B Oracle Database Firewall Database Schema
About the Oracle Database Firewall Schema
The Oracle Database Firewall tables are stored in the SECURELOG schema. This schema contains a set of logically related tables, which are described in this appendix.
Summary Tables
This section contains:
About the Summary Tables
The summary tables store general information about the data that is being monitored, such as the names of the users logging in, the monitored databases, user sessions, database traffic, events, and so on.
applied_baselines Table
Table B-1 provides the name of the policy that is currently used for while traffic is being captured.
Table B-1 applied_baselines Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of this record |
|
|
|
|
Name of the baseline (also available from |
|
|
|
|
ID of the protected database in the |
database_user_addresses Table
Table B-2 provides IP addresses that are expected to be used by a user who has accessed the protected database.
Table B-2 database_user_addresses Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
ID of the address record in this table |
|
|
|
|
ID of the database user in the |
|
|
|
|
Expected IP address of the user (possible one of many) |
database_users Table
Table B-3 records each user who has accessed a protected database.
Table B-3 database_users Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
ID of the user record in this table |
|
|
|
|
Name of the user who started the session (also available from |
|
|
|
|
ID of the protected database in the |
|
|
|
|
Time that the session was ended |
|
|
|
|
Set to 1 if the user is an administrator of the database |
|
|
|
|
Set to 1 if the user is a predefined user of the database (that is, automatically created when the |
dictionary Table
Table B-4 provides a set of mappings from coded values to meaningful text. This table is useful in generating understandable text in a report, without hard-coding the values into the report query. The tables throughout this appendix use values listed in this table. For example, several tables have a column entitled cluster_type. The values possible for the cluster_type column are listed in the dictionary table.
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Name of item. Possible values:
|
|
|
|
|
Value of the item listed in the |
|
|
|
|
Description of value listed in the |
protected_database_addresses Table
Table B-5 provides address and port details for each protected database.
Table B-5 protected_database_addresses Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of this record |
|
|
|
|
IP address of the protected database |
|
|
|
|
Port number used to access the protected database |
|
|
|
|
ID of the protected database in the |
protected_databases Table
Table B-6 provides details about each protected database.
Table B-6 protected_databases Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the database |
|
|
|
|
Name of the database |
|
|
|
|
SQL dialect:
|
|
|
|
|
Description of the database |
|
|
|
|
Set to 1 if SOX reports can be produced from the database (also available from |
|
|
|
|
Set to 1 if PCI reports can be produced from the database (also available from |
|
|
|
|
Set to 1 if DPA reports can be produced from the database (also available from |
|
|
|
|
Set to 1 if GLBA reports can be produced from the database (also available from |
|
|
|
|
Set to 1 if HIPAA reports can be produced from the database (also available from |
sources Table
Table B-7 provides details about the source of an event: either the relevant hardware (or virtual) device for events that apply system-wide, or the monitoring enforcement point for events detected by monitoring.
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the source of the event, which can be an appliance (physical server), in the case of syslog messages, or the enforcement point (in the case of database traffic related events, or enforcement point related syslog messages). |
|
|
|
|
Time that the source of the event was added to the database |
|
|
|
|
Short name of the source of the event |
|
|
|
|
Set to 1 if the source of the event is a syslog source other than an enforcement point |
summary_clusters Table
Table B-8 provides information about individual clusters for the purpose of reporting. As well as providing a unique identity to each cluster, this table provides an example statement that would appear in the cluster.
Table B-8 summary_clusters Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Source ID of the binary data |
|
|
|
|
Grammar-specific version number |
|
|
|
|
SQL dialect:
|
|
|
|
|
Type of statements included in the cluster:
See also |
|
|
|
|
String representation of cluster (path). Not used |
|
|
|
|
An example of a statement in the cluster (also available from |
summary_records Table
Table B-9 provides primary information collected in the traffic log, as an hourly summary of the count of occurrences of each cluster.
