1 About the Salesforce Connector
The Salesforce connector integrates Oracle Identity Manager with the Salesforce.com target system.
This chapter contains the following sections:
1.1 Introduction to the Salesforce Connector
Note:
At some places in this guide, the term target system has been used to refer to Salesforce.com.The Salesforce connector enables you to perform identity management-related tasks (such as creating, updating, and deleting) on user and group identities while managing their profiles at the same time.
In the account management (target resource) mode of the connector, information about all active users created or modified directly on the target system can be reconciled into Oracle Identity Manager. This data is used to add or modify resources (that is, accounts) allocated to OIM Users. In addition, you can use Oracle Identity Manager to provision or update Salesforce resources (accounts) assigned to OIM Users. These provisioning operations performed on Oracle Identity Manager translate into the creation or updates to target system accounts.
In the identity reconciliation (trusted source) mode of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager.
1.2 Certified Components for the Salesforce Connector
These are the software components and their versions required for installing and using the Salesforce connector.
Table 1-1 Certified Components
| Component | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
|
Target systems |
Salesforce Winter 2012 and later releases |
|
Connector Server |
1.4.0 |
|
Connector Server JDK |
JDK 1.6 or later |
1.3 Certified Languages for the Salesforce Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English (US)
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
1.4 Architecture of the Salesforce Connector
The Salesforce connector is implemented by using the Identity Connector Framework (ICF).
The ICF is a component that is required in order to use Identity Connector. ICF provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as, buffering, time outs, and filtering. ICF is distributed together with Oracle Identity Manager. Therefore, you do not need to configure or modify ICF.
The connector is configured to run in one of the following modes:
-
Identity reconciliation
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this mode, the target system is used as the trusted source and users are directly created and modified on it. During reconciliation, each user record fetched from the target system is compared with existing OIM Users. If a match is found between the target system record and the OIM User, then the OIM User attributes are updated with changes made to the target system record. If no match is found, then the target system record is used to create an OIM User.
-
Account management
Account management is also known as target resource management. In this mode, the target system is used as a target resource and the connector enables the following operations:
-
Provisioning
Provisioning involves creating or updating users on the target system through Oracle Identity Manager. When you allocate (or provision) a Salesforce resource to the OIM User, the operation results in the creation of an account on Salesforce for that user. In the Oracle Identity Manager context, the term provisioning also covers updates made to the target system account through Oracle Identity Manager.
-
Target resource reconciliation
In target resource reconciliation, data related to the newly created and modified target system accounts can be reconciled and linked with existing OIM Users and provisioned resources. A scheduled task is used for reconciliation. Salesforce.com provides the details of only the active user accounts.
-
Figure 1-1 Salesforce Connector Architecture
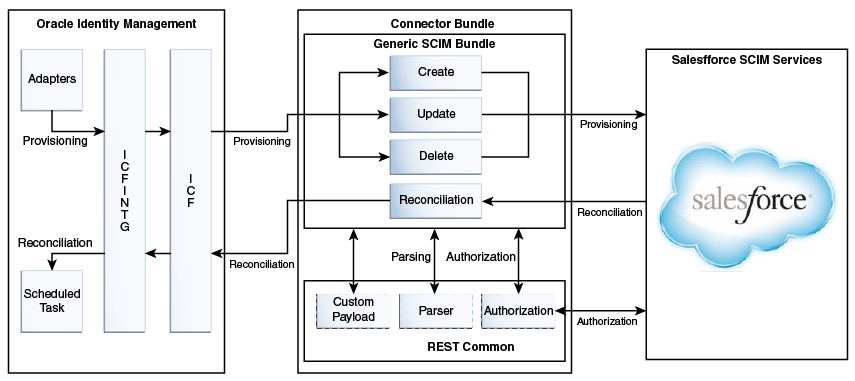
Description of "Figure 1-1 Salesforce Connector Architecture"
As shown in Figure 1-1, Salesforce.com is configured as a target resource of Oracle Identity Manager. Through provisioning operations performed on Oracle Identity Manager, accounts are created and updated on the target system for OIM Users.
Through reconciliation, account data that is created and updated directly on the target system is fetched into Oracle Identity Manager and stored against the corresponding OIM Users.
Identity Connector Framework (ICF) is a component that is required in order to use Identity Connectors. ICF is distributed together with Oracle Identity Manager. You do not need to configure or modify ICF.
During provisioning, the Adapters invoke ICF operation, ICF inturn invokes create operation on Salesforce Identity Connector Bundle and then the bundle calls Salesforce Provisioning API. The Salesforce provisioning API on the target system accepts provisioning data from the bundle, carries out the required operation on the target system, and returns the response from the target system back to the bundle, which passes it to the adapters.
