8 Integrating Access Manager and Oracle Adaptive Access Manager
Integrating Oracle Access Management Access Manager (Access Manager) and Oracle Adaptive Access Manager (OAAM) enables fine control over the authentication process and provides full capabilities of pre- and post-authentication checking against Oracle Adaptive Access Manager policies.
This chapter explains how to integrate Oracle Adaptive Access Manager with Oracle Access Management Access Manager (Access Manager) to secure resources via risk-based authentication.
This chapter contains these sections:
-
About Access Manager and Oracle Adaptive Access Manager Integration
-
Other Access Manager and OAAM Integration Configuration Tasks
Note:
Integration with Oracle Identity Manager provides additional features related to password collection. See Chapter 9, "Integrating Access Manager, OAAM, and OIM".
8.1 About Access Manager and Oracle Adaptive Access Manager Integration
Oracle Access Management Access Manager (Access Manager) provides the core functionality of Web Single Sign On (SSO), authentication, authorization, centralized policy administration and agent management, real-time session management and auditing.
Oracle Adaptive Access Manager 11g safeguards vital online business applications with strong yet easily deployed risk-based authentication, anti-phishing, and anti-malware capabilities.
This integration scenario enables you to control access to resources with Access Manager and provide strong multi-factor authentication and advanced real time fraud prevention with Oracle Adaptive Access Manager. Advanced login security includes the virtual authentication devices, device fingerprinting, real-time risk analysis, and risk-based challenge.
You can integrate Access Manager and Oracle Adaptive Access Manager in one of two ways:
-
OAAM Basic integration with Access Manager
-
OAAM Advanced integration with Access Manager
OAAM Basic integration with Access Manager, which is a native integration, requires the OAM Server and OAAM Admin Server in the Identity Management Middleware WebLogic Server Domain and a functional OAAM database. The OAAM Admin Server is used by Access Manager Administrators to import and export policies, create new policies, view sessions, and configure Oracle Adaptive Access Manager functionality. When policies are imported, exported, or configured, the changes are saved to the OAAM database.
The Oracle Adaptive Access Manager libraries are bundled with the OAM server. Access Manager is integrated with Oracle Adaptive Access Manager through the extension libraries and uses them directly. The rules engine and the runtime functionality of Oracle Adaptive Access Manager are provided using these libraries. When a user enters the registration flow, Access Manager shows the user the virtual authentication devices and runs the pre-authentication policies by using the OAAM libraries to make API calls. The OAAM libraries internally make JDBC calls to save the data related to the user to the OAAM database. The OAAM Server is not needed in this deployment since the Oracle Adaptive Access Manager runtime functionalities are available through the libraries. Knowledge-based Authentication (KBA) is the only challenge mechanism available in this integration.
For more information about the scenarios that are supported by each deployment, and the flow that achieves each scenario see, Section 1.5, "Common Integration Scenarios".
Table 8-1 summarizes the Access Manager and Oracle Adaptive Access Manager integrations types.
Table 8-1 Types of Access Manager-Oracle Adaptive Access Manager Integration
| Details | Basic | Advanced | Advanced Using TAP |
|---|---|---|---|
|
Available |
11.1.1.3.0 and above |
11.1.1.3.0 and OAAM prior to 11.1.1.5 Refer to the Oracle Fusion Middleware Integration Guide for Oracle Access Manager 11g Release 1 (11.1.1) for this version of OAAM Advanced integration with Access Manager. |
11.1.1.5.0 and above Access Manager and OAAM integration using TAP is supported OAAM Advanced integration with Access Manager. |
|
Features |
Authentication schemes, device fingerprinting, risk analysis, and the Knowledge-based Authentication (KBA) challenge mechanism KBA is the only challenge mechanism available in this integration. Libraries and configuration interface for different flows (challenge, registration, and so on). Many of the login security use cases available from OAAM |
Authentication schemes, device fingerprinting, risk analysis, KBA challenge mechanisms Advanced features and extensibility such as OTP Anywhere, challenge processor framework, shared library framework, and secure self-service password management flows. OAAM can also be integrated with third party single sign-on products via systems integrators if required. |
Authentication schemes, device fingerprinting, risk analysis, KBA challenge mechanisms, and additional advanced security access features, such as step up authentication Advanced features and extensibility such as OTP Anywhere, challenge processor framework, shared library framework, and secure self-service password management flows. OAAM can also be integrated with third party single sign-on products via systems integrators if required. |
|
OAAM Server |
Embedded OAAM Server into Access Manager; therefore smaller footprint The Oracle Adaptive Access Manager extension libraries are bundled with the embedded OAM Server and used directly. A separate OAAM Server is not needed in this deployment since the Oracle Adaptive Access Manager runtime functionalities are available through the libraries. Libraries provide rules engine and the runtime functionality of Oracle Adaptive Access Manager. When a user enters the registration flow, Access Manager shows the user the virtual authentication devices and runs the pre-authentication policies by using the OAAM libraries to make API calls. The OAAM libraries internally make JDBC calls to save the data related to the user to the OAAM database. |
Complete integration with OAAM is required Requires a separate managed server for OAAM Server |
Complete integration with OAAM is required Requires a separate managed server for OAAM Server |
|
OAAM Admin Server |
Required The OAAM Admin Server is used by Access Manager Administrators to import and export policies, create new policies, view sessions, and configure Oracle Adaptive Access Manager functionality. |
Required |
Required |
|
OAAM Database |
Required |
Required |
Required |
|
Supported Agents |
10g WebGate and Single Sign-On (OSSO) Agent |
10g WebGate |
10g and 11g WebGates |
|
Authentication Scheme |
OAAMBasic Challenge Parameters:
Specifications:
For information about the scheme, see "Managing Authentication Schemes" in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management. |
OAAMAdvanced Specifications:
For information about the scheme, see "Managing Authentication Schemes" in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management. |
TAPScheme Challenge Parameters:
Specifications:
For information about the scheme, see "Managing Authentication Schemes" in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management. |
|
Where information is located |
Refer to the Oracle Fusion Middleware Integration Guide for Oracle Access Manager 11g Release 1 (11.1.1) |
For information on authentication flows, see "Authentication Flow" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager.
