3.1 About the GoToMeeting Connector
This connector can be configured to run in the account management (or target resource management) mode. In this mode, the GoToMeeting Admin Center (Admin Center) is used as a managed (target) resource of the identity data for Oracle Identity Manager.
The following topics provide a high-level overview of the connector:
3.1.1 Certified Components for the GoToMeeting Connector
These are the software components and their versions required for installing and using the connector.
Table 3-1 Certified Components for the GoToMeeting Connector
| Component | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
|
Target system |
LogMeIn Admin Center |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 or Later |
3.1.2 Certified Languages for the GoToMeeting Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English (US)
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
3.1.3 Architecture of the GoToMeeting Connector
The connector uses GoToMeeting Administration APIs to synchronize user attributes between Oracle Identity Manager and GoToMeeting directory services, and is implemented using the Identity Connector Framework (ICF) component.
The connector enables the following operations:
-
Provisioning
Provisioning involves creating and updating users on the Admin Center through Oracle Identity Manager. When you allocate (or provision) a GoToMeeting resource to an Oracle Identity Manager User, the operation results in the creation of an account in the Admin Center for that user. In the Oracle Identity Manager context, the term provisioning is also used to mean updates made to the account through Oracle Identity Manager.
-
Target resource reconciliation
To perform target resource reconciliation, the GoToMeeting Reconciliation scheduled job is used. The connector then fetches the user attribute values from the Admin Center.
The connector supports OAuth 2.0 security protocol for authenticating to the target system, and uses access token and refresh token values as inputs from the user.
Figure 3-1 depicts the architecture of the GoToMeeting connector.
Figure 3-1 Architecture of the GoToMeeting Connector
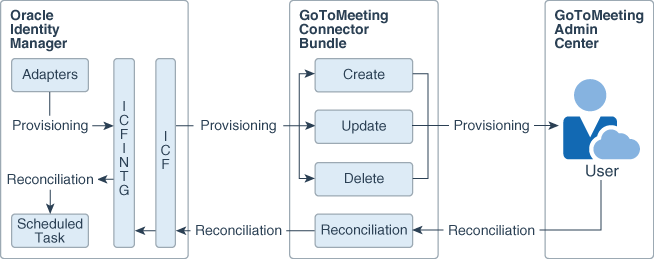
Description of "Figure 3-1 Architecture of the GoToMeeting Connector"
As shown in Figure 3-1, the Admin Center is configured as a target resource of Oracle Identity Manager. Through the provisioning operations that are performed on Oracle Identity Manager, accounts are created and updated on the Admin Center for Oracle Identity Manager Users.
Through reconciliation, account data that is created and updated directly on the Admin Center is fetched into Oracle Identity Manager and stored against the corresponding Oracle Identity Manager Users.
The ICF component provides basic reconciliation and provisioning operations that are common to all Oracle Identity Manager connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. ICF is distributed together with Oracle Identity Manager. Therefore, you do not need to configure or modify ICF.
During provisioning, the adapters invoke ICF operation, ICF invokes the Create operation on GoToMeeting Connector Bundle, and then the bundle calls the OAuth API for connecting to the Admin Center and performing user authentication. The Admin Center accepts provisioning data from the bundle using GoToMeeting Administration APIs, carries out the operation, and returns the response back to the bundle. The bundle then passes it to the adapters.
3.1.4 Features of the GoToMeeting Connector
The features of the connector include support for connector server, full reconciliation, limited reconciliation, and reconciliation of deleted account data.
This connector supports the following features:
3.1.4.1 Full Reconciliation
In full reconciliation, all records are fetched from the target system to Oracle Identity Manager. See Performing Full Reconciliation.
3.1.4.2 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
See Understanding Installation of the GoToMeeting Connector.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for more information about installing, configuring, and running the connector server
3.1.4.3 Limited Reconciliation
You can reconcile records from the target system based on a specified filter criterion. To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled.
3.1.4.4 Transformation and Validation of Account Data
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation.
The following sections provide more information:
3.1.5 Lookup Definitions Used During Connector Operations
Lookup definitions used during reconciliation and provisioning are either preconfigured or can be synchronized with the target system.