During reconciliation, a scheduled task invokes ICF operation, ICF inturn invokes create operation on Salesforce Identity Connector Bundle and then the bundle calls Salesforce Reconciliation API. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Manager.
1.5 Use Cases Supported by the Salesforce Connector
These are common scenarios in which the connector can be used.
-
Salesforce License Management
On Salesforce.com, Profiles are used to manage licences which are in turn associated with user types. So for a particular user type, there is a fixed set of profiles. Using the Salesforce connector, you can reconcile all the profiles from Salesforce and assign them to users without worrying about the user types. Thus, switching the user from one license type to another is accomplished easily with the use of the Salesforce connector. This will arise if one Chatter Free user is promoted to Standard user in Salesforce and can enjoy the privileges that come along with those predefined licenses.
Salesforce Connector is also used to enable specific Salesforce.com profiles for your users, you must choose one profile for each user. A profile is a template that contains a collection of predefined settings and can determine what a user can see and do within the platform. The basic rule of Profiles is whether a given user can see and use each application as well as each tab within the application.
-
One Stop Identity Solution for Multiple Cloud Applications
Salesforce.com can act as a trusted source of identities which can be used to map users against various target cloud applications. In this case, a user from Salesforce can be created in any and every cloud and non-cloud applications that Oracle Identity Manager supports.
Salesforce.com can be used as a trusted source and an organization can use this feature to provide the list of users and further provision the account of these users to a third-party application that has been configured as target source.
-
Evolve Identity and Data Security of Salesforce Beyond the Parameter
Identity management solutions must support more than the traditional parameter-based authentication, and offer a single, simple, and trusted way to manage authentication and authorization of salesforce-based authentications. Enterprises making use of various IT systems (servers, devices, applications etc.) face numerous challenges due to the proliferation of passwords. Any vulnerability for password creates an opportunity for an attacker to acquire password values and consequently impersonate users. Oracle Salesforce Connector helps reduce administrative and help desk costs by enabling self-service password reset and password change.
This following image illustrates about controlling the access that the user has by managing Roles, Groups and Profiles.
Figure 1-2 Manage Roles, Groups, and Profiles to Control Access by the User
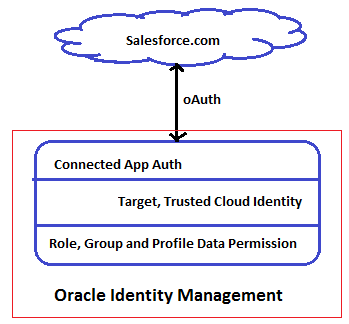
Description of "Figure 1-2 Manage Roles, Groups, and Profiles to Control Access by the User"
1.6 Features of the Salesforce Connector
The features of the connector include support for connector server, full reconciliation, limited reconciliation, and transformation and validation of account data.
1.6.1 Full Reconciliation
Full reconciliation involves reconciling all active user records from the target system into Oracle Identity Manager.
Note:
To eliminate the Automated Process User that the Salesforce sandbox has and to get all the users successfully during full reconciliation, you must add the following filter,greaterThan('userType','AutomatedProcest')|lessThan('userType','AutomatedProcess')To perform a full reconciliation run, remove or delete any value assigned to the Filter and run the scheduled job for user reconciliation.
Note:
-
The connector cannot support incremental reconciliation because the target system does not provide a way for tracking the time at which account data is created or modified.
-
If the target system contains more than 2200 records, then use the Flat File connector to perform full reconciliation as Salesforce.com does not allow you to reconcile more than 2200 users even after pagination. See Reconciling Large Number of Records.
1.6.2 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not want to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements if the bundle works faster when deployed on the same host as the native managed resource.
1.6.3 Limited Reconciliation
Limited or filtered reconciliation is the process of limiting the number of records being reconciled based on a set filter criteria.
To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled. See Limited Reconciliation.
1.6.4 Transformation and Validation of Account Data
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning.
In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation. The following sections provide more information:
1.7 Lookup Definitions Used During Connector Operations
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
Lookup definitions used during connector operations can be categorized as follows:
1.7.1 Lookup Definitions Synchronized with the Target System
Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Group Name lookup field to specify a group for the user for whom the provisioning operation is being performed. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization populates these lookup fields with values from the corresponding lookup definitions.
1.7.1.1 Lookup.Salesforce.Groups
The Lookup.Salesforce.Groups lookup definition holds details of groups defined in Salesforce.com. You populate this lookup definition through lookup field synchronization performed using the Salesforce Group Lookup Reconciliation scheduled job.
