-Directory
Through the Meta-Directory synchronization process, a copy of the entries stored in an external database is provided in a LDAP format. Meta-Directory provides a “view” of the external data in what is known as a Connector View. The Connector View contains information from an external data source after it has been mapped into LDAP format.
The Meta-Directory join process completes the unification of synchronized user entries by joining the entries in the central LDAP repository (the Meta View). The join process is managed by the Meta-Directory join engine which, through the join rules you write, synchronizes information from the authoritative data source for each of the joined attributes. The join engine is also able to propagate changes made in the Meta View back to the external data sources.
The join engine accomplishes the synchronization and joining by linking entries in the Meta View with those in the participating Connector Views.
The specific information contained in the Meta View (the attribute values for each entry) is configured when you set up the join process. You control the information contained in the Meta View by specifying which attributes to accept or reject from each external data source. In addition, you configure which external data sources can accept changes made in (or propagated through) the Meta View.
A Meta-Directory Deployment
Successfully deployed, Meta-Directory provides a consistent view of all directory databases in the enterprise. As shown in Figure 1-3, Meta-Directory leverages the Sun ONE Directory Server, which it uses to store component configuration data and the Meta View itself. The Directory Server also provides user authentication, access control to directory data, and replication and referral services.
In this figure, the join engine and the Meta-Directory console configuration are stored in one directory information table (DIT), while the Meta View (the unified LDAP directory) is stored in another DIT. Connector views (LDAP copies of foreign directory data) may be combined in one directory instance or maintained in separate instances, depending on the directory requirements. All Meta-Directory components, including the Connector Views that participate in the Meta View, are administered as one server group through the Sun ONE Console.
Figure 1-3 The Meta-Directory Solution
The following sections explain in more detail how the Meta-Directory components interact and work with each other. The Meta-Directory configuration process (setting up the Meta View, the join engine, the directory connectors, and Connector Views) is fully explained in the Sun ONE Meta-Directory Administration Guide.
Sun ONE Meta-Directory ComponentsSun ONE Meta-Directory works in conjunction with Sun ONE Console, Sun ONE Administration Server, and Sun ONE Directory Server. You use Sun ONE Console to manage the different Sun ONE server groups that you have installed in your Meta-Directory system. You use Sun ONE Administration Server to administer instances of Sun ONE Directory Server and any installed Meta-Directory components. You use Sun ONE Directory Server to provide support for the Meta-Directory configuration files and to provide the directory instance for the populated Meta View.
With the mixing and matching of these software products and components, it can be difficult to draw a distinct line where one product ends and another begins. However, simply put, Sun ONE Meta-Directory consists of the following components:
Sun ONE Meta-Directory Console
The Meta-Directory console provides a graphical user interface (GUI) that you use to configure Meta-Directory components and manage the flow of information to and from the Meta View and Connector Views.
The Meta-Directory console contains both left and right panes. The left pane displays a navigation tree, which uses icons to represent the components installed in your Meta-Directory system. When you select a particular Meta-Directory component in the navigation tree, an interface to a set of administration tasks displays in the right pane of the console. Refer to the Sun ONE Meta-Directory Administration Guide for detailed information on managing the Meta-Directory components through the Meta-Directory console.
Sun ONE Console and Sun ONE Directory Server Console
In addition to the Meta-Directory console, you will also be working with the Sun ONE Console and the Sun ONE Directory Server console.
The Sun ONE Console
The Sun ONE Console is used to administer the Sun ONE server groups that you have installed. A server group is an installed set of Sun ONE servers that are administered by a single Sun ONE Administration Server. It is likely that you will have more than a single Sun ONE server group, with each server group being installed into a separate directory structure. For example, if you install Sun ONE Directory Server into one directory structure and Sun ONE Meta-Directory into another, they will each be represented in the Sun ONE Console as different server groups.
An Sun ONE Administration Server is installed into each server group. Sun ONE Administration Server allows remote administration through the Sun ONE Console, including the ability to view and modify Meta-Directory component configurations, start and stop agents, and view component status. For more information on the Sun ONE Console, refer to the Sun ONE Console and Administration Server 5.2 Server Management Guide, which can be found at the following Sun ONE web site:
http://docs.sun.com/db/prod/s1.ipconsole.2
In addition to administering server groups, you also use the Sun ONE Console to access both the Meta-Directory console and the Directory Server console. From the Sun ONE console, double-click the Directory Server icon or an icon for a Meta-Directory component to display the associated product console.