8.2 Definitions, Acronyms, and Abbreviations
This section provides key definitions, acronyms, and abbreviations that are related to this integration.
Table 8-2 Advanced Integration Terms
| Term | Definition |
|---|---|
|
Action |
Oracle Adaptive Access Manager provides functionality to calculate the risk of an access request, an event or a transaction, and determine proper outcomes to prevent fraud and misuse. The outcome can be an action, which is an event activated when a rule is triggered. For example: block access, challenge question, ask for PIN or password, and so on. For information, see "Managing Policies, Rules, and Conditions" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
Alert |
Alerts are messages that indicate the occurrence of an event. An event can be that a rule was triggered, a trigger combination was met or an override was used. Alert groups are used as results within rules so that when a rule is triggered all of the alerts within the groups are created. For information, see "Managing Policies, Rules, and Conditions" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
Authentication |
The process of verifying a person's, device's, application's identity. Authentication deals with the question "Who is trying to access my services?" |
|
Authentication Level |
Access Manager supports various authentication levels to which resources can be configured so as to provide discrete levels of security required to access various resources. Discrete authentication levels distinguish highly protected resources from other resources. The TAP token sent by Access Manager provides parameters related to the authentication level. The trust level of the authentication scheme. This reflects the challenge method and degree of trust used to protect transport of credentials from the user. The trust level is expressed as an integer value between 0 (no trust) and 99 (highest level of trust). Note: After a user is authenticated for a resource at a specified level, the user is automatically authenticated for other resources in the same application domain or in different application domains, if the resources have the same or a lower trust level as the original resource. Current Authentication level is the current authentication level of the user. Target Authentication level is the authentication level required to access the protected resource. |
|
Authorization |
Authorization regards the question "Who can access what resources offered by which components?" |
|
Authentication Scheme |
Access to a resource or group of resources can be governed by a single authentication process known as an authentication scheme. An authentication scheme is a named component that defines the challenge mechanism required to authenticate a user. Each authentication scheme must also included a defined authentication module. When you register a partner (either using the Oracle Access Management Console or the remote registration tool), the application domain that is created is seeded with a policy that uses the authentication scheme that is set as the default scheme. You can choose any of the existing authentication schemes as the default for use during policy creation. |
|
Authentipad Checkpoint |
The Authentipad checkpoint determines the type of device to use based on the purpose of the device. |
|
Blocked |
If a user is "Blocked," it is because a policy has found certain conditions to be "true" and is set up to respond to these conditions with a "Block" action. If those conditions change, the user may no longer be "Blocked." The "Blocked" status is not necessarily permanent and therefore may or may not require an administrator action to resolve. For example, if the user was blocked because he was logging in from a blocked country, but he is no longer in that country, he may no longer be "Blocked." |
|
Challenge Parameters |
Challenge parameters are short text strings consumed and interpreted by WebGates and Credential Collector modules to operate in the manner indicated by those values. The syntax for specifying any challenge parameter is: <parameter>=<value> This syntax is not specific to any Webgate release (10g versus 11g). Authentication schemes are independent of Webgate release. |
|
Challenge Questions |
Challenge Questions are a finite list of questions used for secondary authentication. During registration, users are presented with several question menus. For example, he may be presented with three question menus. A user must select one question from each menu and enter answers for them during registration. Only one question from each question menu can be registered. These questions become the user's "registered questions." When rules in OAAM Admin trigger challenge questions, OAAM Server displays the challenge questions and accepts the answers in a secure way for users. The questions can be presented in the QuestionPad, TextPad, and other pads, where the challenge question is embedded into the image of the authenticator, or simple HTML. |
|
Checkpoint |
A checkpoint is a specified point in a session when Oracle Adaptive Access Manager collects and evaluates security data using the rules engine. Examples of checkpoints are:
For information, see "Managing Policies, Rules, and Conditions" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
Delegated Authentication Protocol |
The Delegated Authentication Protocol (DAP) challenge mechanism indicates that Access Manager does an assertion of the token that it receives, which differs from the standard challenge "FORM" mechanism with the external option. |
|
Device |
A computer, PDA, cell phone, kiosk, and other web-enabled device used by a user |
|
Device fingerprinting |
Device fingerprinting collects information about the device such as browser type, browser headers, operating system type, locale, and so on. Fingerprint data represents the data collected for a device during the login process that is required to identify the device whenever it is used to log in. The fingerprinting process produces a fingerprint that is unique to the user and designed to protect against the "replay attacks" and the "cookie based registration bypass" process. The fingerprint details help in identifying a device, check whether it is secure, and determine the risk level for the authentication or transaction. A customer typically uses these devices to log in: PC, notebook, mobile phone, smart phone, or other web-enabled machines. |