The following is the format in which data is stored after lookup definition synchronization:
-
Code Key: IT_RESOURCE_KEY~GROUP_ID
In this format:-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
GROUP_ID is GUID of the group on the target system.
-
-
Decode: IT_RESOURCE_NAME~GROUP_NAME
In this format:-
IT_RESOURCE_NAME is the name assigned to the IT resource in Oracle Identity Manager.
-
GROUP_NAME is the name of the group on the target system.
-
Table 1-2 lists sample entries in this lookup definition.
Table 1-2 Sample Entries in the Lookup.Salesforce.Groups Lookup Definition
| Code Key | Decode |
|---|---|
|
461~00G80000001gXdyEAE |
Salesforce~Company Labs |
|
461~00G54000000FcXxEAK |
Salesforce~IT |
|
461~00G54000000Fcc9EAC |
Salesforce~BusinessIntelligence |
1.7.1.2 Lookup.Salesforce.Profiles
The Lookup.Salesforce.Profiles lookup definition holds details of profiles defined in Salesforce. You populate this lookup definition through lookup field synchronization performed using the Salesforce Profile Lookup Reconciliation scheduled job.
The following is the format in which data is stored after lookup definition synchronization:
-
Code Key: IT_RESOURCE_KEY~PROFILE_ID
In this format:-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
PROFILE_ID is GUID of the Profile on the target system.
-
-
Decode: IT_RESOURCE_NAME~PROFILE_NAME
In this format:-
IT_RESOURCE_NAME is the name assigned to the IT resource in Oracle Identity Manager.
-
PROFILE_NAME is the name of the profile on the target system.
-
Table 1-3 lists sample entries in this lookup definition.
Table 1-3 Entries in the Lookup.Salesforce.Profile Lookup definition
| Code Key | Decode |
|---|---|
|
161~00e80000001aotvAAA |
Salesforce~Chatter Free User |
|
161~00e30000000iEpoAAE |
Salesforce~Standard Platform User |
|
161~ooe800000018uFGAAY |
Salesforce~Salesforce~S&OP 2 |
1.7.2 Preconfigured Lookup Definitions
Preconfigured lookup definitions are automatically created in Oracle Identity Manager after you deploy the connector.
These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed. The preconfigured lookup definitions are as follows:
1.7.2.1 Lookup.Salesforce.Configuration
The Lookup.Salesforce.Configuration lookup definition holds connector configuration entries that are used during target resource reconciliation and provisioning operations.
The Lookup.Configuration.Salesforce lookup definition contains the entries shown in Table 1-4
Note:
Do not modify any of the entries in Table 1-4.Table 1-4 Entries in the Lookup.Configuration.Salesforce Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Bundle Name |
org.identityconnectors.genericscim |
This entry holds the name of the connector bundle. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle. |
|
Connector Name |
org.identityconnectors.genericscim.GenericSCIMConnector |
This entry holds the name of the connector class. |
|
Group Configuration Lookup |
Lookup.Salesforce.GM.Configuration |
This entry holds the name of the lookup definition that contains group-specific configuration properties. This lookup definition is used as the configuration lookup definition when you perform group management operations. |
|
User Configuration Lookup |
Lookup.Salesforce.UM.Configuration |
This entry holds the name of the lookup definition that stores configuration information used during user management operations. |
|
defaultBatchSize |
200 |
This is the number of records that can be retrieved from the target system in one go. |
|
nameAttributes |
"Users=userName","Groups=displayName","Entitlement=displayName" |
This is the __NAME__ attribute mapping of Oracle Identity Manager to the relevant attribute on target system. |
|
attrToOClassMapping |
"__ACCOUNT__.groups=Groups" |
This is used to map an attribute present under one object class to another object class. For example "groups" under "__ACCOUNT__" Object Class should be mapped to "__GROUP__" object class. Sample value is " |
|
jsonResourcesTag |
Resources |
This entry holds the name of the JSON tag that holds user details in the response payload. |
|
customPayload |
"__ACCOUNT__.groups.AddOp={\"displayName\":\"$(__GROUP__.displayName)$\",\"members\":[{\"operation\":\"add\",\"value\":\"$(__ACCOUNT__.__UID__)$\"}]}","__ACCOUNT__.groups.RemoveOp={\"displayName\":\"$(__GROUP__.displayName)$\",\"members\":[{\"operation\":\"delete\",\"value\":\"$(__ACCOUNT__.__UID__)$\"}]}","__ACCOUNT__.phoneNumbers.RemoveOp={\"phoneNumbers\":[{\"type\":\"$(__ACCOUNT__.phoneNumbers.type)$\",\"value\":\"\"}]}" |
This takes the custom payloads necessary to carry out specific operation for specific attributes on the target system. |
|
scimVersion |
1 |
This entry specifies the supported SCIM version of the target system. |
|
statusAttributes |
"Users=active" |
This is the __ENABLE__ attribute mapping of Oracle Identity Manager to the Status attribute on target system. |
|
uidAttributes |
“Users=id","Groups=id", "Entitlement=id" |
This is the __UID__ attribute mapping of Oracle Identity Manager to the GUID attribute on target system. |
|
passwordAttributes |
“Users=password" |
This entry holds the name of the target system attribute that is mapped to the __PASSWORD__ attribute of the connector in OIM. |
1.7.2.2 Lookup.Salesforce.Configuration.Trusted
The Lookup.Salesforce.Configuration.Trusted lookup definition holds connector configuration entries that are used during trusted source reconciliation.