The Directory Server Console
Before you install Meta-Directory, you must first install Sun ONE Directory Server. Directory Server has its own console, the Sun ONE Directory Server console. Centralized LDAP directory administration services—including access control, authentication, backup, and replication—are implemented using the Sun ONE Directory Server console. For more information about the Directory Server, the Directory Server console, and LDAP, refer to the Sun ONE Directory Server Administrator’s Guide and the other documents located at the Sun ONE Directory Server web site:
http://docs.sun.com/db/prod/s1dirsrv
The Join Engine and the Meta View
The core service of Meta-Directory is the join engine, responsible for managing and controlling the flow of information into and out of the Meta View. Its job is to maintain the Meta View by synchronizing its information with the external data repositories.
The Join Engine
The join engine uses a configurable sequence of searches to automatically join (or link) entries in external data repositories with corresponding entries in the Meta View. These searches are called rule sets, which consist of ordered sets of rules that you configure. When information from an external data repository is propagated to the Connector View, the join engine “links” that information with the corresponding entry that exists in the Meta View, if it is configured to do so.
In addition to joining participating Connector Views into the Meta View, the join engine is also responsible for controlling the flow of information from the unified Meta View to external data sources.
Meta View Services
In addition to containing the joined data of the participating directories and databases, the Meta View provides the following centralized directory services:
- Incremental updates. External directories and databases can be updated incrementally as they are modified in the Meta View.
- Object modification. The Meta View can reflect modifications made to an entry in an external directory or database.
- Object creation. Objects in external directories and databases can be created from the Meta View.
- Object deletion. Objects can be deleted from the Meta View and from the external directory or database, depending on entity ownership.
Connectors and Connector Views
Connectors provide to the join engine the data contained in an external data source. The data is provided in the form of a physical directory, called the Connector View. Once a connector populates a Connector View, the join engine can flow the data to the Meta View. There are two types of connectors: indirect and direct.
Indirect Connectors
An indirect connector provides an LDAP-based copy of the entries that reside in an external data repository. The indirect connector presents the information in a corresponding Connector View. The join engine communicates with a Connector View over LDAP and consolidates this information into the Meta View.
Using the Meta-Directory Universal connector, indirect connectors convert data contained in an external data repository into LDAP. The LDAP copy of this data is stored in a Connector View that is hosted by Sun ONE Directory Server. The join engine can then link the entries in the Connector View with the entries contained in the Meta View.
Meta-Directory 5.1.1 provides the following indirect connectors:
- The Universal Text Parser (UTP) is a text-file processor that parses and generates ASCII text files. Using the Universal Text Parser, you can build indirect connectors that interface with text-based data sources, such as an application that outputs a comma-separated value text file.
- The NT Domain connector provides bidirectional synchronization of user and group data from a Windows NT SAM database into a Connector View.
- The Active Directory connector provides bidirectional synchronization of user and group data from an Active Directory database into a Connector View.
- The Microsoft Exchange connector provides bidirectional synchronization of user and group data from a Microsoft Exchange database into a Connector View.
- The Novell Directory Connector provides bidirectional synchronization of user and group data between a Novell directory server and a Connector View in Sun ONE Directory Server.
- The Lotus Notes Connector provides bidirectional synchronization of user and group data from a Lotus Notes address book into a Connector View.
An indirect connector asynchronously copies entries between the external data repository and its corresponding indirect Connector View, as shown in Figure 1-4.
Figure 1-4 Indirect Connector Views
Directory Change Notification System
The Directory Change Notification System (DCNS) is a service provided by Meta-Directory as a shared library. The join engine and Universal Connector use DCNS to detect changes in indirect Connector Views and in the Meta View. The Meta-Directory components also uses this service to provide change notification to the connected data sources that can accept notifications.