Table B-9 summary_records Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the summary record |
|
|
|
|
ID of the session in the |
|
|
|
|
Set with session attributes |
|
|
|
|
ID of the cluster in the |
|
|
|
|
ID of the attribute in the |
|
|
|
|
Grammar-specific version number |
|
|
|
|
Response code of the statement for database response monitoring:
See also |
|
|
|
|
Time that the SQL statement was captured by the Database Firewall (also available from |
|
|
|
|
Threat severity of the statements:
See also |
|
|
|
|
Logging level of the statements:
See also |
|
|
|
|
Action level of the statements:
See also |
|
|
|
|
Number of statements that have the same characteristics, as listed above (also available from |
summary_sessions Table
A new session is started when a client application successfully logs into a database. This session lasts for as long as the connection exists (often, until the application logs out from the database, although the session may terminate in a less controlled way). Sessions are associated with a client application, and with the authentication or identification information (primarily the user name) used to establish the connection. A simple client application creates a single session, or in some cases, one session after another. More complex applications may have many simultaneously active sessions.
Note:
This table does not record each session. Instead, a new record is added when one or more of the fields (source_id, client, user_id, baseline_id, and dialect_version) is different from an existing record.Table B-10 provides details about each database session, typically identified by the source address of the session.
Table B-10 summary_sessions Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the database session |
|
|
|
|
ID of the sources in the |
|
|
|
|
IP address of the database client (also available from |
|
|
|
|
ID of the user who started the session (Table B-3) |
|
|
|
|
ID of the policy in the |
|
|
|
|
Not used |
|
|
|
|
Name of the client program used in this session |
|
|
|
|
Operating system user name |
summary_statement_attributes Table
Table B-11 stores statement attribute values that can be summarized from the summary_records table.
Table B-11 summary_statement_attributes Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
ID of each record in this table |
|
|
|
|
Result of the CRC32 (Cyclic Redundancy Check) of the concatenation of all attribute values. This is for internal use only to enable fast searching. |
|
|
|
|
HTTP response code Note: This and the remaining fields in this table are relevant to the F5 BIG-IP ASM integration only. See Chapter 11, "Using Oracle Database Firewall with BIG-IP ASM," for more information. |
|
|
|
|
HTTP request method |
|
|
|
|
Request protocol |
|
|
|
|
Requested resource |
|
|
|
|
Web client IP address |
|
|
|
|
Web application name |
|
|
|
|
Name of the WAF box |
|
|
|
|
IP address of the WAF management interface |
|
|
|
|
WAF policy name |
|
|
|
|
List of IP addresses provided by |
|
|
|
|
Set to 1 if the http request was blocked |
|
|
|
|
Name of the Web user |
|
|
|
|
HTTP referrer |
|
|
|
|
Web application server name |
|
|
|
|
IHTTP user agent |
|
|
|
|
IP address of the client that initiated the HTTP request. It is either the client IP address of the HTTP connection over which the request was issued, or if the HTTP header record "X-FORWARDED-FOR" is present, then it's value is used. |
|
|
|
|
Violation from |
|
|
|
|
One of the following:
|
traffic_events Table
Table B-12 provides details about events that have been transmitted, or potentially transmitted, over syslog by the enforcement point. These events ares primarily alerts from monitoring.
