2 Deploying the Oracle Identity Cloud Service Connector
The procedure to deploy the connector is divided across three stages: Preinstallation, installation, and postinstallation.
The following topics provide details on these stages:
2.1 Preinstallation
Preinstallation for the Oracle Identity Cloud Service connector involves registering and generating a client application (that is, the Oracle Identity Cloud Service connector) with the target system so that the connector can access Oracle Identity Cloud Service Graph APIs. It also involves creating a target system account for connector operations.
Preinstallation involves performing the following tasks on the target system:
- Register and generate an application. Because the connector operates as a multitarget environment, the application needs to be registered on the Oracle Identity Cloud Service environment for authentication.
- Specify the permissions to choose an application type to configure your own application in the cloud. To do so:
- Select Resource Owner as the allowed grant type for this application.
- Select the Client has Access to Identity Cloud Service Admin APIs checkbox.
- Select Identity Domain Administrator and Me. This provides administrator permissions to any third-party client using this application to perform identity operations such as User and Group management.
- In the Register the Resource of the Application page, select the Register Resources radio button.
- Create a target system account with administrative privileges to enable connector operations such as reconciliation and provisioning.
2.2 Installation
You must install the Oracle Identity Cloud Service connector in Oracle Identity Manager and if required, place the connector code bundle in the Connector Server.
The following topics discuss installing the Oracle Identity Cloud Service connector:
2.2.1 Understanding Installation of the Oracle Identity Cloud Service Connector
You can run the connector code either locally in Oracle Identity Manager or remotely in a Connector Server
Depending on where you want to run the generated connector, the connector provides the following installation options:
-
Run the connector code locally in Oracle Identity Manager. To run the connector code locally in Oracle Identity Manager, perform the procedure described in Installing the Connector in Oracle Identity Manager. In this scenario, you deploy the connector in Oracle Identity Manager.
-
Run the connector code remotely in a Connector Server. To run the connector code remotely in a Connector Server, perform the procedures described in Installing the Connector in Oracle Identity Manager and Deploying the Connector in a Connector Server. In this scenario, you deploy the connector in Oracle Identity Manager, and then, deploy the connector bundle in a Connector Server. For information about installing, configuring, and running the Connector Server, and then installing the connector in a Connector Serve, see Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager .
2.2.2 Installing the Connector in Oracle Identity Manager
Installation on Oracle Identity Manager consists of the following procedures:
2.2.2.1 Running the Connector Installer
When you run the Connector Installer, it automatically copies the connector files to directories in Oracle Identity Manager, imports connector XML files, and compiles adapters used for provisioning.
To run the Connector Installer:
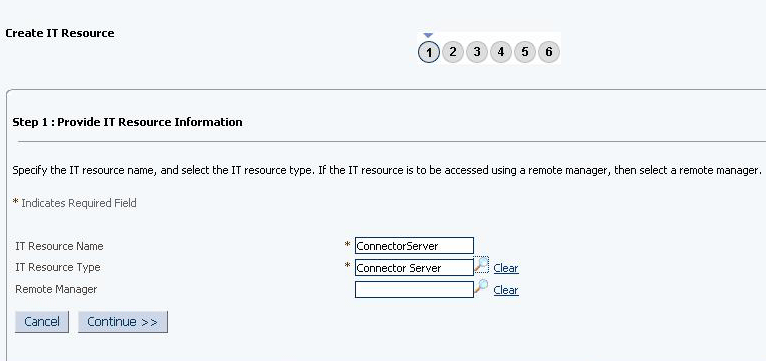
2.2.2.2 Configuring the IT Resource for the Target System
An IT resource for your target system is created after you install the connector. You configure this IT resource to enable the connector to connect Oracle Identity Manager with your target system.
This section contains the following topics:
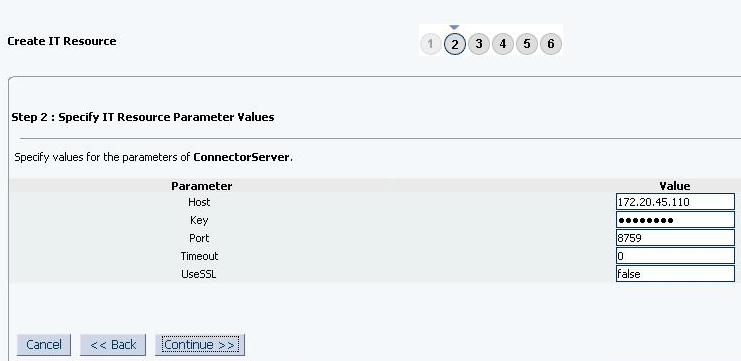
2.2.2.2.1 IT Resource Parameters
An IT resource is composed of parameters that store connection and other generic information about a target system. Oracle Identity Manager uses this information to connect to a specific installation or instance of your target system.
