Chapter 2 Ensuring Security
It is a truism of the Internet that the network is insecure. The very nature of being connected means that you do not completely control the data you process. Because requests can come from outside your network, you need to know who is making the request. Because your data can be routed through many outside networks, you need to protect your network's integrity and privacy. This chapter discusses the security concerns in a Solaris ISP ServerTM installation, and how to maintain that security in a network connected to the Internet.
Specific information in this chapter includes:
Security Concepts
This section provides an introduction to security concepts and terminology. It is not intended as a complete tutorial on the subject. Many good books have been written on the subject. Please see this book's Failed Cross Reference Format for suggested reading on security.
Security Goals
The goals of a good security policy are simple to describe, if not to attain. They are to ensure that only authorized people gain access to the system, that communications on the network are kept private from outsiders, and that data being communicated is kept safe. The terms defined in this section are those commonly used to describe these security goals.
Authentication
Authentication is verifying that a person requesting access is who he or she claims to be. Knowing who is making a request for service, or is sending a piece of information, is crucial to the security of the ISP's system. Technology that provides authentication (such as what SunTM Internet AdministratorTM provides for administrators), assures the system that a message is coming from a trusted source, and not from an intruder pretending to be a legitimate user.
Any technology that requires a login before granting access is providing some user authentication. Signed certificates, which can be used with the SunScreenTM SKIP product, offer a strong form of authentication.
Authorization (Access Control)
Authorization ensures that a given (authenticated) person is allowed access to the requested system resources or data. Even legitimate users are not all allowed root access, for example.
Sun Internet Administrator provides access control, limiting the access of ISP administrators to only those services that they need to manage while doing their jobs.
Accountability
Accountability is the concept of knowing who performed what actions. This is not so much a security guarantee as a way of identifying the source of trouble and removing that user from the system. In Solaris ISP Server, accountability is achieved through a thorough logging of administrator actions. Be sure to examine (audit) the logs regularly to catch any questionable activity.
Privacy
Given the public nature of the Internet, the privacy of data on the wire is of prime importance. You need to know that an intruder cannot listen to communications and pick up user passwords to be used later to gain access to your systems. Data passed between computers must be protected from being read by unauthorized individuals.
Cryptography can ensure the privacy of network communications. The SSL technology in Sun WebServer provides encryption of information accessed over the Web. The SunScreen SKIP software provides encryption of all IP traffic between interfaces on your network.
Data Integrity
Integrity is knowing that the message sent by a legitimate user is identical to that received by the system, and that its content has not been altered along the way. Clearly this is a significant security requirement, given the potentially disastrous effects of an intruder adding dangerous code to the end of an innocuous message. These "Trojan horse" attacks can frequently be devastating.
Encryption of the data, particularly strong encryption coupled with signed certificate authentication, provides data integrity by making it practically impossible for an intruder to modify a legitimate user's message. SunScreenTM SKIP provides this technology in Solaris ISP Server.
Types of Attacks on Network Security
This section describes some of the most common types of attacks on a network connected to the Internet.
Denial of Service Attacks
These attacks make the system unavailable for customers, often by overloading the service with spurious requests. These attacks flood the network with useless traffic resulting in an inability to serve customers. Such attacks can crash the system in extreme cases, or just make the system extremely slow and thus unusable by customers.
Buffer Overrun Exploits
If a program does not check buffer limits when reading and receiving data, this opening can be exploited to add arbitrary data into a program or file system. When run, this data can give the intruder root access to your system.
Snooping and Replay Attacks
Snooping attacks involve an intruder listening to traffic between two machines on your network. If traffic includes passing unencrypted passwords, an unauthorized individual can potentially access your network and read confidential data.
IP Spoofing
In a spoofing attack, the intruder listening to your network traffic finds the IP address of a trusted host and sends messages indicating that the message is coming from that trusted host.
Internal Exposure
Many network break-ins are the result of a malicious or disgruntled present or former employee misusing access to information or breaking into your network.
Solaris ISP Server Structure and Security
This section discusses some aspects of Solaris ISP Server that introduce the potential for some security risks.
Figure 2-1 Areas to Protect in the Solaris ISP Server Network
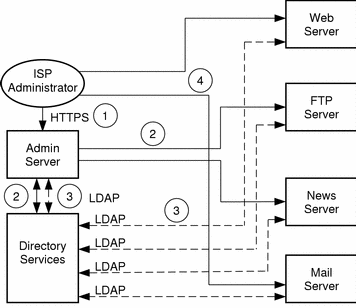
The connections labeled with circled numbers in Figure 2-1 indicate network connections that should be protected for a secure Solaris ISP Server system.
-
The connection between an ISP administrator's browser and Sun Internet Administrator is the first region of vulnerability. The administrator's machine could be anywhere on the Internet, and thus its communications must be protected. The administrator's password, used when logging into Sun Internet Administrator, would allow an intruder snooping on the line to access the same services and cause major damage. To protect this connection, configure the administration web server (AWS) for Sun Internet Administrator to use SSL or SKIP. Instructions for configuring SSL are in the SunTM WebServerTM online help.
Note -The web server instance that is the AWS is called "aws" in the Sun WebServer user interface.
