1 About the Box Connector
The Box connector integrates Oracle Identity Manager (OIM) with the Box target system.
The following topics provide a high-level overview of the Box connector:
1.1 Introduction to the Box Connector
The Box connector enables you to use Box as a managed (target) source of identity data for Oracle Identity Manager.
Oracle Identity Manager is a centralized identity management solution that provides self service, compliance, provisioning and password management services for applications residing on-premise or on the Cloud. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external, identity-aware applications. This guide provides information about the connector that enables you to use Box as a managed (target) resource of Oracle Identity Manager.
Note:
At some places in this guide, the term target system has been used to refer to the Box target system.In the account management (target resource) mode of the connector, data about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. This data is used to provision (allocate) new resources or update resources already assigned to OIM Users. You can use Oracle Identity Manager to provision or update Box resources (that is, accounts) assigned to OIM Users. These provisioning operations performed on Oracle Identity Manager translate into the creation or updates to target system accounts. In addition, the connector aunthenticates to the Box target system using the access token that is provided as a manual input from the user.
1.2 Certified Components for the Box Connector
These are the software components and their versions required for installing and using the Box connector.
Table 1-1 lists the certified components for this connector.
Table 1-1 Certified Components
| Component | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
|
Target System |
Box |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 or later |
1.3 Certified Languages for the Box Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English (US)
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
1.4 Connector Architecture of the Box Connector
The Box connector is implemented by using the Identity Connector Framework (ICF).
The connector enables you to manage accounts on the target system. Managing accounts consists of the following processes:
-
Provisioning
Provisioning involves creating or updating users on the target system through Oracle Identity Manager. When you allocate (or provision) a Box resource to an OIM User, the operation results in the creation of an account on Box for that user. In the Oracle Identity Manager context, the term provisioning also covers updates made to the target system account through Oracle Identity Manager.
-
Target Resource Reconciliation
In target resource reconciliation, data related to newly created and modified target system accounts can be reconciled and linked with existing OIM Users and provisioned resources. A scheduled job is used for reconciliation.
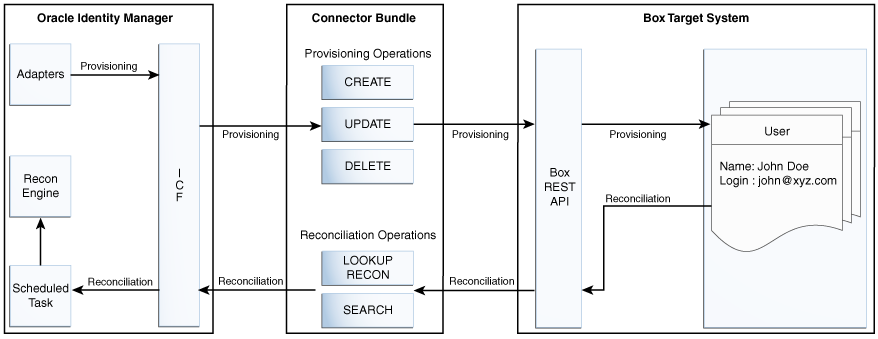
As shown in this figure, Box is configured as a target resource of Oracle Identity Manager. Through provisioning operations performed on Oracle Identity Manager, accounts are created and updated on the target system for OIM Users. Through reconciliation, account data that is created and updated directly on the target system is fetched into Oracle Identity Manager and stored against the corresponding OIM Users. Identity Connector Framework (ICF) is a component that is required in order to use Identity Connectors. ICF is distributed together with Oracle Identity Manager.
You do not need to configure or modify ICF. During provisioning, the Adapters invoke ICF operation, ICF inturn invokes create operation on Box Identity Connector Bundle and then the bundle calls Box REST API for Provisioning operations. The Box REST API on the target system accepts provisioning data from the bundle, carries out the required operation on the target system, and returns the response from the target system back to the bundle, which passes it to the adapters. During reconciliation, a scheduled task invokes ICF operation, ICF inturn invokes search operation on Box Identity Connector Bundle and then the bundle calls Box REST API for Reconciliation operation. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Manager.