The list of IT resource parameters for this connector can be grouped into the following categories:
-
Connection-related parameters
-
Authentication parameters
Connection Parameters
Table 2-1 lists the connection-related parameters.
Table 2-1 Connection IT Resource Parameters
| Parameter | Description |
|---|---|
|
host |
The host name or IP address of the computer hosting the target system. Sample value: |
|
port |
The port number at which the target system is listening. Sample value: |
|
baseURI |
The base URI is the base relative URL of the Oracle Identity Cloud Service target system. Sample value: http://host:port/admin/v1, then baseURI is /admin/v1 |
|
Configuration Lookup |
The name of the lookup definition that stores configuration information used during reconciliation and provisioning. Default value for Oracle Identity Cloud Service: |
|
Connector Server Name |
If you have deployed the Oracle Identity Cloud Service connector in a Java Connector Server, then enter the name of the IT resource for the Connector Server. |
|
acceptType |
The accept type for the header denotes how the request body must be parsed. The request body should only be parsed as JSON if the Content-Type header is application/json. |
|
sslEnabled |
If the target system requires SSL connectivity, set the value of this parameter to true. Otherwise, set the value to false. |
|
grantType |
The type of authentication used by your target system. The default value is: |
|
scope |
Scope is required to authenticate request based on 'OAuth2.0 Resource Owners Password or Client Credentials' authentication type |
|
contentType |
The content type for the header denotes the format of the request being sent to the target system. The request body should only be parsed as JSON if the Content-Type header is application or JSON. |
Table 2-2 lists authentication parameters.
Table 2-2 Basic Authentication IT Resource Parameters
| Parameter | Description |
|---|---|
|
username |
The user name or User ID used if authentication type is “basic” or “password”. Sample value: |
|
password |
The password used if authentication type is “basic” or “password”. Sample value: |
|
authenticationServerUrl |
The URL of the authentication server if authentication type is “BASIC”. Sample value: |
|
customAuthHeaders |
Authorization=Basic
|
2.2.2.2.2 Specifying Values for the IT Resource Parameters
The IT resource for the target system contains connection information about the target system. Oracle Identity Manager uses this information during provisioning and reconciliation. When you run the metadata generator, the IT resource corresponding to this connector is automatically created in Oracle Identity Manager.
You must specify values for the parameters of this IT resource as follows:
- Log in to Oracle Identity System Administration.
- In the left pane, under Configuration, click IT Resource.
- In the IT Resource Name field on the Manage IT Resource page, enter Identity Cloud Services, and then click Search.
- Click the edit icon for the IT resource.
- From the list at the top of the page, select Details and Parameters.
- Specify values for the parameters of the IT resource.
- To save the values, click Update.
2.2.3 Deploying the Connector in a Connector Server
In this scenario, you deploy the connector in Oracle Identity Manager, and then, deploy the connector bundle in a Connector Server.
For information about installing, configuring, and running the Connector Server, and then installing the connector in a Connector Server, see Using an Identity Connector Server in Developing and Customizing Applications for Oracle Identity Manager.
2.3 Postinstallation
Postinstallation for the Oracle Identity Cloud Service connector involves configuring OIM, enabling logging to track information about all connector events, and configuring SSL. It also involves performing optional configurations such as localizing the user interface.
Postinstallation steps are detailed in the following sections:
2.3.1 Postinstallation on Oracle Identity Manager
Configuring Oracle Identity Manager involves performing the following procedures:
2.3.1.1 Configuring Oracle Identity Manager
You must create a UI form and an application instance for the resource against which you want to perform reconciliation and provisioning operations. In addition, you must run entitlement and catalog synchronization jobs.
These procedures are described in the following sections:
2.3.1.1.1 Creating and Activating a Sandbox
You must create and activate a sandbox to begin using the customization and form management features. You can then publish the sandbox to make the customizations available to other users.
