Home | Book List | Contents | Contact Us |
Go to main content
|
|
This chapter contains the following sections:
Introduction to the Microsoft Active Directory User Management Connector
Certified Components for Microsoft Active Directory User Management Connector
Usage Recommendation for the Microsoft Active Directory User Management Connector
Certified Languages for the Microsoft Active Directory User Management Connector
Architecture of Microsoft Active Directory User Management Connector
Features of the Microsoft Active Directory User Management Connector
Connector Objects Used During Target Resource Reconciliation
Note:
At some places in this guide, Microsoft Active Directory, Microsoft ADAM, and Microsoft AD LDS is referred to as the target systems.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
In the identity reconciliation (trusted source) configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager.
These are the software components and their versions required for installing and using the Active Directory connector.
The target system can be Microsoft Active Directory or Microsoft AD LDS. Certified Components lists the certified components for both target systems.
Table 1-1 Certified Components
| Item | Requirement for Microsoft Active Directory | Requirement for Microsoft AD LDS or ADAM |
|---|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
|
Target systems and target system host platforms |
The target system can be any one of the following:
|
The target system can be any one of the following:
|
|
Connector Server |
11.1.2.1.0 or later |
11.1.2.1.0 or later |
|
Other software (Software used for establishing or securing communication between Oracle Identity Manager and target system.) |
Certificate Services IIS Web Server |
Certificate Services IIS Web Server Note: You must configure SSL for the connector to perform all connector operations as expected. |
|
Microsoft .NET framework |
3.5, 4, or 4.5 Note: If you are using Microsoft .NET Framework 3.5, then apply the following patch to prevent a memory leak issue: http://support.microsoft.com/kb/981575 |
3.5, 4, or 4.5 Note: If you are using Microsoft .NET Framework 3.5, then apply the following patch to prevent a memory leak issue:http://support.microsoft.com/kb/981575 |
Depending on the Oracle Identity Manager version that you are using, you must deploy and use one of the following connectors:
Note:
At some places in this section, Microsoft Active Directory User Management connector releases 9.1.0.x and 9.0.4.x have been referred to as release 9.x.
If you are using Oracle Identity Manager release 9.1.0.1 and Microsoft Windows Server 2003 Active Directory, then you must use the 9.0.4.x version of this connector.
If you are using an Oracle Identity Manager release that is later than release 9.1.0.1 and earlier than Oracle Identity Manager 11g Release 1 (11.1.1.5.6), then you must use the 9.1.1 version of this connector.
If you are using Oracle Identity Manager 11g Release 1 (11.1.1.5.6) or later, Oracle Identity Manager 11g Release 2 (11.1.2.0.6) or later, Oracle Identity Manager 11g Release 2 PS2 (11.1.2.2.0) or later, or Oracle Identity Manager 11g Release 2 PS3 (11.1.2.3.0), then use the latest 11.1.1.x version of this connector. However, if you are using Microsoft Exchange 2003, then you must use the 9.x versions for both Microsoft Active Directory User Management and Microsoft Exchange connectors.
The connector supports the following languages:
Arabic
Chinese (Simplified)
Chinese (Traditional)
Czech
Danish
Dutch
English
Finnish
French
German
Greek
Hebrew
Hungarian
Italian
Japanese
Korean
Norwegian
Polish
Portuguese
Portuguese (Brazilian)
Romanian
Russian
Slovak
Spanish
Swedish
Thai
Turkish
Figure 1-1 shows the architecture of the connector.
The Microsoft Active Directory User Management connector is built on top of System.DirectoryServices, a collection of classes managed by .NET that makes using Microsoft Active Directory easy and convenient. In the .NET Framework, classes for managing directory objects are contained within the System.DirectoryServices namespace. The classes in System.DirectoryServices wrap Active Directory Services Interfaces (ADSI) functionality.
ADSI is a built-in component of Microsoft Windows and shipped with different providers to access directories such as WinNT for local account management, NDS for accessing Novell eDirectory (formally known as Novell Directory Services), and LDAP for accessing any directory that supports Lightweight Directory Access Protocol (LDAP) v3. This connector uses the LDAP provider to access Microsoft Active Directory.
The earlier version of this connector represented a high-level connector with many configuration settings and lookup definitions that were used to customize the provisioning process. In addition, using SSL certificate for securing communication between Oracle Identity Manager and the target system was mandatory. In contrast, the current version of the connector provides low-level operations by using the Connector Framework and the consumer application is responsible for setting up the provisioning process. By using the internal mechanism of ADSI and the .NET Framework, the default communication between the .NET Connector Server and Microsoft Active Directory is "secure." However, if you are using Microsoft AD LDS as the target system, then you must configure SSL between Oracle Identity Manger and the target system.
Note:
For performing password reset provisioning operations, the communication with the target system must be secure. If you are using Microsoft AD as the target system, there is no need to enable SSL between the .NET Connector Server and the target system. This is because the default communication between the .NET Connector Server and the target system is "secure."
However, in the case of Microsoft AD LDS, the default communication between the .NET Connector Server and Microsoft AD LDS is not "secure." Therefore, it is required to configure SSL between the .NET Connector Server and Microsoft AD LDS for the password reset functionality to work as expected.
As the current version of this connector provides low-level provisioning functionality, an integration code called Identity Connector Framework (ICF) is used.
Instead of communicating directly with the native API, ICF Common communicates with the connector framework through its API, and then calls SPI operations on a specific version of this connector. Between the Java ICF and the connector, the .NET Connector Framework resides (in the context of which the connector is running) and bridges the Java ICF and .NET connector. The connector is deployed in the .NET connector framework.
Oracle Identity Manager communicates with a .NET Connector Server over the network. The .NET Connector Server serves as a proxy to provide any authenticated application access to the current version of the connector deployed within the .NET Connector Server. Note that the Connector Server need not be on the domain controller on which the target system is running. Connector Server can be configured on any machine in the Microsoft Active Directory domain.
The Microsoft Active Directory User Management connector is a .NET connector that supports provisioning to and reconciliation from Microsoft Windows servers running, Microsoft Active Directory Domain Services (AD DS) and Microsoft Active Directory Lightweight Directory Services (AD LDS).
The Microsoft Active Directory User Management connector is implemented using the ICF. The ICF provides a container that separates the connector bundle from the application (for example, Oracle Identity Manager or Oracle Waveset). The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. The ICF is shipped along with Oracle Identity Manager. Therefore, you need not configure or modify the ICF.
See Also:
Understanding the Identity Connector Framework in Developing and Customizing Applications for Oracle Identity Manager for more information about the ICF
The connector can be configured to run in one of the following modes:
Identity reconciliation
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this form of reconciliation, OIM Users are created or updated corresponding to the creation of and updates to users on the target system. The identity reconciliation mode also supports reconciliation of objects like groups and organizations (OUs) created on the target system.
In the identity reconciliation mode, depending on the data that you want to reconcile, you use different scheduled tasks. For example, you use the Active Directory User Trusted Recon scheduled job to reconcile user data from the target system. See Reconciliation Scheduled Jobs for more information about scheduled tasks used in this mode.
Account Management
Account management is also known as target resource management. This mode of the connector enables the following operations:
Provisioning
Provisioning involves creating, updating, or deleting users on the target system through Oracle Identity Manager. When you allocate (or provision) a Microsoft Active Directory resource to an OIM User, the operation results in the creation of an account on Microsoft Active Directory for that user. In the Oracle Identity Manager context, the term "provisioning" is also used to mean updates (for example enabling or disabling) made to the target system account through Oracle Identity Manager.
Users and organizations are organized in hierarchical format on the target system. Before you can provision users to (that is, create users in) the required organizational units (OUs) on the target system, you must fetch into Oracle Identity Manager the list of OUs used on the target system. This is achieved by using a lookup synchronization scheduled job.
Similarly, before you can provision users to the required groups on the target system, you must fetch into Oracle Identity Manager the list of all groups used on the target system. This is also achieved by using a lookup synchronization scheduled job.
The connector enables group assignment provisioning operations in which you set or change the target system group membership profiles of users. The connector also supports provisioning (updating) of the Windows Terminal Services Profile attributes. Accessing these attributes involves the use of components that are native to the Microsoft Windows platform.
Target resource reconciliation
To perform target resource reconciliation, the Active Directory User Target Recon scheduled job is used. The connector applies filters to locate users to be reconciled from the target system and then fetches the attribute values of these users.
Depending on the data that you want to reconcile, you use different scheduled jobs. For example, you use the Active Directory User Target Recon scheduled job to reconcile user data in the target resource mode. For more information about scheduled jobs used in this mode, see Reconciliation Scheduled Jobs.
This connector cannot propagate password changes from Microsoft Active Directory to Oracle Identity Manager. To implement this feature, you must install the Microsoft Active Directory password synchronization connector. For more information, see Oracle Identity Manager Connector Guide for Microsoft Active Directory Password Synchronization. That guide describes scenarios in which both the password synchronization connector and this connector are deployed.