Note:
Do not modify any of the entries listed in Table 1-5.Table 1-5 Entries in the Lookup.Salesforce.Configuration.Trusted Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Bundle Name |
org.identityconnectors.genericscim |
This entry holds the name of the connector bundle. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle. |
|
Connector Name |
org.identityconnectors.genericscim.GenericSCIMConnector |
This entry holds the name of the connector class. |
|
User Configuration Lookup |
Lookup.Salesforce.UM.Configuration.Trusted |
This entry holds the name of the lookup definition that contains user-specific configuration properties. |
|
defaultBatchSize |
200 |
This is the number of records that can be retrieved from the target system in one go. |
|
nameAttributes |
"Users=userName" |
This is the __NAME__ attribute mapping of Oracle Identity Manager to the relevant attribute on target system. |
|
attrToOClassMapping |
"__ACCOUNT__.groups=Groups" |
This is used to map an attribute present under one object class to another object class. For example "groups" under "__ACCOUNT__" Object Class should be mapped to "__GROUP__" object class. Sample value is " |
|
jsonResourcesTag |
Resources |
This entry holds the name of the JSON tag that holds user details in the response payload. |
|
customPayload |
"__ACCOUNT__.groups.AddOp={\"displayName\":\"$(__GROUP__.displayName)$\",\"members\":[{\"operation\":\"add\",\"value\":\"$(__ACCOUNT__.__UID__)$\"}]}","__ACCOUNT__.groups.RemoveOp={\"displayName\":\"$(__GROUP__.displayName)$\",\"members\":[{\"operation\":\"delete\",\"value\":\"$(__ACCOUNT__.__UID__)$\"}]}","__ACCOUNT__.phoneNumbers.RemoveOp={\"phoneNumbers\":[{\"type\":\"$(__ACCOUNT__.phoneNumbers.type)$\",\"value\":\"\"}]}" |
This takes the custom payloads necessary to carry out specific operation for specific attributes on the target system. |
|
scimVersion |
1 |
This entry specifies the supported SCIM version of the target system. |
|
statusAttributes |
"Users=active" |
This is the __ENABLE__ attribute mapping of Oracle Identity Manager to the Status attribute on target system. |
|
uidAttributes |
"Users=id" |
This is the __UID__ attribute mapping of Oracle Identity Manager to the GUID attribute on target system. |
|
passwordAttributes |
"Users=password" |
This entry holds the name of the target system attribute that is mapped to the __PASSWORD__ attribute of the connector in OIM. |
1.7.2.3 Lookup.Salesforce.UM.Configuration
The Lookup.Salesforce.UM.Configuration lookup definition holds configuration entries that are specific to the user object type.
This lookup definition is used during user management operations when your connector is configured in the target resource mode.
Table 1-6 lists the default entries in this lookup definition.
Table 1-6 Entries in the Lookup.Salesforce.UM.Configuration Lookup
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.Salesforce.UM.ProvAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Manager and the target system. This lookup definition is used during provisioning operations. |
|
Recon Attribute Map |
Lookup.Salesforce.UM.ReconAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Manager and the target system. This lookup definition is used during reconciliation. |
1.7.2.4 Lookup.Salesforce.UM.Configuration.Trusted
The Lookup.Salesforce.UM.Configuration.Trusted lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during trusted source user reconciliation runs.
