67 Work With the Security Workbench
This chapter contains these topics:
67.1 Understanding the Security Workbench
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security and System Admin
From Security Administration (G94), choose Security Officer
From Security Officer (G9401), choose Security Workbench
The Security Workbench program provides a summary view of your security setup and allows you to test certain aspects of your security. Option exits are provided to most security maintenance types. A flexible inquiry capability enables you to answer a variety of security questions. Print and export options allow you to document your security setup.
The Security Workbench program contains a number of features to support its function as a single access point for security inquiries and a starting point for accessing specific security maintenance programs.
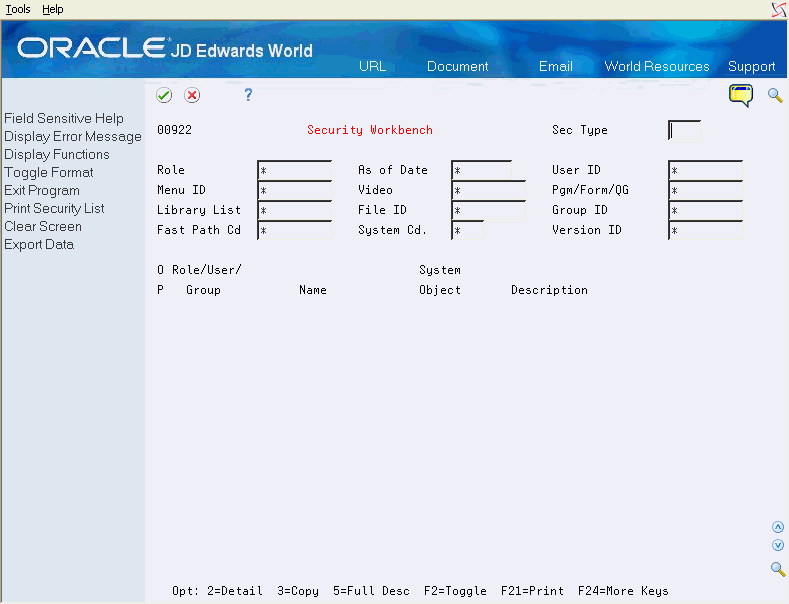
Use the Security Workbench program to inquire on all major security types, such as user profiles, menu security, action code security, and function key security. The workbench adjusts many fields based on which security type you are currently viewing:
-
Position/Filter fields in the header portion display based on the value in the Security Type field.
-
A filter field above the Details column changes format based on the security type.
-
The subfile column headings text changes based on the security type.
-
The Details column on the right of the subfile displays different information based on the security type, showing details relevant to that security type. The filter field works in conjunction with the Details column to allow additional filtering on the detail information.
The Position/Filter fields in the header are enabled for wildcard search which allow you to use the same field to position the subfile or limit the subfile display to specific groups of records. Configurable wildcard characters control the behavior of these fields.
See Also:
67.2 Using the Security Workbench
-
On Security Workbench, press F1 on the Security Type field and select security type.
| Field | Explanation |
|---|---|
| Security Type | Use this field to specify which type of security you wish to view or test. The security type controls many aspects of the video. In addition to security, this field can also be used to show report version ownership. Once you select a security type, the full security type description will appear under the program title. |
| Position/Filter | These wildcard-enabled fields control which records are displayed in the subfile (lower) portion of the video. Only the Position/Filter fields which are relevant to the security type are displayed. |
| Filter by | Use this field to filter the subfile based on the information in the Details column. This field is for filtering the subfile only; it does not work as a positioning field. |
| Effective Dates | Security role records and the records for users, groups and library lists which associate to security roles have effective dates. These are shown in the subfile fold area. Press F4 to show the fold area. |
| Business Unit Thru Number | For the business unit security records, the From Business Unit number is shown on the primary subfile line in the Details column, and the Thru Business Unit number is shown directly beneath the From number in the Details column in the fold area. Press F4 to show the fold area. Filter by is based on the From Business Unit number. |
For advanced menu security records, the value 'all menu selections' is displayed as a zero in the Details column, allowing you to filter on that value. On the Advanced Menu Security maintenance video (V008231), these values are displayed as blank.