3.1.5.1 Preconfigured Lookup Definitions
Preconfigured lookup definitions are automatically created in Oracle Identity Manager after you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
The preconfigured lookup definitions are as follows:
3.1.5.1.1 Lookup.GTM.Configuration
The Lookup.GTM.Configuration lookup definition holds connector configuration entries that are used during the target resource reconciliation and provisioning operations. Table 3-2 lists the default entries in this lookup definition.
Note:
Do not modify the entries in this lookup definition.Table 3-2 Entries in the Lookup.GTM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Bundle Name |
org.identityconnectors.genericrest |
This entry holds the name of the connector bundle. |
|
Bundle Version |
1.0.1115 |
This entry holds the version of the connector bundle. |
|
Connector Name |
org.identityconnectors.genericrest.GenericRESTConnector |
This entry holds the name of the connector class. |
|
customPayload |
"__ACCOUNT__.CREATEOP={\"users\":[{\"email\":\"$(email)$\",\"firstName\":\"$(__NAME__)$\",\"lastName\":\"$(lastName)$\",\"locale\":\"$(locale)$\"}],\"groupKey\":\"$(groupKey)$\",\"licenseKeys\":[$(licenseKeys)$]}" |
This entry lists the request payload formats for all the connector operations that are not in standard JSON format. |
|
httpHeaderAccept |
application/json |
This entry holds the accept type expected from the target system in the request header. |
|
httpHeaderContentType |
application/json |
This entry holds the content type expected by the target system in the request header. |
|
jsonResourcesTag |
"__ACCOUNT__=results","__GROUP__=results","__LICENSE__=results" |
This entry holds the JSON tag value that is used during reconciliation for parsing multiple entries in a single payload. |
|
nameAttributes |
"__ACCOUNT__.firstName","__GROUP__.name","__LICENSE__.description" |
This entry holds the name attribute for all the object classes that are handled by the connector. For example, the value |
|
opTypes |
"__ACCOUNT__.licenseKeys.UPDATEOP=PUT","__ACCOUNT__.groupKey.UPDATEOP=PUT","__ACCOUNT__.CREATEOP=POST", "__ACCOUNT__.UPDATEOP=PUT","__ACCOUNT__.SEARCHOP=GET","__ACCOUNT__.DELETEOP=DELETE", "__ACCOUNT__.__LICENSE__.UPDATEOP=POST", "__ACCOUNT__.__LICENSE__.DELETEOP=DELETE" |
This entry specifies the HTTP operation type for each object class supported by this connector. Values are comma separated, and are in the following format: OBJ_CLASS.OP=HTTP_OP In this format, OBJ_CLASS is the connector object class, OP is the connector operation (for example, CreateOp, UpdateOp, SearchOp), and HTTP_OP is the HTTP operation (GET, PUT, or POST). |
|
relURIs |
"__ACCOUNT__.licenseKeys.UPDATEOP=/admin/rest/v1/accounts/$(account_key)$/licenses/$(licenseKeys)$/users/$(__UID__)$", "__ACCOUNT__.CREATEOP=/admin/rest/v1/accounts/$(account_key)$/users", "__ACCOUNT__.UPDATEOP=/admin/rest/v1/accounts/$(account_key)$/users/$(__UID__)$", "__ACCOUNT__.SEARCHOP=/admin/rest/v1/accounts/$(account_key)$/users/$(Filter Suffix)$", "__ACCOUNT__.DELETEOP=/admin/rest/v1/accounts/$(account_key)$/users/$(__UID__)$", "__LICENSE__.SEARCHOP=/admin/rest/v1/accounts/$(account_key)$/licenses", "__GROUP__.SEARCHOP=/admin/rest/v1/accounts/$(account_key)$/groups", "__ACCOUNT__.__LICENSE__.ADDATTRIBUTE=/admin/rest/v1/accounts/$(account_key)$/licenses/$(__LICENSE__.key)$/users/$(__UID__)$", "__ACCOUNT__.__LICENSE__.REMOVEATTRIBUTE=/admin/rest/v1/accounts/$(account_key)$/licenses/$(__LICENSE__.key)$/users/$(__UID__)$", "__ACCOUNT__.groupKey.UPDATEOP=/admin/rest/v1/accounts/$(account_key)$/groups/$(groupKey)$/users/$(__UID__)$" |
This entry holds the relative URL for all operations supported by the connector for each object class. For example, the |
|
simpleMultivaluedAttribute |
"__ACCOUNT__=primaryLicense" |
This entry holds the name of the attributes that can hold multiple values. For example, the |
|
specialAttributeHandlling |
"__ACCOUNT__.__LICENSE__.ADDATTRIBUTE=SINGLE","__ACCOUNT__.__LICENSE__.REMOVEATTRIBUTE=SINGLE", "__ACCOUNT__.__LICENSE__.CREATEOP=SINGLE","__ACCOUNT__.__LICENSE__.UPDATEOP=SINGLE", "__ACCOUNT__.licenseKeys.UPDATEOP=SINGLE", "__ACCOUNT__.groupKey.UPDATEOP=SINGLE" |