Table 1-7 Entries in the Lookup.Salesforce.UM.Configuration.Trusted Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Recon Attribute Defaults |
Lookup.Salesforce.UM.ReconAttrMap.TrustedDefaults |
This entry holds the name of the lookup definition that maps reconciliation fields to their default values. See Lookup.Salesforce.UM.ReconAttrMap.TrustedDefaults. |
|
Recon Attribute Map |
Lookup.Salesforce.UM.ReconAttrMap.Trusted |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. See Lookup.Salesforce.UM.ReconAttrMap.Trusted. |
1.7.2.5 Lookup.Salesforce.UM.ProvAttrMap
The Lookup.Salesforce.UM.ProvAttrMap lookup definitions hold mappings between process form fields and target system attributes.
This lookup definition is used during provisioning. This lookup definition is preconfigured. Table 1-17 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for provisioning. See Adding New User or Group Attributes for Provisioning.
1.7.2.6 Lookup.Salesforce.UM.ReconAttrMap
The Lookup.Salesforce.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes.
This lookup definition is used during reconciliation. This lookup definition is preconfigured. Table 1-13 lists the default entries.
You can add entries in this lookup definition if you want to map new target system attributes for target resource reconciliation. See Adding New User or Group Attributes for Reconciliation.
1.7.2.7 Lookup.Salesforce.UM.ReconAttrMap.Trusted
The Lookup.Salesforce.UM.ReconAttrMap.Trusted lookup definitions is used during trusted source user reconciliation runs.
The Lookup.Salesforce.UM.ReconAttrMap.Trusted lookup definition holds mappings between resource object fields and target system attributes. This lookup definition is preconfigured. Table 1-19 lists the default entries of this lookup definition.
Note:
You must not modify Code Key and Decode values of the default entries. You cannot remove the mandatory fields. You can add additional fields to manage new attributes. See Adding New User or Group Attributes for Reconciliation.1.7.2.8 Lookup.Salesforce.UM.ReconAttrMap.TrustedDefaults
The Lookup.Salesforce.UM.ReconAttrMap.TrustedDefaults lookup definition holds mappings between reconciliation fields and their default values.
The Lookup.Salesforce.UM.ReconAttrMap.TrustedDefaults lookup definition is used when there is a mandatory field on the OIM User form, but no corresponding field in the target system from which values can be fetched during trusted source reconciliation.
Table 1-8 lists the default entries in this lookup definition.
Table 1-8 Entries in the Lookup.Salesforce.UM.ReconAttrMap.TrustedDefaults Lookup Definition
| Code | Decode |
|---|---|
|
Organization |
Xellerate Users |
|
User Type |
End-User |
|
Employee Type |
Full-Time |
-
Code Key: Name of the reconciliation field of the Salesforce User resource object
-
Decode: Corresponding default value to be displayed
For example, assume a field named Preferred Communication Mode is a mandatory field on the OIM User form. Suppose the target system contains no field that stores information about the preferred mode of communication for a user account. During reconciliation, no value for the Preferred Communication Mode field is fetched from the target system. However, as the Preferred Communication Mode field cannot be left empty, you must specify a value for this field. Therefore, create an entry in this lookup definition with the Code Key value set to Preferred Communication Mode and Decode value set to Email. This implies that the value of the Preferred Communication Mode field on the OIM User form displays Email for all user accounts reconciled from the target system.
1.7.2.9 Lookup.Salesforce.GM.Configuration
The Lookup.Salesforce.GM.Configuration lookup definition holds configuration entries that are specific to the group object type.
This lookup definition is used during group management operations when the connector is configured in the target resource mode.
Table 1-9 lists the default entries in this lookup definition.
Table 1-9 Entries in the Lookup.Salesforce.GM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.Salesforce.GM.ProvAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Manager and the target system. This lookup definition is used during group provisioning operations. |
|
Recon Attribute Map |
Lookup.Salesforce.GM.ReconAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Manager and the target system. This lookup definition is used during reconciliation. |
1.7.2.10 Lookup.Salesforce.GM.ProvAttrMap
The Lookup.Salesforce.GM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes.
This lookup definition is used during group provisioning operations. This lookup definition is preconfigured. Table 1-18 lists the default entries.
1.7.2.11 Lookup.Salesforce.GM.ReconAttrMap
The Lookup.Salesforce.GM.ReconAttrMap lookup definitions are used during reconciliation runs for the Group object.
The Lookup.Salesforce.GM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. This lookup definition is preconfigured. Table 1-14 lists the default entries.
Note:
You must not modify the Code Key and Decode values of the default entries. You must not remove the mandatory fields. You can add additional fields to manage new attributes. See Adding New User or Group Attributes for Reconciliation.1.7.2.12 Lookup.Salesforce.PreferredLanguages
The Lookup.Salesforce.PreferredLanguages lookup definition holds the list of languages that you can select and set a preferred language for a user account that you create through Oracle Identity Manager.