Each record fetched from the target system is compared with Box resources that are already provisioned to OIM Users. If a match is found, then the update made to the Box record from the target system is copied to the Box resource in Oracle Identity Manager. If no match is found, then the user ID of the record is compared with the user ID of each OIM User. If a match is found, then data in the target system record is used to provision an Box resource to the OIM User.
The Box Identity Connector Bundle communicates with the Box REST API using the HTTPS protocol.
1.5 Use Cases Supported by the Box Connector
Box is a cloud computing business which provides file-sharing, collaborating, and other tools for working with files that are uploaded to its servers. Box provides dynamic, flexible content management solution which empowers users to share and access content from anywhere, while providing IT enterprise-grade security and oversight into how content moves within their organizations.
The following are some of the most common scenarios in which this connector can be used:
-
Automated Admin Token Management
Today, security is one of the biggest concerns that organizations face while accessing cloud applications. Each cloud application has its own mechanism to ensure that a security breach does not take place. Box uses automated tokens to achieve this. The administrators of the Box Connector are assigned a security token which is required to authenticate and authorize the administrators in order to perform various operations on the application. This token also gets refreshed periodically to minimize risk.
Oracle Identity Manager Connector for Box provides automated admin token management to ensure that your administrator’s security tokens are up-to-date. This functionality ensures that only authenticated and authorized administrators can perform the operations without any delay due to stale or expired tokens.
-
Box User Management
Organizations across the globe are using Box for content sharing. They want their employees to be able to access and share the most up-to-date information across different geographical locations. To achieve this, a Box administrator has to create and grant login to the concerned employees. The Box administrator must also be sure of the complete life cycle of this particular user. It must be ensured that when an employee leaves the organization, they should no longer be able to access sensitive information or content or files using their Box account. Similarly, during an employee’s tenure, it has to be ensured that they have access towards files and content which they alone are entitled to use while access must be restricted towards classified files and content.
Doing this manually for every employee is very cumbersome thus resulting in errors sometimes. Oracle Identity Manager Connector for Box provides user management functionality which enables automation of provisioning and deprovisioning of the users (employees). Whenever a new employee joins the organization, a Box account will automatically be provisioned to them along with appropriate access rights. Likewise, when they leave the organization, the same account will automatically be deactivated. This not only saves time but provides robust security as manual intervention is minimal here.
-
Exempt Box User from 2-Step Login Verification
As the need for enhanced security increases, Box provides an extra layer of security through the use of 2-step verification. This process requires the user to present the following two authenticating pieces of evidence when they log in:
-
Something they know (their Box password)
-
Something they have (an OTP code that is sent to their mobile device)
The OTP code is sent to the users mobile device as a text message (SMS). In case the user loses their mobile device or cannot access the confirmation codes sent to the mobile device for reasons unknown, the Box Connector provides an option to exempt the user from the 2-Step Login Verification requirement. An exempted user would be able to log in successfully with only the Box password. If you would like to exempt a group of users or the administrator, you can enable the option Exempt this user from 2-Step login verification for that particular user.
-
-
User Email Alias Management
In an organization, a user may have multiple email addresses. For example, in case of acquisitions or mergers, there is a need to manage multiple email addresses for different domains. In such a situation, you may want to add a new email alias for a user who changed their name but left their primary email address the same.
Email alias allows users to link multiple email addresses to a single Box account for easy management of their important content. Now, any user type can add multiple email addresses to their account and designate one as the primary address, where collaboration invites and Box notifications will be sent. With Oracle Identity Manager Connector for Box, you can manage email aliases and mark any one of them as primary for the user account.
-
Box User’s Group Membership Management
Organizations are usually broken down into departments, project teams or other sub-units and with this systematic break-down, there comes a need to grant different teams different levels of access for different content. The group functionality of BOX helps the organization to achieve this, thereby making it easy to replicate the work or resource breakdown easy in BOX. It also helps in creating new teams along new lines. Groups make this division of labor easy to replicate in Box, and also give the opportunity to create new teams along new lines.