|
Knowledge Based Authentication (KBA) |
Knowledge-based authentication (KBA) is a secondary authentication method that provides an infrastructure based on registered challenge questions. Enables end-users to select questions and provide answers which are used to challenge them later on. Security administration include:
For information, see "Managing Knowledge-Based Authentication" in the Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
KeyPad |
Virtual keyboard for entry of passwords, credit card number, and so on. The KeyPad protects against Trojan or keylogging. |
|
LDAPScheme |
Authentication scheme used to protect Access Manager-related resources (URLs) for most directory types based on a form challenge method. |
|
Multi-Level Authentication |
Every authentication scheme requires an authentication level. The lower this number, the less stringent the scheme. A higher level number indicates a more secure authentication mechanism. SSO capability enables users to access more than one protected resource or application with a single sign in. After a successful user authentication at a specific level, the user can access one or more resources protected by one or more application domains. However, the authentication schemes used by the application domains must be at the same level (or lower). When a user accesses a resource protected with an authentication level that is greater than the level of his current SSO token, he is re-authenticated. In the Step Up Authentication case, the user maintains his current level of access even if failing the challenge presented for the higher level. This is "additional authentication". For information, see "Managing Authentication and Shared Policy Components" in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management. |
|
Oracle Access Protocol (OAP) |
Oracle Access Protocol (OAP) enables communication between Access System components (for example, OAM Server, WebGate) during user authentication and authorization. This protocol was formerly known as NetPoint Access Protocol (NAP) or COREid Access Protocol. |
|
One-time Password (OTP) |
One-time Password is a risk-based challenge solution consisting of a server generated one time password delivered to an end user via a configured out of band channel. Supported OTP delivery channels include short message service (SMS), eMail, and instant messaging. OTP can be used to compliment KBA challenge or instead of KBA. As well both OTP and KBA can be used alongside practically any other authentication type required in a deployment. Oracle Adaptive Access Manager also provides a challenge processor framework. This framework can be used to implement custom risk-based challenge solutions combining third party authentication products or services with OAAM real-time risk evaluations. For information, see "Setting Up OTP Anywhere" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
Access Manager-OAAM TAP Integration |
In Access Manager-OAAM TAP Integration, OAAM Server acts as a trusted partner application. The OAAM Server uses the Trusted Authentication Protocol (TAP) to communicate the authenticated user name to OAM Server after it performs strong authentication, risk and fraud analysis and OAM Server will own the responsibility of redirecting to the protected resource. |
|
OAAM Admin |
Administration Web application for all environment and Adaptive Risk Manager and Adaptive Strong Authenticator features. |
|
OAMAdminConsoleScheme |
Authentication scheme for Oracle Access Management Console. |
|
OAAMAdvanced |
Authentication scheme that protects resources with an external context type. This authentication scheme is used when complete integration with OAAM is required. A Webgate must front end the partner. |
|
OAAMBasic |
Authentication scheme that protects resources with a default context type. This scheme should be used when OAAM Basic integration with Access Manager is required. Here, advanced features like OTP are not supported. |
|
OAAM Server |
Adaptive Risk Manager and Adaptive Strong Authentication features, Web services, LDAP integration and user Web application used in all deployment types except native integration |
|
Policies |
Policies contain security rules and configurations used to evaluate the level of risk at each checkpoint. For information, see "Managing Policies, Rules, and Conditions" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
Post-authentication rules |
Post-authentication - Rules are run after a user is successfully authenticated. For information, see "Managing Policies, Rules, and Conditions" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
Pre-authentication rules |
Pre-authentication - Rules are run before a user completes the authentication process. For information, see "Managing Policies, Rules, and Conditions" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager. |
|
Profile |
The customer's registration information including security phrase, image, challenge questions, challenge (question and OTP) counters, and OTP. |
|
Protection level |
There are three protection levels in which to choose from:
|
|
Registration |
Registration is the enrollment process, the opening of a new account, or other event where information is obtained from the user. During the Registration process, the user is asked to register for questions, image, phrase and OTP (email, phone, and so on) if the deployment supports OTP. Once successfully registered, OTP can be used as a secondary authentication to challenge the user. |
|
Risk score |