Table B-12 traffic_events Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the traffic event |
|
|
|
|
ID of the source event in the |
|
|
|
|
Time of the event |
|
|
|
|
ID of the cluster |
|
|
|
|
Action level of the cluster that the statement belongs to:
|
|
|
|
|
Threat severity of the cluster:
|
|
|
|
|
Logging level of the cluster:
|
|
|
|
|
IP address of the database client that sent the statement |
|
|
|
|
IP address of the database server |
|
|
|
|
Name of the database user who sent the statement |
|
|
|
|
Name of the Web user (available only in WAF alerts) |
|
|
|
|
Web application name (available only in WAF alerts) |
|
|
|
|
Request protocol (available only in WAF alerts):
|
|
|
|
|
HTTP request method (available only in WAF alerts). For example, |
|
|
|
|
Requested resource (available only in WAF alerts). For example: |
|
|
|
|
Request. for example, |
|
|
|
|
HTTP referrer (available only in WAF alerts). For example: |
|
|
|
|
Web application server name (available only in WAF alerts). Can be an IP address (for example, 192.0.2.220) |
|
|
|
|
HTTP user agent (available only in WAF alerts). For example, |
|
|
|
|
HTTP response code (available only in WAF alerts) |
|
|
|
|
Full HTTP request. Includes |
|
|
|
|
Name of the WAF appliance (available only in WAF alerts) |
|
|
|
|
IP address of the WAF management interface (available only in WAF alerts) |
|
|
|
|
WAF policy name (available only in WAF alerts) |
|
|
|
|
The time when the WAF policy was applied (available only in WAF alerts) |
|
|
|
|
Unique ID of the event in the WAF system (available only in WAF alerts) |
|
|
|
|
|
|
|
|
|
Contains all the session cookies sent with the HTTP request (available only in WAF alerts) |
|
|
|
|
Violation with the highest priority (available only in WAF alerts) |
|
|
|
|
IP address of attacker |
|
|
|
|
One of the following (which are available only in WAF alerts):
|
|
|
|
|
Unique ID of the statement (sequential number) |
|
|
|
|
SQL statement string (may be truncated) |
traffic_summaries View
Table B-13 provides a view to data in other tables.
Table B-13 traffic_summaries View
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Name of the protected database:
|
|
|
|
|
SQL dialect used by the database:
|
|
|
|
|
Set to 1 if SOX reports can be produced from the database (from |
|
|
|
|
Set to 1 if PCI reports can be produced from the database (from |
|
|
|
|
Set to 1 if DPA reports can be produced from the database (from |
|
|
|
|
Set to 1 if GLBA reports can be produced from the database (from |
|
|
|
|
Set to 1 if HIPAA reports can be produced from the database (from |
|
|
|
|
Name of the baseline |
|
|
|
|
Grammar version |
|
|
|
|
IP address of the database client |
|
|
|
|
Name of the database user |
|
|
|
|
Not used |
|
|
|
|
ID of the source in the |
|
|
|
|
The application name used as a client software in this session |
|
|
|
|
Operating system user name |
|
|
|
|
An example statement in the cluster |
|
|
|
|
Time of the statement count |
|
|
|
|
ID of the cluster (from |
|
|
|
|
Threat severity of the statements:
|
|
|
|
|
Logging level of the statements:
|
|
|
|
|
Action level of the statements:
|
|
|
|
|
Type of statements included in the cluster:
|
|
|
|
|
Response code of the statement:
|
|
|
|
|
Number of SQL statements that have the same characteristics, as listed in this table |