This entry lists the special attribute, which is an attribute in an object class that can be managed only through a separate REST API endpoint rather than the same endpoint of the base object class. Values are sent to the target system in separate calls, one at a time. In addition, values are comma separated, and are in the following format: OBJ_CLASS.ATTR_NAME.PROV_OP=SINGLE For example, the |
|
specialAttributeTargetFormat |
"__ACCOUNT__.__GROUP__=managedGroupKeys","__ACCOUNT__.__LICENSE__=licenseKeys" |
This entry lists the format in which a special attribute is present in the target system response. For example, the |
|
uidAttributes |
"__ACCOUNT__.key","__GROUP__.key","__LICENSE__.key" |
This entry holds the UID attribute for all the object classes that are handled by the connector. For example, the value |
|
User Configuration Lookup |
Lookup.GTM.UM.Configuration |
This entry holds the name of the lookup definition that stores configuration information used during user management operations. |
3.1.5.1.2 Lookup.GTM.UM.Configuration
The Lookup.GTM.UM.Configuration lookup definition holds configuration entries that are specific to the user object type. This lookup definition is used during user management operations in the target resource mode.
Table 3-3 lists the entries in this lookup definition.
Table 3-3 Entries in the Lookup.GTM.UM.Configuration Lookup Definition
| Code Key | Decode | Description |
|---|---|---|
|
Provisioning Attribute Map |
Lookup.GTM.UM.ProvAttrMap |
This entry holds the name of the lookup definition that maps process form fields and target system attributes. This lookup definition is used during user provisioning operations. |
|
Recon Attribute Map |
Lookup.GTM.UM.ReconAttrMap |
This entry holds the name of the lookup definition that maps resource object fields and target system attributes. This lookup definition is used during reconciliation. |
3.1.5.1.3 Lookup.GTM.UM.ProvAttrMap
The Lookup.GTM.UM.ProvAttrMap lookup definition holds mappings between process form fields and target system attributes. This lookup definition is preconfigured, and is used during provisioning.
You can add entries in this lookup definition if you want to map new target system attributes for provisioning. See Adding User Attributes for Provisioning.
See Table 3-10 for a list of the default entries in this lookup definition.
3.1.5.1.4 Lookup.GTM.UM.ReconAttrMap
The Lookup.GTM.UM.ReconAttrMap lookup definition holds mappings between resource object fields and target system attributes. This lookup definition is preconfigured, and is used during reconciliation.
You can add entries in this lookup definition if you want to map new target system attributes for target resource reconciliation. See Adding User Attributes for Reconciliation.
See Table 3-7 for a list of the default entries in this lookup definition.
3.1.5.1.5 Lookup.GTM.Locale
The Lookup.GTM.Locale lookup definition holds information about the supported locale codes for a target system account. This setting determines the display formats for date and time, users’ names, addresses, and commas and periods in numbers.
This is a static lookup definition. This lookup definition is empty by default, and you must manually populate the entries of this lookup definition.
-
Code Key: Standard ISO locale code for a target system account
-
Decode: Name of the corresponding locale
Table 3-4 lists the sample entries in this lookup definition.
Table 3-4 Sample Entries in the Lookup.GTM.Locale Lookup Definition
| Code | Decode |
|---|---|
|
de_DE |
Deutsch German |
|
en_GB |
International English |
|
en_US |
US English |
3.1.5.2 Lookup Definitions Synchronized with the Target System
During a provisioning operation, you use a lookup field on the process form to select a single value from a set of values. For example, you may want to select a license from the Licenses lookup field to specify the license being assigned to the user. Lookup field synchronization involves copying additions or changes made to specific fields in the target system to lookup definitions in Oracle Identity Manager.
