2 Deploying the Salesforce Connector
The procedure to deploy the connector is divided across three stages namely preinstallation, installation, and postinstallation.
The following topics discuss these stages:
2.1 Preinstallation
Preinstallation for the Salesforce connector involves registering a client application (that is, the Salesforce connector) with the target system and obtaining the client ID and client secret for authenticating to the target system. It also involves creating a custom profile and an account in the target system that the connector (or client) can use for performing connector operations.
Note:
The detailed instructions for performing these preinstallation tasks are available in the Salesforce documentation.2.2 Installation
You must install the Salesforce connector in Oracle Identity Manager and if required, place the connector code bundle in the Connector Server.
The following topics discuss installing the Salesforce connector:
2.2.1 Understanding Installation of the Salesforce Connector
You can run the connector code either locally in Oracle Identity Manager or remotely in a Connector Server.
-
Run the connector code locally in Oracle Identity Manager.
In this scenario, you deploy the connector in Oracle Identity Manager. Deploying the connector in Oracle Identity Manager involves performing the procedures described in Running the Connector Installer and Configuring the IT Resource for the Target System.
-
Run the connector code remotely in a Connector Server.
In this scenario, you deploy the connector in Oracle Identity Manager, and then, deploy the connector bundle in a Connector Server. See Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for information about installing, configuring, and running the Connector Server, and then installing the connector in a Connector Server.
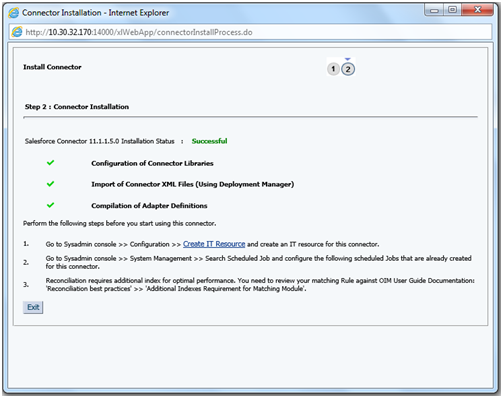
2.2.2 Running the Connector Installer
Note:
In this guide, the term Connector Installer has been used to refer to the Install Connectors feature of Oracle Identity System Administration.2.2.3 Configuring the IT Resource for the Target System
The IT resource for the target system is created during connector installation. This IT resource contains connection information about the target system. Oracle Identity Manager uses this information during reconciliation and provisioning.
The Salesforce IT resource is automatically created when you run the Connector Installer. You must specify values for the parameters of the IT resource.
To specify values for the parameters of the IT resource:
2.3 Postinstallation
Postinstallation steps are divided across the following sections:
2.3.1 Configuring Oracle Identity Manager
You must create a UI form and an application instance for the resource against which you want to perform reconciliation and provisioning operations. In addition, you must run entitlement and catalog synchronization jobs.
The following topics describe the procedures to configure Oracle Identity Manager:
2.3.1.1 Creating and Activating a Sandbox
2.3.1.2 Creating a New UI Form
2.3.1.3 Creating an Application Instance
Create an application instance as follows.
For detailed instructions, see Managing Application Instances in Oracle Fusion Middleware Administering Oracle Identity Manager.
2.3.1.4 Publishing a Sandbox
- In Identity System Administration, deactivate the sandbox.
- Log out of Identity System Administration.
- Log in to Identity Self Service using the xelsysadm user credentials and then activate the sandbox that you deactivated in Step 1.
- In the Catalog, ensure that the Salesforce application instance form appears with correct fields.
- Publish the sandbox. See Publishing a Sandbox in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager.
2.3.1.5 Harvesting Entitlements and Sync Catalog
- Run the scheduled jobs for lookup field synchronization listed in Scheduled Jobs for Lookup Field Synchronization.
- Run the Entitlement List scheduled job to populate Entitlement Assignment schema from child process form table. See Predefined Scheduled Tasks in Oracle Fusion Middleware Administering Oracle Identity Manager for more information about this scheduled job.
- Run the Catalog Synchronization Job scheduled job. See Predefined Scheduled Tasks in Oracle Fusion Middleware Administering Oracle Identity Manager for more information about this scheduled job.
2.3.1.6 Updating an Existing Application Instance with a New Form
- Create a sandbox and activate it as described in Creating and Activating a Sandbox.
- Create a new UI form for the resource as described in Creating a New UI Form.
- Open the existing application instance.
- In the Form field, select the new UI form that you created.
- Save the application instance.
- Publish the sandbox as described in Publishing a Sandbox.
2.3.2 Localizing Field Labels in UI Forms
You can localize UI form field labels by using the resource bundle corresponding to the language you want to use. Resource bundles are available in the connector installation media.
2.3.3 Clearing Content Related to Connector Resource Bundles from the Server Cache
When you deploy the connector, the resource bundles are copied from the resources directory on the installation media into the Oracle Identity Manager database. Whenever you add a new resource bundle to the connectorResources directory or make a change in an existing resource bundle, you must clear content related to connector resource bundles from the server cache.
2.3.4 Managing Logging for the Salesforce Connector
Oracle Identity Manager uses the Oracle Diagnostic Logging (ODL) logging service for recording all types of events pertaining to the connector.
2.3.4.1 Understanding Log Levels
When you enable logging, Oracle Identity Manager automatically stores in a log file information about events that occur during the course of provisioning and reconciliation operations. ODL is the principle logging service used by Oracle Identity Manager and is based on java.util.Logger. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that might allow Oracle Identity Manager to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These log levels are mapped to ODL message type and level combinations as shown in Table 2-2.
Table 2-2 Log Levels and ODL Message Type:Level Combinations
| Log Level | ODL Message Type:Level |
|---|---|
|
SEVERE.intValue()+100 |
INCIDENT_ERROR:1 |
|
SEVERE |
ERROR:1 |
|
WARNING |
WARNING:1 |
|
INFO |
NOTIFICATION:1 |
|
CONFIG |
NOTIFICATION:16 |
|
FINE |
TRACE:1 |
|
FINER |
TRACE:16 |
|
FINEST |
TRACE:32 |
The configuration file for OJDL is logging.xml, which is located at the following path:
DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SERVER are the domain name and server name specified during the installation of Oracle Identity Manager.
2.3.5 Obtaining GUID of Roles
You must obtain the GUID of roles from the target system to populate the Code Key values of the Lookup.Salesforce.Roles lookup definition.
00E800000016mY is the GUID of the selected role:https://cs40.salesforce.com.00E800000016mY.setupid=Roles2.3.6 Configuring SSL for connector
Configure SSL to secure data communication between Oracle Identity Manager and Salesforce.
Note:
If you are using this connector along with a Connector Server, then there is no need to configure SSL. You can skip this section.Importing the Certificate
Use the keytool command to import the SSL certificate from the target system into the identity keystore in Oracle Identity Manager.
keytool -import -alias alias -trustcacerts -file file-to-import -keystore keystore-name -storepass keystore-password
In this example, the certificate file supportcert.pem is imported to the identity keystore client_store.jks with password weblogic1:
keytool -import -alias serverwl -trustcacerts -file supportcert.pem -keystore client_store.jks -storepass weblogic1
Note:
Change the parameter values passed to the keytool command according to your requirements. Ensure that there is no line break in the keytool arguments.