| C H A P T E R 8 |
|
Security |
In general, the J2EE model assumes that security is set up at the module level. It assumes that component providers will consider security when designing and developing business logic. Many component providers will have a general idea of the user roles that will be accessing their business logic and which roles should be allowed to access which functionality.
The sections that follow show how to use the IDE to set up security for web modules, for EJB modules, and how to integrate the two when they are assembled into an J2EE application.
Suppose you are the component provider for a web module that works with human resources data. You probably know which web resources should be available to all employees for maintenance of their personal information, and which web resources should be accessed only by human resources clerical roles, by human resources supervisory roles, by auditing roles, and so on.
As the component provider and initial module assembler, you can set up generic security roles that represent these roles and map them to the web resources you create. These generic roles can later be mapped to the actual user names and group names in the application server environment. This mapping can be done at the application level, perhaps when the application is assembled, or perhaps later, when the application is deployed into the production environment.
There may be projects when you are the component provider and initial module assembler but you have no idea how security should be applied to your business logic. In these cases, you can defer setting up security roles to a later stage of the development process. For example, the application assembler can work with module-level deployment descriptors before assembling the modules into an application.
The sections that follow explain how to set up security roles at the module level and map them to web resources.
Declarative security for web modules consists of mapping security roles to web resources. To do this you need to:
2. Define the "web resources" you want to protect. Web resources are URIs in your module.
3. Map security roles to web resources. This gives the mapped roles permission to access the specified web resources.
You declare security roles on the Security Roles Property Editor. (To open this property editor, right-click on the web.xml node, and then choose the following sequence from the contextual menu: Properties  Security Tab
Security Tab  Security Roles
Security Roles  ellipsis (...) button.)
ellipsis (...) button.)
The Add button on the property editor opens a dialog that lets you declare a new security role; the Edit and Remove buttons let you work with roles that have already been declared.
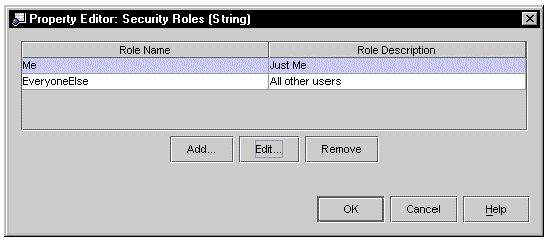
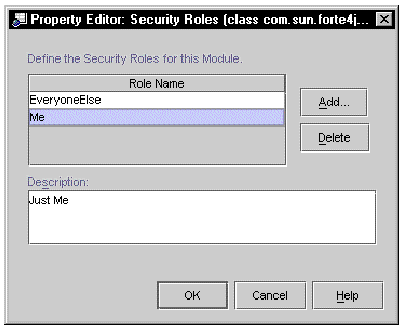
FIGURE 8-1 shows the Security Roles Property editor after two roles have been declared, Me and EveryoneElse.
 [ D ]
[ D ]You can both define web resources and specify the roles that are authorized to access them in the Security Constraints Property Editor. (To open this property editor, right-click on the web.xml node, and then choose the following sequence from the contextual menu: Properties  Security Tab
Security Tab  Security Constraints
Security Constraints  ellipsis (...) button.)
ellipsis (...) button.)
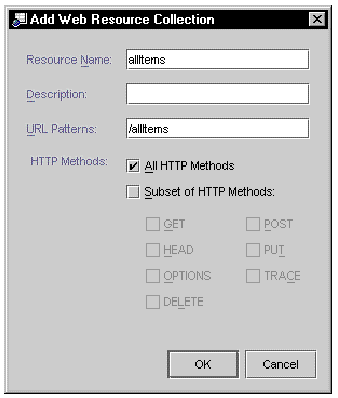
The Add button on the property editor opens a dialog on which you can define a web resource.
FIGURE 8-2 shows how to define the URL pattern /allItems as a web resource. (To see how this URL pattern is mapped to a web component see and .)
 [ D ]
[ D ]
Notice that you can choose to define the web resource as all of the HTTP methods associated with the URL pattern or a subset of them.
In addition to defining web resources, you can map the web resources that you define to security roles. After you complete this dialog, a summary of the information will be displayed on the Security Constraints Property Editor. FIGURE 8-3 shows the Security Constraints Property Editor after a web resource is set up under the name AllItems.
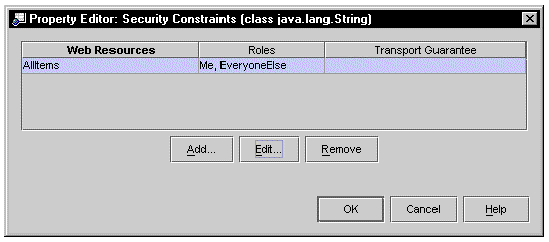 [ D ]
[ D ]
You can use the Edit and Remove buttons to modify any security constraint that appears on the property editor.
If any of the web components in your module use programmatic security, you need to map the security role references used in the security-checking code to the security roles declared at the module level.