When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are created in Oracle Identity Manager. Lookup field synchronization populates these lookup fields with values from the corresponding lookup definitions.
3.1.5.2.1 Lookup.GTM.Group
The Lookup.GTM.Group lookup definition holds values of all active groups that are available on the target system. The Group Name lookup field is populated with values from the Lookup.GTM.Group lookup definition, which is automatically created on Oracle Identity Manager after you deploy the connector.
You populate this lookup definition through lookup field synchronization performed using the GoToMeeting Group Lookup Reconciliation scheduled job.
The following is the format in which data is stored after lookup field synchronization:
-
Code Key: IT_RESOURCE_KEY~KEY
In this format:-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
KEY is GUID of the group on the target system.
-
-
Decode: IT_RESOURCE_NAME~NAME
In this format:-
IT_RESOURCE_NAME is the name assigned to the IT resource in Oracle Identity Manager.
-
NAME is the name of the group on the target system.
-
Table 3-5 lists sample entries in this lookup definition.
Table 3-5 Sample Entries in the Lookup.GTM.Group Lookup Definition
| Code Key | Decode |
|---|---|
|
87~123876986986986 |
GoToMeeting~Group1 |
|
87~123456786954321 |
GoToMeeting~Group2 |
3.1.5.2.2 Lookup.GTM.License
The Lookup.GTM.License lookup definition holds values of all account licenses that are available on the target system. The License lookup field is populated with values from the Lookup.GTM.License lookup definition, which is automatically created on Oracle Identity Manager after you deploy the connector.
You populate this lookup definition through lookup field synchronization performed using the GoToMeeting License Lookup Reconciliation scheduled job.
The following is the format in which data is stored after lookup field synchronization:
-
Code Key: IT_RESOURCE_KEY~KEY
In this format:-
IT_RESOURCE_KEY is the numeric code assigned to each IT resource in Oracle Identity Manager.
-
KEY is the license key on the target system.
-
-
Decode: IT_RESOURCE_NAME~DESCRIPTION
In this format:-
IT_RESOURCE_NAME is the name assigned to the IT resource in Oracle Identity Manager.
-
DESCRIPTION is the description of the license on the target system.
-
Table 3-6 lists sample entries in this lookup definition.
Table 3-6 Sample Entries in the Lookup.GTM.License Lookup Definition
| Code Key | Decode |
|---|---|
|
87~1234567891234567890 |
GoToMeeting~GoToMeeting Starter |
|
87~5432167891234512345 |
GoToMeeting~GoToMeeting Pro |
3.1.6 Connector Objects Used During Target Resource Reconciliation
Connector objects such as reconciliation rules, reconciliation action rules, and scheduled jobs are used for reconciling user records from the target system into Oracle Identity Manager.
The GoToMeeting Target Resource User Reconciliation scheduled job is used to initiate a reconciliation run. See Reconciliation Scheduled Jobs for the GoToMeeting Connector.
See Also:
Managing Reconciliation in Oracle Fusion Middleware Administering Oracle Identity Manager for generic information about connector reconciliationThis section contains the following topics related to connector objects:
3.1.6.1 User Fields for Target Resource Reconciliation
-
Code Key: Reconciliation field of the resource object
-
Decode: Name of the target system attribute
Table 3-7 lists the entries in this lookup definition.
Table 3-7 Entries in the Lookup.GTM.UM.ReconAttrMap Lookup Definition
| Code Key | Decode |
|---|---|
|
|
|
|
First Name |
__NAME__ |
|
Group[LOOKUP] |
groupKey |
|
Last Name |
lastName |
|
Locale |
locale |
|
PrimaryLicense[LOOKUP] |
PARENT.licenseKeys |
|
Licenses~License Name[LOOKUP] |
CHILD.licenseKeys |
|
key |
__UID__ |
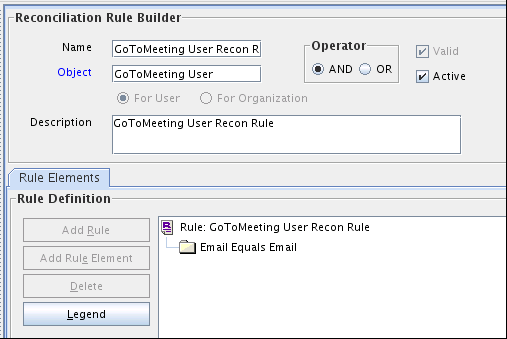
3.1.6.2 Reconciliation Rules for Target Resource Reconciliation
Reconciliation rules for target resource reconciliation are used by the reconciliation engine to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system.
