1 About the Oracle Identity Cloud Service Connector
The Oracle Identity Cloud Service connector integrates Oracle Identity Manager (OIM) with Oracle Identity Cloud Service.
Oracle Identity Manager is a centralized identity management solution that provides self service, compliance, provisioning and password management services for applications residing on-premise or on the Cloud. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external, identity-aware applications. The Oracle Identity Cloud Service connector enables you to use Oracle Identity Cloud Service as a managed (target) resource Oracle Identity Manager.
Note:
In this guide, the term target system is sometimes used to refer to Oracle Identity Cloud Service.
The following topics provide a high-level overview of the Oracle Identity Cloud Service connector:
1.1 Introduction to the Oracle Identity Cloud Service Connector
The Oracle Identity Cloud Service connector enables you to use Oracle Identity Cloud Service as a managed (target) source of identity data for Oracle Identity Manager.
In the account management (target resource) mode of the connector, the data about the users created or modified directly on the target system can be reconciled into Oracle Identity Manager. This data is used to provision (allocate) new resources or update resources already assigned to Oracle Identity Manager users. You can also use Oracle Identity Manager to provision or update Oracle Identity Cloud Service resources (accounts) assigned to Oracle Identity Manager users. These provisioning operations performed on Oracle Identity Manager translate into the creation or updates to target system accounts.
1.2 Certified Components for the Oracle Identity Cloud Service Connector
These are the software components and their versions required for installing and using the Oracle Identity Cloud Service connector.
Table 1-1 lists the certified components for this connector.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Governance or Oracle Identity Manager:
|
|
Target System |
Oracle Identity Cloud Service 16.3.6 or later |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 or later |
1.3 Certified Languages for the Oracle Identity Cloud Service Connector
The connector supports the following languages:
-
Arabic
-
Chinese Simplified
-
Chinese Traditional
-
Danish
-
English
-
French
-
German
-
Italian
-
Japanese
-
Korean
-
Portuguese (Brazilian)
-
Spanish
1.4 Architecture of the Oracle Identity Cloud Service Connector
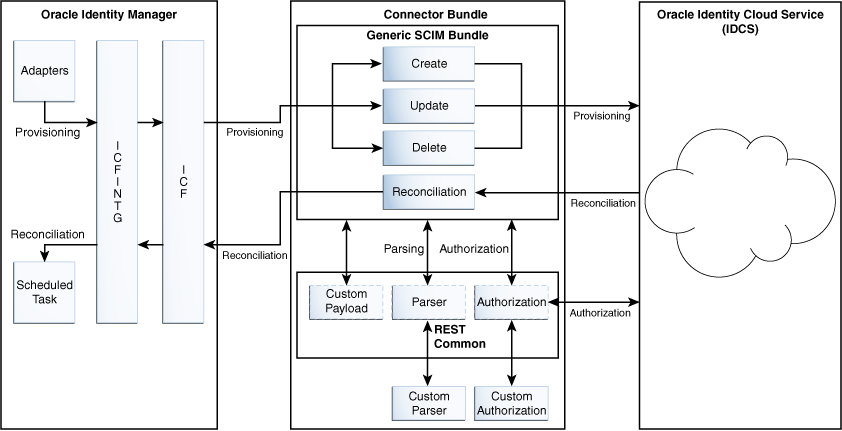
The Oracle Identity Cloud Service connector is implemented by using the Identity Connector Framework (ICF).
The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. The ICF is shipped together with Oracle Identity Manager.
Figure 1-1 shows the integration of on-premise Oracle Identity Manager with the Identity Cloud Service. The Oracle Identity Cloud Service connector follows a hybrid data management system providing opportunities for organizations having roots in Oracle Identity Manager but with an intent of migrate to the Oracle Identity Cloud Service framework. As the diagram suggests, Oracle Identity Cloud Service connector can carry out provisioning and reconciliation operations on Oracle Identity Cloud Service. In the diagram, the connector bundle is responsible for interacting with Oracle Identity Cloud Service, which is a SCIM compliant target. Therefore, the connector package uses the Generic SCIM bundle. Parsing and authorization is handled by the REST common bundle, which is a part of the Generic SCIM bundle. By default, it supports OAuth 2.0 Resource Owner Password authentication. In addition, custom parser and custom authorization can be implemented to enhance the connector.