The following are features of the connector:
Support for Connector Operations on User-Defined Object Classes
Support for Adding the Group Name (pre-Windows 2000) Attribute
Support for Provisioning Groups of the Security Group - Universal Group Type
Support for Provisioning and Reconciling Custom Object Categories
Support for High-Availability Configuration of the Target System
If you have multiple installations of the target system, the entries in lookup definitions (used as an input source for lookup fields during provisioning) can be linked to the target system installation from which they are copied. Therefore, during a provisioning operation, you can select lookup field values that are specific to the target system installation on which the provisioning operation is being performed.
See Lookup Definitions Synchronized with the AD and AD LDS Target Systems for more information about the format in which data is stored in dependent lookup definitions.
After you deploy the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, incremental reconciliation is automatically enabled. In incremental reconciliation, user accounts that have been added or modified since the last reconciliation run are fetched into Oracle Identity Manager.
You can perform a full reconciliation run at any time.
See Full Reconciliation and Incremental Reconciliation for more information.
You can set a reconciliation filter as the value of the Filter attribute of the user reconciliation job. This filter specifies the subset of added and modified target system records that must be reconciled.
See Limited Reconciliation for more information.
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch.
See Batched Reconciliation for more information.
You can configure the connector for reconciliation of deleted user records. In target resource mode, if a user record is deleted on the target system, then the corresponding AD User resource is revoked from the OIM User. In trusted source mode, if a user record is deleted on the target system, then the corresponding OIM User is deleted.
See Scheduled Jobs for Reconciliation of Deleted User Records for more information about scheduled jobs used for reconciling deleted user records.
You can configure the connector for reconciling information about groups deleted in the target system.
In target resource mode, if a group is deleted on the target system, then the corresponding group is revoked from Oracle Identity Manager.
See Scheduled Job for Reconciliation of Deleted Groups for more information about the scheduled job used for reconciling deleted groups.
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation. The following sections provide more information:
The Active Directory User Management connector is written using Microsoft .NET. A .NET environment is required for the execution of this connector code. Therefore, it is mandatory for this connector to be deployed on the .NET Connector Server shipped along with the connector package. The Active Directory User Management connector operates in the context of the .NET Connector Framework, which in turn requires an application to execute. Therefore, by default, Oracle provides the .NET Connector Server to run the Active Directory User Management connector.
Connector Server is a component provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles. In other words, a connector server enables remote execution of an Oracle Identity Manager connector.
See the following sections for more information:
A connection pool is a cache of objects that represent physical connections to the target. Oracle Identity Manager connectors can use these connections to communicate with target systems. At run time, the application requests a connection from the pool. If a connection is available, then the connector uses it and then returns it to the pool. A connection returned to the pool can again be requested for and used by the connector for another operation. By enabling the reuse of connections, the connection pool helps reduce connection creation overheads like network latency, memory allocation, and authentication.
One connection pool is created for each IT resource. For example, if you have three IT resources for three installations of the target system, then three connection pools will be created, one for each target system installation.
See Setting Up the Lookup Definition for Connection Pooling for more information.
The connector supports reconciliation and provisioning operations across domains. This means that, for example, you can assign a user in one domain to a group in another domain. You can also reconcile a user record even if the user and the user's manager belong to different domains.
See Enabling Reconciliation and Provisioning Operations Across Multiple Domains for more information.
The connector can be configured to reconcile from and provision to user-defined object classes and their attributes. By default, the target system uses the user object class. The connector can be configured to accommodate user-defined object classes that you define on the target system.
See Configuring the Connector for User-Defined Object Classes for more information.
The connector provides support for adding dynamic auxiliary object classes. In addition, you can add the attributes of these dynamic auxiliary object classes for reconciliation and provisioning.
See Adding Dynamic Auxiliary Object Classes and Their Attributes to Users for more information.
During group provisioning, by default, the value that you specify for the Group Name field on the OIM process form, is entered as the value of the Group Name and Group Name (pre-Windows 2000) attributes of the target system. If you want to specify different values for the Group Name and Group Name (pre-Windows 2000) attributes in the target system, then you must create the Group Name (pre-Windows 2000) field on the OIM process form.
See Adding the Group Name (pre-Windows 2000) Attribute for more information.
The connector provides support for provisioning groups of the type Security Group - Universal. See Configuring the Connector for Provisioning Groups of the Security Group - Universal Group Type for more information.
If you are using AD LDS as the target system, then add custom object categories for provisioning and reconciliation. See Configuring the Connector for Provisioning and Reconciling Custom Object Categories for more information.
The connector supports any scripting language that has a script executor in the ICF. Currently, there are two script executor implementations: a Windows shell script executor (batch scripts) and a Boo script executor. Although Visual Basic scripts are not directly supported, a Visual Basic script can be called using a shell script.
See Action Scripts for more information.
The connector can be configured for compatibility with high-availability target system environments. It can read information about backup target system hosts from the BDCHostNames parameter of the Active Directory IT resource and apply this information when it is unable to connect to the primary host.
See Step 7 of Configuring the IT Resource for Microsoft AD and AD LDS for more information about the BDCHostNames parameter of the IT resource.
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
Lookup definitions used during connector operations can be categorized as follows:
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Organizational Unit lookup field to select an organizational unit from the list of organizational units in the lookup field. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
The following is the format in which data is stored after lookup definition synchronization:
Code Key: <IT_RESOURCE_KEY>~<LOOKUP_FIELD_VALUE>
In this format:
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
LOOKUP_FIELD_VALUE is the connector attribute value defined for code.
Sample value: 1~OU=TestOrg8,DC=matrix,DC=com
Decode: <IT_RESOURCE_NAME>~<LOOKUP_FIELD_VALUE>
In this format:
IT_RESOURCE_NAME is the name of the IT resource in Oracle Identity Manager.
LOOKUP_FIELD_VALUE is the connector attribute value defined for decode.
Sample value: Active Directory~OU=TestOrg8,DC=matrix,DC=com
For example, in the Lookup.ActiveDirectory.Groups lookup definition, values will be stored in the following format:
Code Key: <IT_RESOURCE_KEY>~<DISTINGUISHED_NAME>
Decode: <IT_RESOURCE_NAME>~<DISTINGUISHED_NAME>
During a provisioning operation, lookup fields are populated with values corresponding to the target system that you select for the operation.
The "Lookup Definition" column of Table 1-2 lists the Oracle Identity Manager lookup definitions that correspond to target system lookup fields listed in the "Target System Field" column of the table.
Table 1-2 Lookup Definitions Synchronized with the Target System
| Lookup Definition | Target System Field | Scheduled Task for Synchronization |
|---|---|---|
|
Lookup.ActiveDirectory.Groups |
The distinguishedName field of groups |
You use the Active Directory Group Lookup Recon scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
|
Lookup.ActiveDirectory.OrganizationalUnits |
The distinguishedName field of organizations |
You use the Active Directory Organization Lookup Recon scheduled job to synchronize this lookup definition. This scheduled job is discussed in Scheduled Jobs for Lookup Field Synchronization. |
This section discusses the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed. The other lookup definitions are as follows:
The Lookup.Configuration.ActiveDirectory lookup definition holds connector configuration entries that are used during target resource reconciliation and provisioning operations.
Table 1-3 lists the default entries in this lookup definition.
Note:
If you want to use dynamic auxiliary object classes, then you must add a new entry to this lookup definition. See Adding Dynamic Auxiliary Object Classes and Their Attributes to Users for more information.
If you want to use user-defined object classes, then you must update this lookup definition. See Configuring the Connector for User-Defined Object Classes for more information.