Oracle Identity Manager Connector for Box enables an organization to manage user’s group memberships. A user can be a member of one or more groups. Oracle Identity Manager Connector for Box has the capability to enable the IT group to retain visibility into how content is managed and accessed. With monitoring and granular access control capabilities, it can be ensured that only authorized users have access.
One other benefit of collaborating using the Box User’s Group Membership Management is that, as new users are added to any specific group, they are automatically eligible to gain access to the content already shared. This means that, such new users can log in and gain access to relevant content required by them to perform their job effectively.
-
User and Group Reconciliation
If a user with an existing Box application (which has other users and groups configured) wants to manage users and group membership, they must initially migrate the pre-existing Box groups into Oracle Identity Manager. The Box Connector facilitates User Reconciliation and Group Lookup Reconciliation to bulk load these users and their group memberships to Oracle Identity Manager respectively.
1.6 Features of the Box Connector
The features of the connector include support for connector server, full reconciliation, and limited reconciliation.
1.6.1 Full Reconciliation
In full reconciliation, all records are fetched from the target system to Oracle Identity Governance.
Note:
The connector cannot support incremental reconciliation because of the target system limitation. The target system does not provide a way to filter user records based on the attribute which stores the time at which the account data is created or modified.In full reconciliation, all records are fetched from the target system to Oracle Identity Governance. See Full Reconciliation for Box Connector.
1.6.2 Limited Reconciliation
You can reconcile records from the target system based on a specified filter criterion.
To limit or filter the records that are fetched into Oracle Identity Governance during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled. See Limited Reconciliation for Box Connector.
1.6.3 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not want to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements if the bundle works faster when deployed on the same host as the native managed resource.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for information about installing and configuring connector server and running the connector server
1.6.4 Transformation and Validation of Account Data
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning.
In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation. The following sections provide more information:
1.7 Lookup Definitions Used During Connector Operations
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
1.7.1 Lookup Definition Synchronized with the Target System
Lookup field synchronization involves copying additions or changes made to specific fields in the target system to lookup definitions in Oracle Identity Manager.
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Group Name lookup field to select a group (from a list of group names) to which the user being provisioned must belong to. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
After you deploy the connector, the Lookup.Box.Groups lookup definition is used as an input source for lookup fields which are automatically created in Oracle Identity Manager.
Lookup fields are populated with values corresponding to the target system that you select for the operation. The Group Name lookup field is populated with values from the Lookup.Box.Groups lookup definition, which is automatically created on Oracle Identity Manager when you deploy the connector. When you perform lookup field synchronization, Groups on the target system are fetched to Oracle Identity Manager and populated in the Lookup.Box.Groups lookup definition. You use the Box Lookup Recon scheduled task to perform lookup field synchronization.
The Lookup.Box.Groups lookup definition holds values of all Groups available on the target system after successful reconciliation. It brings a list of all available and active Groups from Box which are then created in OIM identity console under the Organization tab.
This lookup definition is empty by default and is populated with values fetched from the target system when you run the scheduled jobs for lookup field synchronization.
After lookup field synchronization, data in each of the lookup definitions for lookup field synchronization is stored in the following format:
Code Key:
<IT_RESOURCE_KEY>~<LOOKUP_FIELD_VALUE>
-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE is the connector attribute value defined for code.
Sample value: 188~3502898
In this sample value, 188 is the numeric code assigned to the IT resource associated with the target system and 3502898 is the lookup field value in the target system.
Decode:
<IT_RESOURCE_NAME>~<LOOKUP_FIELD_VALUE>
-
IT_RESOURCE_NAME is the name of the IT resource in Oracle Identity Manager.
-
LOOKUP_FIELD_VALUE is the connector attribute value defined for code.
Sample value: BOX~BOX Sales
In this sample value, BOX is the value assigned to the IT resource associated with the target system and BOX Sales is the lookup field value in the target system.
1.7.2 Preconfigured Lookup Definitions for the Box Connector
Preconfigured lookup definitions are the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
The other lookup definitions are as follows:
1.7.2.1 Lookup.Box.Configuration
The Lookup.Box.Configuration lookup definition holds connector configuration entries that are used during target resource reconciliation and provisioning operations.
