Chapter 8 Using a Multi-Federation Protocol Hub
The Multi-Federation Protocol Hub enables you to use multiple single sign-on protocols such as SAMLv2, IDFF1.2, or WS-Fed together within a circle of trust. In OpenSSO Enterprise 8.0, the Multi-Federation Protocol Hub is supported only at the Identity Provider. The Identity Provider can be configured to support multiple Service Providers, with each Service Provider using a different federation protocol. The session is shared across these heterogeneous protocols, providing single sign-on and single logout within the circle of trust.
The following topics are included in this chapter:
About Identity and Web Services Federation Protocols
Sun OpenSSO identity federation is based on the Liberty Alliance specification which includes the Identity Federation Framework (ID-FF) and SAMLv2 protocols. Microsoft Active Directory Federation Service (ADFS) is based on the Web Services Architecture specification which uses the Microsoft Web Browser Federated Sign-On (MS-MWBF) and Web Services Federation (WS-Federation) protocols. OpenSSO Enterprise provides support for MS-MWBF so that single sign-on can work among OpenSSO and ADFS-based environments. For more information about identity and web service federation protocols, see the Sun OpenSSO Enterprise 8.0 Technical Overview.
Analyzing the Deployment
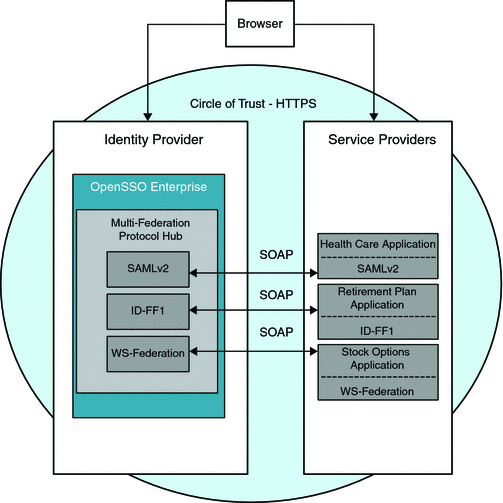
The typical configuration for Multi-Federation Protocol Hub requires one OpenSSO Enterprise instance as an Identity Provider, and two or more OpenSSO Enterprise instances as Service Providers. In this deployment example, the Multi-Federation Protocol Hub is configured with three different Service Providers. Each Service Provider uses a different federation protocol to connect to a single OpenSSO Enterprise instance. Single Logout occurs through a browser redirect when the HTTP post profile is used. If the SOAP binding is used, then a direct SOAP request is sent from the Identity Provider to the Service Provider.
The following illustration illustrates the major components that are involved in the Multi-Federation Protocol Hub.
Figure 8–1 Deployment Architecture for the Multi-Federation Protocol Hub
Considering Assumptions, Dependencies, and Constraints
The following are issues you must resolve before choosing to use the Multi-Federation Protocol Hub.
Constraints
The Multi-federation Protocol Hub in OpenSSO Enterprise can be configured with only the following federation protocols:
-
SAMLv2
-
Liberty ID-FF1
-
WS-Federation
The Multi-Federation Protocol Hub in Open SSO Enterprise 8.0 is only supported on the Identity Provider configuration.
Assumptions and Dependencies
-
Single Logout over HTTP post profile must be supported by the Service Providers running HTTP.
-
Single Logout over SOAP must be supported by the Service Providers running SOAP.
Understanding Typical Business Use Cases
A company uses the following services and federation protocols to manage employee benefits:
-
Health Care Administration (SAMLv2)
-
Retirement Plan Administration (ID-FF1)
-
Stock Plan Administration (WS-Federation)
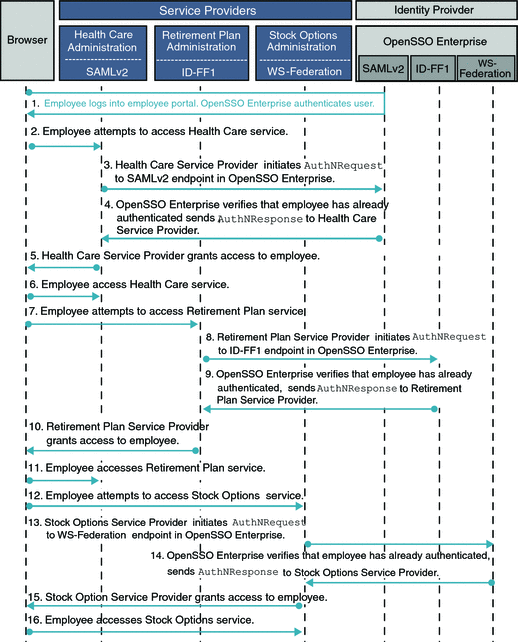
The company itself acts as an Identity Provider, managing employee information in its corporate user database. The Identity Provider enables employees to access any of the three Service Providers through an employee portal. The Health Care Service Provider uses the SAMLv2 federation protocol. The Retirement Plan Service Provider uses ID-FF1, and the Stock Plan Service Provider uses WS-Federation. The Identity Provider is configured as a Multi-Federation Protocol Hub and provides single sign-on and single logout across all these services.
The following figures illustrates a typical Multi-Federation Protocol Hub process flow.