Web components that use the programmatic security feature contain code that accesses the user's credential directly and perform verification beyond that which is performed by the container's declarative security mechanism. For example:
... context.isCallerInRole(roleRefMe); ... |
Since roles are defined at the module level, they are likely to be unknown at the time this component-level code is written. Therefore, the code uses a security role reference (roleRefMe) which is later mapped to an actual security role. You perform this mapping on the Edit Servlet dialog. Open this dialog by selecting a servlet that uses a role reference on the Servlet Property Editor and clicking Edit. FIGURE 8-4 shows this dialog, with the reference roleRefMe mapped to the role Me.
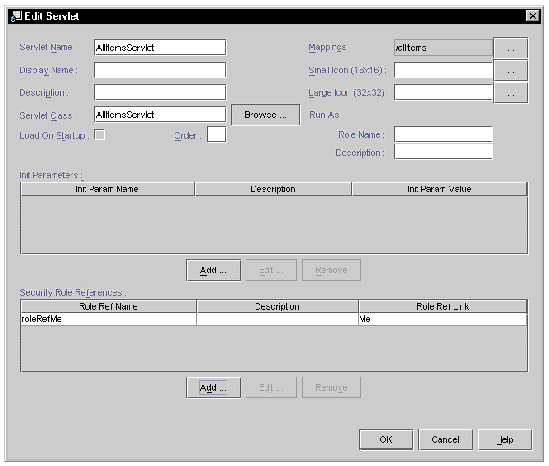 [ D ]
[ D ]
Notice that roles must be declared at the module level before you can perform this type of mapping.
Suppose you are a component provider. You have developed several enterprise beans that accesses human resources data and you are assembling them into an EJB module. You probably know which data should be available to all employees for maintenance of their personal information, and which data should be accessed only by human resources clerical roles, by human resources supervisory roles, by auditing roles, and so on.
As the component provider and initial module assembler, you can set up generic security roles that represent these roles and map them to the methods that access those data. These generic roles can later be mapped to the actual user and group names in the deployment environment. (This second mapping can be done at the application level, perhaps when the application is assembled, or perhaps later, when the application is deployed into the production environment.)
On another project, you are the component provider and the initial module assembler but you have no idea how security should be applied to your business logic. In these cases, you can defer setting up security to a later stage of the development process. For example, the application assembler can work with module-level security before assembling the modules into an application.
Setting up security for EJB modules consists of mapping security roles to enterprise bean methods. To do this you need to:
1. Declare generic security roles that represent the categories of users that can use the module's services.
2. Map these security roles to the module's enterprise bean methods. This determines which roles are allowed to access which methods.
3. If the module contains enterprise beans that use the programmatic security feature, map the security role references used in these enterprise beans to security roles.
The sections that follow explain how to perform these assembly tasks.
You declare security roles on the Edit Module Role dialog. (To open this dialog, right-click on the module node, and then choose the following sequence from the contextual menu: Properties  Security Roles
Security Roles  ellipsis (...) button. When the Security Roles Property Editor opens, click the Edit Module Roles button.)
ellipsis (...) button. When the Security Roles Property Editor opens, click the Edit Module Roles button.)
FIGURE 8-5 shows the Edit Module Role dialog after two roles have been declared, Me and EveryoneElse.
After declaring security roles for the module, you can give each role permission to execute a specific subset of the enterprise beans in the module. You do this on the Method Permissions Property editor. (To open this property editor, you work with the included EJB nodes. There are the subnodes of the EJB module.)
Right-click a node that represents an enterprise beans included in the module, and then choose the following sequence from the contextual menu: Properties  Method Permissions
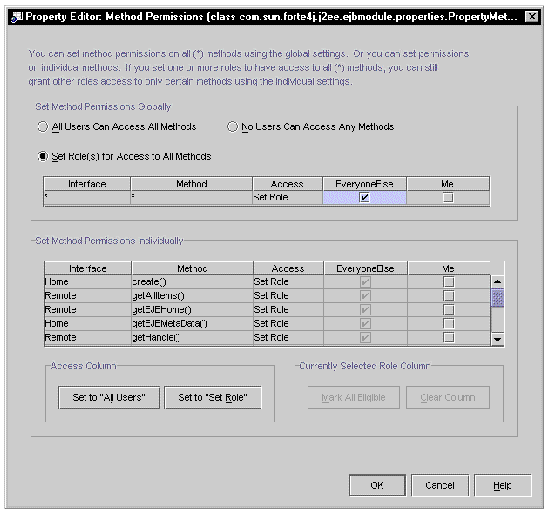
Method Permissions  ellipsis (...) button.) The property editor is a table, with a row for each of the enterprise bean's methods and a column for each security role that has been declared for the module. FIGURE 8-6 shows how the property editor looks with the two security roles declared in the preceding section.
ellipsis (...) button.) The property editor is a table, with a row for each of the enterprise bean's methods and a column for each security role that has been declared for the module. FIGURE 8-6 shows how the property editor looks with the two security roles declared in the preceding section.
 [ D ]
[ D ]
There are a number of ways to use this dialog.
This buttons below this table provide several shortcuts for editing in the table.
