29 Configuring the Policy and Credential Store
For most environments, and especially production environments, you must reassociate your policy store with an external LDAP such as Oracle Internet Directory (OID), or a database. Note that when using an external LDAP-based store, the credential store and policy store must be configured to use the same LDAP server (either Oracle Internet Directory 11gR1 or 10.1.4.3). The identity store can, however, use any of the other supported LDAP servers; it does not need to use the same LDAP server as the policy and credential stores.
Reassociating the policy and credential store with OID consists of creating a root node in the LDAP directory, and then reassociating the policy and credential store with the OID server using Fusion Middleware Control, or from the command line using WLST. Reassociating the policy and credential store with a database consists of setting up the schema and database connection in the RCU, and then migrating the policy and credential store to the database from the command line using WLST.
Caution:
Before reassociating the policy store, be sure to back up the relevant configuration files:-
jps-config.xml -
system-jazn-data.xml
As a precaution, you should also back up the boot.properties file for the Administration Server for the domain.
This chapter contains the following sections:
-
Section 29.2, "Reassociating the Credential and Policy Store Using Fusion Middleware Control"
-
Section 29.3, "Reassociating the Credential and Policy Store Using WLST"
-
Section 29.4, "Reassociating the Policy and Credential Store with a Database"
-
Section 29.6, "Configuring Self-Registration By Invitation in WebCenter Spaces"
The content of this chapter is intended for Fusion Middleware administrators (users granted the Admin role through the Oracle WebLogic Server Administration Console). Users with the Monitor or Operator roles can view security information but cannot make changes. See also, Section 1.8, "Understanding Administrative Operations, Roles, and Tools."
29.1 Creating a root Node
The first step in reassociating the policy and credential store with OID, is to create an LDIF file in the LDAP directory and add a root node under which all data is added. After creating the file and adding the node, continue by reassociating the store using either Fusion Middleware Control or WLST.
To create a root node:
-
Create a root node by adding the following to an LDIF file (for example,
root.ldif) in the LDAP directory:dn: cn=root_webcenter_xxxx cn: root_webcenter_xxxx objectclass: top objectclass: orclcontainer
Where xxxx is a string (for example, the server name) that uniquely identifies the node.
-
Add this node to the directory by running the following LDAP command from your LDAP installation directory:
OID_ORACLE_HOME/as_1/bin/ldapadd -h ldap_host_name -p ldap_port -D cn=orcladmin -w password -v -f root.ldif
where:
-
OID_ORACLE_HOMEis the directory in which LDAP is installed -
ldap_host_nameis the host name of the OID server -
ldap_portis the OID server port number -
passwordis the password with which to access the OID server
Note that each root container must have a unique name.
-
29.2 Reassociating the Credential and Policy Store Using Fusion Middleware Control
Before reassociating the policy and credential store with Oracle Internet Directory, you must first have created the root node as described in Section 29.1, "Creating a root Node."
To reassociate the policy and credential store with the OID server:
-
Open Fusion Middleware Control and log in to your target instance.
For information on logging into Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, click your domain.
When initially installed, WebCenter Spaces and Enterprise Manager are already associated and deployed in the same domain.
-
From the WebLogic Domain menu, select Security > Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 29-1).
Figure 29-1 Security Provider Configuration Page
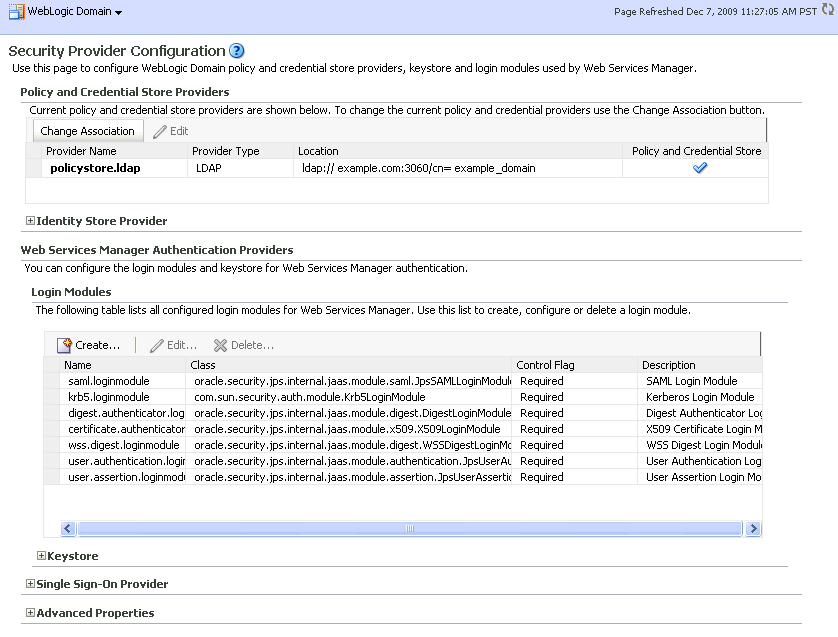
Description of "Figure 29-1 Security Provider Configuration Page"
-
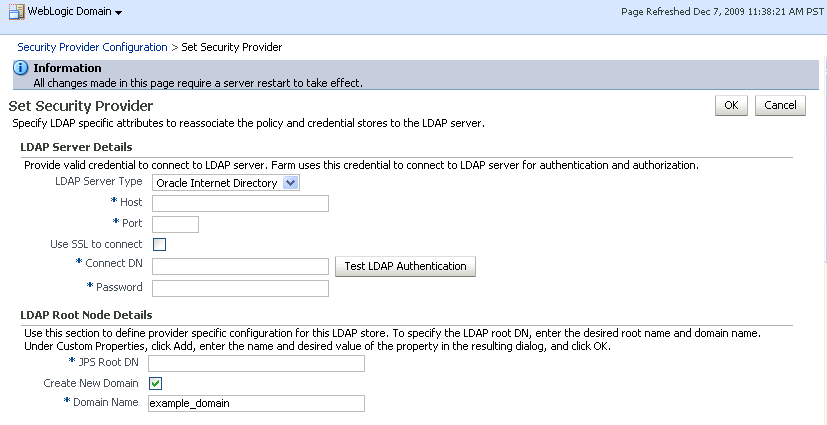
On the Security Provider Configuration page, click Change Association... to add the new Oracle Internet Directory provider.