Relationship Diagram of the Summary Tables
Figure B-1 illustrates the relationships between the summary database tables.
Figure B-1 Relationship Diagram of the Summary Tables
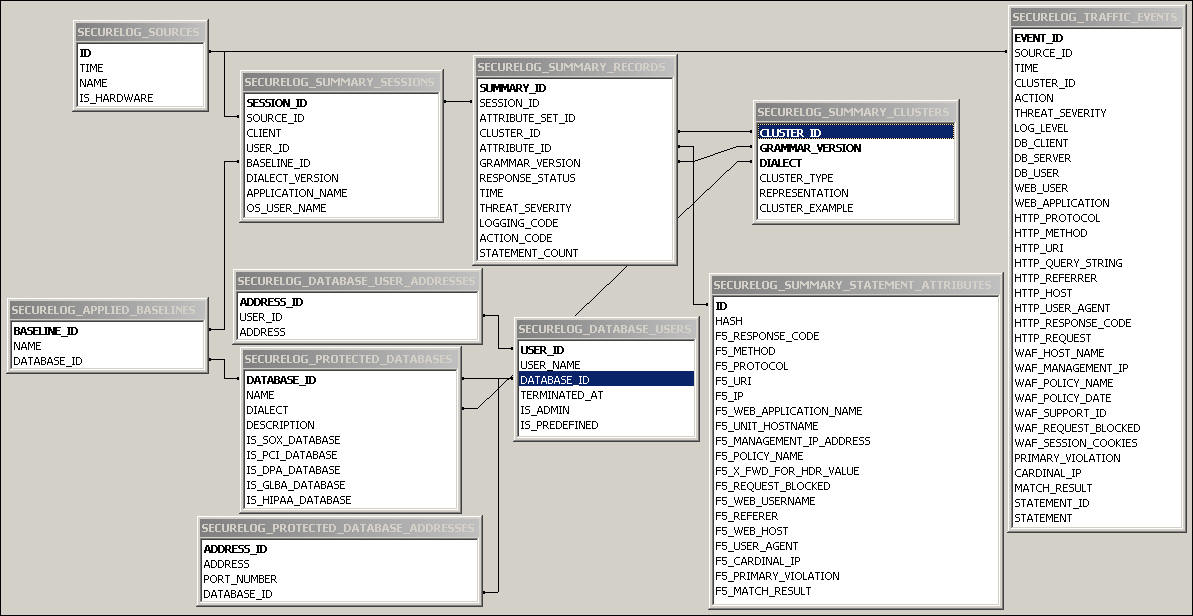
Description of "Figure B-1 Relationship Diagram of the Summary Tables"
Log Forensic Tables
About the Forensic Tables
The forensic tables contain information about all the SQL statements that Oracle Database Firewall logs. Because the amount of data can be large, Oracle Database Firewall enables you to query the log files through the Administration Console. It stores these log files in the two tables described in this section, traffic_log_queries and traffic_log_query_results.
To search through the log files:
-
Log in to the standalone Database Firewall or Management Server Administration Console.
See "Logging in to the Administration Console" for more information.
-
Select the Reporting tab.
-
In the Traffic Log menu, select either Search Log or Log Search Results.
See Oracle Database Firewall Security Management Guide for more information about accessing the traffic log.
In addition to these two tables, for each search, Oracle Database Firewall creates a new table. This table is derived from traffic_log_query_results and has a name in form of traffic_log_query_results_id where id is the identifier of the search. This table is deleted when the entry in the traffic_log_queries table for a given search is deleted.
traffic_log_queries Table
Table B-14 provides the properties of each log search, such as the period that the log search covers and the filter settings. Each use of Search Log in the reporting page of the Administration Console adds a new row to the table. See Table B-15 for more information about the meaning of each field.
Table B-14 traffic_log_queries Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID for the query |
|
|
|
|
The title of the report |
|
|
|
|
The time when the query was started |
|
|
|
|
The time when the query was finished |
|
|
|
|
The time when the user cancelled the query |
|
|
|
|
The time when the query was deleted |
|
|
|
|
The name of the results table: |
|
|
|
|
The begin of the data time range to be extracted (filtering) |
|
|
|
|
The end of the data time range to be extracted (filtering) |
|
|
|
|
The beginning of the time range relative to end of the time range |
|
|
|
|
The ending of the time range relative to arbitrary time |
|
|
|
|
Filter to reduce the number of entries |
|
|
|
|
Specifies the maximum number of records that should be extracted (filtering) ( |
|
|
|
|
Records how many records were found and displayed in the Administration Console |
|
|
|
|
Records how many files have already been searched and displayed in the Administration Console |
|
|
|
|
Records how many files are be searched and displayed in the Administration Console |
|
|
|
|
Status for the search |
traffic_log_query_results Table
Table B-15 provides a template for traffic_log_query_results_id, where id is an integer that specifies the ID of the search. The table stores the results of a log search and contains one row for each SQL statement retrieved. The table traffic_log_query_results_id is created automatically when a log search is performed, and is deleted when the user deletes the log search.
