Appendix A
Netscape's Use of Public-Key Cryptography
Public-Private Key Pairs
Public-key cryptography involves a pair of keys--a public key and a private key--associated with an entity that needs to authenticate its identity electronically or to sign or encrypt data. Each public key is published as part of a certificate, and the corresponding private key is kept secret. Data encrypted with your public key can be decrypted only with your private key. Figure 17 shows a simplified view of the way this works.
Figure 17 Using public and private keys for encryption
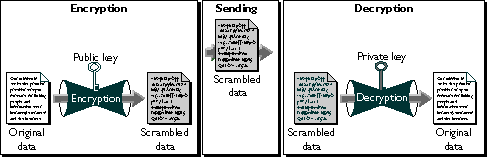
As it happens, the reverse is also true: data encrypted with your private key can be decrypted only with your public key. This would not be a desirable way to encrypt sensitive data, however, because it means that anyone with your public key, which is by definition published, could decrypt the data. Nevertheless, private-key encryption is useful, because it means you can use your private key to sign data with your digital signature. Client software such as Communicator (with the aid of your public key) can then confirm that the message was signed with your private key and that it hasn't been tampered with since being signed. For more information about the way this works, see Digital Signatures.
Certificates
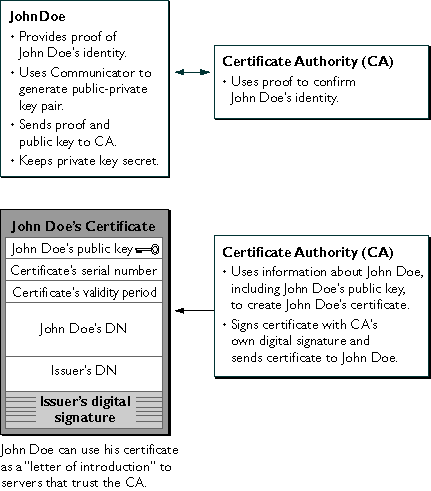
A certificate is an electronic document used to identify an individual, company, or other entity. Certificate authorities (CAs) are entities that validate identities and issue certificates. They can be either independent third parties or organizations running their own certificate-issuing server software (such as Netscape Certificate Server). The methods used to validate an identity vary depending on the policies of a given CA. In general, before issuing a certificate, the CA must use its published verification procedures for that type of certificate to ensure that an entity requesting a certificate is in fact who it claims to be.
Before submitting a request for a certificate to a CA, client software such as Communicator generates a public key and the corresponding private key. The certificate issued by the CA binds the public key to the name of the requesting entity (such as the name of an employee or a server). Certificates help prevent the use of fake public keys for impersonation.
A certificate is like a driver's license, a passport, or any other personal ID that provides generally recognized proof of a person's identity. A certificate always includes a public key, the name of the entity it identifies, an expiration date, the name of the CA that issued the certificate, a serial number, and other information. Most importantly, a certificate always includes the digital signature of the issuing CA. The CA's digital signature allows the certificate to function as a "letter of introduction" for users who know and trust the CA but don't know the entity identified by the certificate.
Types of Certificates
Communicator recognizes five kinds of certificates. The first two in this list are used with the Secure Sockets Layer (SSL), a standard protocol for authentication and encryption over TCP/IP networks:
- Client SSL certificates. Used to identify clients to servers via SSL.
- Server SSL certificates. Used to identify servers to clients via SSL.
uid=doe,e=doe@netscape.com,cn=John Doe,o=Netscape Communications Corp.,c=USEach attribute tag, such as
uid, labels a value, such as doe. The attribute tags used in a DN may vary somewhat from one organization to another, but the combination of AVAs must be unique to the entity the certificate identifies.
Every certificate includes the following information:
- the certificate's serial number
- the DN of the CA that issued the certificate
- the algorithm used by the CA to create its own digital signature
Keeping Track of Certificates
When a user receives a client SSL certificate, it is typically installed in the user's copy of Communicator or other client software. Communicator supports the public-key cryptography standard known as PKCS #12, which governs key portability. This means, for example, that you can move your certificates (and the corresponding private keys) from one computer to another on floppy disks. Communicator also supports PKCS #11, which governs communication with devices like smartcards and PCMCIA cards. This support means that Communicator can exchange information with smartcards in smartcard readers attached to client machines. For example, Communicator can use certificates and private keys stored on smartcards as well as those stored within Communicator itself. Navigator 3.x doesn't support PKCS #11 or PKCS #12, although it is possible, for example, to manually move certificate (cert5.db) and key (key.db) database files from a central directory on the network into the Navigator directory (on Windows 95) or equivalent.