67.2.1 Security Workbench Options
The following options are available for each subfile record:
-
Option 1 - Generic Text: Use this option to call the Generic Text window for the selected security record to add notes. This is the same generic text that you access in the maintenance program for the selected security type. If text exists for a security record, the Option field displays in reverse image for that record. This option is only active for those security types that support generic text.
-
Option 2 - Details: Use this option to select the current row and call the appropriate maintenance program to edit the data.
-
Option 3 - Copy User/Group: Use this option to call the Copy User/Group program (P00922C), which allows you to copy the user profile and security records for a user or group. This option is only active for security types which display user/group information.
-
Option 4 - Security Tester: Use this option to call the Security Tester video (V0092T). This video allows you test the selected security record to see if authorization is granted or not, and what security records are involved in the decision.
See Section 67.3, "Working With the Security Tester" for additional information. NOTE: Not all security types are supported for the Security Tester. Currently supported security types for the test option are:
-
Action code security
-
Function key security
-
-
Option 5 - Display Full Descriptions: Use this option to call the Full Descriptions video (V009221) which displays the full descriptions for the selected subfile record.
-
Option 8 - Audit Information: Use this option to display the Audit Information Window (V0045) for the selected subfile record.
-
Option 9 - Delete User/Group: Use this option to call the Delete User/Group program (V00922D), which allows you to delete the user profile and security records for a user or group. This option is only valid for those security types that display user/group information.
See Section 19.2, "Deleting a User or Group" in this manual for additional information.
67.2.2 Security Workbench Function Keys
following function keys are available on the Security Workbench screen:
-
F2 - Toggle Format: Use this function key to toggle the video display by switching the left and right parts of the subfile display and also switching the sequence of the subfile records. When you access the Security Workbench screen, the left half shows User/Group/*PUBLIC IDs for most security types; the right half shows the system resource appropriate to the security type currently displayed. The primary sequence of the subfile is always based on the information displayed in the far left column
-
F21 - Print: Use this function key to print the Security Detail Report for the current inquiry settings. NOTE: In order to see the report, you will need to do a WRKSPLF after using the F21 utility.
-
F23 - Export Data: Use this function key to export data from the screen.
67.2.3 DREAM Writer Considerations
The processing options for the DREAM Writer program control default behaviors for the Security Workbench program. Use these options to specify the DREAM Writer versions of programs called by the Security Workbench program:
-
Copy User/Group Security (P00922C)
There are DREAM Writer processing options which control certain aspects of the copy behavior. Check these to be sure the copy will do what you want.
-
Report Writer Form Security - DREAM Writer (P9425)
Use program P9425 for maintaining report form security for all four report writers. The version contains a processing option which sets the video to the correct report writer for the security type. This version should set the video to look at DREAM Writer form security records.
-
Report Writer Form Security - FASTR (P9425)
Use program P9425 for maintaining report form security for all four report writers. The version contains a processing option which sets the video to the correct report writer for the security type. This version should set the video to look at FASTR form security records.
-
Report Writer Form Security - STAR (P9425)
Use program P9425 for maintaining report form security for all four report writers. The version contains a processing option which sets the video to the correct report writer for the security type. This version should set the video to look at STAR form security records.
-
Report Writer Form Security - World Writer (P9425)
Use program P9425 for maintaining report form security for all four report writers. The version contains a processing option which sets the video to the correct report writer for the security type. This version should set the video to look at World Writer form security records.
67.2.4 Security Workbench Examples
The following examples illustrate how you can select and display security data using the Security Workbench program.
67.2.4.1 Example 1
In this example, you inquire on all user profiles whose user ID begins with the letters 'MJ', and filter the subfile to determine which of these users have both Menu Travel and Command Entry authority. This example assumes that the wildcard search character is set to '*'. Use the following steps to perform the inquiry:
-
Enter Security Type = USER (User Profiles Security Type)
-
Press the Enter key to allow the header portion of the video to format to this security type.
-
Enter the following values:
-
User = MJ* (All User IDs starting with 'MJ')
-
Group = * (All Groups)
-
Filter by = Y Y * * * (MT=Y, CE=Y, DL=Any, AM=Any, BU=Any)
-
-
Press the Enter key to view the results displayed in the subfile.