If any of the enterprise beans in your module use programmatic security, you need to map the security references used in the security-checking code to the security roles declared at the module level.
Enterprise beans that use the programmatic security feature contain code that accesses the user's credential directly and perform verification beyond that which is performed by the container's declarative security mechanism. For example:
... context.isCallerInRole(everyOne); ... |
Since security roles are defined at the module level, they are likely to be unknown at the time this enterprise bean code is written. Therefore, the code uses a security role reference (everyOne) which is mapped to an actual security role when you add the enterprise bean to a module. The role must be declared as a property of the enterprise bean. FIGURE 8-7 shows a role declared on an enterprise bean's Security Role Reference property editor. The role is unlinked.
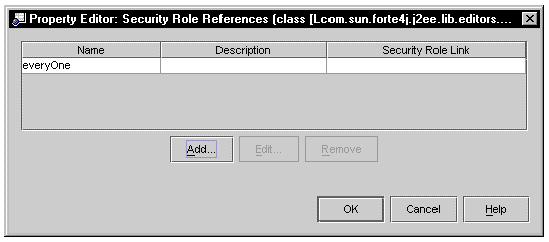
In this case, this role reference is mapped to a role at the module level. You perform this mapping on the module's Security Roles Property Editor. When you open this editor is shows all security role references in the module and indicates whether they are linked or unlinked. FIGURE 8-8 shows the editor with the everyOne reference still unlinked.
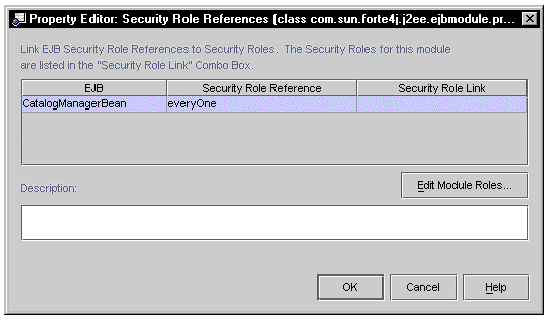 [ D ]
[ D ]
To map a reference, click in Security Role Link field and select a role. FIGURE 8-9 shows the property editor after the everyOne link has been mapped.
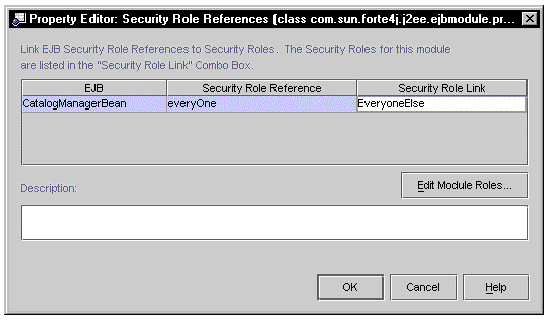 [ D ]
[ D ]The application assembler can find a newly assembled application in one of several states:
If additional mapping is needed, you do it on the application's Security Roles property editor. (To open this editor, right-click on the application node, and then choose the following sequence from the contextual menu: Properties  Security Roles
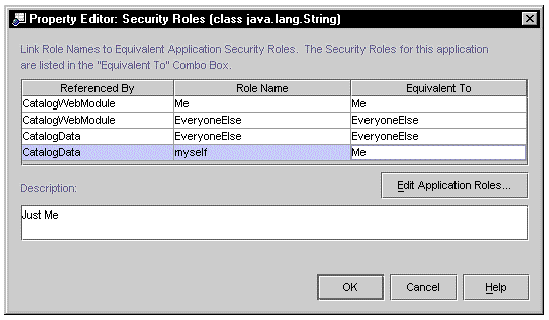
Security Roles  ellipsis (...) button.) FIGURE 8-10 shows this editor with security roles defined at the module level.
ellipsis (...) button.) FIGURE 8-10 shows this editor with security roles defined at the module level.
 [ D ]
[ D ]
The security roles declared at the module level appear in the first two columns of the dialog. Each role is identified by its module and name. For each module-level role, the IDE creates a default application-level role, which has the same name as the module-level role. The application-level roles are displayed in the Equivalent To column.
There are two ways to resolve role discrepancies with this editor. The example in FIGURE 8-10 shows an application with two modules. Each module has two security roles. There is one discrepancy; the web module has a role named myself and the EJB module has a role named Me. These roles are equivalent, so you would like to have only one application-level role. In the figure, this discrepancy was resolved by remapping the role myself to the role Me. What is actually happening here is that both module-level roles, Me and myself, have been mapped to the same application-level role, Me.
You can also create an entirely new role at the application level and map several module-level roles to it. Suppose one of the modules in your applications has a role named sa, and the other has a role named sadmin. You decide to resolve this discrepancy by creating a new application-level role named sysadmin. To do this click the "Edit Application Roles" button. This opens a dialog in which you can declare application-level roles.
After declaring the sysadmin role, you return to the Security Roles Property Editor. Remap both of the module-level roles by clicking in their "Equivalent To" column. This will display the application-level roles. Select the sysadmin role.
Copyright © 2002, Sun Microsystems, Inc. All rights reserved.