Table 1-3 Entries in the Lookup.Configuration.ActiveDirectory Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
ADLDSLockoutThreshold |
5 |
This entry holds the number of unsuccessful login attempts after which a user's account must be locked. Note: This entry is applicable only for the Microsoft AD LDS target system. |
|
AlwaysUseObjectGUID |
yes |
This entry specifies whether the GUID of an object must be used for searching records during reconciliation. Note: Do not change the value of this entry. |
|
Bundle Name |
ActiveDirectory.Connector |
This entry holds the name of the connector bundle package. Do not modify this entry. |
|
Bundle Version |
1.1.0.6380 |
This entry holds the version of the connector bundle class. Do not modify this entry. |
|
Connector Name |
Org.IdentityConnectors.ActiveDirectory.ActiveDirectoryConnector |
This entry holds the name of the connector class. Do not modify this entry. |
|
CreateHomeDirectory |
yes |
This entry holds information whether a home directory must be created. Enter |
|
Group Configuration Lookup |
Lookup.ActiveDirectory.GM.Configuration |
This entry holds the name of the lookup definition that contains group-specific configuration properties. Do not modify this entry.. |
|
NativeGuidConvention |
true |
This entry specifies whether GUID is stored in its native format. This entry is used by the connector internally. Note: Do not change the value of this entry. |
|
ObjectClass |
User |
This entry holds the name of the object class to which newly created users on the target system are assigned. If you create a custom object class, then specify the name of that object class. For example, |
|
organizationalUnit Configuration Lookup |
Lookup.ActiveDirectory.OM.Configuration |
This entry holds the name of the lookup definition that contains organization-specific configuration properties. This lookup definition is used as the configuration lookup definition when you perform reconciliation of organizational units. Do not modify this entry. |
|
PageSize |
1000 |
This entry holds the page size of records fetched in each call to the target system during a reconciliation run. Paging splits the entire result set of a query into smaller subsets called, appropriately enough, pages. In general, it is recommended to set this value to the maximum page size for simple searches. By setting the page size to the maximum value, you can minimize the network roundtrips necessary to retrieve each page, which tends to be the more expensive operation for simple searches. While it is possible to specify a PageSize greater than the MaxPageSize of the target system, the Active Directory server will ignore it and use the MaxPageSize instead. No exception will be generated in this case. In some cases, you might need to specify a smaller page size to avoid timeouts or overtaxing the server. Some queries are especially expensive, so limiting the number of results in a single page can help avoid this. |
|
Recon Date Format |
yyyyMMddHHmmss.0Z |
This entry holds the format in which the last reconciliation run timing must be displayed. |
|
SearchChildDomains |
no |
This entry determines the search scope of users, groups, or organizational units within the domain name specified as the value of the DomainName attribute. Enter Enter Note: If you enter |
|
UseDeleteTreeForAccounts |
false |
This entry specifies whether the associated leaf nodes of an __ACCOUNT__ object to be deleted are to be removed along with the object. If the value of this entry is not If you set the value of this entry to |
|
User Configuration Lookup |
Lookup.ActiveDirectory.UM.Configuration |
This entry holds the name of the lookup definition that contains user-specific configuration properties. Do not modify this entry. |
The Lookup.Configuration.ActiveDirectory.Trusted lookup definition holds connector configuration entries that are used during trusted source reconciliation.
Table 1-4 lists the default entries in this lookup definition.
Table 1-4 Entries in the Lookup.Configuration.ActiveDirectory.Trusted Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
ADLDSLockoutThreshold |
5 |
This entry holds the number of unsuccessful login attempts after which a user's account must be locked. Note: This entry is applicable only for the Microsoft AD LDS target system. |
|
AlwaysUseObjectGUID |
yes |
This entry specifies whether the GUID of an object must be used for searching records during reconciliation. If the object class is of a non-account type and if you set the value of this entry to |
|
Bundle Name |
ActiveDirectory.Connector |
This entry holds the name of the connector bundle package. Do not modify this entry. |
|
Bundle Version |
1.1.0.6380 |
This entry holds the version of the connector bundle class. Do not modify this entry. |
|
Connector Name |
Org.IdentityConnectors.ActiveDirectory.ActiveDirectoryConnector |
This entry holds the name of the connector class. Do not modify this entry. |
|
MaintainHierarchy |
no |
Enter |
|
NativeGuidConvention |
true |
This entry specifies whether GUID is stored in its native format. This entry is used by the connector internally. Note: Do not change the value of this entry. |
|
ObjectClass |
User |
This entry holds the name of the object class to which newly created users on the target system are assigned. If you create a custom object class, then specify the name of that object class. For example, |
|
organizationalUnit Configuration Lookup |
Lookup.ActiveDirectory.OM.Configuration.Trusted |
This entry holds the name of the lookup definition that contains organization-specific configuration properties. This lookup definition is used as the configuration lookup definition when you perform reconciliation of organizational units. Do not modify this entry. |
|
PageSize |
1000 |
This entry holds the page size of records fetched in each call to the target system during a reconciliation run. Paging splits the entire result set of a query into smaller subsets called, appropriately enough, pages. In general, it is recommended to set this value to the maximum page size for simple searches. By setting the page size to the maximum value, you can minimize the network roundtrips necessary to retrieve each page, which tends to be the more expensive operation for simple searches. While it is possible to specify a PageSize greater than the MaxPageSize of the target system, the Active Directory server will ignore it and use the MaxPageSize instead. No exception will be generated in this case. In some cases, you might need to specify a smaller page size to avoid timeouts or overtaxing the server. Some queries are especially expensive, so limiting the number of results in a single page can help avoid this. |
|
Recon Date Format |
yyyyMMddHHmmss.0Z |
This entry holds the format in which the last reconciliation run timing must be displayed. |
|
SearchChildDomains |
no |
This entry determines the search scope of users, groups, or organizational units within the domain name specified as the value of the DomainName attribute. Enter Enter |
|
User Configuration Lookup |
Lookup.ActiveDirectory.UM.Configuration.Trusted |
This entry holds the name of the lookup definition that contains user-specific configuration properties. Do not modify this entry. |
This section discusses the following lookup definitions for user operations:
The Lookup.ActiveDirectory.UM.Configuration lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during user management operations when your target system is configured as a target resource.
Table 1-5 lists the default entries in this lookup definition.
Table 1-5 Entries in the Lookup.ActiveDirectory.UM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.ActiveDirectory.UM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.ActiveDirectory.UM.ProvAttrMap for more information about this lookup definition. |
|
Provisioning Validation Lookup |
Lookup.ActiveDirectory.UM.ProvValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values entered on the process form during provisioning operations. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
|
Recon Attribute Map |
Lookup.ActiveDirectory.UM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.ActiveDirectory.UM.ReconAttrMap for more information about this lookup definition. |
|
Recon Transformation Lookup |
Lookup.ActiveDirectory.UM.ReconTransformation |
This entry holds the name of the lookup definition that is used to configure transformation of attribute values that are fetched from the target system during user reconciliation. See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition. |
|
Recon Validation Lookup |
Lookup.ActiveDirectory.UM.ReconValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values that are fetched from the target system during reconciliation. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
The Lookup.ActiveDirectory.UM.Configuration.Trusted lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during trusted source user reconciliation runs.
Table 1-6 lists the default entries in this lookup definition.
Table 1-6 Entries in the Lookup.ActiveDirectory.UM.Configuration.Trusted Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Recon Attribute Defaults |
Lookup.ActiveDirectory.UM.ReconAttrMap.Trusted.Defaults |
This entry holds the name of the lookup definition that maps reconciliation fields to their default values. See Lookup.ActiveDirectory.UM.ReconAttrMap.Trusted.Defaults for more information. |
|
Recon Attribute Map |
Lookup.ActiveDirectory.UM.ReconAttrMap.Trusted |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.ActiveDirectory.UM.ReconAttrMap for more information about this lookup definition. |
The Lookup.ActiveDirectory.UM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes. This lookup definition is preconfigured and is used during provisioning operations.