After you have selected the USER security type, the system displays only the User and Group Position/Filter fields in the header. The Details column shows security information from the user profile:
-
MT = Menu Travel Allowed Y/N
-
CE = Command Entry Allowed Y/N
-
DL = Menu Display Level
-
AM = Advanced Menu Security Activated for This User Y/N
-
BU = Advanced Business Unit Security Activated for This User Y/N
67.2.4.2 Example 2
In this example, you inquire on action code security and determine all users and groups that are locked out of Data Item Revisions. In action code security, if a user or group is denied authority to the Inquire and Add action codes, the user or group has no access to the program). This example assumes that the wildcard search character is set to '*':
-
Enter Security Type = SAC (Action Code Security Type)
-
Press the Enter key to allow the header portion of the video to format to this security type.
-
Enter the following values:
-
User = * (All User IDs)
-
Group = * (All Groups)
-
Pgm/Form/QG = P9201* (Data Item Revisions)
-
Filter by = N N * * * (I=N, A=N, C=Any, D=Any, F=Any, T=Any)
-
-
Press the Enter key to view the results displayed in the subfile.
After you have selected the SAC security type, the system displays only the User, Group and Pgm/Form/QG Position/Filter fields in the header. The Details column shows security information from the Action Code Security file for user/group and program:
-
I = Allow Inquire Y/N
-
A = Allow Add Y/N
-
C = Allow Change Y/N
-
D = Allow Delete Y/N
-
F = Allow From Y/N (Import)
-
T = Allow To Y/N (Export)
67.2.5 Exporting Security Data from the Security Workbench
You can export records displayed on the Security Workbench screen to an export file on the Integrated File System (IFS). To export records, inquire on the records first. Then use Function Key F23 to display the Interactive Export Parameters (P00SFDLP). See the help instructions for that window for more information on how to proceed with exporting records to an export file.
The Security Workbench program does not allow you to import records from a file on the IFS.
67.3 Working With the Security Tester
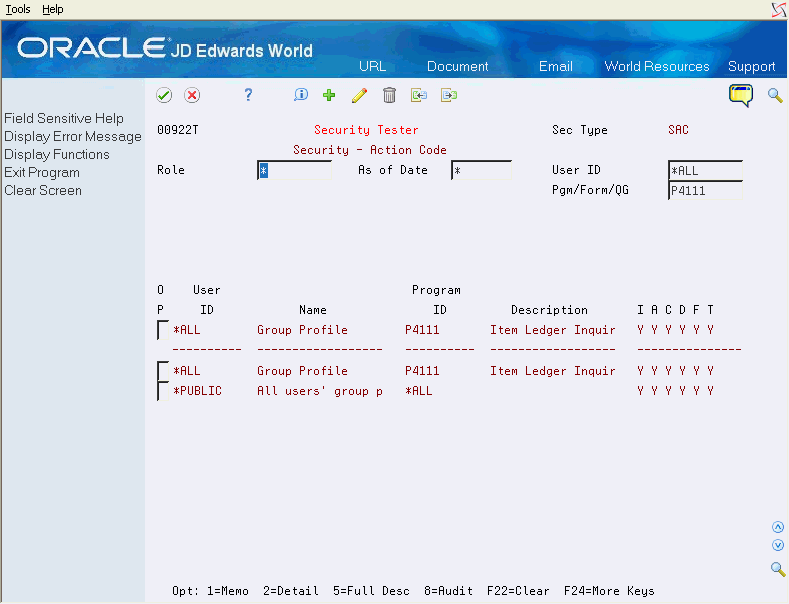
The Security Tester screen allows you to test whether specific security combinations allow or deny authority, and to see which security setup records are involved in the decision.
You access the Security Tester screen from the Security Workbench screen. The system adjusts the display of the header fields of the Security Tester screen in a manner similar to the header of the Security Workbench screen based on the security type that you display. However, the Security Tester displays one specific security scenario at a time, so the header fields are not Position/Filter fields as on the Security Workbench screen. You must enter specific values in the header fields. A special Details column at the right of the subfile displays different information based on security type, showing details relevant to the selected security type.
On the Security Workbench screen, use the Option column (Option 4) to test security for a specific security record. The Security Tester screen (V00922T) appears.