Note:
The values for these lookup definitions are preconfigured and cannot be modified.Table 1-2 lists the default entries in this lookup definition.
Table 1-2 Entries in the Lookup.Box.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Bundle Name |
org.identityconnectors.genericrest |
This entry holds the name of the connector bundle. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle. |
|
Connector Name |
org.identityconnectors.genericrest.GenericRESTConnector |
This entry holds the name of the connector class. |
|
customPayload |
"__ACCOUNT__.__GROUP__.UPDATEOP={ \"user\": { \"id\": \"$(__UID__)$\"}, \"group\": { \"id\": \"$(id)$\" } }","__ACCOUNT__.__GROUP__.CREATEOP={ \"user\": { \"id\": \"$(__UID__)$\"}, \"group\": { \"id\": \"$(id)$\" } }" |
This entry holds the payloads for all operations that are not in the standard format. |
|
httpHeaderAccept |
application/json |
This holds the accept-type expected from the target system in the header. |
|
httpHeaderContentType |
application/json |
This holds the content-type expected by the target system in the header. |
|
jsonResourcesTag |
"__ACCOUNT__=entries","__GROUP__=entries","__ACCOUNT__.__GROUP__=entries","__ACCOUNT__.email=entries", "__ACCOUNT__.__MEMBERSHIP__.__GROUP__=entries","__ACCOUNT__.__MEMBERSHIP__.email=entries" nameAttributes "__ACCOUNT__.login","__GROUP__.name" |
This json tag value is used during reconciliation for parsing multiple entries in a single response payload (ex: Resources). |
|
nameAttributes |
"__ACCOUNT__.login","__GROUP__.name" |
This entry holds the name attribute for all the objects that are handled by this connector. For example, for the __ACCOUNT__ object class that it used for User accounts, the name attribute is login. |
|
opTypes |
"__ACCOUNT__.CREATEOP=POST","__ACCOUNT__.UPDATEOP=PUT","__ACCOUNT__.DELETEOP=DELETE", "__ACCOUNT__.__GROUP__.UPDATEOP=POST","__ACCOUNT__.__GROUP__.DELETEOP=DELETE"," __ACCOUNT__.email.UPDATEOP=POST","__ACCOUNT__.email.DELETEOP=DELETE" |
This entry specifies the HTTP operation type for each object class supported by the connector. Values are comma separated and are in the following format: Format: OBJ_CLASS.OP=HTTP_OP In this format, OBJ_CLASS is the connector object class, OP is the connector operation (for example, CreateOp, UpdateOp, SearchOp), and HTTP_OP is the HTTP operation (GET, PUT, or POST). |
|
relURIs |
"__ACCOUNT__.CREATEOP=/users","__ACCOUNT__.UPDATEOP=/users/$(__UID__)$","__ACCOUNT__.SEARCHOP=/users/$(Filter Suffix)$","__ACCOUNT__.DELETEOP=/users/$(__UID__)$","__GROUP__.SEARCHOP=/groups/$(Filter Suffix)$","__ACCOUNT__.__GROUP__.CREATEOP=/group_memberships","__ACCOUNT__.__GROUP__.UPDATEOP=/group_memberships","__ACCOUNT__.__GROUP__.SEARCHOP=/users/$(__UID__)$/memberships","__ACCOUNT__.__GROUP__.DELETEOP=/group_memberships/$(__MEMBERSHIP__.id)$","__ACCOUNT__.__MEMBERSHIP__.__GROUP__.SEARCHOP=/users/$(__UID__)$/memberships","__ACCOUNT__.email.UPDATEOP=/users/$(__UID__)$/email_aliases","__ACCOUNT__.email.SEARCHOP=/users/$(__UID__)$/email_aliases","__ACCOUNT__.email.DELETEOP=/users/$(__UID__)$/email_aliases/$(__MEMBERSHIP__.id)$","__ACCOUNT__.__MEMBERSHIP__.email.SEARCHOP=/users/$(__UID__)$/email_aliases","__ACCOUNT__.role.SEARCHOP=/users/$(__UID__)$?fields=role","__ACCOUNT__.is_sync_enabled.SEARCHOP=/users/$(__UID__)$?fields=is_sync_enabled","__ACCOUNT__.is_exempt_from_login_verification.SEARCHOP=/users/$(__UID__)$?fields=is_exempt_from_login_verification" |
This entry holds the relative URL of every object class supported by this connector and the connector operations that can be performed on these object classes. For example, the __ACCOUNT__.UPDATEOP=/users/$(__UID__)$ is the relative URL for all update provisioning operations performed on the __ACCOUNT__ object class. |