You can add entries in this lookup definitions if you want to map new target system attributes for provisioning. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
Table 1-7 Default Entries in the Lookup.ActiveDirectory.UM.ProvAttrMap Lookup Definition
| Code key (Process Form Field) | Decode (Target System Field) | Description |
|---|---|---|
|
Manager Name |
manager |
Manager name You must enter the manager name in the DN format. For example: |
|
Terminal Home Directory |
TerminalServicesHomeDirectory Part of the data stored in the userParameters field Note: This field does not exist in Microsoft AD LDS. A value that you enter in this field would be ignored during provisioning operations in Microsoft AD LDS. |
Full path of the home directory for the Terminal Server userSample value: During a provisioning operation, you must enter the full, absolute path of the home directory, as shown in the sample value. |
|
UD_ADUSRC~Group Name[Lookup] |
__GROUPS__ |
Group name |
|
Terminal Profile Path |
TerminalServicesProfilePath Part of the data stored in the userParameters field Note: This field does not exist in Microsoft AD LDS. A value that you enter in this field would be ignored during provisioning operations in Microsoft AD LDS. |
Profile that is used when the user logs on to a Terminal Server The profile can be roaming or mandatory. A roaming profile remains the same, regardless of the computer from which the user logs in. The user can make changes to a roaming profile, but not to a mandatory profile. Any changes a user makes while logged in with a mandatory profile are retained only for that Terminal Services session. The changes are lost when the user starts another Terminal Services session. |
|
Account Expiration Date[DATE] This is a date field. |
__PASSWORD_EXPIRATION_DATE__ |
Date when the account expires |
|
Street |
streetAddress |
Street address |
|
Zip |
postalCode |
ZIP code |
|
Middle Name This field is on both the process form and the OIM User form. During a provisioning operation, the Middle Name field on the process form is prepopulated with the value entered in the Middle Name field on the OIM User form. |
middleName |
Initials for the user's middle name |
|
User Must Change Password At Next Logon This is a check box. |
__PASSWORD_EXPIRED__ |
Flag that indicates whether or not the user must change the password at next logon. If the value is yes (check box is selected), then the user must change the password at next logon. |
|
Office |
physicalDeliveryofficeName |
Office Location |
|
Home Phone |
homePhone |
Home phone number |
|
City |
l |
City |
|
Account is Locked out This is a check box |
__LOCK_OUT__ |
Specifies whether the user account must be locked or unlocked |
|
Last Name This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the Last Name field on the process form is prepopulated with the value entered in the Last Name field on |
sn |
Last name |
|
IP Phone |
ipPhone |
IP phone number |
|
Mobile |
mobile |
Mobile number |
|
Telephone Number |
telephoneNumber |
Telephone number |
|
State |
st |
State |
|
Fax |
facsimileTelephoneNumber |
Fax number |
|
First Name This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the First Name field on the process form is prepopulated with the value entered in the First Name field on the OIM User form. |
givenName |
First name |
|
Password This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the Password field on the process form is prepopulated with the value entered in the Password field on the OIM User form. If SSL is configured between Oracle Identity Manager and the target system, then the Password field on the process form is a mandatory field. |
__PASSWORD__ This connector uses ADSI to set the password of the user. It uses the IADsUser#SetPassword API. This API sets the user's unicodePwd attribute. See the following URL for more information:
|
User's password in UTF-8 format |
|
Full Name |
displayName |
Display name for a user During a Create User provisioning operation, the cn and displayName fields are populated with a combination of the user's first name, middle initial, and last name entered on the OIM User form. The full name is displayed in the following format on the process form: FIRSTNAME MIDDLE_INITIAL. LASTNAME For example: If the middle initial is not entered, then the name is displayed as, for example, John Doe. During an Update provisioning operation, only the value in the displayName field is updated. |
|
Redirection Mail Id |
__MAILREDIRECTION__ |
E-mail address to which e-mail sent to the user must be redirected This e-mail address overrides the one set in the E Mail field. |
|
__NAME__ |
__NAME__="CN=$(Common_Name),$(Organization_Name)" |
User name with full DN |
|
Password Not Required This is a check box. |
PasswordNotRequired |
Specifies whether or not Password is required. If it is true, then there is no need to specify the password. If it is false, then password is required. |
|
Terminal Allow Login This is a check box. |
AllowLogon This field does not exist in Microsoft ADAM and AD LDS. A value that you enter in this field would be ignored during provisioning operations in Microsoft ADAM and AD LDS. |
Specifies whether or not the user is permitted to log on to the Terminal Server |
|
Country |
c |
Country |
|
User Id This field is on both the process form and the OIM User form. It is a mandatory field. During a provisioning operation, the User ID field on the process form is prepopulated with the value entered in the User |
sAMAccountName This is a mandatory field in Microsoft Active Directory. This field does not exist in Microsoft ADAM and AD LDS. |
User's logon name |
|
Pager |
pager |
Pager number |
|
Organization Name[LOOKUP,IGNORE] |
IGNORED |
Name of the organization |
|
Unique Id This is a hidden field on both the process form and the OIM User form. |
__UID__ |
Object GUID of the user |
|
E Mail This field is on both the process form and the OIM User form. |
|
Email address |
|
Common Name[IGNORE] |
IGNORED |
Common name of the user |
|
Title |
title |
Title |
|
Company |
company |
Company |
|
Password Never Expires This is a check box. |
PasswordNeverExpires |
Flag that controls the Password Never Expires property |
|
Department |
department |
Department |
|
User Principal Name This is a mandatory field. |
userPrincipalName This is a mandatory field. Note: The value for UserPrincipalName must be entered in the format shown in the following example: If the root context is |
The user principal name is the domain-specific name of the user. This field is pre-populated on the Administrative and User Console. The format is as follows: USER_ID_VALUE@UPN_DOMAIN_VALUE Note: When you update this field, you can change the User ID part but you must not change the domain name. If you change the domain name, then the user will not be matched on the target system. |
|
Homedirectory |
homeDirectory |
Home directory of the user |
|
Post Office Box |
postOfficeBox |
Post-office box |
The Lookup.ActiveDirectory.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. This lookup definition is preconfigured and is used during target resource reconciliation.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
Table 1-8 Entries in the Lookup.ActiveDirectory.UM.ReconAttrMap Lookup Definition
| Code Key (Resource Object Field) | Decode (Target System Field) | Description |
|---|---|---|
|
Department |
department |
Department |
|
Full Name |
displayName |
Full name |
|
Terminal Home Directory This is a string data type field. |
TerminalServicesHomeDirectory This field does not exist in Microsoft AD LDS. |
Full path of the home directory for the Terminal Server user Note: Reconciliation of values in this field is enabled by the Remote Manager. |
|
Unique Id |
__UID__ |
GUID of each user on the target system |
|
Mobile |
mobile |
Mobile number |
|
Terminal Profile Path This is a string data type field. |
TerminalServicesProfilePath This field does not exist in Microsoft AD LDS. |
Profile that is used when the user logs on to a Terminal Server The profile can be roaming or mandatory. A roaming profile remains the same, regardless of the computer from which the user logs in. The user can make changes to a roaming profile, but not to a mandatory profile. Any changes a user makes while logged in with a mandatory profile are retained only for that Terminal Services session. Changes are lost when the user starts another Terminal Services session. |
|
Home Phone |
homePhone |
Home phone number |
|
Company |
company |
Company |
|
Account is Locked out This is a check box. |
__LOCK_OUT__ |
Specifies whether the user account must be locked or unlocked |
|
Middle Name |
middleName |
Initials for the user's middle name |
|
Organization Name[LOOKUP] |
ad_container |
Organization name on the target system |
|
IP Phone |
ipPhone |
IP phone number |
|
Common Name This is a mandatory field. |
cn This is a mandatory field. |
Common name on the target system You can change the value of this field. |
|
State |
st |
State |
|
Country This is a lookup field. |
c |
Country |
|
Street |
streetAddress |
Street address |
|
City |
l |
City |
|
User Principal Name This is a mandatory field. |
userPrincipalName This is a mandatory field on the target system. |
The user principal name is the domain-specific name of the user. |
|
Last Name This is a mandatory field. |
sn This is a mandatory field. |
Last name |
|
E Mail |
|
Email address |
|
User Must Change Password At Next Logon This is a check box. |
__PASSWORD_EXPIRED__ |
Flag that indicates whether or not the user must change the password at next logon.If the value is yes (check box is selected), then the user must change the password at next logon. |
|
Fax |
facsimileTelephoneNumber |
Fax number |
|
Homedirectory |
homeDirectory |
Home directory for each user on the target system. |
|
Manager Name |
manager |
Manager name |
|
Password Never Expires This is a check box. |
PasswordNeverExpires |
Flag that controls the Password Never Expires property |
|
Terminal Allow Login This is a check box. |
AllowLogon Note: This field does not exist in Microsoft AD LDS. |
Specifies whether or not the user is permitted to log on to the Terminal Server |
|
First Name |
givenName This is a mandatory field. |
First name |
|
Pager |
pager |
Pager number |
|
Account Expiration Date[DATE] This is a date field. |
__PASSWORD_EXPIRATION_DATE__ |
Date when the account expires |
|
groups~Group Name[LOOKUP] |
__GROUPS__ |
Group name |
|
Office |
physicalDeliveryofficeName |
Office location |
|
Telephone Number |
telephoneNumber |
Telephone number |
|
Post Office Box |
postOfficeBox |
Post-office box |
|
User Id This is a mandatory field. |
sAMAccountName This is a mandatory field in Microsoft Active Directory. This field does not exist in Microsoft AD LDS. |
User's logon name |
|
Title |
title |
Title |
|
Status |
__ENABLE__ |
The value that controls the account is enabled or disabled |
The Lookup.ActiveDirectory.UM.ProvValidation lookup definition is used to configure validation of attribute values entered on the process form during provisioning operations. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.UM.ReconTransformation lookup definition is used to configure transformation of attribute values that are fetched from the target system during user reconciliation. See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.UM.ReconValidation lookup definition is used to configure validation of attribute values that are fetched from the target system during reconciliation. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.UM.ReconAttrMap.Trusted lookup definition holds mappings between resource object fields and target system attributes. This lookup definition is preconfigured and used during trusted source user reconciliation runs.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
Table 1-9 Entries in the Lookup.ActiveDirectory.UM.ReconAttrMap.Trusted Lookup Definition
| Code Key (OIM User Form Field) | Decode (Target System Field) | Description |
|---|---|---|
|
E Mail |
|
Email address |
|
Employee Type |
OIM Employee Type |
Employee type of the OIM User |
|
First Name This is a mandatory field. |
givenName This is a mandatory field. |
First name |
|
Last Name This is a mandatory field. |
sn This is a mandatory field. |
Last name For a record fetched during trusted source reconciliation, if there is no value in this attribute, then the value from the Common Name attribute is populated in the Last Name field on the process form. |
|
Manager ID |
Manager Id |
Manager name |
|
Middle Name |
middleName |
Middle name |
|
objectGUID |
__UID__ |
Object GUID of each user on the target system |
|
Organization This is a mandatory field. |
__PARENTCN__ |
This is the name of the organization to which users belong if you set the value of the MaintainHierarchy entry of the Lookup.Configuration.ActiveDirectory.Trusted lookup definition to If Maintain Hierarchy is set to |
|
TrustedStatus[TRUSTED] |
__ENABLE__ |
This field stores the status of the user account. |
|
User Id This is a mandatory field. |
sAMAccountName |
User's logon name |
|
User Type |
OIM User Type |
Type of the OIM User Values can be one of the following:
|
The Lookup.ActiveDirectory.UM.ReconAttrMap.TrustedDefaults lookup definition holds mappings between reconciliation fields and their default values. This lookup definition is used when there is a mandatory field on the OIM User form, but no corresponding field in the target system from which values can be fetched during trusted source reconciliation.