Figure 8–2 Process Flow for Single Sign-On Using a Multi-Federation Protocol Hub
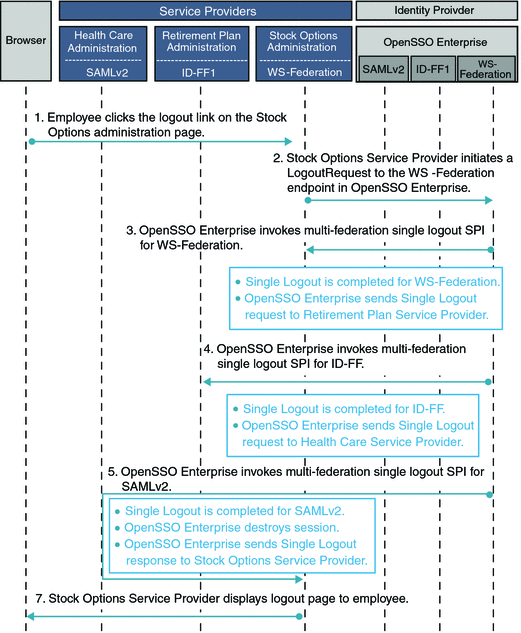
The following figure illustrates the process flow for Single Logout using the Multi-Federation Protocol Hub.
Figure 8–3 Process Flow for Single Logout Using the Multi-Federation Protocol Hub
Setting Up and Configuring a Multi-Federation Protocol Hub
The following information provides a high-level overview of setup and configuration instructions. Before you can begin, OpenSSO Enterprise must be deployed on a supported web container. You can configure the Multi-Federation Protocol Hub by importing the metadata using either the OpenSSO Enterprise administration console, or using the ssoadmin command-line interface. For detailed configuration steps, see the Sun OpenSSO Enterprise 8.0 Administration Guide. A code JSP file is contained in theopensso.war file. The sample JSP demonstrates how to configure a Multi-Federation Protocol Hub.
Using the Sample JSP
-
Install and deploy OpenSSO Enterprise instances on four separate host computers, one instance in each domain.
-
Locate the sample JSP on the Open SSO instance.
http://FQDN/opensso/samples/multiprotocol/index.html
-
Configure OpenSSO Enterprise instance 1 as a SAMLv2 Service Provider named SP1.
Run the sample JSP to create one hosted SAMLv2 Service Provider and one remote SAMLv2 Identity Provider in the same circle of trust.
-
Configure OpenSSO Enterprise instance 2 as an ID-FF Service Provider named Service Provider 2.
Run the sample JSP to create one host ID-FF Service Provider and one remote ID-FF Identity Provider in the same circle of trust.
-
Configure OpenSSO Enterprise instance 3 as a WS-Federation Service Provider named Service Provider 3.
Run the sample JSP to created one hosted WS-Federation Service Provider and one remote WS-Federation Identity Provider in one circle of trust.
-
Configure OpenSSO Enterprise instance 4 as an Identity Provider using the following protocols: IDP, referred as IDP1, IDP2 and IDP3 respectively.
-
SAMLv2 (Identity Provider 1)
-
ID-FF (Identity Provider 2)
-
WS-Federation (Identity Provider 3)
Run the sample JSP to create three hosted Identity Providers (one each for SAMLv2, ID-FF and WS-Federation), and three remote Service Providers (one each for SAMLv2, ID-FF and WS-Federation) the same circle of trust.
-
-
Run single sign-on from Service Provider 1 to Identity Provider 2, then from Service Provider 2 to Identity Provider 2 without logging in again, then Service Provider 3 to Identity Provider 3 without logging in.
-
Run single logout from Service Provider 1.
All sessions on Service Provider 2, Service Provider 3, and on all Identity Providers are destroyed.
-
Run single sign-on again, and then run single Logout from Identity Provider 1.
All sessions on Service Provider 1, Service Provider 2, Service Provider 3, and on Identity Providers are destroyed.
Evaluating Benefits and Tradeoffs
The Multi-Federation Protocol Hub feature in OpenSSO Enterprise enables the Identity Provider to integrate with any existing or future service provider or service partner. The Multi-Federation Protocol Hub achieves single sign-on and single Logout regardless of which federation protocol the service provider or partner uses. Without this feature, the Identity Provider has to force the Service Providers to use a single federation protocol.
With the Multi-Federation Protocol Hub only one circle-of-trust is required when using heterogeneous Service Providers and Identity Providers in the same circle of trust. Without this feature, you must set up and configure multiple circles of trust, one for each federation protocol used. The Identity Provider could require multiple OpenSSO Enterprise instances. Each OpenSSO Enterprise would have to act as an Identity Provider, and each OpenSSO Enterprise instance would require a different protocol. To achieve single sign-on and single Logout, you would have to install some kind of intelligent proxy in front of the Identity Provider. The proxy would have to be able to recognize the incoming protocol from the Service Provider, and route the request to the correct Identity Provider instance accordingly.
The Multi-Federation Protocol Hub configuration steps are simple. The only configuration required is one extra metadata file for each protocol to be supported by the Identity Provider.
- © 2010, Oracle Corporation and/or its affiliates