DCNS relies on the change log files that are generated by the Directory Server instances that host your Meta-Directory views. Without the DCNS service, the join engine and your connectors would not be able to react to the changes made to any of the Meta-Directory views. If the change log is not enabled, the DCNS will be unable to function and the error message mds_controller_unavailable will be written to the Meta-Directory logs.
Direct Connectors
The join engine communicates directly with external data sources that format their data using the LDAP protocol (such as Sun ONE Directory Server). Because of this, the join engine forms a direct connection with applications that provide data in LDAP format. In addition to LDAP, the join engine also “speaks” SQL. With this, the join engine can also form a direct connection with SQL-based data sources.
The LDAP and SQL direct connectors are actually a part of the join engine. Because the join engine can directly connect to LDAP and SQL data repositories, Meta-Directory does not require a separate connector component to copy the data into an LDAP-based Connector View. Instead, the join engine provides a direct “view” of the data that resides in the external data repository. With the LDAP and SQL direct connections, the join engine is able to synchronously access entries in both the Meta View and the Connector View that resides on the external data source. Note: Oracle connector uses the o=netscaperoot to act as an object cache, so deployments using Oracle direct connector may consider special attention to the location of this directory instance.
The Meta-Directory direct connectors are shown in Figure 1-5.
Figure 1-5 Direct Connectors
How Meta-Directory WorksTwo types of services integrate information from different data repository systems into and out of Meta-Directory:
These services act upon data created and stored within two types of Meta-Directory views: the Meta View and the Connector Views.
How Connectors Work
While there are inherent differences between direct and indirect connectors, they both perform the same basic function: connectors allow the join engine to synchronize entries between the Meta View and the disparate Connector Views. With direct connectors, the associated Connector View is located on the external data source. On the contrary, indirect connectors must first flow data to an LDAP-based Connector View before the join engine can synchronize data.
Figure 1-6 shows the process of transferring information between external data repositories, the connectors, and the Meta View. Note that LDAP and SQL data repositories do not use a connector component to populate the associated Connector View.
Figure 1-6 Meta-Directory Component Overview
With direct connectors, the join process rules that you define are enough to synchronize data between the external data source and the Meta View. However, with indirect connectors, you need to configure a separate set of indirect connector rules to define what attributes should flow between the external data source and the indirect Connector View. Once the entries are in the Connector View, the join engine can link them to the Meta View.
Indirect Connector Rules
When you configure indirect connectors, you specify the entries and attributes that should flow between an external data source and its associated Connector View using indirect connector rules. Indirect connector rules consist of the following rule sets:
- Attribute flow rules specify which attributes should be synchronized between the external data source and the Connector View. With attribute flow rules, you specify attribute name mapping, attribute filtering, and modification propagation.
- Default value rules specify attribute values to use for a destination value when the value of the source attribute is empty or when the source attribute itself is not present.
- Filtering rules specify particular domains, containers, or user entries to include or exclude from the synchronization process.
However, these rules are not supported by the Novell Directory Connector and Lotus Notes Connector. It is recommended that the same features are achieved via the "Attribute Construction" and "Filters" features of the Join-Engine configuration when the Connector View corresponding to either a Novell Directory Connector or Lotus Notes Connector is enabled as a predicating view and configured wrt the Join-Engine.
Indirect connector rules are similar to the join process rules used by the join engine (which are described on "The Join Process Rules"). However, while the join engine uses its rule sets to determine what flows between the Meta View and the participating Connector Views, connectors use attribute flow rules to determine what should be synchronized between an external data source and the indirect Connector View.
Attribute Flow Rules
With attribute flow rules, you specify the actual attributes that you want to synchronize between the external data source and the Connector View. In addition, attribute flow rules specify how modifications flow between the views.
Attribute flow rules specify the following:
- Attribute name mapping specifies how attribute names are mapped between the external data source and the Connector View. You control both how the names are mapped from the external data source to the Connector View and how they are mapped from the Connector View back to the external data source.
- Attribute filtering specifies which attributes will flow from the external data source into the Connector View. Attribute filtering works one way in that Meta-Directory does not filter any attributes output by the Connector View to the external data source; all attributes contained in the Connector View will be flowed out to the external data source.