|
specialAttributeHandling |
"__ACCOUNT__.__GROUP__.CREATEOP=SINGLE","__ACCOUNT__.__GROUP__.UPDATEOP=SINGLE","__ACCOUNT__.email.CREATEOP=SINGLE", "__ACCOUNT__.email.UPDATEOP=SINGLE","__ACCOUNT__.role.SEARCHOP=SINGLE","__ACCOUNT__.is_exempt_from_login_verification.SEARCHOP=SINGLE", "__ACCOUNT__.is_sync_enabled.SEARCHOP=SINGLE" |
This entry specifies the special attributes whose values should be sent to the target system one by one ("SINGLE"). Values should be comma separated. Format: objectClass.attributeName.opeartion=SINGLE |
|
specialAttributeTargetFormat |
"__ACCOUNT__.__GROUP__=group","__ACCOUNT__.__MEMBERSHIP__.__GROUP__=group.id" |
This entry lists the format in which a special attribute is present in the target system endpoint. For example, the alias attribute will be present as aliases.alias in the target system endpoint. Values are comma separated and are presented in the following format: OBJ_CLASS.ATTR_NAME= TARGET_FORMAT |
|
statusAttributes |
__ACCOUNT__.status |
This entry lists the name of the target system attribute that holds the status of an account. For example, for the __ACCOUNT__ object class that it used for User accounts, the status attribute is accountEnabled. |
|
statusDisableValue |
inactive |
This entry holds the value of the status attribute in the target system which represents the disable value. |
|
statusEnableValue |
active |
This entry holds the value of the status attribute in the target system which represents the enable value. |
|
uidAttributes |
"__ACCOUNT__.id","__GROUP__.id" |
This entry holds the UID attribute for the object which are handled by the connectors. For example for User accounts the uid attribute is id. |
|
User Configuration Lookup |
Lookup.Box.UM.Configuration |
This entry holds the name of the lookup Lookup.Box.UM.Configuration definition that stores configuration information used during user management operations. |
|
enableEmptyString |
true |
This entry holds the configuration value. If this configuration is set to true, the connector will send an empty string instead of null to the target system when any attribute of the Box account of Oracle Identity Manager user is updated with a blank value. |
1.7.2.2 Lookup.Box.UM.Configuration
The Lookup.Box.UM.Configuration lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during user management operations in the target resource mode.
Table 1-3 lists the entries in this lookup definition.
Table 1-3 Entries in the Lookup.Box.UM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.Box.UM.ProvAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Manager and the target system. This lookup definition is used during user provisioning operations |
|
Recon Attribute Map |
Lookup.Box.UM.ReconAttrMap |
This entry holds the name of the lookup definition that stores attribute mappings between Oracle Identity Manager and the target system. This lookup definition is used during reconciliation |
1.7.2.3 Lookup.Box.UM.ProvAttrMap
The Lookup.Box.UM.ProvAttrMap lookup definitions hold mappings between process form fields and target system attributes.
This lookup definition is preconfigured and used during provisioning. Table 1-11 lists the default entries.
You can add entries in this lookup definitions if you want to map new target system attributes for provisioning. See Adding New User Attributes for Provisioning.
1.7.2.4 Lookup.Box.UM.ReconAttrMap
The Lookup. Box.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes.
This lookup definition is preconfigured and used during target resource reconciliation. Table 1-8 lists the default entries. You can add entries in this lookup definitions if you want to map new target system attributes for target resource reconciliation. See Adding New User Attributes for Reconciliation.