Use the Security Tester screen to inquire on the authority for specific security scenarios for the supported security types. The security types supported by the Security Tester are:
-
Action Code Security
-
Function Key Security
The Security Tester adjusts fields based on which security type you are currently viewing:
-
Selection fields in the header portion display based on the security type
-
The subfile column headings change the column heading text based on the security type
The program hides and protect selection field that are not relevant to the security type being displayed. Column headings and the Details column display information that is relevant to the security type.
| Field | Explanation |
|---|---|
| Security Type | The security type selected displays in the upper right corner of the video. You may not change the displayed security type in this video. |
| Selection Fields | These fields are used to select specific security scenarios to display. Only the selection fields which are relevant to the security type are displayed. Role, As of Date, and User ID are always displayed. |
| Subfile Records | The subfile will display the final result of the authorization test in the first subfile line. i.e., does the user, group or *PUBLIC profile have authorization to the system resource. A dashed line separates the authorization result line from the list of security records which are potentially accessed in this specific security scenario. |
67.3.1 Security Tester Options
The following options are available on the Security Tester screen:
-
Option 1 - Generic Text: Use this option to call the Generic Text window for the selected security record to add notes. This is the same generic text that you access in the maintenance program for the selected security type. If text exists for a security record, the Option field displays in reverse image for that record.
-
Option 2 - Details: Use this option to select the current row and call the appropriate maintenance program to edit the data.
-
Option 5 - Display Full Descriptions: Use this option to call the Full Descriptions video (V009221) which displays the full descriptions for the selected subfile record.
-
Option 8 - Audit Information: Use this option to display the Audit Information Window (P0045) for the selected subfile record.
67.3.2 Security Tester Examples
The following examples illustrate how you can test security setup using the Security Tester screen:
67.3.2.1 Example 1
In this example, you test which actions Joe User has authority for in the Address Book Revisions program (P01051). Joe belongs to the *APCLERK group. Use the following steps to perform the test:
-
Access the Security Tester screen from the Security Workbench by selecting Option 4, for the SAC Security-Action Code Security Type.
-
Enter the following values:
-
User ID = JOEUSER (Joe Users' profile name)
-
Pgm/Form/QG = P01051 (Address Book Revisions)
-
-
Press the Enter key to test the security authorization. The Security Tester screen displays the following information:
User ID Name Program ID Description I A C D F T JOEUSER Joe User P01051 Address Book Revis Y N N N Y N *APCLERK A/P Clerk Group P01051 Address Book Revis Y N N N Y N *PUBLIC All users' group p *ALL N N N N N N
In this example, Joe User has Inquire (I) and Export (F) authority in the Address Book Revisions program (P01051). No security record is set up for Joe User in the Action Code Security file, and Joe's authority derives from the record set up for the *APCLERK group. A *PUBLIC security record exists, but it is not checked because the group record is found first.
67.3.2.2 Example 2
In this example, you test what actions Sally Manager is authorized for in the program Address Book Revisions (P01051). Sally Manager signs on with role GLSUPR which is associated with groups *APCLERK, *ARCLERK and *GLCLERK.
-
Access the Security Tester screen from the Security Workbench by selecting Option 4, for the SAC Security-Action Code Security Type.
-
Enter the following values:
-
Role = GLSUPR (Security Role for G/l Supervisors)
-
User ID = SALLYMGR (Sally Managers' profile name)
-
Pgm/Form/QG = P01051 (Address Book Revisions)
-
-
Press the Enter key to test the security authorization. The Security Tester screen displays the following information:
User ID Name Program ID Description I A C D F T SALLYMGR Sally Manager P01051 Address Book Revis Y Y Y Y Y Y *APCLERK A/P Clerk Group P01051 Address Book Revis Y N N N Y N *ARCLERK A/R Clerk Group P01051 Address Book Revis Y N N N Y N *GLCLERK G/L Clerk Group P01051 Address Book Revis Y Y Y Y Y N *PUBLIC All users' group p *ALL N N N N N N
In this example, Sally Manager has access to all actions for the Address Book Revisions program (P01051). No specific security record is set up for Sally in the Action Code Security file, and Sally's authority derives from the records set up for the groups associated with the GLSUPR role. A *PUBLIC security record exists, but it is not checked because a group record for the role is found first.