1.5 Use Cases Supported by the Oracle Identity Cloud Service Connector
The promise of simplified deployment, reduced acquisition costs, reduced management overhead and quick time to value are driving organizations to adopt SaaS applications to meet the various business needs. Since recently, very large number of applications are being developed in the cloud. Oracle Identity Cloud Service provides a set of foundational services for Oracle’s Public Cloud applications and their customers by delivering simple, secure integration with Oracle and third party SaaS applications for customers interested in a Public Identity as a service offering from Oracle.
Similarly, many of Oracle’s existing customers using on-premise IDM are also moving their HCM, CRM, directories and other applications from on-premise to the Cloud. Customers also want to move their IDM services into cloud. To keep pace with the changing trends and to support customers who are adopting cloud, Oracle’s on-premise Identity Management software, Oracle Identity Manager provides a new integration called the Oracle Identity Cloud Service connector. This integration will not only facilitate customer’s migration from on-premise to cloud but it will also support the hybrid strategy where customers can have both on-premise IDM and cloud IDM working together to achieve greater value.
Let’s say ACME Corporation has been using Oracle Identity Manager for some time to manage its identities and various applications on premise. The long-term plan of ACME Corporation is to move into cloud but they want to achieve this in phases. At one point of time, they have both on-premise and cloud applications. As part of this move, they now have Oracle Identity Cloud Service to manage cloud applications but for the time being, they want to use only Oracle Identity Manager to manage identities in their ecosystem.
Oracle Identity Cloud Service connector will facilitate ACME Corporation in achieving this use case by providing Oracle Identity Cloud Service user and group management for the cloud applications.
After installing the Oracle Identity Cloud Service connector, customer can manage complete lifecycle of the users and groups in Oracle Identity Cloud Service from Oracle Identity Manager. Using this integration, ACME Corporation can create, update, enable, and disable Oracle Identity Cloud Service users accessing the cloud applications. Also, it can assign or revoke Oracle Identity Cloud Service groups for a particular user accessing the cloud applications using Oracle Identity Manager.
With the RBAC policies defined in Oracle Identity Manager, granting or revoking appropriate groups using connector will ensure that user has proper, authorized access to the cloud applications registered with the Oracle Identity Cloud Service.
1.6 Features of the Oracle Identity Cloud Service Connector
The features of the connector include support for the connector server, full reconciliation, limited reconciliation, and reconciliation of deleted account data.
1.6.1 Support for Account and Group Provisioning
You can use the connector to provision Oracle Identity Cloud Service user accounts and groups.
You can create a new user in Oracle Identity Manager by using the Create User page. The connector provides separate process forms and resource objects for user account and group operations.
1.6.2 Full and Incremental Reconciliation
In full reconciliation, all records are fetched from the target system to Oracle Identity Manager.
After you deploy the connector, you can perform full reconciliation to bring all user data from the target system to Oracle Identity Manager. After the first full reconciliation run, incremental reconciliation is automatically enabled. In incremental reconciliation, user accounts that have been added or modified since the last reconciliation run are fetched into Oracle Identity Manager. You can perform a full reconciliation run at any time. See Performing Full Reconciliation.
1.6.3 Limited Reconciliation
You can reconcile records from the target system based on a specified filter criteria.
To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled. See Performing Limited Reconciliation.
1.6.4 Support for Batched Reconciliation
Depending on the number of records to be reconciled, a batched reconciliation operation can be configured.
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch. See Performing Batched Reconciliation.
