| Skip Navigation Links | |
| Exit Print View | |
|
Managing Serial Networks Using UUCP and PPP in Oracle Solaris 11.1 Oracle Solaris 11.1 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
Managing Serial Networks Using UUCP and PPP in Oracle Solaris 11.1 Oracle Solaris 11.1 Information Library |
2. Planning for the PPP Link (Tasks)
Overall PPP Planning (Task Map)
Before You Set Up the Dial-out Machine
Before You Set Up the Dial-in Server
Example of a Configuration for Dial-up PPP
Where to Go for More Information About Dial-up PPP
Before You Set Up the Leased-Line Link
Hardware That Is Needed for a Leased-Line Link
Information to Be Gathered for the Leased-Line Link
Example of a Configuration for a Leased-Line Link
Where to Go for More Information About Leased Lines
Planning for Authentication on a Link
Before You Set Up PPP Authentication
Examples of PPP Authentication Configurations
Example of a Configuration Using PAP Authentication
Planning for DSL Support Over a PPPoE Tunnel
Before You Set Up a PPPoE Tunnel
Before Configuring a PPPoE Client
Before Configuring a PPPoE Server
Example of a Configuration for a PPPoE Tunnel
Example of a PPPoE Client Configuration
Example of a PPPoE Server Configuration
Where to Get More Information About PPPoE
3. Setting Up a Dial-up PPP Link (Tasks)
4. Setting Up a Leased-Line PPP Link (Tasks)
5. Setting Up PPP Authentication (Tasks)
6. Setting Up a PPPoE Tunnel (Tasks)
7. Fixing Common PPP Problems (Tasks)
8. Solaris PPP 4.0 (Reference)
9. Migrating From Asynchronous Solaris PPP to Solaris PPP 4.0 (Tasks)
This section contains planning information for providing authentication on the PPP link. Chapter 5, Setting Up PPP Authentication (Tasks) contains tasks for implementing PPP authentication at your site.
PPP offers two types of authentication, PAP, which is described in detail in Password Authentication Protocol (PAP) and CHAP, which is described in Challenge-Handshake Authentication Protocol (CHAP).
Before you set up authentication on a link, you must choose which authentication protocol best meets your site's security policy. Then, you set up the secrets file and PPP configuration files for the dial-in machines, or callers' dial-out machines, or both types of machines. For information about choosing the appropriate authentication protocol for your site, see Why Use PPP Authentication?.
This section includes the following information:
Planning information for both PAP and CHAP authentication
Explanations of the sample authentication scenarios that are shown in Figure 2-3 and Figure 2-4
For tasks about setting up authentication, see Chapter 5, Setting Up PPP Authentication (Tasks).
Setting up authentication at your site should be an integral part of your overall PPP strategy. Before implementing authentication, you should assemble the hardware, configure the software, and test the link.
Table 2-5 Prerequisites Before Configuring Authentication
|
This section contains examples of authentication scenarios to be used in the procedures in Chapter 5, Setting Up PPP Authentication (Tasks).
The tasks in Configuring PAP Authentication show how to set up PAP authentication over the PPP link. The procedures use as an example a PAP scenario that was created for the fictitious “Big Company” in Example of a Configuration for Dial-up PPP.
Big Company wants to enable its users to work from home. The system administrators want a secure solution for the serial lines to the dial-in server. UNIX-style login that uses the NIS password databases has served Big Company's network well in the past. The system administrators want a UNIX-like authentication scheme for calls that come in to the network over the PPP link. So, the administrators implement the following scenario that uses PAP authentication.
Figure 2-3 Example of a PAP Authentication Scenario (Working From Home)
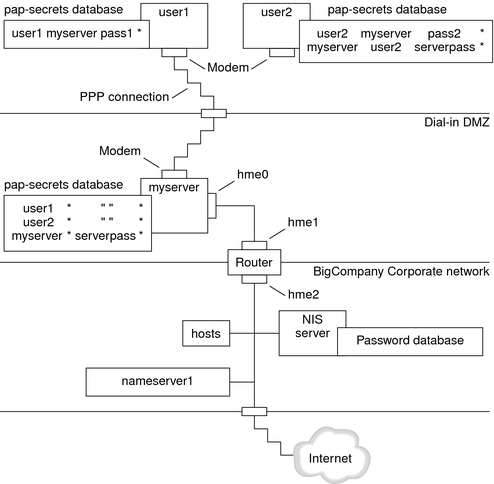
The system administrators create a dedicated dial-in DMZ that is separated from the rest of the corporate network by a router. The term DMZ comes from the military term “demilitarized zone.” The DMZ is an isolated network that is set up for security purposes. The DMZ typically contains resources that a company offers to the public, such as web servers, anonymous FTP servers, databases, and modem servers. Network designers often place the DMZ between a firewall and a company's Internet connection.
The only occupants of the DMZ that is pictured in Figure 2-3 are the dial-in server myserver and the router. The dial-in server requires callers to provide PAP credentials, including user names and passwords, when setting up the link. Furthermore, the dial-in server uses the login option of PAP. Therefore, the callers' PAP user names and passwords must correspond exactly to their UNIX user names and passwords in the dial-in server's password database.
After the PPP link is established, the caller's packets are forwarded to the router. The router forwards the transmission to its destination on the corporate network or on the Internet.
The tasks in Configuring CHAP Authentication show how to set up CHAP authentication. The procedures use as an example a CHAP scenario to be created for the fictitious LocalCorp that was introduced in Example of a Configuration for a Leased-Line Link.
LocalCorp provides connectivity to the Internet over a leased line to an ISP. The Technical Support department within LocalCorp generates heavy network traffic. Therefore, Technical Support requires its own, isolated private network. The department's field technicians travel extensively and need to access the Technical Support network from remote locations for problem-solving information. To protect sensitive information in the private network's database, remote callers must be authenticated in order to be granted permission to log in.
Therefore, the system administrators implement the following CHAP authentication scenario for a dial-up PPP configuration.
Figure 2-4 Example of a CHAP Authentication Scenario (Calling a Private Network)
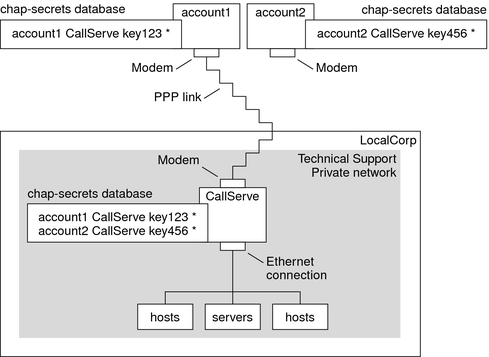
The only link from the Technical Support network to the outside world is the serial line to the dial-in server's end of the link. The system administrators configure the laptop computer of each field service representative for PPP with CHAP security, including a CHAP secret. The chap-secrets database on the dial-in server contains the CHAP credentials for all machines that are allowed to call in to the Technical Support network.
Choose from the following:
See Authenticating Callers on a Link and the pppd(1M) man page.