| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Directory Server Enterprise Edition Reference 11 g Release 1 (11.1.1.5.0) |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Directory Server Enterprise Edition Reference 11 g Release 1 (11.1.1.5.0) |
1. Directory Server Enterprise Edition File Reference
Software Layout for Directory Server Enterprise Edition
Directory Server Instance Default Layout
Directory Proxy Server Instance Default Layout
Part I Directory Server Reference
4. Directory Server LDIF and Search Filters
6. Directory Server Monitoring
7. Directory Server Replication
8. Directory Server Data Caching
11. Directory Server Groups and Roles
Deciding Between Groups and Roles
Advantages of the Groups Mechanism
Advantages of the Roles Mechanism
Restricting Permissions on Roles
12. Directory Server Class of Service
14. Directory Server Internationalization Support
Part II Directory Proxy Server Reference
15. Directory Proxy Server Overview
16. Directory Proxy Server Load Balancing and Client Affinity
17. Directory Proxy Server Distribution
18. Directory Proxy Server Virtualization
19. Connections Between Directory Proxy Server and Backend LDAP Servers
20. Connections Between Clients and Directory Proxy Server
21. Directory Proxy Server Client Authentication
22. Security in Directory Proxy Server
23. Directory Proxy Server Logging
A group is an entry that identifies the other entries that are in the group. The group mechanism makes it easy to retrieve a list of entries that are members of a given group.
Although groups may identify members anywhere in the directory, the group definitions themselves should be located under an appropriately named node such as ou=Groups. This makes them easy to find, for example, when defining access control instructions (ACIs) that grant or restrict access when the bind credentials are members of a group.
Static groups explicitly name their member entries. For example, a group of directory administrators would name the specific people who formed part of that group, as shown in the following illustration.
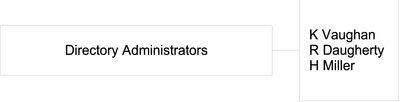
The following LDIF extract shows how the members of this static group would be defined.
dn: cn=Directory Administrators, ou=Groups, dc=example,dc=com ... member: uid=kvaughan, ou=People, dc=example,dc=com member: uid=rdaugherty, ou=People, dc=example,dc=com member: uid=hmiller, ou=People, dc=example,dc=com
Static groups specify the DN of each member of the group. Static groups use one of the following object class and attribute pairs:
The groupOfNames object class, with a multi-valued member attribute
The groupOfUniqueNames object class, with a multi-valued uniqueMember attribute
The member attribute and uniqueMember attribute contain the DN for every entry that is a member of the group. The uniqueMember attribute value for the DN is optionally followed by a hash, #, and a unique identifier label to guarantee uniqueness.
Dynamic groups specify a filter and all entries that match the filter are members of the group. These groups are dynamic because membership is defined each time the filter is evaluated.
Imagine, for example, that all management employees and their assistants were situated on the 3rd floor of your building, and that the room number of each employee commenced with the number of the floor. If you wanted to create a group containing just the employees on the third floor, you could use the room number to define just these employees, as shown in the following illustration.
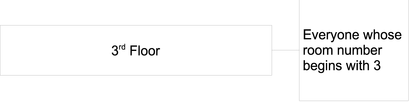
The following LDIF extract shows how the members of this dynamic group would be defined.
dn: cn=3rd Floor, ou=Groups, dc=example,dc=com ... memberURL: ldap:///dc=example,dc=com??sub?(roomnumber=3*)
Dynamic groups use one of the following object class and attribute pairs:
The groupOfURLs object class, with the memberURL attribute
The groupOfUniqueNames object class, with the uniqueMember attribute
The group members are listed either by one or more filters represented as LDAP URL values of the memberURL attribute or by one or more DNs as values of the uniqueMember attribute.
Static and dynamic groups can be nested by specifying the DN of another group as a value for the member attribute or uniqueMember attribute. The depth to which nested groups are supported by ACIs is controlled by the nsslapd-groupevalnestlevel configuration parameter. Directory Server also supports mixed groups, that is groups that reference individual entries, static groups, and dynamic groups.
Imagine for example that you wanted a group containing all directory administrators, and all management employees and their assistants. You could use a combination of the two groups defined earlier to create one nested group, as shown in the following illustration.

The following LDIF extract shows how the members of this nested group would be defined.
dn: cn=Admins and 3rd Floor, ou=Groups, dc=example,dc=com ... member: cn=Directory Administrators, ou=Groups, dc=example,dc=com member: cn=3rd Floor, ou=Groups, dc=example,dc=com
 | Caution - Nested groups are not the most efficient grouping mechanism. Dynamic nested groups incur an even greater performance cost. To avoid these performance problems, consider using roles instead. |