- Modification propagation specifies how modifications to attributes are handled. Depending on the attribute flow granularity, modifications to existing data can be restricted to the owner of the object or they can be allowed by either the external data source or the Connector View.
Attribute Name Mapping
Attribute mappings specify attribute names and they specify how attributes should be matched between two different data repositories. When you define attribute flow rules, you map the attributes from one data repository to another. For example, you might specify that an external database field LastName will map into the indirect Connector View attribute sn. If you are flowing data to an external data source, you can also specify how the attribute names will map from the Connector View to the external data source.
Because an indirect Connector View is an LDAP DIT, information stored in a Connector View must conform to a declared LDAP schema. Because of this, all attribute names must be conform with the schema that is loaded into that view. In contrast, an external database will likely contain data fields that do not conform to an LDAP schema. Attribute name mapping ensures that the attribute names are correctly named between the two data sources.
For example, Table 1-1 shows possible external database field names and the names that they could be mapped to in the Connector View, (the Connector View attribute names are part of the LDAP schema inetOrgPerson):
Table 1-1 Sample Name Mapping
External Database Field Name
Mapped Connector View Attribute Name
LastName
sn
Firstname
givenname
FullName
cn
Position
title
PhoneNumber
telephoneNumber
In this example, when flowing entries between an external data source and the Connector View, the attribute LastName in the external data source maps to the attribute name sn in the Meta-Directory Connector View. Once mapped into an LDAP schema, the attribute sn can be propagated to the Meta View, which is also stored in LDAP format.
Attribute Filtering
Attribute filtering controls the flow of object attributes from an external data source to its associated Connector View. When you map the attribute names from the external data source to the Connector View, you specify only those attributes whose values you want to flow to the Connector View. External attributes whose names you do not specify will not be flowed to the Connector View.
Attribute filtering is a one-way filter, it filters only the attributes that will be flowed to the Connector View from the external data source. If you are flowing data out of the Connector View back to the external data source, no filtering will take place; the Connector View will flow all the data that it contains. You control the filtering at this stage through the import function of your external data source.
Modification Propagation
Modification propagation specifies how modifications to existing data will be propagated between the Connector View and its associated external data source.
Modification propagation is determined by the attribute flow granularity, which is defined as follows:
Meta-Directory uses the defined attribute flow granularity to determine how it will propagate entries that contain modified attribute values. If a Connector View has entry-level granularity defined, then Meta-Directory will only flow the entries whose data was modified by the source that owns the entry (Meta-Directory will not flow a modified entry if the entry was modified by a data source other than the one that created it). However, if you have defined any attribute flow rules for the Connector View, then attribute-level granularity prevails and Meta-Directory will flow all modified entries between the Connector View and its associated external data source, regardless of who owns the entries.
The Novell Directory Connector and Lotus Notes Connector require the user to always select one of the attribute flow rules (the preset rules or user-created custom rules). Hence, there is no support for entry-level granularity.
Object Class Flow Rules
The Novell Directory Connector and Lotus Notes Connector use object class flow rules to specify the mapping between external data source object classes and the corresponding Connector View object classes. Novell Directory Connector and Lotus Notes Connector provide a single preset configuration for Object Class Flow:
By default "Object Class Set for Default Schema" is selected as the "Object Class Flow Configuration". In addition to the preset object class flow configuration, you can also create new/custom object class flow rules manually. This allows you to flow entries belonging to any object class (not just those corresponding to user and group) in both directions.
For more details, see the sections - "Object Class Flow", "To add Object Classes for Novell Directory connectors", "To add Object Classes for Lotus Notes connectors" and "To Configure an Object Class Flow Rule" in the Sun ONE Meta-Directory Administration guide.
Default Value Rules
A default attribute value is a pre-configured value that Meta-Directory will use in a Connector View if an entry in the external data source has no value for the corresponding attribute, or if the attribute has no value.
When updating a Connector View or external data source, Meta-Directory updates all attributes or fields in the external directory that have associated values. Normally, if an field has no value in the external directory, it is not added to the Connector View, and vice versa. To make sure that the Connector View or external directory contains appropriate attributes and values, you can define a default attribute value to use with a particular attribute or field.