This lookup definition is a static lookup definition. You must populated its entries manually.
Table 1-10 Entries in the Lookup.Salesforce.PreferredLanguages Lookup Definition
| Code Key | Decode |
|---|---|
|
en_US |
ENGLISH |
1.7.2.13 Lookup.Salesforce.PhoneType
This is a static lookup defintion where each value denotes the Phone type specific to the target system and the values should not be changed.
Table 1-11 Entires in the Lookup.Salesforce.PhoneType Lookup Definition
| Code | Decode |
|---|---|
|
fax |
FAX |
|
mobile |
MOBILE |
|
work |
WORK |
1.7.2.14 Lookup.Salesforce.Roles
The Lookup.Salesforce.Roles lookup definition holds the list of roles that you can select for a user account that you create through Oracle Identity Manager.
The Lookup.Salesforce.Roles lookup definition is a static lookup definition and has to be manually populated with all the roles present on the target.
-
Code Key: ROLE_ID
In this format, ROLE_ID is GUID of the Roles on the target system. See Obtaining GUID of Roles.
-
Decode: ROLE_NAME
In this format, ROLE_NAME is the name of the Role on the target system.
Table 1-12 Entries in the Lookup.Salesforce.Roles Lookup Definition
| Code Key | Decode |
|---|---|
|
00E800000024rvLEA |
practices |
|
00E800000016occ2EA |
CEO |
1.7.2.15 Lookup.Salesforce.Locale
The Salesforce locale settings determine the display formats for date and time, users’ names, addresses, and commas and periods in numbers.
1.8 Connector Objects Used During Target Resource Reconciliation
Target resource reconciliation involves fetching data about newly created or modified accounts on the target system and using this data to add or modify resources assigned to OIM Users.
The Salesforce.com Target Resource User Reconciliation scheduled job is used to initiate a reconciliation run. This schedule job is discussed in Reconciliation Scheduled Jobs.
This section discusses the following topics related to connector objects:
1.8.1 User Fields for Target Resource Reconciliation
The Lookup.Salesforce.UM.ReconAttrMap lookup definition maps resource object fields with target system attributes. This lookup definition is used for performing target resource user reconciliation runs.
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system attribute
Table 1-13 lists the entries in the lookup definition.
Table 1-13 Entries in the Lookup.Salesforce.UM.ReconAttrMap Lookup Definition
| Code Key (Resource Object Field) | Decode (Salesforce Field) |
|---|---|
|
Role |
__ACCOUNT__.roles.value |
|
Profile[LOOKUP] |
__ACCOUNT__.entitlements.value,primary:true |
|
Status |
__ENABLE__ |
|
Groups~Group Name[LOOKUP] |
__ACCOUNT__.groups~__ACCOUNT__.groups~value |
|
Phone Numbers~Value |
__ACCOUNT__.phoneNumbers~__ACCOUNT__.phoneNumbers~value |
|
Phone Numbers~Type |
__ACCOUNT__.phoneNumbers~__ACCOUNT__.phoneNumbers~type |
|
ID |
__UID__ |
|
User Name |
__NAME__ |
|
First Name |
name.givenName |
|
Last Name |
name.familyName |
|
Preferred Language |
preferredLanguage |
|
Title |
Title |
|
Locale |
Locale |
|
Nick Name |
Nickname |
|
|
__ACCOUNT__.emails.value,type:work |
1.8.2 Group Fields for Reconciliation
The Lookup.Salesforce.GM.ReconAttrMap lookup definition maps user resource object fields and target system attributes.
This lookup definition is used for performing target resource group reconciliation runs.
Table 1-14 lists the group fields of the target system from which values are fetched during reconciliation. The Salesforce Group Recon scheduled job is used to reconcile group data.
Table 1-14 Entries in the Lookup.Salesforce.GM.ReconAttrMap Lookup Definition
| Group Field on Oracle Identity Manager | Salesforce Field |
|---|---|
|
Display Name |
__NAME__ |
|
ID |
__UID__ |
|
OIM Organization Name |
OIM Organization Name |
1.8.3 Reconciliation Rules for Target Resource Reconciliation
Reconciliation rules for target resource reconciliation are used by the reconciliation engine to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system.
The Salesforce connector can perform reconciliation of both users and groups. Therefore, the connector has reconciliation rules defined for both users and groups.