-
The connections between the AWS and the applications it manages are also vulnerable to various snoop and spoof attacks. Sun Internet Administrator passes administrator login information to each application's administration interface. Should that information be picked up by an intruder, that intruder could log in as the administrator and cause damage.
In addition, Sun Internet Administrator invokes command-line functions via its own remote execution mechanism. Should this mechanism be broken into, the intruder would have access to powerful command-line functions, some of which run as root. To protect against both of these risks, you should configure SunScreen SKIP (or its equivalent) on these communication paths. SKIP authenticates incoming traffic and encrypts data so that it cannot be viewed or modified by others while in transit.
-
Connections to the directory services are particularly important, as user and service information is passed along constantly, and all such information is stored in the directory. SunTM Directory Services encrypts password values, but data is readily available to a snooper on the wire. To protect this information, you should configure SunScreen SKIP on these communication paths.
-
Connections between the administrator's machine and two-tier applications also require protection. You can configure an IP-level security mechanism, such as SunScreen SKIP between the two machines. In the case of Sun WebServer, you can configure the administrative user interface to use SSL. Refer to the Sun WebServer online help for information on configuring SSL. Because SSL uses a different port, remember to reregister the service with Sun Internet Administrator. Instructions for this are in the Sun Internet Administrator online help.
How To Tighten Security
This section discusses standard security precautions you can take to protect your network, the security mechanisms in Solaris ISP Server, and how to use these mechanisms in a Solaris ISP Server installation.
Standard Security Precautions
The following standard security precautions will help safeguard your network.
-
Design your network for as few software components per machine as is compatible with the machine's purpose. Any software product has the potential to introduce security holes, whether through known vulnerabilities or through bugs. The fewer processes running and the fewer protocols supported, the more secure the computer will be.
In addition, if an intruder were to compromise one computer, only a portion of the resources and services in your system would be involved.
-
Disable Solaris services that are not needed on the particular computer. Solaris ISP Server host configuration software offers recommendations based on your choice of application software, for example, disabling some 'r' commands (such as rlogin) to ensure protection for passwords and to restrict access to hosts for unauthorized individuals. Unless you have a specific reason for enabling a service, accept these recommendations.
-
Change passwords regularly and encourage using difficult-to-guess passwords. The directory services do not enforce periodic changing of passwords; you must have your users change them at appropriate intervals.
-
Use public-key cryptography to encrypt all traffic between trusted hosts at the IP level. SunScreen SKIP, bundled with Solaris ISP Server, authenticates incoming IP traffic and ensures that outgoing data is not altered or viewed by others while in transit.
-
Use routers that can identify trusted hosts and block spoofed IP addresses.
-
Fix vulnerabilities and bullet proof your code. Ensure that all applications check buffer limits and prevent overruns.
-
Grant access only to the portions of the system that employees need to do their jobs. Limit administrator rights to only those services they actually manage. Sun Internet Administrator supports this effort by offering a centralized way to manage administrator access. Administrators do not even need UNIX accounts to do their work.
-
Implement security mechanisms such as network monitoring and firewalls.
Security Mechanisms in Solaris ISP Server
Security mechanisms in Solaris ISP Server include a hardening step performed during installation, access control lists (ACLs), encryption software (SunScreen SKIP), and intrusion detection based on examination of log files.
Authentication
Authentication in Solaris ISP Server is performed using a private Pluggable Authentication Module (PAM). User login information is validated against the directory using LDAP. This form of authentication allows for more users on a single system, and provides a better security model than standard UNIX authentication. It allows central authentication for users of all systems on the network and removes the need to create a UNIX account for every user.
Access Control
Sun Directory Services has ACLs that are set during installation. They are defined so that only appropriate entities can add, change, or delete entries. Specific information on the ACLs configured by Solaris ISP Server is in Chapter 3, Using Directory Services of this book.
Sun WebServer has ACLs that protect web site content based on user-definable realms. All Solaris ISP Server web-based interfaces are protected by these ACLs, to prevent unauthorized access.
Hardening of the Solaris Operating System
The Solaris ISP Server host configuration software disables unnecessary Solaris services and changes the modes and owners of certain system files, reducing the potential security gaps in the system. This process is configurable; you control which services are disabled and which other hardening steps are performed.
Intrusion Detection
Using syslog, Solaris ISP Server applications log administrator's actions. These logs are checked at a configurable interval for login attempts. A user-specified alert is triggered if failed attempts are noted.
Secure Sockets Layer (SSL)
SSL provides authentication and authorization (access control) by the use of signed (or self-signed) certificates. Privacy of communications and data integrity are provided by cryptography. SSL encryption uses a 40-bit algorithm in the global version of the product and a 128-bit algorithm in the US/Canada version.
To configure SSL on Sun WebServer, refer to the Sun WebServer online help.
SunScreenTM SKIP
SunScreen SKIP provides cryptographic technology configurable at the IP level. It performs host-level authentication and access control by use of certificates and ACLs. It provides privacy by way of encryption (40-bit global, and 128-bit US/Canada), and data integrity by means of encryption.
To configure SunScreen SKIP between two machines, first use the Solaris ISP Server host configuration software to install it on both systems. Then, see the SunScreenTM SKIP User's Guide for instructions on creating certificates and further configuration steps.
- © 2010, Oracle Corporation and/or its affiliates