67.3.3 Wildcard Search
Wildcard search characters can substitute for one or more characters when searching for data in the subfile. Use Configuration Master Setup (P00CFG) on menu G944 option 19 to set up wildcard characters.
For more information, see Chapter 68, "Work with Configuration Master Records" in this guide.
Using wildcards in a search tells the system to search for characters relative to their position in the field. Using wildcard characters will result in an exclusive search as opposed to a subfile reposition.
Wildcard search options include:
-
* = Default wildcard search character for zero or many characters
-
_ = Default wildcard search character for one and only one character
-
| = Default escape wildcard search character. Use the escape wildcard search character to override the wildcard search character to the literal character value.
67.3.3.1 Wildcard Search Examples
These examples illustrate wildcard search options and the records they return:
-
User/Group = A*: This entry will return all users beginning with A.
-
Using 'AN' in the User/Group field repositions the User/Group subfile in alphabetical order starting with AN.
-
Using 'AN*' in the User/Group field returns only the User/Group subfile values with A in the first position, N in the second position, then any number of characters after that.
-
User/Group = *8: This entry returns all users ending with 8.
-
User/Group = *88: This entry returns all users ending with 88.
-
User/Group = *8*: This entry returns all user records containing an 8 anywhere in the user ID.
-
User/Group = T__1: This entry returns all users beginning with T, then any two characters, then 1 (and no characters after that).
-
User/Group = I__253*: This entry returns all users beginning with I, then any two characters, then 253, then any number of characters.
-
User/Group = _N*: This entry will return all users beginning with any single character, then N, then any number of characters.
-
User/Group = |*AN: This entry repositions the subfile to all users greater than *AN.
-
User/Group = PO|_ENTRY: This entry repositions the subfile to all users beginning with or greater than PO_ENTRY.
67.3.4 Detail Column
The Details column changes based on the security type. The column headings for each security type are as follows:
-
GU Group/Users
-
None
-
-
IM Initial Menu
-
None
-
-
IP Initial Program
-
None
-
-
JDE JDE Environments
-
None
-
-
RG Role/Group
-
None
-
-
RL Role\Library List
-
None
-
-
RU Role/User
-
None
-
-
SABU Security - Advanced Bus. Unit
-
None
-
-
SAC Security - Action Code
-
None
-
-
GU Group / Users
-
I = Allow Inquire Y/N
-
A = Allow Add Y/N
-
C = Allow Change Y/N
-
D = Allow Delete Y/N
-
F = Allow From Y/N (Import)
-
T = Allow To Y/N (Export)
-
-