Reconciliation Rule for Users
The following is the process-matching rule for users:
Rule name: Salesforce User Recon Rule
Rule element: User Login Equals User Name
-
User Login is the User ID field of the OIM User form.
-
User Name is the name attribute which is unique field of the Salesforce account.
Reconciliation Rule for Groups
The following is the process-matching rule for groups:
Rule name: Salesforce Groups Recon Rule
Rule element: Organization Name Equals OIM Org Name
-
Organization Name is the Organization Name field of the OIM User form.
-
OIM Org Name is the organization name of the groups in Oracle Identity Manager. OIM Org Name is the value specified in the Organization Name attribute of the Salesforce Group Recon scheduled job.
1.8.4 Viewing Reconciliation Rules for Target Resource Reconciliation
You can view reconciliation rules by using Oracle Identity Manager Design Console.
- Log in to the Oracle Identity Manager Design Console.
- Expand Development Tools.
- Double-click Reconciliation Rules.
- Search for and open one of the following reconciliation rules:
- For Users: Salesforce User Recon Rule
Figure 1-3 shows the target resource reconciliation rule for users.
Figure 1-3 Reconciliation Rule for Target Resource Reconciliation of Users
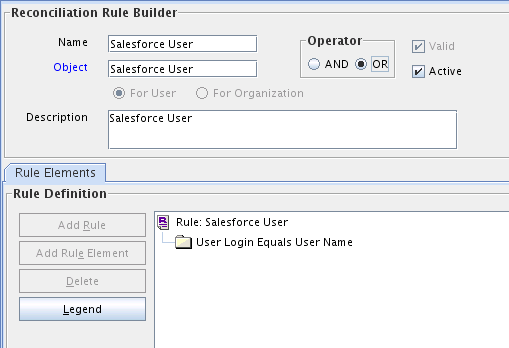
Description of "Figure 1-3 Reconciliation Rule for Target Resource Reconciliation of Users"
- For Groups: Salesforce Groups Recon Rule
Figure 1-4 shows the target resource reconciliation rule for groups.
Figure 1-4 Reconciliation Rule for Target Resource Reconciliation of Groups
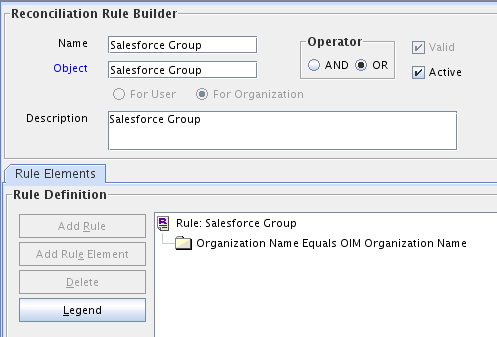
Description of "Figure 1-4 Reconciliation Rule for Target Resource Reconciliation of Groups"
- For Users: Salesforce User Recon Rule
1.8.5 Reconciliation Action Rules for Target Resource Reconciliation
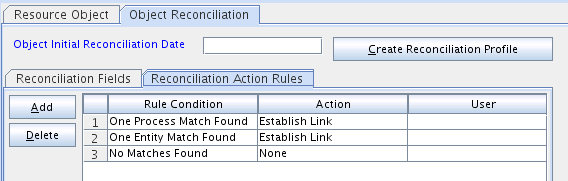
Reconciliation action rules define that actions the connector must perform based on the reconciliation rules defined for Users and Groups.
Table 1-15 Action Rules for Target Resource Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
None |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
1.9 Connector Objects Used During Provisioning
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
This section confers the following topics:
1.9.1 Provisioning Functions
These are the supported provisioning functions and the adapters that perform these functions for the Salesforce connector.
The Adapter column in Table 1-16 gives the name of the adapter that is used when the function is performed.
Table 1-16 User provisioning functions
| Function | Adapter |
|---|---|
|
Create User |
adpSALESFORCECREATEOBJECT |
|
Update User |
adpSALESFORCEUPDATEATTRIBUTEVALUE |
|
Delete user |
adpSALESFORCEDELETEOBJECT |
|
Enable user |
adpSALESFORCEENABLETASK |
|
Disable user |
adpSALESFORCEDISABLETASK |
|
Change or reset password |
adpSALESFORCEUPDATEATTRIBUTEVALUE |
|
Update child table values |
adpSALESFORCEUPDATECHILDTABLEVALUE |
|
Add child table values |
adpSALESFORCEADDCHILDATA |
|
Remove child table values for a user |
adpSALESFORCEREMOVECHILDATA |
Note:
Delete user is not supported in Salesforce.com. Deleting the user through SCIM API results in disabling the user on the target system.1.9.2 User Fields for Provisioning
The Lookup.Salesforce.UM.ProvAttrMap lookup definition maps process form fields with target system fields. This lookup definition is used for performing user provisioning operations.