1.6.5 Transformation and Validation of Account Data
Transformation and validation of account data can be configured during reconciliation and provisioning operations.
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation. The following sections provide more information:
1.6.6 Reconciliation of Deleted User Accounts and Groups
You can configure the connector to fetch details of deleted target system users and groups in the target resource mode.
You can configure the connector for reconciliation of deleted user accounts and groups. In target resource mode, if a user record is deleted or a token is unassigned on the target system, then the corresponding Oracle Identity Cloud Service resource is revoked from the Oracle Identity Manager User.
See IDCS Delete User Reconciliation and IDCS Delete Group Reconciliation for more information about scheduled jobs used for reconciling deleted user records and groups.
1.6.7 Support for the Connector Server
The Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for information about the installation options for this connector
1.7 Lookup Definitions Used During Connector Operations
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
Lookup definitions used during connector operations can be categorized as follows:
1.7.1 Lookup Definitions Synchronized With the Target System
During a provisioning operation, you use a lookup field on the process form to select a single value from a set of values. For example, you may want to select a group from the Groups lookup field to specify the group being assigned to the user. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to specific fields in the target system to lookup definitions in Oracle Identity Manager.
After you deploy the connector, the following lookup definitions, which are used as an input source for lookup fields, are automatically created in Oracle Identity Manager:
-
Lookup.IDCS.Groups
-
Lookup.IDCS.Managers
The Lookup.IDCS.Groups and Lookup.IDCS.Managers lookup definitions are populated with values fetched from the target system by the scheduled jobs for lookup field synchronization.
During a provisioning operation, you use the Group lookup field on the process form to specify a group and the Managers lookup definition to specify users already assigned as managers. The Groups and Managers lookup fields are populated with values from the Lookup.IDCS.Groups and Lookup.IDCS.Managers lookup definitions, which are automatically created on Oracle Identity Manager when you deploy the connector.
By default, these lookup definitions are empty. They are populated with values fetched from the target system when you run the scheduled jobs for lookup field synchronization. For example, when you run the scheduled job, all groups on the target system are fetched to Oracle Identity Manager and populated in the Lookup.IDCS.Groups lookup definition.
After synchronization, the data in each of the lookup definitions is stored in the following format:
-
Code Key: <IT_RESOURCE_KEY>~<FIELD_VALUE_ID>
In this format:
-
IT_RESOURCE_KEY is the numeric code assigned to an IT resource in Oracle Identity Manager.
-
FIELD_VALUE_ID is the ID of the target system field value.
For example, for the Lookup.IDCS.Groups lookup definition, the code key value for one of its entries is
89~1b5d6697-f4a6-4f03-8df7-4fae1512fd16. In this example,89is the numeric code assigned to the IT resource associated with the target system and1b5d6697-f4a6-4f03-8df7-4fae1512fd16is the ID of the Group in the target system.
-
-
Decode: <IT_RESOURCE_NAME>~<FIELD_VALUE>
In this format:
-
IT_RESOURCE_NAME is the name of the IT resource in Oracle Identity Manager.
-
FIELD_VALUE is the value of the field in the target system.
For example, for the Lookup.IDCS.Groups lookup definition, the decode value for one of its entries is
IDCS~HR. In this example,IDCSis the name of the IT resource andHRis the value of the Group field in the target system.
-
Table 1-2 shows sample entries in the Lookup.IDCS.Groups lookup definition.
Table 1-2 Sample Entries in the Lookup.IDCS.Groups Lookup Definition
| Code Key | Decode |
|---|---|
|
IDCS~Finance |
89~9b3b3faf-e7fb-427e-8038-b8021cfbab30 |
|
IDCS~HR |
89~eb1b204e-2de0-41ec-98e9-1c33684d698a |
|
IDCS~ISP |
89~4457f158-d1ec-47f2-aeb4-79d5a2be0e38 |
1.7.2 Preconfigured Lookup Definitions
Preconfigured lookup definitions are the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
1.7.2.1 Lookup.IDCS.Configuration
The Lookup.IDCS.Configuration lookup definition holds connector configuration entries that are used during target resource reconciliation and provisioning operations.