1.7.2.5 Lookup.Box.Timezone
The Lookup.Box.Timezone lookup definition holds information about timezones that you can assign to a target system account that you create through Oracle Identity Manager. This is a static lookup definition.
You must populate the entries of this lookup definition manually. The following is the format of the Code Key and Decode values in this lookup definition:
-
Code Key: Timezone value as expected by the target system.
-
Decode: Value which will be displayed to User on OIM form. This can be same as the decode key value or can modified by the user for better readability purposes.
Table 1-4 lists default entries in this lookup definition.
Table 1-4 Entries in the Lookup.Box.Timezone Lookup Definition
| Code Key | Decode |
|---|---|
|
America/Chicago |
America/Chicago |
|
America/Los_Angeles |
America/Los_Angeles |
|
America/New_York |
America/New_York |
|
Asia/Calcutta |
Asia/Calcutta |
|
Asia/Hong_Kong |
Asia/Hong_Kong |
|
Australia/Melbourne |
Australia/Melbourne |
|
Australia/Sydney |
Australia/Sydney |
|
Europe/London |
Europe/London |
1.7.2.6 Lookup.Box.BooleanValues
The Lookup.Box.BooleanValues lookup definition maps boolean values that are used for some of the fields in the target system with the corresponding boolean values to be displayed in the fields of the OIM User form.
Table 1-5 lists default entries in this lookup definition.
Table 1-5 Entries in the Lookup.Box.BooleanValues Lookup Definition
| Code Key | Decode |
|---|---|
|
0 |
False |
|
1 |
True |
1.7.2.7 Lookup.Box.Language
The Lookup.Box.Language lookup definition holds a list of languages that you can assign as a preferred language for a target system account that you create through Oracle Identity Manager. This is a static lookup definition.
You must populate the entries of this lookup definition manually. The following is the format of the Code Key and Decode values in this lookup definition:
-
Code Key: 2-letter ISO code for a language
-
Decode: Language name
Table 1-6 lists the default entry in this lookup definition.
Table 1-6 Entry in the Lookup.Box.Language Lookup Definition
| Code Key | Decode |
|---|---|
|
en |
English |
1.7.2.8 Lookup.Box.Role
The Lookup.Box. Role lookup definition holds information about roles that you can select for a target system user account that you create through Oracle Identity Manager. This is a static lookup definition.
These Roles can be seen as a Lookup value in the Box Form. To add new attributes that you want the connector to handle, we can add new entries to this lookup definition using the Design console. See Adding New User Attributes for Reconciliation for more information about adding a new user attribute during reconciliation. When you go to the Lookup definition, you can see the Add and the Delete buttons. These can help you to add and delete entries. See Adding New User Attributes for Provisioning for more information about adding a new user attribute during provisioning.
You must populate the entries of this lookup definition manually. The following is the format of the Code Key and Decode values in this lookup definition:
-
Code Key: Value as expected by the target system.
-
Decode: Value which will be displayed to User on OIM form. This can be same as the decode key value or can modified by the user.
Table 1-7 holds default entries for this lookup definition.
Table 1-7 Entries in the Lookup.Box.Role Lookup Definition
| Code Key | Decode |
|---|---|
|
coadmin |
Co-Admin |
|
user |
User |
1.8 Connector Objects Used During Target Resource Reconciliation
Target resource reconciliation involves fetching data about newly created or modified accounts on the target system and using this data to add or modify resources assigned to OIM Users.
The Box Resource User Reconciliation scheduled job is used to initiate a reconciliation run. This scheduled job is discussed in Reconciliation Scheduled Jobs for Box Connector.
See Also:
Managing Reconciliation in Oracle Fusion Middleware Administering Oracle Identity Manager for generic information about connector reconciliationThis section discusses the following topics :
1.8.1 User Fields for Target Resource Reconciliation
The Lookup. Box.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. This lookup definition is used for performing target resource user reconciliation runs.
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system attribute
Table 1-8 lists the default entries in this lookup definition.