Table 1-17 Entries in the Lookup.Salesforce.UM.ProvAttrMap Lookup Definitions
| Code Key (Process Form Field) | Decode (Salesforce Field) |
|---|---|
|
Role |
__ACCOUNT__.roles.value |
|
UD_SF_UGP~Group Name[LOOKUP] |
ACCOUNT__.groups~__ACCOUNT__.groups~value |
|
UD_SF_PHONE~Phone Number |
__ACCOUNT__.phoneNumbers~__ACCOUNT__.phoneNumbers~value |
|
UD_SF_PHONE~Type |
__ACCOUNT__.phoneNumbers~__ACCOUNT__.phoneNumbers~type |
|
User Name |
__NAME__ |
|
Last Name |
name.familyName |
|
First Name |
name.givenName |
|
Preferred Language |
preferredLanguage |
|
Title |
Country |
|
Nick Name |
Nickname |
|
Locale |
Locale |
|
Profile[LOOKUP] |
__ACCOUNT__.entitlements.value,primary:true |
|
ID |
__UID__ |
|
|
__ACCOUNT__.emails.value,type:work |
|
Password |
___PASSWORD___ |
1.9.3 Group Fields for Provisioning
The Lookup.Salesforce.GM.ProvAttrMap lookup definition maps user resource object fields and target system attributes. This lookup definition is used for performing group provisioning operations.
While assigning multiple groups with the same name, the target appends a number to the group name. Therefore, you must execute Group target reconciliation job every time multiple groups with the same name are provisioned on the target system to bring target and OIM in synchronization. Table 1-18 lists the group fields of the target system for which you can specify or modify values during provisioning operations.
Table 1-18 Entries in the Lookup.Salesforce.GM.ProvAttrMap Lookup Definition
| Group Field on Oracle Identity Manager | Salesforce Field |
|---|---|
|
Display Name |
__NAME__ |
|
ID |
__UID__ |
1.10 Connector Objects Used During Trusted Source Reconciliation
Trusted source reconciliation involves fetching data about newly created or modified accounts on the target system and using that data to create or update OIM Users.
The Salesforce Trusted User Recon and Salesforce Trusted User Reconciliation scheduled jobs are used to initiate trusted source reconciliation runs.
This section discusses the following topics:
1.10.1 User Fields for Trusted Source Reconciliation
The Lookup.Salesforce.UM.ReconAttrMap.Trusted lookup definition maps user fields of the OIM User form with corresponding field names in the target system. This lookup definition is used for performing trusted source reconciliation runs.
Table 1-19 Entries in the Lookup.Salesforce.UM.ReconAttrMap.Trusted Lookup Definition
| Code Key (OIM User Form Field) | Decode (Target System Field) |
|---|---|
|
Preferred Language |
preferredLanguage |
|
|
__ACCOUNT__.emails.value,type:wor k |
|
Status[TRUSTED] |
__ENABLE__ |
|
ID |
__UID__ |
|
User Name |
__NAME__ |
|
First Name |
name.givenName |
|
Last Name |
name.familyName |
|
Display Name |
displayName |
1.10.2 Reconciliation Rules for Trusted Source Reconciliation
Reconciliation rules for trusted source reconciliation are used by the reconciliation engine to determine the OIM User identity that must be created or updated for the corresponding account in the target system.
In the reconciliation rule, Salesforce GUID on OIM should match the Account ID on target or User Login on OIM should match the UserName on the target system.
Reconciliation Rule for Users
The following is the process-matching rule for users:
Rule name: Salesforce User Trusted Recon Rule
Rule element: Salesforce GUID Equals ID or User Login Equals User Name
-
Salesforce GUID is the UDF Field for Salesforce Connector on OIM
-
ID is the Account ID of Salesforec User on the target.
-
User Login is the User ID field of the OIM User form.
-
User Name is the name attribute which is unique field of the Salesforce account.
1.10.3 Reconciliation Action Rules for Trusted Source Reconciliation
Reconciliation action rules define the actions that must be performed based on the reconciliation rules.
Table 1-20 Action Rules for Trusted Source Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Create User |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
1.11 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Deploying the Salesforce Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the Salesforce Connector describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Extending the Functionality of the Salesforce Connector describes the procedures to perform if you want to extend the functionality of the connector.
-
Files and Directories on the Installation Media lists the files and directories in the installation media.