Table B-15 traffic_log_query_results Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
ID of this result set |
|
|
|
|
ID of the query used to define this result set |
|
|
|
|
ID of the log file containing this particular statement. |
|
|
|
|
ID of the statement or event |
|
|
|
|
Type of the record:
|
|
|
|
|
Name of the device that collected the log file |
|
|
|
|
Origin of the record. Can be one of the following:
|
|
|
|
|
Name of the protected database |
|
|
|
|
The database type (dialect) of the protected database:
|
|
|
|
|
Database user name associated with the statement |
|
|
|
|
Origin of the database user name:
|
|
|
|
|
The database user name that was used at the time Oracle Database Firewall applied the statement policy |
|
|
|
|
Internal session sequence number |
|
|
|
|
IP address of the database client that sent the statement |
|
|
|
|
Port number of the database client that sent the statement |
|
|
|
|
IP address of the database server that received the statement |
|
|
|
|
Port number of the database server that received the statement |
|
|
|
|
Name of the policy used when the statement was recorded |
|
|
|
|
Source of the traffic:
|
|
|
|
|
Internal version or revision of the grammar implementation |
|
|
|
|
Statement text captured by the system |
|
|
|
|
Time when the statement was captured by the system |
|
|
|
|
Threat severity of the statement:
|
|
|
|
|
Logging level of the statement:
|
|
|
|
|
Reason for logging the statement:
|
|
|
|
|
Action level of the statement:
|
|
|
|
|
Alert criterion that caused the statement to be logged:
|
|
|
|
|
Number of the statements that this record represents.
|
|
|
|
|
Global ID of the cluster associated with the statement |
|
|
|
|
Type or class of statement included in the cluster:
|
|
|
|
|
Grammar-specific version number |
|
|
|
|
Response code returned by the database server |
|
|
|
|
Error message returned by a database query failure |
|
|
|
|
Detailed text of the response returned by the database server |
|
|
|
|
Number of subsequent failed statements |
|
|
|
|
Time that Oracle Database Firewall captures the statement response |
|
|
|
|
Status of the response:
|
|
|
|
|
Difference between response time and request time |
|
|
|
|
Name of the client application connected to the database |
|
|
|
|
Origin of the application:
|
|
|
|
|
Operating system user name that executed the statement |
|
|
|
|
Origin of the operating system user:
|
|
|
|
|
Full HTTP request, including POST data Note: This and the remaining fields in this table are relevant to the F5 BIG-IP ASM integration only. See Appendix 11, "Using Oracle Database Firewall with BIG-IP ASM," for more information. |
|
|
|
|
HTTP request |
|
|
|
|
HTTP response code |
|
|
|
|
HTTP request method |
|
|
|
|
Request protocol |
|
|
|
|
Requested resource |
|
|
|
|
Part of the URL containing request parameters sent using the |
|
|
|
|
Web client IP address |
|
|
|
|
Web application name |
|
|
|
|
Identified WAF violations |
|
|
|
|
Name of the WAF box |
|
|
|
|
IP address of the WAF management interface |
|
|
|
|
WAF policy name |
|
|
|
|
The time when the policy was applied |
|
|
|
|
List of IP addresses provided by |
|
|
|
|
Unique ID of the event in the WAF system |
|
|
|
|
Set to 1 if the HTTP request was blocked |
|
|
|
|
Name of the Web user |
|
|
|
|
Session authentication method |
|
|
|
|
HTTP referrer |
|
|
|
|
Web application server name |
|
|
|
|
HTTP user agent |
|
|
|
|
IP address derived from |
|
|
|
|
Violation from |
|
|
|
|
Contains all the session cookies sent with the HTTP request |
|
|
|
Match result may be one of:
|
|
|
|
|
|
Stored Procedure and User Role Audit Tables
About the Stored Procedure and User Role Audit Tables
The database object auditing tables contain information about the stored procedures and user roles collected by the stored procedure auditing and user role auditing functions.
To find reports that describe the information captured in the Stored Procedure and User Role Audit tables:
-
Log in to the standalone Database Firewall or Management Server Administration Console.
See "Logging in to the Administration Console" for more information.
-
Select the Reporting tab.
-
Do one of the following:
-
For stored procedure auditing, select from the Stored Procedure Auditing menu.
For more information, see Oracle Database Firewall Security Management Guide.
-
For user role auditing, select from the User Role Auditing menu.
For more information, see Oracle Database Firewall Security Management Guide.
-
doa_approved_edits Table
Table B-16 provides details about each set of changes to an object (stored procedure or user role) that have been approved. This information is used for user role auditing and stored procedure auditing.
