Solaris ISP Server Structure and Security
This section discusses some aspects of Solaris ISP Server that introduce the potential for some security risks.
Figure 2-1 Areas to Protect in the Solaris ISP Server Network
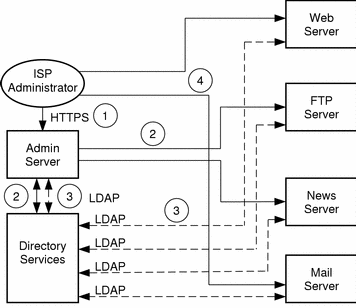
The connections labeled with circled numbers in Figure 2-1 indicate network connections that should be protected for a secure Solaris ISP Server system.
-
The connection between an ISP administrator's browser and Sun Internet Administrator is the first region of vulnerability. The administrator's machine could be anywhere on the Internet, and thus its communications must be protected. The administrator's password, used when logging into Sun Internet Administrator, would allow an intruder snooping on the line to access the same services and cause major damage. To protect this connection, configure the administration web server (AWS) for Sun Internet Administrator to use SSL or SKIP. Instructions for configuring SSL are in the SunTM WebServerTM online help.
Note -The web server instance that is the AWS is called "aws" in the Sun WebServer user interface.
-
The connections between the AWS and the applications it manages are also vulnerable to various snoop and spoof attacks. Sun Internet Administrator passes administrator login information to each application's administration interface. Should that information be picked up by an intruder, that intruder could log in as the administrator and cause damage.
In addition, Sun Internet Administrator invokes command-line functions via its own remote execution mechanism. Should this mechanism be broken into, the intruder would have access to powerful command-line functions, some of which run as root. To protect against both of these risks, you should configure SunScreen SKIP (or its equivalent) on these communication paths. SKIP authenticates incoming traffic and encrypts data so that it cannot be viewed or modified by others while in transit.
-
Connections to the directory services are particularly important, as user and service information is passed along constantly, and all such information is stored in the directory. SunTM Directory Services encrypts password values, but data is readily available to a snooper on the wire. To protect this information, you should configure SunScreen SKIP on these communication paths.
-
Connections between the administrator's machine and two-tier applications also require protection. You can configure an IP-level security mechanism, such as SunScreen SKIP between the two machines. In the case of Sun WebServer, you can configure the administrative user interface to use SSL. Refer to the Sun WebServer online help for information on configuring SSL. Because SSL uses a different port, remember to reregister the service with Sun Internet Administrator. Instructions for this are in the Sun Internet Administrator online help.
- © 2010, Oracle Corporation and/or its affiliates