Note:
The values for these lookup definitions are preconfigured and cannot be modified.Table 1-3 lists the default entries in this lookup definition.
Table 1-3 Entries in the Lookup.IDCS.Configuration lookup definition
| Code | Decode | Description |
|---|---|---|
|
Any Incremental Recon Attribute Type |
true |
By default, during incremental reconciliation, Oracle Identity Manager accepts time stamp information sent from the target system only in Long datatype format. A decode value of True for the Incremental Recon Attribute Type entry indicates that Oracle Identity Manager will accept time stamp information in any datatype format. |
|
attrToOClassMapping |
"__ACCOUNT__.groups=Groups" |
This entry denotes that the groups attribute of the __ACCOUNT__ object class is mapped to the Groups object class on the target. |
|
Bundle Name |
org.identityconnectors.genericscim |
This entry holds the name of the connector bundle package. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle. |
|
Connector Name |
org.identityconnectors.genericscim.GenericSCIMConnector |
This entry holds the name of the connector class. |
|
customPayload |
"__ACCOUNT__.password.UpdateOp={\"userName\":\"$(__ACCOUNT__.userName)$\",\"password\":\"$(__ACCOUNT__.password)$\",\"schemas\":[\"urn:ietf:params:scim:schemas:oracle:idcs:UserPasswordChanger\"]}","__ACCOUNT__.groups.AddOp={\"schemas\":[\"urn:ietf:params:scim:api:messages:2.0:PatchOp\"],\"Operations\":[{\"op\":\"add\",\"path\":\"members\",\"value\":[{\"value\":\"$(__ACCOUNT__.__UID__)$\"}]}]}" |
This entry holds the payloads for all operations that are not in the standard format. |
|
Group Configuration Lookup |
Lookup.IDCS.GM.Configuration |
This entry holds the name of the lookup definition that contains group-specific configuration properties. |
|
httpOperationTypes |
"__ACCOUNT__.password.UpdateOp=PUT" |
This entry indicates that for a Password Update operation, the target needs a PUT operation instead of PATCH. |
|
jsonResourcesTag |
Resources |
This JSON tag value is used during reconciliation for parsing multiple entries in a single response payload. |
|
nameAttributes |
"Users=userName","Groups=displayName" |
This entry indicates which attributes need to be treated as the __NAME__ attribute for which Object class. |
|
passwordAttributes |
"Users=password" |
This entry indicates which attributes need to be treated as the __PASSWORD__ attribute for which object class. |
|
relURLs |
"__ACCOUNT__.password.UpdateOp=/UserPasswordChanger/$(__ACCOUNT__.__UID__)$" |
This entry holds the relative URL of every object class supported by this connector and the connector operations that can be performed on these object classes. This entry indicates that for a Password Update operation, the /UserPasswordChanger endpoint needs to be hit, instead of the default /Users end point. |
|
scimVersion |
17 |
This indicates the SCIM version on which the target is implemented. |
|
statusAttributes |
"Users=active" |
This entry lists the name of the target system attribute that holds the status of an account. This entry indicates the status field: The __ENABLE__ field on the target for which object class. |
|
uidAttributes |
"Users=id","Groups=id" |
"This entry holds the UID attribute for the object which are handled by the connectors. For example for User accounts the UID attribute is ID. |
|
reconSortByAttrs |
"Users=id","Groups=id" |
This entry holds the attribute used for sorting the records during a reconciliation operation. |
|
User Configuration Lookup |
Lookup.IDCS.UM.Configuration |
This entry holds the name of the lookup definition that contains user-specific configuration properties. |
1.7.2.2 Lookup.IDCS.GM.Configuration
The Lookup.IDCS.GM.Configuration lookup definition holds configuration entries that are specific to the group object type.