See Creating a Sandbox and Activating and Deactivating a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager.
2.3.1.1.2 Creating a New UI Form
You can use Form Designer in Oracle Identity System Administration to create and manage application instance forms. See Creating Forms By Using the Form Designer in Oracle Fusion Middleware Administering Oracle Identity Manager.
While creating the UI form, ensure that you select the resource object corresponding to the Oracle Identity Cloud Service connector that you want to associate the form with. In addition, select the Generate Entitlement Forms check box.
2.3.1.1.3 Creating an Application Instance
Create an application instance as follows:
- In the left pane of the System Administration console, under Configuration, click Application Instances. The Application Instances page appears.
- From the Actions menu, select Create. Alternatively, click Create on the toolbar. The Create Application Instance page appears.
- Enter appropriate values for the fields displayed on the Attributes form and click Save.
- Click Save. The application instance is created.
- Publish the application instance to an organization to make the application instance available for requesting and subsequent provisioning to users. See Publishing an Application Instance to Organizations in Oracle Fusion Middleware Administering Oracle Identity Manager.
2.3.1.1.4 Publishing a Sandbox
After you publish a sandbox, it is difficult to revert changes. Therefore, before you publish a sandbox, perform the following procedure to validate all sandbox changes made until this stage:
- In the System Administration console, deactivate the sandbox.
- Log out of the System Administration console.
- Log in to the Self Service console using the xelsysadm user credentials, and then activate the sandbox that you deactivated in Step 1.
- In the catalog, ensure that the Oracle Identity Cloud Service application instance form appears with the correct fields.
- After you Publish the sandbox. See Publishing a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager.
2.3.1.1.5 Harvesting Entitlements and Sync Catalog
To harvest entitlements and sync the catalog:
- Run the scheduled jobs for lookup field synchronization listed in Scheduled Job for Lookup Field Synchronization.
- Run the Entitlement List scheduled job to populate Entitlement Assignment schema from the child process form table.
- Run the Catalog Synchronization Job scheduled job.
See Also:
For a description of the Entitlement List and Catalog Synchronization Job scheduled jobs, see Predefined Scheduled Tasks in Administering Oracle Identity Manager
2.3.1.1.6 Updating an Existing Application Instance with a New Form
For any changes that you make in the Form Designer, you must create a new UI form and update the changes in an application instance. To update an existing application instance with a new form:
- Create a sandbox and activate it. See Creating a Sandbox and Activating and Deactivating a Sandbox in Developing and Customizing Applications for Oracle Identity Manager.
- Create a new UI form for the resource. See Creating Forms By Using the Form Designer in Administering Oracle Identity Manager.
- Open the existing application instance.
- In the Form field, select the new UI form that you created.
- Save the application instance.
- Publish the sandbox. See Publishing a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager.
2.3.1.2 Clearing Content Related to Connector Resource Bundles from the Server Cache
When you deploy the connector, the resource bundles are copied from the resources directory on the installation media into the Oracle Identity Manager database. Whenever you add a new resource bundle to the connectorResources directory or make a change in an existing resource bundle, you must clear content related to connector resource bundles from the server cache.
To clear content related to connector resource bundles from the server cache:
-
In a command window, switch to the OIM_HOME/server/bin directory.
-
Enter one of the following commands:
Note:
You can use the PurgeCache utility to purge the cache for any content category. RunPurgeCache.batCATEGORY_NAMEon Microsoft Windows orPurgeCache.shCATEGORY_NAMEon UNIX. TheCATEGORY_NAMEargument represents the name of the content category that must be purged.For example, the following commands purge Metadata entries from the server cache:
PurgeCache.bat MetaData
PurgeCache.sh MetaData
-
On Microsoft Windows:
PurgeCache.bat All -
On UNIX:
PurgeCache.sh All
When prompted, enter the user name and password of an account belonging to the SYSTEM ADMINISTRATORS group. In addition, you are prompted to enter the service URL in the following format:
t3://OIM_HOST_NAME:OIM_PORT_NUMBER
In this format:
-
Replace OIM_HOST_NAME with the host name or IP address of the Oracle Identity Manager host computer.
-
Replace OIM_PORT_NUMBER with the port on which Oracle Identity Manager is listening.
You can use the PurgeCache utility to purge the cache for any content category. See Purging Cache in Oracle Fusion Middleware Administering Oracle Identity Manager.