This lookup definition is empty by default. If you add entries to this lookup definition, the Code Key and Decode values must be in the following format:
Code Key: Name of the reconciliation field of the AD User resource object
Decode: Corresponding default value to be displayed
For example, assume a field named Preferred Language is a mandatory field on the OIM User form. Suppose the target system contains no field that stores information about the preferred language of communication for a user account. During reconciliation, no value for the Preferred Language field is fetched from the target system. However, as the Preferred Language field cannot be left empty, you must specify a value for this field. Therefore, create an entry in this lookup definition with the Code Key value set to Preferred Language and Decode value set to English. This implies that the value of the Preferred Language field on the OIM User form displays English for all user accounts reconciled from the target system.
This section discussed the following lookup definitions for group operations:
The Lookup.ActiveDirectory.GM.Configuration lookup definition holds configuration entries that are specific to the group object type. This lookup definition is used during group management operations when your target system is configured as a target resource.
Table 1-5 lists the default entries in this lookup definition.
Table 1-10 Entries in the Lookup.ActiveDirectory.GM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.ActiveDirectory.GM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.ActiveDirectory.GM.ProvAttrMap for more information about this lookup definition. |
|
Provisioning Validation Lookup |
Lookup.ActiveDirectory.GM.ProvValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values entered on the process form during provisioning operations. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
|
Recon Attribute Defaults |
Lookup.ActiveDirectory.GM.ReconAttrMap.Defaults |
This entry holds the name of the lookup definition that maps fields on the group form and their default values. See Lookup.ActiveDirectory.GM.ReconAttrMap.Defaults for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.ActiveDirectory.GM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.ActiveDirectory.GM.ReconAttrMap for more information about this lookup definition. |
|
Recon Transformation Lookup |
Lookup.ActiveDirectory.GM.ReconTransformation |
This entry holds the name of the lookup definition that is used to configure transformation of attribute values that are fetched from the target system during user reconciliation. See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition. |
|
Recon Validation Lookup |
Lookup.ActiveDirectory.GM.ReconValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values that are fetched from the target system during reconciliation. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
The Lookup.ActiveDirectory.GM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes. This lookup definition is preconfigured and is used during group provisioning operations.
You can add entries in this lookup definitions if you want to map new target system attributes for provisioning. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
Table 1-11 Default Entries in the Lookup.ActiveDirectory.GM.ProvAttrMap
| Group Field on Oracle Identity Manager | Target System Field | Description |
|---|---|---|
|
__NAME__ |
__NAME__="CN=${Group_Name},${Organization_Name}" |
Group name with full DN |
|
Display Name |
displayName |
Display name for a group |
|
Group Name |
sAMAccountName |
Group name |
|
Group Type |
groupType |
Group type |
|
Organization Name[LOOKUP,IGNORE] |
IGNORED |
Name of the organization to which the group belongs |
|
Unique Id |
__UID__ |
Object GUID of the group |
The Lookup.ActiveDirectory.GM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. This lookup definitions is used during reconciliation. This lookup definition is preconfigured. Table 1-15 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectory.GM.ProvValidation lookup definition is used to configure validation of attribute values entered on the process form during group provisioning operations. See Configuring Validation of Data During Reconciliation and Provisioning or more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.GM.ReconTransformation lookup definition is used to configure transformation of attribute values that are fetched from the target system during user reconciliation. See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.GM.ReconValidation lookup definition is used to configure validation of attribute values that are fetched from the target system during group reconciliation. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.GM.ReconAttrMap.Defaults lookup definition holds mappings between reconciliation fields (for group) and their default values. This lookup definition is used when there is a mandatory field on the group form, but no corresponding field in the target system from which values can be fetched during group reconciliation.
This lookup definition is empty by default. If you add entries to this lookup definition, then the Code Key and Decode values must be in the following format:
Code Key: Name of the reconciliation field of the AD Group resource object
Decode: Corresponding default value to be displayed
For example, assume a field named Group ID is a mandatory field on the group form. Suppose the target system contains no field that stores information about the group ID for an account. During reconciliation, no value for the Group ID field is fetched from the target system. However, as the Group ID field cannot be left empty, you must specify a value for this field. Therefore, create an entry in this lookup definition with the Code Key value set to Group ID and Decode value set to GRP1223. This implies that the value of the Group ID field on the group form displays GRP1223 for all accounts reconciled from the target system.
The Lookup.ActiveDirectory.GroupTypes lookup definition holds information about group types that you can select for the group that you create through Oracle Identity Manager. The following is the format of the Code Key and Decode values in this lookup definition:
Code Key: Group type code on the target system
Decode: Corresponding group type to be displayed in the Group Type lookup field of the OIM User form
This section discusses the following lookup definitions for organizational unit operations:
The Lookup.ActiveDirectory.OM.Configuration lookup definition holds configuration entries that are specific to the organizational unit object type. This lookup definition is used during organizational unit management operations when your target system is configured as a target resource.
Table 1-5 lists the default entries in this lookup definition.
Table 1-12 Entries in the Lookup.ActiveDirectory.OM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.ActiveDirectory.OM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.ActiveDirectory.OM.ProvAttrMap for more information about this lookup definition. |
|
Provisioning Validation Lookup |
Lookup.ActiveDirectory.OM.ProvValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values entered on the process form during provisioning operations. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
|
Recon Attribute Defaults |
Lookup.ActiveDirectory.OM.ReconAttrMap.Defaults |
This entry holds the name of the lookup definition that maps fields on the organizational unit form and their default values. See Lookup.ActiveDirectory.OM.ReconAttrMap.Defaults for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.ActiveDirectory.OM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.ActiveDirectory.OM.ReconAttrMap for more information about this lookup definition. |
|
Recon Transformation Lookup |
Lookup.ActiveDirectory.OM.ReconTransformation |
This entry holds the name of the lookup definition that is used to configure transformation of attribute values that are fetched from the target system during user reconciliation. See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition. |
|
Recon Validation Lookup |
Lookup.ActiveDirectory.OM.ReconValidation |
This entry holds the name of the lookup definition that is used to configure validation of attribute values that are fetched from the target system during reconciliation. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition. |
The Lookup.ActiveDirectory.OM.Configuration.Trusted lookup definition holds configuration entries that are specific to the organizational unit object type. This lookup definition is used during trusted source reconciliation runs for organizational units.
Table 1-13 lists the default entries in this lookup definition.
Table 1-13 Entries in the Lookup.ActiveDirectory.OM.Configuration.Trusted Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Recon Attribute Defaults |
Lookup.ActiveDirectory.OM.ReconAttrMap.Defaults |
This entry holds the name of the lookup definition that maps fields on the organizational unit form and their default values. See Lookup.ActiveDirectory.OM.ReconAttrMap.Defaults for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.ActiveDirectory.OM.ReconAttrMap.Trusted |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.ActiveDirectory.OM.ReconAttrMap.Trusted for more information about this lookup definition. |
The Lookup.ActiveDirectory.OM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes. This lookup definition is used during provisioning. This lookup definition is preconfigured. Table 1-21 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for provisioning. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectory.OM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. This lookup definitions is used during reconciliation of organizational units. This lookup definition is preconfigured. Table 1-16 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectory.OM.ProvValidation lookup definition is used to configure validation of attribute values entered on the process form during provisioning operations for organizational units. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.OM.ReconTransformation lookup definition is used to configure transformation of attribute values that are fetched from the target system during reconciliation of organizational units. See Configuring Transformation of Data During Reconciliation for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.OM.ReconValidation lookup definition is used to configure validation of attribute values that are fetched from the target system during reconciliation. See Configuring Validation of Data During Reconciliation and Provisioning for more information about adding entries in this lookup definition.