The following is the process-matching rule for users:
Rule name: GoToMeeting User Recon Rule
Rule element: Email Equals Email
-
The first Email reference is the email address attribute of the OIM user.
-
The second Email reference is the email address attribute of the user in GoToMeeting.
3.1.6.3 Viewing Reconciliation Rules for Target Resource Reconciliation
You can view reconciliation rules by using Oracle Identity Manager Design Console. To view reconciliation rules for target resource reconciliation:
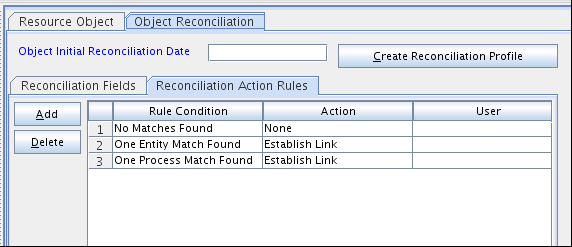
3.1.6.4 Reconciliation Action Rules for Target Resource Reconciliation
Reconciliation action rules define the actions the connector must perform based on the reconciliation rules defined for Users. Table 3-8 lists the rule condition and the corresponding action to be performed during target resource reconciliation.
Table 3-8 Action Rules for Target Resource Reconciliation
| Rule Condition | Action |
|---|---|
|
No Matches Found |
None |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
3.1.7 Connector Objects Used During Provisioning
Connector objects such as adapters are used for performing provisioning operations on the target system. These adapters perform provisioning functions on the fields defined in the lookup definition for provisioning.
This section contains the following topics:
3.1.7.1 Provisioning Functions
These are the supported provisioning functions and the adapters that perform these functions for the connector. The Adapter column in Table 3-9 gives the name of the adapter that is used when the function is performed.
See Also:
Types of Adapters in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for generic information about process tasks and adaptersTable 3-9 User Provisioning Functions
| Function | Adapter |
|---|---|
|
Create User |
adpGTMCREATEOBJECT |
|
Update User |
adpGTMUPDATEOBJECT |
|
Delete user |
adpGTMDELETEOBJECT |
|
Update child table values |
adpGTMUPDATECHILDDATA |
|
Add child table values |
adpGTMADDCHILDOBJECT |
|
Remove child table values for a user |
adpGTMREMOVECHILDOBJECT |
3.1.7.2 User Fields for Provisioning
The Lookup.GTM.UM.ProvAttrMap lookup definition holds the user fields for provisioning. This lookup definition holds mapping between process form fields and target system attributes.
Table 3-10 Entries in the Lookup.GTM.UM.ProvAttrMap Lookup Definitions
| Code Key | Decode |
|---|---|
|
|
|
|
First Name |
__NAME__ |
|
Group[LOOKUP] |
groupKey |
|
Last Name |
lastName |
|
Locale |
locale |
|
PrimaryLicense[LOOKUP] |
licenseKeys |
|
UD_GTM_LIC~License Name[LOOKUP] |
__LICENSE__~__LICENSE__~key |
|
key |
__UID__ |
3.1.8 Roadmap for Deploying and Using the GoToMeeting Connector
This is the organization of information available in this guide for deploying and using the connector.
The rest of this guide is divided into the following chapters:
-
Deploying the GoToMeeting Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Using the GoToMeeting Connector describes guidelines on using the connector, and explains procedures to configure reconciliation runs and perform provisioning operations.
-
Extending the Functionality of the GoToMeeting Connector describes procedures that you can perform if you want to extend the functionality of the connector.
-
Known Issues and Workarounds for the GoToMeeting Connector lists known issues associated with this release of the connector.
-
Files and Directories on the GoToMeeting Connector Installation Media lists the files and directories that comprise the connector installation media.