OAAM risk scoring is a product of numerous fraud detection inputs such as a valid user, device, location, and so on. These inputs are weighted and analyzed within the OAAM fraud analytics engine. The policy generates a risk score based on dozens of attributes and factors. Depending on how the rules in a policy are configured, the system can yield an elevated risk score for more risky situations and lower scores for lower-risk situations. The degree of elevation can be adjusted with the weight assigned to the particular risk. The risk score is then used as an input in the rules engine. The rules engine evaluates the fraud risk and makes a decision on the action to take. |
|
Fraud rules are used to evaluate the level of risk at each checkpoint. For information on policies and rules, see "OAAM Security and Autolearning Policies" in the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager. |
|
|
Step Up Authentication |
Step Up Authentication occurs when a user is attempting to access a resource more sensitive than ones he had already accessed in this session. To gain access to the more sensitive resource, a higher level of assurance is required. Access Manager resources are graded by authentication level, which defines the relative sensitivity of a resource. For example, if a user accesses a corporate portal home page that is defined as authentication level 3, a basic password authentication is required. The time card application that links off the portal home is more sensitive than the portal home page, so the application is defined as authentication level 4, which requires basic password and risk-based authentication provided by OAAM. So, if a user logs in to the portal with a valid user name and password, and then clicks the time card link, his device is fingerprinted and risk analysis determines if additional authentication, such as a challenge question, is required to allow him access. |
|
Strong Authentication |
An authentication factor is a piece of information and process used to authenticate or verify the identity of a person or other entity requesting access under security constraints. Two-factor authentication (T-FA) is a system wherein two different factors are used in conjunction to authenticate. Using two factors as opposed to one factor generally delivers a higher level of authentication assurance. Using more than one factor is sometimes called strong authentication or multi-factor authentication. |
|
TAP |
TAP stands for trusted authentication protocol. This is to be used, when authentication is performed by a third party and Access Manager asserts the token sent back. After asserting the token, Access Manager creates its cookie and continues the normal single-sign on flow. A trust mechanism exists between the OAM Server and the external third party which performs the authentication. In this scenario, Access Manager acts as an asserter and not authenticator. |
|
TAPScheme |
This is the authentication scheme that is used to protect resources in an Access Manager and OAAM integration that uses TAP. If you want two TAP partners with different tapRedirectUrls, create a new authentication scheme using the Oracle Access Management Console and use that scheme. When configured, this authentication scheme can collect context-specific information before submitting the request to the Access Server. Context-specific information can be in the form of an external call for information. |
|
TextPad |
Personalized device for entering a password or PIN using a regular keyboard. This method of data entry helps to defend against phishing. TextPad is often deployed as the default for all users in a large deployment then each user individually can upgrade to another device if they wish. The personal image and phrase a user registers and sees every time they login to the valid site serves as a shared secret between user and server. |
|
Virtual authenticators |
A personalized device for entering a password or PIN or an authentication credential entry device to protect users while interacting with a protected web application. The virtual authentication devices harden the process of entering and transmitting authentication credentials and provide end users with verification they are authenticating on the valid application. For information on virtual authenticators, see "Using Virtual Authentication Devices" in the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager. |
|
Web Agent |
A single sign-on agent (also known as a policy-enforcement agent, or simply an agent) is any front-ending entity that acts as an access client to enable single sign-on across enterprise applications. To secure access to protected resources, a Web server, Application Server, or third-party application must be associated with a registered policy enforcement agent. The agent acts as a filter for HTTP requests, and must be installed on the computer hosting the Web server where the application resides. Individual agents must be registered with Access Manager 11g to set up the required trust mechanism between the agent and OAM Server. Registered agents delegate authentication tasks to the OAM Server. |
|
WebGate |
Web server plug-in that acts as an access client. WebGate intercepts HTTP requests for Web resources and forwards them to the OAM Server for authentication and authorization |
8.3 OAAM Basic Integration with Access Manager
This section explains how to configure OAAM Basic integration with Access Manager.
The following topics explain how this type of integration is implemented:
8.3.1 Prerequisites
Prior to configuring Access Manager with Oracle Adaptive Access Manager, you must have installed all the required components, including any dependencies, and configured the environment in preparation of the integration tasks that follow.
Note:
Key installation and configuration information is provided in this section. However, not all component prerequisite, dependency, and installation instruction is duplicated here. Adapt information as required for your environment.
For complete installation information, follow the instructions in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
The following are the required components that must be installed and configured before the integration tasks are performed.