The Lookup.ActiveDirectory.OM.ReconAttrMap.Trusted lookup definition holds mappings between resource object fields and target system attributes. This lookup definitions is used during trusted source reconciliation runs for organizational units. This lookup definition is preconfigured. Table 1-23 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectory.OM.ReconAttrMap.Defaults lookup definition holds mappings between fields on the organizational unit form and their default values. This lookup definition is used when there is a mandatory field on the organizational unit form, but no corresponding field in the target system from which values can be fetched during organizational unit reconciliation.
This lookup definition is empty by default. If you add entries to this lookup definition, then the Code Key and Decode values must be in the following format:
Code Key: Name of the reconciliation field of the AD Organizational Unit resource object
Decode: Corresponding default value to be displayed
For example, assume a field named Organization ID is a mandatory field on the organizational unit form. Suppose the target system contains no field that stores information about the organization ID for an account. During reconciliation, no value for the Organization ID field is fetched from the target system. However, as the Organization ID field cannot be left empty, you must specify a value for this field. Therefore, create an entry in this lookup definition with the Code Key value set to Organization ID and Decode value set to ORG1332. This implies that the value of the Organization ID field on the organizational unit form displays ORG1332 for all accounts reconciled from the target system.
This section discusses the following lookup definitions for AD LDS:
The Lookup.ActiveDirectoryLDS.UM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes for AD LDS. This lookup definition is used during provisioning. This lookup definition is preconfigured.
You can add entries in this lookup definitions if you want to map new target system attributes for provisioning. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectoryLDS.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes for AD LDS. This lookup definition is used during reconciliation. This lookup definition is preconfigured.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectoryLDS.UM.ReconAttrMap.Trusted lookup definition holds mappings between resource object fields and target system attributes for AD LDS. This lookup definitions is used during trusted source user reconciliation runs. This lookup definition is preconfigured.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectoryLDS.GM.ProvAttrMap lookup definition holds mappings between group process form fields and target system attributes for AD LDS. This lookup definition is used during provisioning. This lookup definition is preconfigured.
You can add entries in this lookup definitions if you want to map new target system attributes for provisioning. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
The Lookup.ActiveDirectoryLDS.GM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes for AD LDS. This lookup definition is used during reconciliation of groups. This lookup definition is preconfigured.
You can add entries in this lookup definitions if you want to map new target system attributes for reconciliation. See Extending the Functionality of the Microsoft Active Directory User Management Connector for more information.
Target resource reconciliation involves fetching data about newly created or modified accounts on the target system and using this data to add or modify resources assigned to OIM Users.
The Active Directory User Target Recon scheduled job is used to initiate a target resource reconciliation run. This scheduled task is discussed in Scheduled Jobs for Reconciliation of User Records.
See Also:
Managing Reconciliation in Performing Self Service Tasks with Oracle Identity Manager for conceptual information about reconciliation
This section discusses the following topics:
The Lookup.ActiveDirectory.UM.ReconAttrMap lookup definition maps user resource object fields and target system attributes. This lookup definition is used for performing target resource user reconciliation runs.
In this lookup definition, entries are in the following format:
Code Key: Reconciliation field of the resource object
Decode: Name of the target system attribute
Table 1-14 lists the entries in this lookup definition.
Table 1-14 Entries in the Lookup.ActiveDirectory.UM.ReconAttrMap Lookup Definition
| Resource Object Field | Target System Field | Description |
|---|---|---|
|
Department |
department |
Department |
|
Full Name |
displayName |
Full name |
|
Terminal Home Directory This is a string data type field. |
TerminalServicesHomeDirectory This field does not exist in Microsoft AD LDS. |
Full path of the home directory for the Terminal Server user Note: Reconciliation of values in this field is enabled by the Remote Manager. |
|
Unique Id |
__UID__ |
GUID of each user on the target system |
|
Mobile |
mobile |
Mobile number |
|
Terminal Profile Path This is a string data type field. |
TerminalServicesProfilePath This field does not exist in Microsoft AD LDS. |
Profile that is used when the user logs on to a Terminal Server The profile can be roaming or mandatory. A roaming profile remains the same, regardless of the computer from which the user logs in. The user can make changes to a roaming profile, but not to a mandatory profile. Any changes a user makes while logged in with a mandatory profile are retained only for that Terminal Services session. Changes are lost when the user starts another Terminal Services session. |
|
Home Phone |
homePhone |
Home phone number |
|
Company |
company |
Company |
|
Account is Locked out This is a check box. |
__LOCK_OUT__ |
Specifies whether the user account must be locked or unlocked |
|
Middle Name |
middleName |
Initials for the user's middle name |
|
Organization Name[LOOKUP] |
ad_container |
Organization name on the target system |
|
IP Phone |
ipPhone |
IP phone number |
|
Common Name This is a mandatory field. |
cn This is a mandatory field. |
Common name on the target system You can change the value of this field. |
|
State |
st |
State |
|
Country This is a lookup field. |
c |
Country |
|
Street |
streetAddress |
Street address |
|
City |
l |
City |
|
User Principal Name This is a mandatory field. |
userPrincipalName This is a mandatory field on the target system. |
The user principal name is the domain-specific name of the user. |
|
Last Name This is a mandatory field. |
sn This is a mandatory field. |
Last name |
|
E Mail |
|
Email address |
|
User Must Change Password At Next Logon This is a check box. |
__PASSWORD_EXPIRED__ |
Flag that indicates whether or not the user must change the password at next logon.If the value is yes (check box is selected), then the user must change the password at next logon. |
|
Fax |
facsimileTelephoneNumber |
Fax number |
|
Homedirectory |
homeDirectory |
Home directory for each user on the target system. |
|
Manager Name |
manager |
Manager name |
|
Password Never Expires This is a check box. |
PasswordNeverExpires |
Flag that controls the Password Never Expires property |
|
Terminal Allow Login This is a check box. |
AllowLogon Note: This field does not exist in Microsoft AD LDS. |
Specifies whether or not the user is permitted to log on to the Terminal Server |
|
First Name |
givenName This is a mandatory field. |
First name |
|
Pager |
pager |
Pager number |
|
Account Expiration Date[DATE] This is a date field. |
__PASSWORD_EXPIRATION_DATE__ |
Date when the account expires |
|
groups~Group Name[LOOKUP] |
__GROUPS__ |
Group name |
|
Office |
physicalDeliveryofficeName |
Office location |
|
Telephone Number |
telephoneNumber |
Telephone number |
|
Post Office Box |
postOfficeBox |
Post-office box |
|
User Id This is a mandatory field. |
sAMAccountName This is a mandatory field in Microsoft Active Directory. This field does not exist in Microsoft AD LDS. |
User's logon name |
|
Title |
title |
Title |
|
Status |
__ENABLE__ |
The value that controls the account is enabled or disabled |
The Lookup.ActiveDirectory.GM.ReconAttrMap lookup definition maps user resource object fields and target system attributes. This lookup definition is used for performing target resource group reconciliation runs.
Table 1-15 lists the group fields of the target system from which values are fetched during reconciliation. The Active Directory Group Recon scheduled job is used to reconcile group data.
Table 1-15 Entries in the Lookup.ActiveDirectory.GM.ReconAttrMap
| Group Field on Oracle Identity Manager | Microsoft Active Directory Field | Description |
|---|---|---|
|
Display Name |
displayName |
Display name for a group |
|
Group name |
sAMAccountName |
Group name |
|
Group Type |
groupType |
Group type |
|
OIM Org Name |
sAMAccountName |
OIM organization name Note that this value does not contain the DN. |
|
Organization Name[LOOKUP] |
ad_container |
Organization name with DN format For example, |
|
Org Name |
sAMAccountName |
Organization name without DN format |
|
Org Type |
OIM Organization Type |
Organization type |
|
Unique Id |
__UID__ |
Object GUID of the group |
The Lookup.ActiveDirectory.OM.ReconAttrMap lookup definition maps organization resource object fields and target system attributes. This lookup definition is used for performing target resource reconciliation runs for organizational units
Table 1-16 lists the organizational unit fields of the target system from which values are fetched during reconciliation.
Table 1-16 Entries in the Lookup.ActiveDIrectory.OM.ReconAttrMap
| Organization Field on Oracle Identity Manager | Microsoft Active Directory Field | Description |
|---|---|---|
|
Container[LOOKUP] |
ad_container |
Organization name with DN format.For example, |
|
Display Name |
ou |
Display name for an organizational unit |
|
Unique Id |
__UID__ |
Object GUID of the organizational unit |
See Also:
Reconciliation Engine in Performing Self Service Tasks with Oracle Identity Manager for generic information about reconciliation matching and action rules
The following is the process matching rule:
Rule name: AD User Target Recon Rule
Rule element: (ObjectGUID Equals Unique Id) OR (User Login Equals User Id)
In the first rule component:
ObjectGUID is the objectGUID of the resource assigned to the OIM User.
Unique Id is the ID that uniquely identifies a user account. Unique Id is mapped to UID, which is the GUID value of the user account in the target system
In the second rule component:
User Login is the User ID field on the OIM User form.