-
2.3.1.3 Managing Logging for Oracle Identity Cloud Service Connector
Oracle Identity Manager uses the Oracle Diagnostic Logging (ODL) logging service for recording all types of events pertaining to the connector.
The following topics provide detailed information about logging:
2.3.1.3.1 Understanding Log Levels
When you enable logging, Oracle Identity Manager automatically stores in a log file information about events that occur during the course of provisioning and reconciliation operations.
ODL is the principle logging service used by Oracle Identity Manager and is based on java.util.Logger. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that might allow Oracle Identity Manager to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These log levels are mapped to ODL message type and level combinations as shown in Table 2-3.
Table 2-3 Log Levels and ODL Message Type: Level Combinations
| Log Level | ODL Message Type:Level |
|---|---|
|
SEVERE.intValue()+100 |
INCIDENT_ERROR:1 |
|
SEVERE |
ERROR:1 |
|
WARNING |
WARNING:1 |
|
INFO |
NOTIFICATION:1 |
|
CONFIG |
NOTIFICATION:16 |
|
FINE |
TRACE:1 |
|
FINER |
TRACE:16 |
|
FINEST |
TRACE:32 |
The configuration file for OJDL is logging.xml, which is located at the following path: DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SERVER are the domain name and server name specified during the installation of Oracle Identity Manager.
2.3.1.3.2 Enabling Logging
To enable logging in Oracle WebLogic Server:
-
Edit the logging.xml file as follows:
-
Add the following blocks in the file:
<log_handler name='idcs-handler' level='[LOG_LEVEL]' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='/scratch/IDCS/Logs/IDCS.log'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler><logger name='ORG.IDENTITYCONNECTORS.GENERICSCIM' level='TRACE:32' useParentHandlers='false'> <handler name='idcs-handler'/> <handler name='console-handler'/> </logger> -
Replace both occurrences of
[LOG_LEVEL]with the ODL message type and level combination that you require. Table 2-3 lists the supported message type and level combinations.Similarly, replace
[FILE_NAME]with the full path and name of the log file in which you want log messages specific to connector operations to be recorded.The following blocks show sample values for
[LOG_LEVEL]and[FILE_NAME]:<log_handler name='idcs-handler' level='TRACE:32' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='/scratch/IDCS/Logs/IDCS.log'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler> </log_handlers> <logger name='ORG.IDENTITYCONNECTORS.GENERICSCIM' level='TRACE:32' useParentHandlers='false'> <handler name='idcs-handler'/> <handler name='console-handler'/> </logger>
With these sample values, when you use Oracle Identity Manager, all messages generated for this connector that are of a log level equal to or higher than the
NOTIFICATION:1level are recorded in the specified file. -
-
Save and close the file.
-
Set the following environment variable to redirect the server logs to a file:
-
For Microsoft Windows:
set WLS_REDIRECT_LOG=FILENAME -
For UNIX:
export WLS_REDIRECT_LOG=FILENAME
Replace FILENAME with the location and name of the file to which you want to redirect the output.
-
-
Restart the application server.
2.3.1.4 Localizing Field Labels in UI Forms
You can localize UI form field labels by using the resource bundle corresponding to the language you want to use. Resource bundles are available in the connector installation media
To localize field label that is added to the UI forms:
2.3.1.5 Configuring SSL for Oracle Identity Cloud Service
Importing the Certificate
Configure SSL to secure data communication between Oracle Identity Manager and Oracle Identity Cloud Service.
Oracle Identity Cloud Service validates the client system dates to be in sync with the SSL certificate (the certificate issued by Oracle Identity Cloud Service application) date. If there is any deviation, then the target system might throw an error. The client machine date must be in sync with the certificate timestamp range. Obtain SSL certificate from the target system.
Use the keytool command to import the SSL certificate from the target system into the identity keystore in Oracle Identity Manager.
keytool -import -alias alias -trustcacerts -file file-to-import -keystore keystore-name -storepass keystore-password
In this example, the certificate file supportcert.pem is imported to the identity keystore client_store.jks with password weblogic1:
keytool -import -alias serverwl -trustcacerts -file supportcert.pem -keystore client_store.jks -storepass weblogic1
Note:
Change the parameter values passed to the keytool command according to your requirements. Ensure that there is no line break in the keytool arguments.