For example, if the PhoneNumber field in an external data source has no value, but you want the telephoneNumber attribute in the Connector View to contain a valid phone number, you can specify a default attribute value (such as the main office telephone number) to be used in the Connector View whenever the field is empty or missing in the external data source.
Filtering Rules
By default, all entries in both the Connector View and the external data source are included in the synchronization process. However, you can set up filters to designate that particular entries are to be included or excluded from the synchronization. With filtering rules, you have the control to specify which level of a directory tree you want to include (or exclude) from the synchronization process. Within that tree, you can then exclude (or include) specific groups of entries.
How the Join Engine Works
The Meta-Directory join process, which the join engine performs, is the key to unifying directory and database entries into the Meta View. The join process links entries that exist in each of the Connector Views with an entry in the Meta View. A link between an entry in the Meta View and the entries in one or more Connector Views allows attributes to flow between the views.
The outcome of the join process depends on the join engine applying the sets of join process rules that you define. After the join process occurs, entries between the views are either linked or not linked, depending on how well they match the criteria defined in your join process rules.
When creating the join process rules, you have a lot of flexibility in determining which entries become linked between the different views. In addition, many elements of the join engine configuration are shared between views, making it easy to administer the rules that are shared between Connector Views.
The Join Process Rules
When the join engine synchronizes one view with another, it uses a set configuration settings, or join process rules, to determine the correct join and data flow. The following join engine settings are configurable from the Meta-Directory console:
Join rules enable you to specify the rules for joining entries between a Connector View and the Meta View.
Attribute flow rules enable you to specify which attributes should be propagated between a Connector View and the Meta View.
Filters enable you to include or exclude entries from a Connector View by a subtree or a specific entry in a subtree. With filters, you specify groups of entries that you want to include or exclude from the Connector View.
Distinguished Name (DN) mapping rules let you specify where you will map entries between a Connector View and a Meta View. Using DN mapping rules, you create an RDN under a Connector View or Meta View which you can populate with data. You can also create a DN mapping rule to calculate the primary key of an Oracle table.
Constructed attributes enable you to create attributes in entries stored in the Meta View or Connector View by combining and manipulating entry information.
A general description of these items is given in the sections below; for complete information on how to configure these items, refer to the Sun ONE Meta-Directory Administration Guide.
Join Rules
Join rules specify which entries will be linked between the participating Connector Views and the Meta View. When Meta-Directory applies the join rules, the result will be a one-to-one correspondence between the entries that are linked the respective views. If a join rule is applied against a view, and the rule results in more than one candidate entry being selected from a view, no entries will be joined (links between views cannot be one-to-many).
Filters can be built to select an entry, or set of entries, from the opposing view. A filter is an LDAP search rule (or an SQL query) that when applied against a meta or Connector View, result in a set of entries being selected to flow to the opposing view.
Join rules are applied in sets. When creating your join rules, you will add individual rules in a particular sequence to form a join rule set. A join rule set specifies an ordered list of join rules that are sequentially tested until either an individual join rule identifies a single entry or until all rules fail.
Each rule in the join rule is fully evaluated, one rule at a time, until a rule returns one or more entry matches. If the evaluation of a join rule results in more than a single candidate match, then no entries will be joined by that rule. In addition, no entries will be joined if the evaluation of the entire join rule set fails to match any entry. In each of these cases, you can manually join specific entries using the Fix-It Tool. See "Manually Joining Entries" for more information.
Attribute Flow Rules
Passing data from an external data source, through a connector to a Connector View, and to the Meta View is known as flowing data. You specify the authoritative attributes, those that flow to the Meta View, using attribute flow rules. Attribute flow rules enable you to specify the specific data source for each of the attributes represented in the Meta View. They also let you specify which external data repositories can be modified when an entry or attribute value changes.
Attribute flow defines the flow of attributes between Connector View and Meta View entries. An attribute flow rule lists the attributes that flow between two linked entries and provides pairs of source/target attribute names.
Multiple attribute flow rules may be grouped together into an attribute flow set. The join engine scans through the attribute flow set and selects the first attribute flow rule that matches the selection criteria. The join engine then applies all the attribute flow pairs from the selected rule.