User Id is the sAMAccountName field of Microsoft Active Directory or the userPrincipalName field of Microsoft ADAM.
This rule supports the following scenarios:
You can provision multiple Microsoft Active Directory resources to the same OIM User, either on Oracle Identity Manager or directly on the target system.
You can change the user ID of a user on the target system.
This is illustrated by the following use cases:
Use case 1: You provision an AD account for an OIM User, and you also create an account for the user directly on the target system.
When the first rule condition is applied, no match is found. Then, the second rule condition is applied and it is determined that a second account has been given to the user on the target system. Details of this second account are associated with the OIM User by the reconciliation engine.
Use case 2: An OIM User has an AD account. You then change the user ID of the user on the target system.
During the next reconciliation run, application of the first rule condition helps match the resource with the record.
After you deploy the connector, you can view the reconciliation rule for target resource reconciliation by performing the following steps:
Note:
Perform the following procedure only after the connector is deployed.
Table 1-17 lists the action rules for target resource reconciliation.
Table 1-17 Action Rules for Target Resource Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Assign to Authorizer With Least Load |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. For information about setting a reconciliation action rule, see
Setting a Reconciliation Action Rule (Developing Identity Connectors using Java)
Setting a Reconciliation Action Rule (Developing Identity Connectors using .net)
in Developing and Customizing Applications for Oracle Identity Manager.
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
See Also:
Managing Provisioning Tasks in Performing Self Service Tasks with Oracle Identity Manager for conceptual information about provisioning
The following topics are discussed:
Table 1-18 lists the supported user provisioning functions and the adapters that perform these functions. The functions listed in the table correspond to either a single or multiple process tasks.
Table 1-18 Provisioning Functions
| Function | Adapter |
|---|---|
|
User Provisioning Functions |
|
|
Create a user account |
ADIDC Create Object |
|
Delete a user account |
ADIDC Delete Object |
|
Enable a disabled user account |
ADIDC Enable User |
|
Disable a user account |
ADIDC Disable User |
|
Update the password |
ADIDC Return Text Value |
|
Update the redirection e-mail address |
ADIDC Update Attribute Value |
|
Update the zip code |
ADIDC Update Attribute Value |
|
Update the terminal home directory |
ADIDC Update Attribute Value |
|
Update the pager |
ADIDC Update Attribute Value |
|
Update the IP phone |
ADIDC Update Attribute Value |
|
Update the first name |
ADIDC Update Attribute Value |
|
Update the title |
ADIDC Update Attribute Value |
|
Update the user account principal name |
ADIDC Update Attribute Value |
|
Update the middle name |
ADIDC Update Attribute Value |
|
Update the account expiration date |
ADIDC Update Attribute Value |
|
Update the password never expires flag |
ADIDC Update Attribute Value |
|
Update the password not required flag |
ADIDC Update Attribute Value |
|
Update organization name |
ADIDC Update Attribute Value |
|
Update the company name |
ADIDC Update Attribute Value |
|
Update the account is locked flag |
ADIDC Update Attribute Value |
|
Update the last name |
ADIDC Update Attribute Value |
|
Update the user home directory |
ADIDC Update Attribute Value |
|
Update the post office box |
ADIDC Update Attribute Value |
|
Update the terminal allow login field |
ADIDC Update Attribute Value |
|
Update the state |
ADIDC Update Attribute Value |
|
Update the mobile number |
ADIDC Update Attribute Value |
|
Update the telephone number |
ADIDC Update Attribute Value |
|
Update the street |
ADIDC Update Attribute Value |
|
Update the country |
ADIDC Update Attribute Value |
|
Update the fax |
ADIDC Update Attribute Value |
|
Update the e-mail ID |
ADIDC Update Attribute Value |
|
Update the terminal profile path |
ADIDC Update Attribute Value |
|
Update the department |
ADIDC Update Attribute Value |
|
Update the full name |
ADIDC Update Attribute Value |
|
Update home phone |
ADIDC Update Attribute Value |
|
Update the city |
ADIDC Update Attribute Value |
|
Update the manager name |
ADIDC Update Attribute Value |
|
Update the user ID |
ADIDC Update Attribute Value |
|
Update common name |
ADIDC Update Attribute Value |
|
Update the user must change password at next logon flag |
ADIDC Update Attribute Value |
|
Delete group membership |
ADIDC Update Child Table Values |
|
Create object class |
ADIDC Update Child Table Values |
|
Update group membership |
ADIDC Update Child Table Values |
|
Create group membership |
ADIDC Update Child Table Values |
|
Update object class |
ADIDC Update Child Table Values |
|
Delete object class |
ADIDC Update Child Table Values |
|
Group Provisioning Functions |
|
|
Create group |
ADIDC Create Object |
|
Delete group |
ADIDC Delete Object |
|
Display Name Updated |
ADIDC Update Attribute Value |
|
Group Name Updated |
ADIDC Update Attribute Value |
|
Group Type Updated |
ADIDC Update Attribute Value |
|
Organization Name Updated |
ADIDC Update Attribute Value |
|
Organizational Unit Provisioning Functions |
|
|
Create Organizational Unit |
ADIDC Create Object |
|
Display Name Updated |
ADIDC Update Attribute Value |
|
Container Updated |
ADIDC Update Attribute Value |
|
Delete Organizational Unit |
ADIDC Delete Object |
The Lookup.ActiveDirectory.UM.ProvAttrMap lookup definition maps process form fields with target system attributes. This lookup definition is used for performing user provisioning operations.
Table 1-19 lists the user identity fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-19 Entries in the Lookup.ActiveDirectory.UM.ProvAttrMap Lookup Definition
| Process Form Field | Target System Field | Description |
|---|---|---|
|
Manager Name |
manager |
Manager name You must enter the manager name in the DN format. For example: |
|
Terminal Home Directory |
TerminalServicesHomeDirectory Part of the data stored in the userParameters field Note: This field does not exist in Microsoft AD LDS. A value that you enter in this field would be ignored during provisioning operations in Microsoft AD LDS. |
Full path of the home directory for the Terminal Server userSample value: During a provisioning operation, you must enter the full, absolute path of the home directory, as shown in the sample value. |
|
UD_ADUSRC~Group Name[Lookup] |
__GROUPS__ |
Group name |
|
Terminal Profile Path |
TerminalServicesProfilePath Part of the data stored in the userParameters field Note: This field does not exist in Microsoft AD LDS. A value that you enter in this field would be ignored during provisioning operations in Microsoft AD LDS. |
Profile that is used when the user logs on to a Terminal Server The profile can be roaming or mandatory. A roaming profile remains the same, regardless of the computer from which the user logs in. The user can make changes to a roaming profile, but not to a mandatory profile. Any changes a user makes while logged in with a mandatory profile are retained only for that Terminal Services session. The changes are lost when the user starts another Terminal Services session. |
|
Account Expiration Date[DATE] This is a date field. |
__PASSWORD_EXPIRATION_DATE__ |
Date when the account expires |
|
Street |
streetAddress |
Street address |
|
Zip |
postalCode |
ZIP code |
|
Middle Name This field is on both the process form and the OIM User form. During a provisioning operation, the Middle Name field on the process form is prepopulated with the value entered in the Middle Name field on the OIM User form. |
middleName |
Initials for the user's middle name |
|
User Must Change Password At Next Logon This is a check box. |
__PASSWORD_EXPIRED__ |
Flag that indicates whether or not the user must change the password at next logon. If the value is yes (check box is selected), then the user must change the password at next logon. |
|
Office |
physicalDeliveryofficeName |
Office Location |
|
Home Phone |
homePhone |
Home phone number |
|
City |
l |
City |
|
Account is Locked out This is a check box |
__LOCK_OUT__ |
Specifies whether the user account must be locked or unlocked |
|
Last Name This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the Last Name field on the process form is prepopulated with the value entered in the Last Name field on |
sn |
Last name |
|
IP Phone |
ipPhone |
IP phone number |
|
Mobile |
mobile |
Mobile number |
|
Telephone Number |
telephoneNumber |
Telephone number |
|
State |
st |
State |
|
Fax |
facsimileTelephoneNumber |
Fax number |
|
First Name This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the First Name field on the process form is prepopulated with the value entered in the First Name field on the OIM User form. |
givenName |
First name |
|