Table 8-3 Required Components for Integration
| Component | Information |
|---|---|
|
Oracle Database |
Ensure that you have an Oracle Database installed on your system before installing Oracle Identity and Access Management. The database must be up and running to install the relevant Oracle Identity and Access Management component. For more information, see "Database Requirements" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
|
WebLogic Servers |
For more information, see Installing Oracle WebLogic Server and Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
|
Access Manager and Oracle Adaptive Access Manager schemas |
Run RCU to create the schemas for Access Manager and OAAM. Oracle Fusion Middleware Repository Creation Utility is available on the Oracle Technology Network (OTN) Web site. For more information about using RCU, see Oracle Fusion Middleware Repository Creation Utility User's Guide. |
|
Access Manager and Oracle Adaptive Access Manager |
Install Access Manager and OAAM. For information on installing and configuring Access Manager, see "Installing and Configuring Oracle Identity and Access Management (11.1.2)" and "Configuring Oracle Access Management" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. For information on installing and configuring Oracle Adaptive Access Manager, see "Installing and Configuring Oracle Identity and Access Management (11.1.2)" and "Configuring Oracle Adaptive Access Manager" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. Run the Oracle Identity Management 11g Fusion Middleware Configuration Wizard to configure Oracle Adaptive Access Manager and Access Manager in a new WebLogic administration domain or in an existing one. They can be on the same domain or different domains. Patch the software to the latest version. For information, see Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
8.3.2 Start WebLogic Server
Start the WebLogic Administration Server for the WebLogic Server domain.
DOMAIN_HOME/bin/startWeblogic.sh
8.3.3 Configuring OAAM Basic Integration with Access Manager
Follow the steps in this section to implement the Access Manager and Oracle Adaptive Access Manager integration.
Create a Policy to Protect Application
-
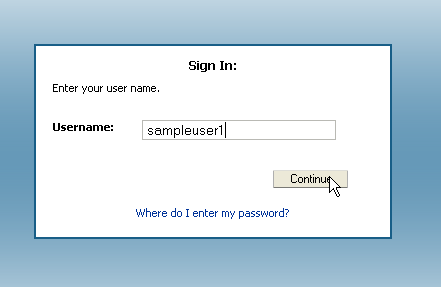
Log in to the Oracle Access Management Console:
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
Select Resources under IDMDomainAgent.
-
Add the protected resource.
For example, provide the following information for the resource:
-
Host Identifier:
IDMDomain -
Resource URL:
/resource/.../*
-
Create a New Authentication Policy
Create a new Authentication Policy under IDMDomainAgent and make sure to set the Authentication Scheme to OAAMBasic.
In this step, you are associating the protected resource with the OAAMBasic Authentication Scheme.
-
In the left pane, double-click Application Domains, then click Search, and in the search results, click IAM Suite.
-
Click the Authentication Policies tab and then the Create Authentication Policy button.
-
Add general policy details:
Name: A unique name used as an identifier in the left pane. For example,
HighPolicy.Authentication Scheme:
OAAMBasic -
Add global policy elements and specifications:
Description (optional): Optional unique text that describes this authentication policy.
Success URL: The redirect URL to be used upon successful authentication.
Failure URL: The redirect URL to be used if authentication fails.
-
Add Resources:
Choose the URL of a resource from those listed. The listed URLs were added to this application domain earlier. You can add one or more resources to protect with this authentication policy. The resource definition must exist within the application domain before you can include it in a policy.
-
Click the Resources tab on the Authentication Policy page.
-
Click the Add button on the tab.
-
Choose the URL from the list. For example,
/higherriskresource.
-
-
Click Apply to save changes and close the Confirmation window.
-
Add policy responses.
Responses are the obligations (post authentication actions) to be carried out by the Web agent. After a successful authentication, the application server hosting the protected application should be able to assert the User Identity based on these responses.After a failed authentication, the browser redirects the request to a pre-configured URL
-
Close the page when you finish.
Create a New Authorization Policy
Create a new Authorization Policy.
-
In the left pane, double-click Authorization Policies and then the Create button.
-
Enter a unique name for this authorization policy.
-
On the Resource tab, click the Add button.
-
From the list provided, click a resource URL.
Resource URL:
IDMDomain:/<resource>/.../* -
Click Apply to save changes and close the Confirmation window.
Create User with Privileges to Log into the OAAM Administration Console
By default there is not a user that has the correct privileges to log in to the OAAM Administration console. You must create a user that has the correct privileges to log in to the OAAM Administration Console and then grant the necessary groups to the user.
-
Log in to the Oracle WebLogic Administration Console for your WebLogic administration domain.
-
Under Domain Structure in the left pane, select Security Realms.
-
On the Summary of Security Realms page, select the realm that you are configuring (for example,
myrealm). -
On the Settings for Realm Name page select Users and Groups and then Users.
-
Click New and provide the required information to create a user, such as
user1, in the security realm:-
Name:
oaam_admin_username -
Description: optional
-
Provider:
DefaultAuthenticator -
Password/Confirmation
-
-
Click the newly created user,
user1. -
Click the Groups tab.
-
Assign any of the groups with the
OAAMkeyword to the user,user1.Move those groups from the left (available) to the right (chosen).
-
Click Save.