Table B-16 doa_approved_edits Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the monitoring point auditing this object |
|
|
|
|
ID of the enforcement point monitoring the object |
|
|
|
|
ID of the protected database |
|
|
|
|
Object type:
|
|
|
|
|
Object subtype:
|
|
|
|
|
Object class:
|
|
|
|
|
Name of the object |
|
|
|
|
Tags associated with the object |
|
|
|
|
Contains a summary of the set of changes approved (for example: |
|
|
|
|
Comma-separated list of the names of the database users who were responsible for the modifications (copy of the value from |
|
|
|
|
The date and time when the object was changed |
|
|
|
|
The date and time when the change was detected on the Management Server |
|
|
|
|
The name of the Administration Console user who approved the set of changes |
|
|
|
|
The date and time when the changes were approved |
|
|
|
|
Comment added by the user when the changes were approved |
doa_approved_objects Table
Table B-17 provides a summary of the last set of changes to an object (stored procedure or user role) that have been approved. This information is used for user role auditing and stored procedure auditing.
Table B-17 doa_approved_objects Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the object |
|
|
|
|
ID of the enforcement point monitoring the object |
|
|
|
|
ID of the protected database |
|
|
|
|
Object type:
|
|
|
|
|
Object subtype:
|
|
|
|
|
Object class:
|
|
|
|
|
Name of the object |
|
|
|
|
Tags associated with the object |
|
|
|
|
Hash of the object (base64) (signature change means object change) |
|
|
|
|
Summary of the changes |
|
|
|
|
Database users who modified the object |
|
|
|
|
Time when the object was changed |
|
|
|
|
The name of the Administration Console user who approved the last set of changes |
|
|
|
|
The date and time when the changes were approved |
|
|
|
|
Current approved content of the object |
doa_edit_comments Table
Table B-18 provides details about each comment added when approving changes. This information is used for user role auditing and stored procedure auditing.
Table B-18 doa_edit_comments Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the comment |
|
|
|
|
ID of the pending approval in the |
|
|
|
|
The comment text |
|
|
|
|
The name of the Administration Console user who added the comment |
|
|
|
|
The date and time that the comment was created |
doa_edits Table
Table B-19 provide details about all approved objects. This information is used for stored procedure auditing and user role auditing.
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the object (stored procedure or user role) |
|
|
|
|
ID of the pending approval in the |
|
|
|
|
The hash of the object (signature change means object change) |
|
|
|
|
New content of the object |
|
|
|
|
Type of change:
|
|
|
|
|
Name of the database user who modified the object |
|
|
|
|
The date and time when the object was changed |
|
|
|
|
The date and time when the change was detected on the Management Server |
doa_pending_approvals Table
Table B-20 provides a summary of the changes to an object (stored procedure or user role) that are pending approval. This information is used for User Role Auditing and Stored Procedure Auditing.
Table B-20 doa_pending_approvals Table
| Column | Datatype | NULL | Description |
|---|---|---|---|
|
|
|
|
Unique ID of the object |
|
|
|
|
ID of the enforcement point monitoring the object |
|
|
|
|
ID of the protected database |
|
|
|
|
Object type:
|
|
|
|
|
Object subtype:
|
|
|
|
|
Object class:
|
|
|
|
|
Name of the object |
|
|
|
|
Tags associated with the object |
|
|
|
|
Set to 1 if the change must not be approved in bulk operation (default is |
|
|
|
|
Set to 1 if the change has been updated by the Management Server after being previously declined. (To decline this pending approval, set |
|
|
|
|
Comma-separated list of the names of the database users who have modified the object since the previous approval |
|
|
|
|
The date and time of the last change to the object |
|
|
|
|
The hash of the object (signature change means object change) |
|
|
|
|
Last type of change:
|
|
|
|
|
Specifies the number of new changes of type |
|
|
|
|
Specifies the number of new changes of type |
|
|
|
|
Specifies the number of new changes of type |
|
|
|
|
Contains a summary of the above changes (for example, |
|
|
|
|
Specifies the date and time that the record was last updated in the Database Firewall |
doa_tag_definitions Table
Table B-21 contains the definitions of tags that may be applied to stored procedures or user roles.
Table B-21 doa_tag_definitions Table