This lookup definition is used during group management operations when your target system is configured as a target resource.
Table 1-4 lists the default entries in this lookup definition.
Table 1-4 Lookup.IDCS.GM.Configuration lookup definition
| Code | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.IDCS.GM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.IDCS.GM.ProvAttrMap for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.IDCS.GM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.IDCS.GM.ReconAttrMap for more information about this lookup definition. |
1.7.2.3 Lookup.IDCS.GM.ProvAttrMap
The Lookup.IDCS.GM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes.
This lookup definition is preconfigured and used during group provisioning operations. Table 1-13 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for provisioning. See Adding New User or Group Attributes for Provisioning.
1.7.2.4 Lookup.IDCS.GM.ReconAttrMap
The Lookup.IDCS.GM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes.
This lookup definition is preconfigured and used during target resource reconciliation of groups. Table 1-9 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for reconciliation. See Adding New User or Group Attributes for Reconciliation.
1.7.2.5 Lookup.IDCS.UM.Configuration
The Lookup.IDCS.UM.Configuration lookup definition holds configuration entries that are specific to the user object type.
This lookup definition is used during user management operations when your target system is configured as a target resource.
Table 1-5 lists the default entries in this lookup definition.
Table 1-5 Entries in the Lookup.IDCS.UM.Configuration Lookup Definition
| Code | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.IDCS.UM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. See Lookup.IDCS.UM.ProvAttrMap for more information about this lookup definition. |
|
Recon Attribute Map |
Lookup.IDCS.UM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.IDCS.UM.ReconAttrMap for more information about this lookup definition. |
1.7.2.6 Lookup.IDCS.UM.ProvAttrMap
The Lookup.IDCS.UM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes.
This lookup definition is preconfigured and used during provisioning. Table 1-12 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for provisioning. See Adding New User or Group Attributes for Provisioning.
1.7.2.7 Lookup.IDCS.UM.ReconAttrMap
The Lookup.IDCS.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes.
This lookup definition is preconfigured used during target resource reconciliation. Table 1-8 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for reconciliation. See Adding New User or Group Attributes for Reconciliation .
1.7.2.8 Lookup.IDCS.UserTypes
The Lookup.IDCS.UserTypes lookup definition holds the list of user types.
This is a static lookup definition. You cannot modify or add entries in this lookup definition.
Table 1-6 lists the default entries in this lookup definition.
Table 1-6 Entries in the Lookup.IDCS.UserTypes Lookup Definition
| Code Key | Decode |
|---|---|
|
contractor |
CONTRACTOR |
|
employee |
EMPLOYEE |
|
external |
EXTERNAL |
|
intern |
INTERN |
|
service |
SERVICE |
|
temp |
TEMP |
1.7.2.9 Lookup.IDCS.Organizations
The Lookup.IDCS.Organizations lookup definition holds the list of organizations.
This is a static lookup definition. The entries of this lookup needs to be updated manually based on the Organizations on the target.
Table 1-7 lists the default entry in this lookup definition.
Table 1-7 Entries in the Lookup.IDCS.Organizations Lookup Definition
| Code Key | Decode |
|---|---|
|
Xellerate Users |
Xellerate Users |
1.8 Connector Objects Used During Target Resource Reconciliation
Target resource reconciliation involves fetching data about newly created or modified accounts on the target system and using this data to add or modify resources assigned to Oracle Identity Manager users.
The IDCS Target Resource User Reconciliation scheduled job is used to initiate a reconciliation run. This scheduled job is discussed in Reconciliation Scheduled Jobs for Oracle Identity Cloud Service Connector.
See Also:
Managing Reconciliation in Oracle Fusion Middleware Administering Oracle Identity Manager for generic information about connector reconciliationThis section contains the following topics related to connector objects:
1.8.1 User Fields for Target Resource Reconciliation
The Lookup.IDCS.UM.ReconAttrMap lookup definition maps resource object fields with target system attributes.