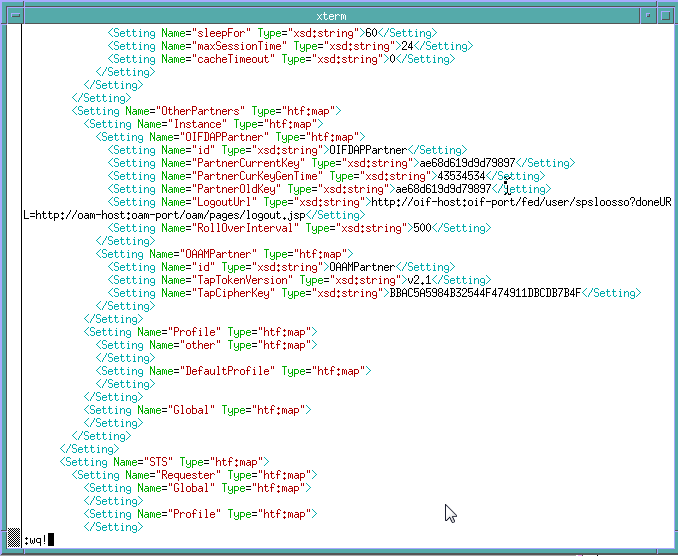
Locate and modify the oam-config.xml file manually.
The oam-config.xml file contains all Access Manager-related system configuration data and is located in the DOMAIN_HOME/config/fmwconfig directory.
Set the OAAMEnabled property to true as shown in the following example:
<Setting Name="OAAM" Type="htf:map"> <Setting Name="OAAMEnabled" Type="xsd:boolean">true</Setting> <Setting Name="passwordPage" Type="xsd:string">/pages/oaam/password.jsp</Setting> <Setting Name="challengePage" Type="xsd:string">/pages/oaam/challenge.jsp</Setting> <Setting Name="registerImagePhrasePage" Type="xsd:string">/pages/oaam/registerImagePhrase.jsp</Setting> <Setting Name="registerQuestionsPage" Type="xsd:string">/pages/oaam/registerQuestions.jsp</Setting>
If you prefer to use the configureOAAM WLST command to create the data source, associate it as a target with the OAM Server, and enable the property in the oam-config.xml, refer to "Using ConfigureOAAM WLST to Create the Datasource in OAAM Basic Integration with Access Manager".
Start the OAAM Admin Server, oaam_admin_server1, to register the newly created managed servers with the domain.
DOMAIN_HOME/bin/startManagedWeblogic.sh oaam_admin_server1
A full snapshot of policies, rules, challenge questions, dependent components, and configurations is shipped with Oracle Adaptive Access Manager. This snapshot is required for the minimum configuration of OAAM. Import the snapshot into the system by following these instructions:
-
Log in to the OAAM Administration Console.
http://oaam_managed_server_host:oaam_admin_managed_server_port/oaam_admin
-
Load the snapshot file from the MW_HOME/IDM_ORACLE_HOME/oaam/init directory into the system by following these instructions:
-
In the left pane, open System Snapshot under the Environment node.
-
Click the Load from File button.
A Load and Restore Snapshot screen appears.
-
Deselect Back up current system now and click Continue.
-
When the dialog appears with the message that you have not chosen to back up the current system, and do you want to continue, click Continue.
The Load and Restore Snapshot page appears for you to choose a snapshot to load.
-
Browse for
oaam_base_snapshot.zipand click the Load button to load the snapshot into the system database.The default
oaam_base_snapshot.zipis located in the OAAM_HOME/oaam/initdirectory. -
Click OK and then Restore.
-
To ensure correct operation, make sure that the default base policies and challenge questions shipped with Oracle Adaptive Access Manager have been imported into your system. For details, see Setting Up the Oracle Adaptive Access Manager Environment in the Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager.
You may encounter a non-working URL if policies and challenge questions are not available as expected in your Oracle Adaptive Access Manager environment.
Shut down the OAAM Administration Server
Shut down the OAAM Administration Server, oaam_admin_server1.
DOMAIN_HOME/bin/stopManagedWeblogic.sh oaam_admin_server1
-
Access the Oracle WebLogic Administration Console:
http://weblogic_admin_server:7001/console -
If Oracle Adaptive Access Manager is not configured to be in the same WebLogic domain as Access Manager, perform the following steps for Access Manager:
-
Create a datasource with the following JNDI name:
jdbc/OAAM_SERVER_DB_DS
Note:
The name of the datasource can be any valid string, but the JNDI name should be as shown above.
-
To the schema you created as part of the Oracle Adaptive Access Manager configuration, provide the connection details for the Oracle Adaptive Access Manager database.
-
-
Click Services and then Database Resources and locate the OAAM_SERVER_DB_DS resource.
-
Lock the environment by clicking the Lock button in the upper left corner of the WebLogic Administration Console.
-
Open the OAAM_SERVER_DB_DS resource and click the Target tab. Once there, you are presented a list of WebLogic servers that are available.
-
Associate Administration Server and oam_server1 as targets with the datasource.
-
Click the Activate button in the upper left corner of the Oracle WebLogic Administration Console.
-
Access the protected resource configured in earlier to verify the configuration.
At this point the configuration of Oracle Adaptive Access Manager is completed.
You are prompted to enter a user name. Then, on a separate screen you are prompted for the password.