SAM Security - Advanced Menu
-
None
-
-
GU Group / Users
-
Sy Cd = System Code
-
Mnu Sel = Menu Selection
-
Auth = Authorized Y/N
-
-
SBA Security - Batch Approval
-
None
-
-
SBU Security - Business Unit
-
Bus. Unit From = Beginning Business Unit in Range
-
Bus. Unit Thru = Ending Business Unit in Range (shown in fold)
-
-
SFFL Security - File/Field
-
Field Name = File Field Name
-
Alw D = Allow Display Y/N
-
Alw U = Allow Update Y/N
-
-
SFK Security - Function Keys
-
Field Name = Field Name for Function Key
-
Alw Use = Allow Use Y/N
-
-
SFP Security - Fast Path
-
Allow Fast Path = Allow Fast Path Command Y/N
-
-
SGT Security - Generic Text
-
Sy Cd = System Code
-
Inq = Allow Inquiry Y/N
-
Upd = Allow Update Y/N
-
-
SM Security - Menu
-
A = Authorization Mask
-
J = Job Mask
-
K = Knowledge Mask
-
DP = Department Mask
-
F = Future Use Mask
-
-
SNS Security - Name Search
-
I = Allow Inquire Y/N
-
A = Allow Add Y/N
-
C = Allow Change Y/N
-
D = Allow Delete Y/N
-
-
SUDC Security - UDC
-
UDC Code = User Defined Code or *ALL
-
Auth = Update Authorized Y/N
-
-
SVA Sleeper Versions
-
Sy Cd = System Code
-
Object Library = Library
-
-
USER User Information
-
MT = Menu Travel Allowed Y/N
-
CE = Command Entry Allowed Y/N
-
DL = Menu Display Level
-
AM = Advanced Menu Security Activated for This User Y/N
-
BU = Advanced Bus Unit Security Activated for This User Y/N
-
-
VODW Version Owned - DW
-
Version ID = DREAM Writer Version ID
-
EX = User Exclusive Flag
-
-
VOF Version Owned - FASTR
-
Version ID = FASTR Version ID
-
EX = User Exclusive Flag
-
-
VOS Version Owned - STAR
-
Version ID = STAR Version ID
-
EX = User Exclusive Flag
-
-
VOWW Version Owned - WW
-
Version ID = World Writer Version ID
-
EX = User Exclusive Flag
-
-
VSDW Version Security - DW Report
-
Exec Auth = Allow Execute Y/N
-
A = Allow Add Y/N
-
C = Allow Change Y/N
-
D = Allow Delete Y/N
-
U = Allow Update Y/N
-
-
VSF Version Security - FASTR Reprt
-
Exec Auth = Allow Execute Y/N
-
A = Allow Add Y/N
-
C = Allow Change Y/N
-
D = Allow Delete Y/N
-
U = Allow Update Y/N
-
-
VSS Version Security - STAR Report
-
Exec Auth = Allow Execute Y/N
-
A = Allow Add Y/N
-
C = Allow Change Y/N
-
D = Allow Delete Y/N
-
U = Allow Update Y/N
-
-
VSWW Version Security - WW Report
-
Exec Auth = Allow Execute Y/N
-
A = Allow Add Y/N
-
C = Allow Change Y/N
-
D = Allow Delete Y/N
-
U = Allow Update Y/N
-
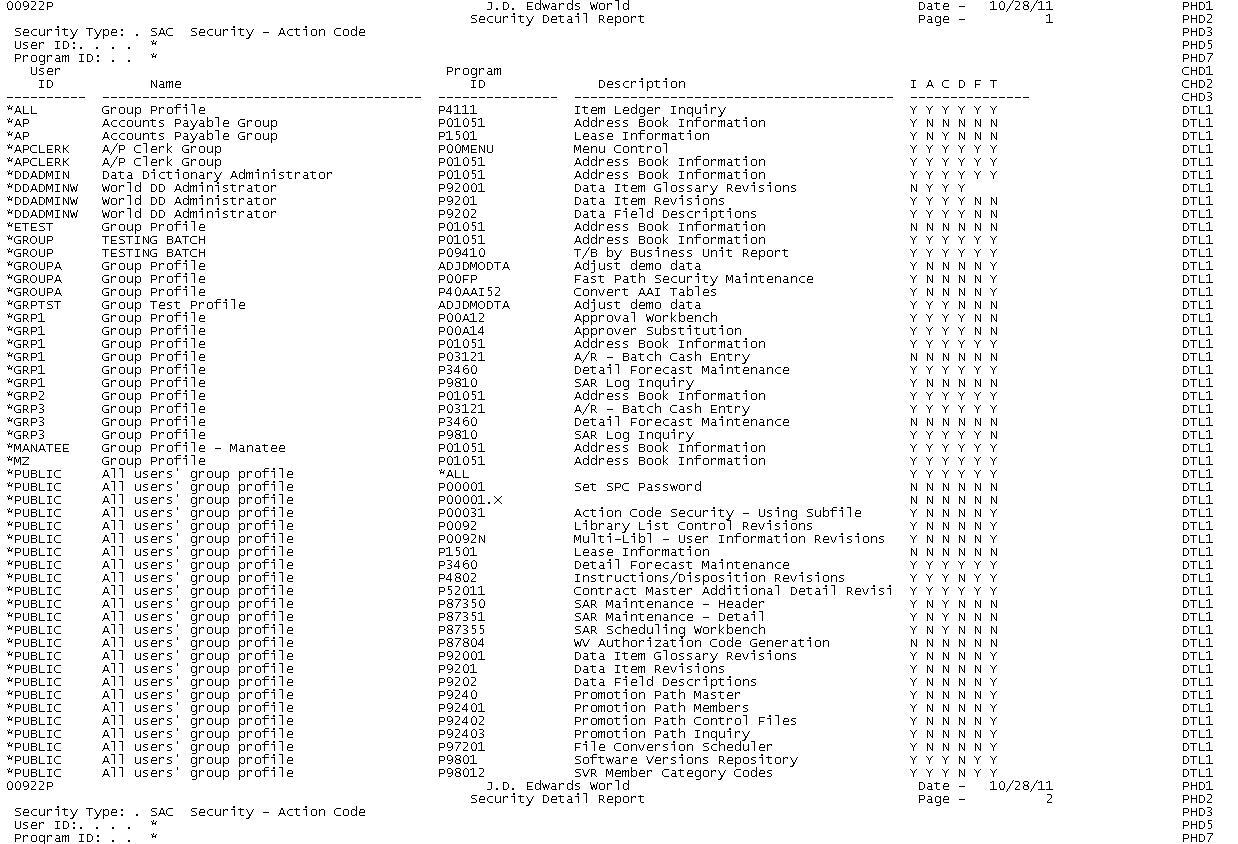
67.4 Understanding the Security Detail Report
The Security Detail Report program generates a printed report of your security setup. The Security Detail report is based on the Security Workbench program (P00922). The processing options for the report provide the same flexible inquiry capability that the Security Workbench program provides.