The Set Security Provider page displays (see Figure 29-2).
-
Under LDAP Server Details, select Oracle Internet Directory as the LDAP Server Type.
-
In the Host and Port fields, enter the host name and the LDAP port for Oracle Internet Directory.
-
Set the User DN field to
cn=orcladmin,and enter the associated password in the Password field. -
Under LDAP Root Node Details, set the JPS Root DN field to the one you added to the
root.ldiffile (for example,cn=root_webcenter_abcd99). Be sure to include thecn=. -
Click OK to begin the reassociation. Restart the WebLogic server when prompted after migration.
29.3 Reassociating the Credential and Policy Store Using WLST
Before reassociating the policy and credential store with Oracle Internet Directory, you must first have created the root node as described in Section 29.1, "Creating a root Node."
-
Start WLST as described in Section 1.13.3.1, "Running Oracle WebLogic Scripting Tool (WLST) Commands."
-
Connect to the Administration Server for the target domain with the following command:
connect('username>,'password', 'host_id:port')where:
-
usernameis the administrator account name used to access the Administration Server (for example,weblogic) -
passwordis the administrator password used to access the Administration Server (for example,weblogic) -
host_idis the server ID of the Administration Server (for example,example.com) -
portis the port number of the Administration Server (for example,7001).
-
-
Reassociate the policy and credential store using the
reassociateSecurityStorecommand:reassociateSecurityStore(domain="domain_name", admin="admin_name", password="password", ldapurl="ldap_uri", servertype="ldap_srvr_type", jpsroot="root_webcenter_xxxx")
Where:
-
domain_namespecifies the domain name where reassociation takes place. -
admin_namespecifies the administrator's user name on the LDAP server. The format iscn=usrName. -
passwordspecifies the password associated with the user specified for the argumentadmin. -
ldap_urispecifies the URI of the LDAP server. The format isldap://host:port, if you are using a default port, orldaps://host:port, if you are using a secure LDAP port. The secure port must have been configured to handle an anonymous SSL connection, and it is distinct from the default (non-secure) port. -
ldap_srvr_typespecifies the kind of the target LDAP server. SpecifyOIDfor Oracle Internet Directory. -
root_webcenter_xxxxspecifies the root node in the target LDAP repository under which all data is migrated. Be sure to include thecn=. The format iscn=nodeName.
All arguments are required. For example:
reassociateSecurityStore(domain="myDomain", admin="cn=adminName", password="myPass", ldapurl="ldaps://myhost.example.com:3060", servertype="OID", jpsroot="cn=testNode")
-
29.4 Reassociating the Policy and Credential Store with a Database
As well as using an LDAP server, such as OID, for your policy and credential store, you can also reassociate the policy and credential store with an Oracle database. Prior to reassociating the policy and credential store with a database, you should have:
-
Installed the RCU and the OPSS schema
-
Installed an Oracle database (Oracle RDBMS version 10.2.0.4+, 11.1.0.7+, or 11.2.0.1+)
-
Installed WebLogic Server and SOA
-
Created a domain
For instructions on how to create a new domain, see "Creating a New Domain" in the Oracle Fusion Middleware Installation Guide for Oracle WebCenter.
-
Created a data source
For instructions on how to create a data source, see "Creating a JDBC Data Source" in the Oracle Fusion Middleware Configuring and Managing JDBC for Oracle WebLogic Server.
Follow the steps below to configure a database as your policy and credential store:
-
Associate the schema and database connection. For information about how to associate the schema and database connection, see Section 7.1.5, "Creating and Registering the Metadata Service Repository."
-
Migrate the policy and credential store to the database using WLST using the following command:
reassociateSecurityStore(domain="your_domain", datasourcename="your_data_source", servertype="DB_ORACLE", jpsroot="cn=jpsTestNode")
For more information about using the
reassociateSecurityStorecommand, see "reassociateSecurityStore" in the Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
29.5 Managing Credentials
Administrators can manage credentials for the WebCenter domain credential store using Fusion Middleware Control and WLST commands. For more information, see "Managing Credentials" in the Oracle Fusion Middleware Security Guide.
29.6 Configuring Self-Registration By Invitation in WebCenter Spaces
WebCenter Spaces supports self-registration by invitation, as described in "Enabling Self-Registration By Invitation-Only" in Oracle Fusion Middleware User's Guide for Oracle WebCenter. The self-registration 'by-invitation' feature requires that the WebCenter domain credential store contain the following password credentials:
-
map name = o.webcenter.security.selfreg -
key= o.webcenter.security.selfreg.hmackey -
user name = o.webcenter.security.selfreg.hmackey
To enable 'self-registration by invitation' in WebCenter Spaces, use Fusion Middleware Control or the WLST command createCred to create the password credentials detailed above. For example:
createCred(map="o.webcenter.security.selfreg", key="o.webcenter.security.selfreg.hmackey", type="PC", user="o.webcenter.security.selfreg.hmackey", password="<password>", url="<url>", port="<port>", [desc="<description>"])
For more information, see "Managing Credentials" in the Oracle Fusion Middleware Security Guide.