Attribute flow sets provide ordered sets of rules that the join engine scans until it finds a match in the Connector View or Meta View it is searching. Each rule set is applied in order until a valid rule is found.
Types of Attribute Flow
The selection criteria for attribute flow is based on two types of attributes: entry attributes and context attributes. While entry attributes deal strictly with the source entry and the target entry, context attributes are involved with the context of the operation the join engine is performing. Context attributes are based on a selection of items from the following list:
Entry Ownership and Membership
The ownership and membership of entries are key concepts when working with the propagation of changes through Meta-Directory. The join engine updates entries based on entry ownership. Entry membership allows the join engine to work with sets of entries.
Entry ownership dictates the way the join engine decides which data source has ultimate control over an entry. Entry ownership is configurable from the Meta-Directory console—using the console, you specify who will own the entry when the entry is created in one of the Meta-Directory views.
The ability to delete an entry from a view (either the Meta View or a Connector View) depends on who “owns” the entry. If a view does not “own” an entry, and you delete the entry from that view, the entry will be added back to the view during the next synchronization process.
In Meta-Directory, it is possible to have a Connector View that contains data from a variety of data sources. Membership identifies an entry within a Connector View that is native to the data source represented by that Connector View. Rules can then be configured and applied based on the attributes that are already present in the data source. Membership can be used to control the flow of attributes to and from a view. Membership can also be used when you create selection criteria rules. For example, you can specify that only members of a view can flow from that view to other views, or that a view will take modifications only if the object being modified is a member of that view.
Filters
Filters are used to explicitly include or exclude entries within specific directory subtrees during synchronization. Filters enable you to configure the Meta View or Connector View to exclude specific subtrees or entries from the unification process.
Distinguished Name (DN) Mapping Rules
Distinguished Name (DN) mapping rules identify where to create a new entry in the destination view (either the Meta View or a Connector View) given a source entry. The input into a DN mapping rule is the source entry, and the result is a partial DN, which the join engine concatenates with the view location DN to produce a fully qualified DN. The DN mapping rule actually creates an RDN for a specific entry, placing it in the appropriate place under the root of the associated Meta View or Connector View.
Multiple DN mapping rules may be grouped into a DN Mapping Rule Set to allow for an ordered testing of rules. These rules can be defined differently for entries originating from each different Connector View connected to Meta-Directory.
Constructed Attributes
The term constructed attribute refers to the broader scope of any additional attribute that is not explicitly part of a source entry, but that may be derived in a target entry given source data. A simple example would be as follows: if a user has an attribute “state equals New York,” a constructed country attribute of “country equals USA” can be created.
The real functionality of constructed attributes comes into play when you use them in the creation of attribute flow settings. You can use constructed attributes in the join rules you write, giving you flexibility when flowing data between two data sources.
Manually Joining Entries
When you add, delete, or modify an entry in a Connector View, a search is performed on the Meta View for a matching user entry using the configured join rules. If a match is found, a link is made between the two views and any changes made to the entry in either view will be reflected in the other view (of course, depending on the attribute flow configurations).
For example, if an entry for the user David Lewis appears in the Human Resource’s database Connector View and the join engine links the David Lewis entry in the Meta View, user information for David Lewis may be modified in the Meta View. Likewise, any Human Resource database attribute changes for David Lewis that are made in the Meta View will flow to the Human Resource database.
However, if while evaluating a join rule, the join engine returns more than a single candidate entry, the join will fail (joins can only exist between a single entry in the Meta View and an associated Connector View). For example, if a join rule links entries based on the sn attribute, and there happens to be two entries in the Connector View that have the same sn attribute, the join rule will return multiple candidate entries after processing the rule. Because of this, it is possible for an entry to be left out of the join process. Using the Query Fix-It Tool, you can manually link entries that your join rules miss.
It’s good practice to examine the Meta-Directory logs after each synchronization cycle to ensure that no entries were left out of the synchronization cycle. If you find that the cycle missed an entry, you can use the Query Fix-It Tool. The Query Fix-It Tool enables you to manually control the joining process. With this tool, you can link, exclude, unlink, or create entries on an individual basis. For information on using the Query Fix-It Tool, refer to the Sun ONE Meta-Directory Administration Guide.