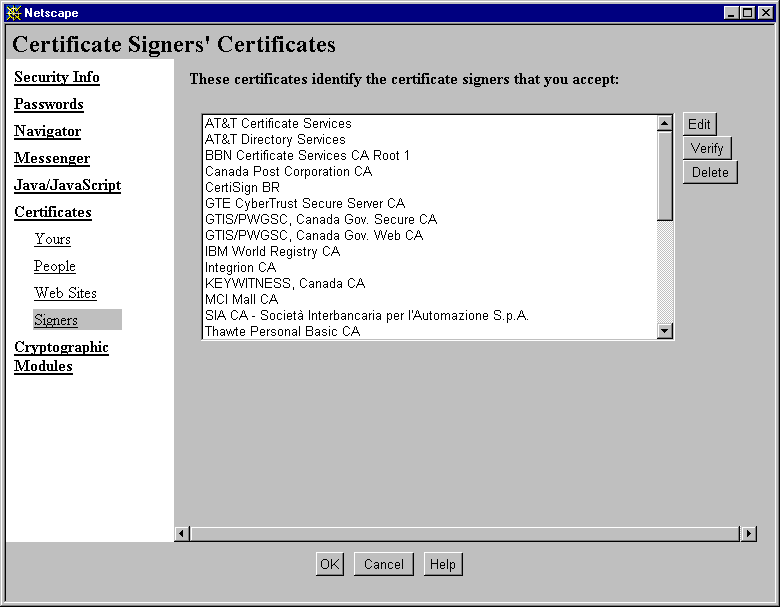
To validate a certificate, Netscape client software relies in part on its list of accepted CAs. A CA can be a publicly recognized independent company (such as those listed at Certificate Authority Services), or it can be an individual or department recognized only within a corporation's intranet or extranet (such as the internal Netscape CA). The user can add CAs to the list of trusted CAs and, if necessary, delete CAs that the user decides not to trust. If a certificate cannot be traced back to one of the CAs on Communicator's list, the user identified by that certificate can't be authenticated by a server that supports single sign-on. To view your current list of CAs in Communicator, click the Security button near the top of the Navigator window, then click Signers under Certificates. The list of certificate signers (that is, CAs recognized by your copy of Communicator for validating certificates) looks like the one shown in Figure 18.
Figure 18 Viewing CA certificates in the Security Info window
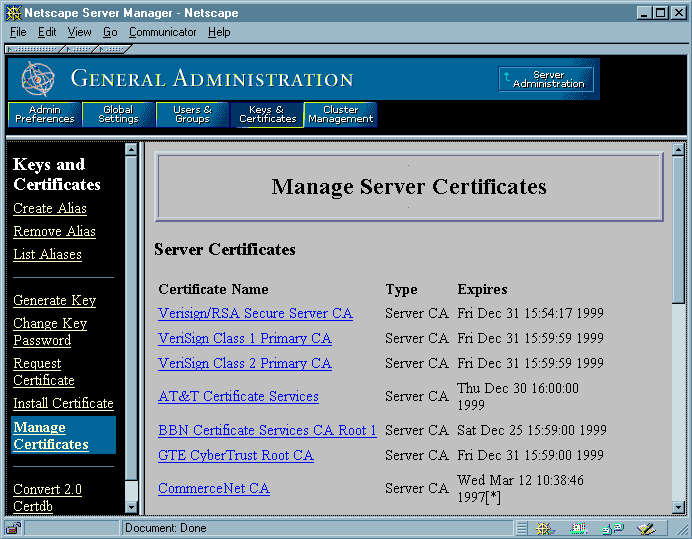
- Click the Keys & Certificates tab.
- Click Manage Certificates in the left frame.
- Using the pop-up menu, select the server whose certificates you want to see, then click OK.
Figure 19 A server's list of certificates
Digital Signatures
When Netscape software signs data, such as an email message or Java code, it first creates a one-way hash of that data. A one-way hash (also called a message digest) is a number of fixed length with the following characteristics:
Figure 20 shows a simplified view of the way a digital signature can be used to validate the integrity of signed data.
Figure 20 Using a digital signature to validate data integrity
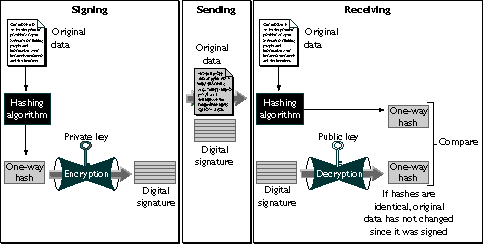
If the two hashes match, the recipient can be certain that the public key in the signer's certificate corresponds to the signer's private key. To confirm the identity of the signer, however, also involves confirming the validity of the digital signature of the CA who issued the signer's certificate. For a discussion of the way this works, see Authenticating a User's Identity.