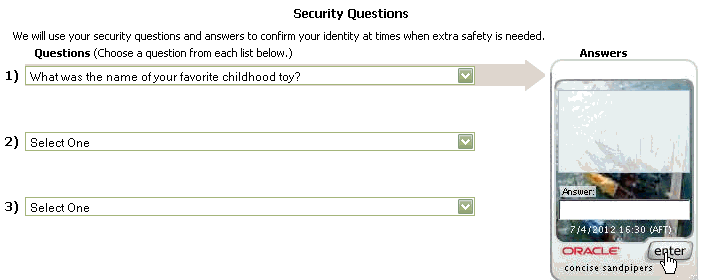
Once the user name and password are validated you are asked to select and answer three challenge questions. Once completed you are taken to the protected application.
-
For verify the configuration, remote-register two agents, each protecting a resource.
-
Use the Oracle Access Management Console to associate the first resource with the
OAAMBasicpolicy for the authentication flow. Associate the second resource with theLDAPScheme.
8.4 OAAM Advanced Integration with Access Manager
Integrating Oracle Adaptive Access Manager with Oracle Access Manager provides an enterprise with advanced access security features that greatly improve the level of protection for applications. Features including anti-phishing, anti-malware, device fingerprinting, behavioral profiling, geolocation mapping, real-time risk analysis and multiple risk-based challenge mechanisms such as one-time password and knowledge based authentication questions provide an increased level of access security.
This section explains how to integrate Oracle Access Management Access Manager (Access Manager) 11g and Oracle Adaptive Access Manager (OAAM) 11g as an Advanced integration.
In Access Manager and OAAM TAP integration, OAAM Server acts as a trusted partner application. The OAAM Server uses the Trusted authentication protocol (TAP) to communicate the authenticated username to OAM server after it performs strong authentication and risk and fraud analysis. The OAM server then redirects the user to the protected resource.
OAAM Advanced integration with Access Manager can involve scenarios with or without Oracle Identity Manager.
Integration with Oracle Identity Manager provides users with richer password management functionality, including secure "Forgot Password" and "Change Password" flows.
For integration details, see Chapter 9, "Integrating Access Manager, OAAM, and OIM".
Without Oracle Identity Manager
If Oracle Identity Manager is not part of your environment, follow the integration procedure described in this chapter.
8.4.1 Integration Roadmap
Table 8-4 lists the high-level tasks for integrating Access Manager and Oracle Adaptive Access Manager.
The configuration instructions assume Access Manager and Oracle Adaptive Access Manager are integrated using the out-of-the box integration.
Table 8-4 Integration Flow for Access Manager and Oracle Adaptive Access Manager
| Number | Task | Information |
|---|---|---|
|
1 |
Verify that all required components have been installed and configured prior to integration. |
For information, see "Integration Prerequisites". |
|
2 |
Ensure the Access Manager and OAAM Administration Consoles and managed servers are running. |
For information, see "Restarting the Servers". |
|
3 |
Create the OAAM users. Before you can access the OAAM Administration Console, you must create administration users. |
For information, see "Creating the OAAM Admin Users and OAAM Groups". |
|
4 |
Import the OAAM base snapshot. A full snapshot of policies, dependent components and configurations is shipped with Oracle Adaptive Access Manager. For Oracle Adaptive Access Manager to be functional, you must import the snapshot into the system. |
For information, see "Importing Oracle Adaptive Access Manager Snapshot". |
|
5 |
Validate that Access Manager was set up correctly. You should be able to log in to the Oracle Access Management Console successfully. |
For information, see "Validating Initial Configuration of Access Manager" |
|
6 |
Validate that OAAM was set up correctly. |
For information, see "Validating Initial Configuration of Oracle Adaptive Access Manager". |
|
7 |
Register the WebGate agent. The WebGate is an out-of-the-box access client. This Web server access client intercepts HTTP requests for Web resources and forwards these to the OAM Server 11g. |
For information, see "Registering WebGate Using the Oracle Access Management Console" |
|
8 |
Register the OAAM server to act as a trusted partner application to Access Manager. A partner application is any application that delegates the authentication function to Access Manager 11g. |
For information, see "Registering the OAAM Server as a Partner Application to Access Manager" |
|
9 |
Add the agent password. When Access Manager is installed, a default agent profile called IAMSuiteAgent is created. This profile is used by Oracle Adaptive Access Manager when integrating with Access Manager. When the IAMSuiteAgent profile is first created, it has no password. You must set a password before the profile can be used by Oracle Adaptive Access Manager for integration. |
For information, see "Adding a Password to the IAMSuiteAgent Profile in the Oracle Access Management Console" |
|
10 |
Update the IAMSuiteAgent. |
For information, see "Updating the IAMSuiteAgent in the WebLogic Administration Console". |
|
11 |
Verify TAP partner registration using the Oracle Access Management tester. |
For information, see "Verifying TAP Partner Registration". |
|
12 |
Set up TAP integration properties in OAAM. |
For information, see "Setting Up Access Manager TAP Integration Properties in OAAM". |
8.4.2 Integration Prerequisites
Prior to configuring Access Manager with Oracle Adaptive Access Manager, you must have installed all the required components, including any dependencies, and configure the environment in preparation of the integration tasks that follow.