These lookup definitions are used for performing target resource reconciliation runs.
In these lookup definition, entries are in the following format:
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system attribute
Table 1-8 lists the entries in the Lookup.IDCS.UM.ReconAttrMap lookup definition.
Table 1-8 Entries in the Lookup.IDCS.UM.ReconAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
|
__ACCOUNT__.emails.value,type:work,primary:true |
|
Employee Number |
employeeNumber |
|
First Name |
name.givenName |
|
Groups~Group Value[LOOKUP] |
__ACCOUNT__.groups~__ACCOUNT__.groups~value |
|
Id |
__UID__ |
|
Last Name |
name.familyName |
|
Manager[LOOKUP] |
manager.value |
|
Middle Name |
name.middleName |
|
Organization |
organization |
|
Status |
__ENABLE__ |
|
User Name |
__NAME__ |
|
User Type |
userType |
1.8.2 Group Fields for Reconciliation
The Lookup.IDCS.GM.ReconAttrMap lookup definition maps group resource object fields and target system attributes.
This lookup definition is used for performing target resource group reconciliation runs.
Table 1-9 lists the entries in the Lookup.IDCS.GM.ReconAttrMap lookup definition.
Table 1-9 Entries in the Lookup.IDCS.GM.ReconAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
Description |
description |
|
Group Id |
__UID__ |
|
Group Name |
__NAME__ |
|
OIM Organization Name |
OIM Organization Name |
1.8.3 Reconciliation Rules for Target Resource Reconciliation
The reconciliation engine uses rules to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system.
This section discuss the following topics related to users and groups reconciliation rule for target resource reconciliation:
1.8.3.1 Reconciliation Rule for Users
The Oracle Identity Cloud Service connector can perform reconciliation of both users and groups. Therefore, the connector has reconciliation rules defined specifically for users.
Rule name: IDCS User Recon Rule
Rule element: User Login Equals User Name
-
User Loginis the User ID field of the Oracle Identity Manager User form. -
User Nameis the Username attribute for users on the target.
1.8.3.2 Reconciliation Rule for Groups
The Oracle Identity Cloud Service connector can perform reconciliation of both users and groups. Therefore, the connector has reconciliation rules defined specifically for groups.
Rule name: IDCS Groups Recon Rule
Rule element: Organization Name Equals OIM Org Name.
-
Organization Nameis the Organization Name field of the Oracle Identity Manager User form. -
OIM Org Nameis the organization name of the groups in Oracle Identity Manager. OIM Org Name is the value specified in the Organization Name attribute of the IDCS Group Recon scheduled job.
1.8.3.3 Viewing Reconciliation Rules in the Design Console
After you deploy the connector, you can view the reconciliation rules for users and groups on the Reconciliation Rule Builder form in Oracle Identity Manager Design Console.
To view the reconciliation rule for target resource reconciliation of users and groups:
1.8.4 Reconciliation Action Rules for Oracle Identity Cloud Service
Reconciliation action rules specify the actions that the connector must perform depending on whether or not matching Oracle Identity Cloud Service resources or Oracle Identity Manager Users are found when the reconciliation rule is applied.
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions.The following sections provide information about the action rules for this connector:
1.8.4.1 Reconciliation Action Rules
Reconciliation action rules specify the actions the connector must perform based on the result of the processing of a reconciliation event. The reconciliation action rules for both users and groups are the same.
Table 1-10 lists the action rules for target resource reconciliation.
Table 1-10 Action Rules for Reconciliation for Target
| Rule Condition | Action |
|---|---|
|
No matches found |
None |
|
One entity match found |
Establish link |
|
One process match found |
Establish link |
1.8.4.2 Viewing Reconciliation Action Rules Reconciliation in Design Console
After you deploy the connector, you can view the reconciliation action rules for users and groups reconciliation by performing the following steps:
- Log in to the Oracle Identity Manager Design Console.