Table 1-8 Entries in the Lookup. Box.UM.ReconAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
Address |
address |
|
Aliases~Alias |
|
|
Groups~Group Name[LOOKUP] |
__GROUP__~__GROUP__~id |
|
ID |
__UID__ |
|
Job Title |
job_title |
|
Language |
language |
|
Login |
__NAME__ |
|
Name |
name |
|
Phone |
phone |
|
Space Amount |
space_amount |
|
Status |
__ENABLE__ |
|
Timezone |
timezone |
|
Role |
role |
|
Enable Sync |
is_sync_enabled |
|
Exempt From Login Verification |
is_exempt_from_login_verification |
1.8.2 Reconciliation Rules for the Box Connector
Reconciliation rules for target resource reconciliation are used by the reconciliation engine to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system.
The following sections provide information about the reconciliation rules for this connector:
1.8.2.1 Reconciliation Rule for Users
Rule name: Box User Recon Rule
Rule element: User Login Equals Tokenize (Login).
-
User Login is the attribute which is present in the OIM User form.
-
Tokenize (Login) where Login is the name attribute which is unique field of the Box account.
1.8.3 Reconciliation Action Rules for the Box Connector
Reconciliation action rules specify actions that must be taken depending on whether or not matching Box resources or OIM Users are found when the reconciliation rule is applied.
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions.The following sections provide information about the action rules for this connector:
1.8.3.1 Reconciliation Action Rules
Table 1-9 lists the action rules for target resource reconciliation.
Table 1-9 Action Rules for Reconciliation for Target System
| Rule Condition | Action |
|---|---|
|
No Matches Found |
None |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
1.8.3.2 Viewing Reconciliation Action Rules Reconciliation in Design Console
After you deploy the connector, you can view the reconciliation action rules for user reconciliation by performing the following steps:
- Log in to the Oracle Identity Manager Design Console.
- Expand Resource Management and double-click Resource Objects.
- Open the Box User resource object.
- Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector.
1.9 Connector Objects Used During Provisioning
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
This section contains the following topics:
1.9.1 Provisioning Functions
These are the supported provisioning functions and the adapters that perform these functions for the Box connector.
Table 1-10 lists the supported provisioning functions and the adapters that perform these functions. The Adapter column gives the name of the adapter that is used when the function is performed.
See Also:
Types of Adapters in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about process tasks and adaptersTable 1-10 User Provisioning Functions
| Function | Adapter |
|---|---|
|
Create User |
adpBOXCREATEOBJECT |
|
Enable User |
adpBOXENABLE |
|
Disable User |
adpBOXDISABLE |
|
Update User |
adpBOXUPDATEOBJECTTASK |
|
Delete User |
adpBOXDELETEOBJECT |
|
Add Child table values |
adpBOXADDCHILDOBJECT |
|
Remove Child table values for user |
adpBOXREMOVECHILDOBJECT |
|
Update Child table values |
adpBOXUPDATECHILDDATA |
1.9.2 User Fields for Provisioning
The Lookup.Box.UM.ProvAttrMap lookup definition maps process form fields with Box fields. This lookup definition is used for performing user provisioning operations.
In this lookup definition, entries are in the following format:
Code Key: Name of the process form field.
Decode: Name of the target system attribute.
Table 1-11 lists the default entries in this lookup definition.
Table 1-11 Entries in the Lookup.Box.UM.ProvAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
Address |
address |
|
Enable Sync |
is_sync_enabled |
|
Exempt From Login Verification |
is_exempt_from_login_verification |
|
ID |
__UID__ |
|
Job Title |
job_title |
|
Language |
language |
|
Login |
__NAME__ |
|
Name |
name |
|
Phone |
phone |
|
Role |
role |
|
Space Amount |
space_amount |
|
Timezone |
timezone |
|
UD_BOX_UAL~Alias |
|
|
UD_BOX_UGP~Group Name[LOOKUP] |
__GROUP__~__GROUP__~id |
1.10 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Deploying the Box Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the Box Connector describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Extending the Functionality of the Box Connector describes procedures that you can perform if you want to extend the functionality of the connector.
-
Files and Directories on the Box Connector Installation Media lists the files and directories that comprise the connector installation media.