The Security Workbench program contains a number of features. Like the Security Workbench program, the Security Detail report has many features to support its function as a single access point for generating security setup lists. For example, depending on the security type for which you creating the report, the header portion of the report adjusts the display for the selected security type. A special Details column on the right side of the report displays a variety of information including details that are relevant to the selected security type.
Use the Security Detail Report program to run a report for all major security types, such as user profiles, menu security, action code security, abd function key security. The report adjusts the display of fields based on which security type you are currently viewing.
You can generate this report directly from the Security Workbench screen using the Print function key (F21). If you run the report from the Print function key, the report displays the current subfile from the Security Workbench screen. For greater flexibility in print options, run the report from DREAM Writer. For example, you can generate the report for all security types at once.
Note:
In order to see the report, you will need to do a WRKSPLF after using the F21 utility.67.4.1 DREAM Writer Considerations
Use the processing options for the DREAM Writer program to set selection criteria for the report.
-
Security Type: Use this field to specify which type of security you wish to view or test. The security type controls many aspects of the video. In addition to security, this field can also be used to show report version ownership and user exclusive flags.
-
Sequence: Use this field to specify how to print the detail portion of the report. Select '1' to list the User/Role/Group object first. Select '2' to list the system object first on the report.
-
Security Role: Use this field to specify the security role value to be used for selecting data for the report.Wildcard values are accepted.
-
As Of Date: this field to specify the As Of Date to be usedfor selecting data for the report.
-
User ID: Use this field to specify the user ID value to be used for selecting data for the report. Wildcard values are accepted.
-
Menu ID: Use this field to specify the menu ID value to be used for selecting data for the report. Wildcard values are accepted.
-
Video ID: Use this field to specify the video ID value to be used for selecting data for the report.
-
Program/Form/Query Group: Use this field to specify the program ID, form ID or query group value to be used for selecting data for the report.
-
Library List: Use this field to specify the library list value to be used for selecting data for the report. Wildcard values are accepted.
-
File ID: Use this field to specify the file ID value to be usedforn selecting data for the report. Wildcard values are accepted.
-
Group ID: Use this field to specify the group ID value to be used for selecting data for the report. Wildcard values are accepted.
-
Fast Path Code: Use this field to specify the fast path code value to be used for selecting data for the report. Wildcard values are accepted.
-
System Code: Use this field to specify the system code value to be used for selecting data for the report. Wildcard values are accepted.
-
Version ID: Use this field to specify the version ID value to be used for selecting data for the report. Wildcard values are accepted.
67.4.2 Exporting Security Data from the Security Detail Report
You can export this report to an export file on the Integrated File System (IFS). To export this report, access the Additional Parameters screen in your DREAM Writer Version and press F6 to display the Spooled File Export Parms (P00SPDLP). See the help instructions for that window for more information on how to proceed with exporting the report.
When Export is enabled, the system displays literals that guide the export on the right-hand side of the report. If you want to generate a printed version of the report without these literals, run a DREAM Writer Version with the Export feature disabled.
You are not required to have Printer Overrides set for this report. However, if do you have Printer Overrides for the DREAM Writer version that you use for export, you must set the the Maximum Form Width value to 138.