Password This field is on both the process form and the OIM User form. It is a mandatory field on the OIM User form. During a provisioning operation, the Password field on the process form is prepopulated with the value entered in the Password field on the OIM User form. If SSL is configured between Oracle Identity Manager and the target system, then the Password field on the process form is a mandatory field. |
__PASSWORD__ This connector uses ADSI to set the password of the user. It uses the IADsUser#SetPassword API. This API sets the user's unicodePwd attribute. See the following URL for more information:
|
User's password in UTF-8 format |
|
Full Name |
displayName |
Display name for a user During a Create User provisioning operation, the cn and displayName fields are populated with a combination of the user's first name, middle initial, and last name entered on the OIM User form. The full name is displayed in the following format on the process form: FIRSTNAME MIDDLE_INITIAL. LASTNAME For example: If the middle initial is not entered, then the name is displayed as, for example, John Doe. During an Update provisioning operation, only the value in the displayName field is updated. |
|
Redirection Mail Id |
__MAILREDIRECTION__ |
E-mail address to which e-mail sent to the user must be redirected This e-mail address overrides the one set in the E Mail field. |
|
__NAME__ |
__NAME__="CN=$(Common_Name),$(Organization_Name)" |
User name with full DN |
|
Password Not Required This is a check box. |
PasswordNotRequired |
Specifies whether or not Password is required. If it is true, then there is no need to specify the password. If it is false, then password is required. |
|
Terminal Allow Login This is a check box. |
AllowLogon This field does not exist in Microsoft ADAM and AD LDS. A value that you enter in this field would be ignored during provisioning operations in Microsoft ADAM and AD LDS. |
Specifies whether or not the user is permitted to log on to the Terminal Server |
|
Country |
c |
Country |
|
User Id This field is on both the process form and the OIM User form. It is a mandatory field. During a provisioning operation, the User ID field on the process form is prepopulated with the value entered in the User |
sAMAccountName This is a mandatory field in Microsoft Active Directory. This field does not exist in Microsoft ADAM and AD LDS. |
User's logon name |
|
Pager |
pager |
Pager number |
|
Organization Name[LOOKUP,IGNORE] |
IGNORED |
Name of the organization |
|
Unique Id This is a hidden field on both the process form and the OIM User form. |
__UID__ |
Object GUID of the user |
|
E Mail This field is on both the process form and the OIM User form. |
|
Email address |
|
Common Name[IGNORE] |
IGNORED |
Common name of the user |
|
Title |
title |
Title |
|
Company |
company |
Company |
|
Password Never Expires This is a check box. |
PasswordNeverExpires |
Flag that controls the Password Never Expires property |
|
Department |
department |
Department |
|
User Principal Name This is a mandatory field. |
userPrincipalName This is a mandatory field. Note: The value for UserPrincipalName must be entered in the format shown in the following example: If the root context is |
The user principal name is the domain-specific name of the user. This field is pre-populated on the Administrative and User Console. The format is as follows: USER_ID_VALUE@UPN_DOMAIN_VALUE Note: When you update this field, you can change the User ID part but you must not change the domain name. If you change the domain name, then the user will not be matched on the target system. |
|
Homedirectory |
homeDirectory |
Home directory of the user |
|
Post Office Box |
postOfficeBox |
Post-office box |
The Lookup.ActiveDirectory.GM.ProvAttrMap lookup definition maps user resource object fields and target system attributes. This lookup definition is used for performing group provisioning operations.
Table 1-20 lists the group fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-20 Entries in the Lookup.ActiveDirectory.GM.ProvAttrMap
| Group Field on Oracle Identity Manager | Target System Field | Description |
|---|---|---|
|
__NAME__ |
__NAME__="CN=${Group_Name},${Organization_Name}" |
Group name with full DN |
|
Display Name |
displayName |
Display name for a group |
|
Group Name |
sAMAccountName |
Group name |
|
Group Type |
groupType |
Group type |
|
Organization Name[LOOKUP,IGNORE] |
IGNORED |
Name of the organization to which the group belongs |
|
Unique Id |
__UID__ |
Object GUID of the group |
The Lookup.ActiveDirectory.OM.ProvAttrMap lookup definition maps organization resource object fields and target system attributes. This lookup definition is used for performing organizational unit provisioning operations.
Table 1-21 lists the organizational unit fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-21 Entries in the Lookup.ActiveDirectory.OM.ProvAttrMap
| Organizational Unit Field on Oracle Identity Manager | Target System Field | Description |
|---|---|---|
|
__NAME__ |
__NAME__="OU=$(Display_Name),$(Container) |
Organizational unit name with full DN |
|
Container[LOOKUP,IGNORE] |
IGNORED |
Organization name with DN formatFor example, |
|
Display Name[IGNORE] |
IGNORED |
Display name for an organizational unit |
|
Unique Id |
__UID__ |
Object GUID of the organizational unit |
Trusted source reconciliation involves fetching data about newly created or modified accounts on the target system and using that data to create or update OIM Users.
The Active Directory User Trusted Recon scheduled task is used to initiate a trusted source reconciliation run. This scheduled task is discussed in Scheduled Jobs for Reconciliation of User Records.
See Also:
Managing Reconciliation in Performing Self Service Tasks with Oracle Identity Manager for conceptual information about reconciliation
This section discusses the following topics:
The Lookup.ActiveDirectory.UM.ReconAttrMap.Trusted lookup definition maps user fields of the OIM User form with corresponding field names in the target system. This lookup definition is used for performing trusted source reconciliation runs.
Table 1-22 lists the user identity fields whose values are fetched from the target system during a trusted source reconciliation run.
Table 1-22 Entries in the Lookup.ActiveDirectory.UM.ReconAttrMap.Trusted Lookup Definition
| OIM User Form Field | Target System Field | Description |
|---|---|---|
|
E Mail |
|
Email address |
|
Employee Type |
OIM Employee Type |
Employee type of the OIM User |
|
First Name This is a mandatory field. |
givenName This is a mandatory field. |
First name |
|
Last Name This is a mandatory field. |
sn This is a mandatory field. |
Last name For a record fetched during trusted source reconciliation, if there is no value in this attribute, then the value from the Common Name attribute is populated in the Last Name field on the process form. |
|
Manager ID |
Manager Id |
Manager name |
|
Middle Name |
middleName |
Middle name |
|
objectGUID |
__UID__ |
Object GUID of each user on the target system |
|
Organization This is a mandatory field. |
__PARENTCN__ |
This is the name of the organization to which users belong if you set the value of the MaintainHierarchy entry of the Lookup.Configuration.ActiveDirectory.Trusted lookup definition to If Maintain Hierarchy is set to |
|
TrustedStatus[TRUSTED] |
__ENABLE__ |
This field stores the status of the user account. |
|
User Id This is a mandatory field. |
sAMAccountName |
User's logon name |
|
User Type |
OIM User Type |
Type of the OIM User Values can be one of the following:
|
The Lookup.ActiveDirectory.OM.ReconAttrMap.Trusted lookup definition maps organizational unit fields of the OIM User form with corresponding field names in the target system. This lookup definition is used for performing trusted source reconciliation runs.
Table 1-23 lists the organizational unit field whose value is fetched from the target system during a trusted source reconciliation run.
Table 1-23 Entries in the Lookup.ActiveDirectory.OM.ReconAttrMap.Trusted Lookup Definition
| OIM User Form Field | Target System Field |
|---|---|
|
Org Name |
ou |
See Also:
Reconciliation Engine in Performing Self Service Tasks with Oracle Identity Manager for generic information about reconciliation matching and action rules
The following is the entity matching rule:
Rule name: AD User Trusted Recon Rule
Rule: User Login Equals User Id
In this rule:
User Login is the User ID field on the OIM User form.
User Id is the sAMAccountName field of Microsoft Active Directory or the userPrincipalName field of Microsoft AD LDS.
After you deploy the connector, you can view the reconciliation rule for trusted source reconciliation by performing the following steps:
Figure 1-4 Reconciliation Rule for Trusted Source Reconciliation
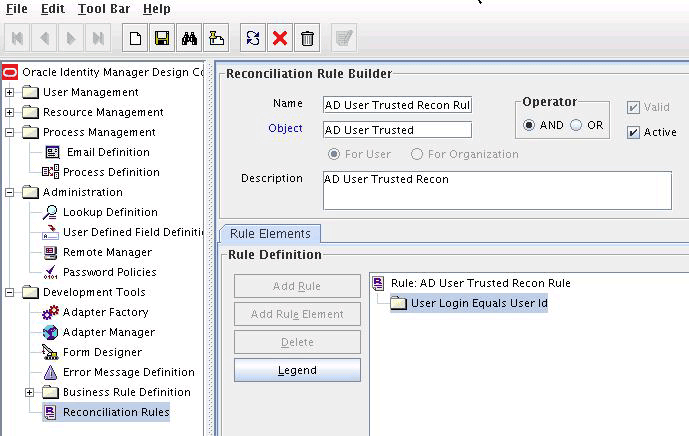
Note:
In Microsoft Active Directory, sAMAccountName attribute is a mandatory and unique field.
Table 1-24 lists the action rules for trusted source reconciliation.
Table 1-24 Action Rules for Trusted Source Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Create User |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. See
Setting a Reconciliation Action Rule (Developing Identity Connectors using Java)
Setting a Reconciliation Action Rule (Developing Identity Connectors using .net)
in Developing and Customizing Applications for Oracle Identity Manager for information about setting a reconciliation action rule.