The significance of a digital signature is comparable to the significance of a handwritten signature. Once you have signed some data, it is difficult to deny doing so later--assuming that the private key has not been compromised or out of the owner's control. This quality of digital signatures is described as nonrepudiation. In some situations, a digital signature may be as legally binding as a handwritten signature. Therefore, signers should take great care to ensure that they can stand behind any data they sign.
Getting a Certificate
The public key and the corresponding private key are created locally by the server or client software that requests the certificate. To help ensure that the private key isn't compromised, it remains on the local machine, and client software or the system administrator submits the public key along with other information to the certificate authority (CA) that issues the certificate. The CA may be an independent company that issues certificates for a fee or an administrator running a Netscape Certificate Server within an organization. The CA verifies the identity of the requester according to the CA's security policies, then issues the certificate.
In addition to the public key, DN, and other information, every certificate includes the name and digital signature of the CA that issued it, as shown in Figure 21.
Figure 21 shows a simplified view of the way a user named John Doe might use Communicator to obtain a client SSL certificate from a CA. The details of this procedure vary depending on the kind of certificate requested, the software doing the requesting, and the security policies of the CA. However, the overall process works basically the same way for any software (including Communicator, Navigator 3.x, and SuiteSpot servers) used to request any kind of certificate.
Figure 21 Using Communicator to request a client certificate
Authenticating a User's Identity
SSL-enabled servers can be configured to require client authentication, or cryptographic evidence of the user's identity. When a server configured this way requests client authentication during the SSL handshake, the client sends the server both a certificate and a separate piece of digitally signed data to authenticate itself. The server uses the digitally signed data to validate the public key in the certificate and to authenticate the identity the certificate claims to represent.
Both Communicator and Navigator 3.x create a digital signature in this situation by first creating a one-way hash from a piece of randomly generated data, called the nonce. (The client and the server both contribute toward the creation of the nonce, which is unique to each SSL session.) The hash of the nonce is then encrypted with the private key that corresponds to the public key in the certificate being presented to the server.
To authenticate the binding between the public key and the person or other entity identified by the certificate that contains the public key, a server configured to support single sign-on as described in this guide must receive a "yes" answer to the five questions shown in Figure 22. The server's list of trusted CAs, on the right side of the figure, determines which certificates the server will accept.
Figure 22 How a server authenticates a user's certificate
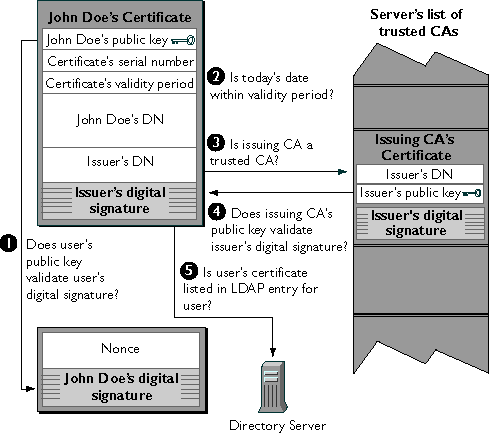
- Does the user's public key validate the user's digital signature? The server checks that the user's digital signature can be validated with the public key in the certificate. If so, the server has established that the public key asserted to belong to John Doe matches the private key used to create the signature and that the nonce has not been tampered with since it was signed.
- Is the issuing CA a trusted CA? Each SSL-enabled server maintains a list of trusted CA certificates. If the DN of the issuing CA matches the DN of a CA on the list of trusted CAs, the answer to this question is yes, and the server goes on to step 4. If the issuing CA is not on the list, the client will not be authenticated unless it can verify a certificate chain ending in a CA that is on the list (see Verifying Certificate Chains for details). Administrators can control which certificates are trusted or not trusted within their organizations by controlling the lists of CA certificates maintained by clients and servers.
However, at this point the binding between the public key and the DN specified in
the certificate has not yet been established. The certificate might have been created
by someone attempting to impersonate the user. To authenticate the binding
between the public key and the DN, the server must also complete steps 3 and 4.
[Contents] [Previous] [Next] [Last]
Last Updated: 10/20/97 14:15:46
Any sample code included above is provided for your use on an "AS IS" basis, under the Netscape License Agreement - Terms of Use