- Expand Resource Management, and double-click Resource Objects.
- Search for and open one of the following resource objects:
- For Users: IDCS User
- For Groups: IDCS Group
- Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules that are defined for this connector.
1.9 Connector Objects Used During Provisioning
Provisioning involves creating or modifying user data on the target system using Oracle Identity Manager.
This section provides information related to connector objects used during a provisioning operation:
1.9.1 Provisioning Functions
These are the supported provisioning functions and the adapters that perform these functions for the Oracle Identity Cloud Service connector.
The Adapter column in Table 1-11 provides the name of the adapter that is used when the function is performed.
See Also:
Types of Adapters in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about process tasks and adaptersTable 1-11 Provisioning Functions
| Function | Adapter |
|---|---|
|
Disable a user |
adpADIDCDISABLEUSER |
|
Add child data |
adpIDCSADDCHILDDATA |
|
Bulk update adapter |
adpIDCSBULKUPDATEADAPTER |
|
Create object |
adpIDCSCREATEOBJECT |
|
Delete object |
adpIDCSDELETEOBJECT |
|
Enable user |
adpIDCSENABLEUSER |
|
Prepopulate adapter |
adpIDCSPREPOPULATEADAPTER |
|
Remove child data |
adpIDCSREMOVECHILDDATA |
|
Update child data |
adpIDCSUPDATECHILDDATA |
|
Update object |
adpIDCSUPDATEOBJECT |
Note:
The password update task does not work with the parent form. It works only with the reset password operation.1.9.2 User Fields for Provisioning
The Lookup.IDCS.UM.ProvAttrMap lookup definition maps process form fields with target system attributes. This lookup definition is used for performing provisioning operations.
In this lookup definition, entries are in the following format:
-
Code Key: Name of the process form field
-
Decode: Name of the target system user attribute
Table 1-12 lists default entries in the Lookup.IDCS.UM.ProvAttrMap lookup definition.
Table 1-12 Entries in the Lookup.IDCS.UM.ProvAttrMap lookup definition
| Code | Decode |
|---|---|
|
Creation Mechanism |
creationMechanism |
|
|
__ACCOUNT__.emails.value,type:work,primary:true |
|
Employee Number |
employeeNumber |
|
First Name |
name.givenName |
|
Id |
__UID__ |
|
Last Name |
name.familyName |
|
Manager[LOOKUP] |
manager.value |
|
Middle Name |
name.middleName |
|
Organization |
organization |
|
Password |
__PASSWORD__ |
|
Status |
__ENABLE__ |
|
UD_IDCS_UGP~Group Value[LOOKUP] |
__ACCOUNT__.groups~__ACCOUNT__.groups~value |
|
User Name |
__NAME__ |
|
User Type |
userType |
1.9.3 Group Fields for Provisioning
The Lookup.IDCS.GM.ProvAttrMap lookup definition maps user resource object fields and target system attributes. This lookup definition is used for performing group provisioning operations.
In this lookup definition, entries are in the following format:
-
Code Key: Name of the process form field
-
Decode: Name of the target system group attribute
Table 1-13 lists default entries in the Lookup.IDCS.GM.ProvAttrMap lookup definition.
Table 1-13 Entries in the Lookup.IDCS.GM.ProvAttrMap lookup definition
| Code | Decode |
|---|---|
|
Description |
description |
|
Group Id |
__UID__ |
|
Group Name |
__NAME__ |
|
OIM Organization Name |
OIM Organization Name |
1.10 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Deploying the Oracle Identity Cloud Service Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the Oracle Identity Cloud Service Connector describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Extending the Functionality of the Oracle Identity Cloud Service Connector describes procedures that you can perform if you want to extend the functionality of the connector.
-
Files and Directories on the Installation Media lists the files and directories that comprise the connector installation media.