Note:
Key installation and configuration information is provided in this section. However, not all component prerequisite, dependency, and installation instruction is duplicated here. Adapt information as required for your environment.
For complete installation information, follow the instructions in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
The following are the required components that must be installed and configured before the integration tasks are performed.
Table 8-5 Required Components for Integration
| Component | Information |
|---|---|
|
Oracle HTTP Server |
For more information on installing the HTTP Server, see Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
|
Oracle Access Manager 10g or Access Manager 11g agent (WebGate) |
For information on installing the Oracle Access Management 11g WebGate, see "Installing and Configuring Oracle HTTP Server 11g WebGate" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. For information on installing the OAM 10g WebGate, see "Registering and Managing 10g Webgates with Access Manager 11g" in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management. |
|
Oracle Database |
Ensure that you have an Oracle Database installed on your system before installing Access Manager and OAAM. The database must be up and running to install the products. For more information, see "Database Requirements" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
|
Repository Creation Utility (RCU) |
Oracle Fusion Middleware Repository Creation Utility (RCU) is available on the Oracle Technology Network (OTN) Web site. For more information about using RCU, see "Creating Database Schema Using the Oracle Fusion Middleware Repository Creation Utility (RCU)" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management and Oracle Fusion Middleware Repository Creation Utility User's Guide. You will need to install and run RCU to create database schemas for Access Manager and OAAM. |
|
Oracle Access Management Access Manager and Oracle Adaptive Access Manager schemas |
Execute the Oracle Fusion Middleware Repository Creation Utility (RCU) to load the Access Manager and OAAM schemas into the database. Note: Ensure that the database and listener are running before creating the schemas. |
|
Oracle WebLogic Servers |
Install WebLogic servers. In this chapter, For more information, see "Installing Oracle WebLogic Server and Creating the Oracle Middleware Home" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
|
Access Manager |
You must install and configure Access Manager. At installation, Access Manager is configured with the database policy store. The Access Manager and Oracle Adaptive Access Manager wiring requires the database policy store. For information on installing and configuring Access Manager, see "Installing and Configuring Oracle Identity and Access Management (11.1.2)" and "Configuring Oracle Access Management" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
|
Oracle Adaptive Access Manager |
You must install and configure Oracle Adaptive Access Manager: For information on installing and configuring Oracle Adaptive Access Manager, see "Installing and Configuring Oracle Identity and Access Management (11.1.2)" and "Configuring Oracle Adaptive Access Manager" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management. |
If so preferred, Oracle Access Manager and Oracle Adaptive Access Manager can be installed in separate domains or on the same WebLogic domain.
For multiple domain installation, the oaam.csf.useMBeans property must be set to true. Refer to "Oracle Adaptive Access Manager Command-Line Interface Scripts" in the Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager for information on setting this parameter.
During the integration steps below, for reference we will refer to the WLS Domain which contains Oracle Access Manager as OAM_DOMAIN_HOME, and the WLS Domain which contains OAAM as OAAM_DOMAIN_HOME.
For information on installing the Identity Management Suite, see Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
8.4.3 Restarting the Servers
Before you can perform tasks in this section, ensure that the Access Manager and OAAM Administration Consoles and managed servers are running. To restart the servers, perform these steps:
-
Start the WebLogic Administration Server.
OAM_DOMAIN_HOME/bin/startWeblogic.shIf OAAM is in a different domain, you must also start the WebLogic Administration Server located in
OAAM_Domain_Home:OAAM_DOMAIN_HOME/bin/startWeblogic.sh -
Start the managed server hosting the OAM Server.
OAM_DOMAIN_HOME/bin/startManagedWeblogic.sh oam_server1
-
Start the managed server hosting OAAM Admin Server.
OAAM_DOMAIN_HOME/bin/startManagedWeblogic.sh oaam_admin_server1
-
Start the managed server hosting the Oracle Adaptive Access Manager runtime server.
OAAM_DOMAIN_HOME/bin/startManagedWeblogic.sh oaam_server_server1
8.4.4 Creating the OAAM Admin Users and OAAM Groups
Before integrating Access Manager and OAAM, you must take into account whether the OAAM Administration Console is being protected. In order to access the OAAM Administration Console, you must create administration users.
-
If protecting the OAAM Administration Console, you must take care of user and group creation in the external LDAP store. For details, see Chapter 2, "Using the idmConfigTool Command."
OR
-
If not protecting the OAAM Administration Console, then the administration user must be created in the WebLogic Administration Console.
To disable OAAM Administration Console protection, refer to Section 8.5.5, "Disabling OAAM Administration Console Protection."
The following are instructions to create administration users in the WebLogic Administration Console:
-
Log in to the Oracle WebLogic Administration Console for your WebLogic administration domain.
-
In the Domain Structure tab in the left pane, select Security Realms.
-
On the Summary of Security Realms page, select the realm that you are configuring (for example,
myrealm). -
On the Settings for Realm Name page select Users and Groups and then Users.
-
Click New and provide the required information to create a user, such as
user1, in the security realm:-
Name:
oaam_admin_username -
Description: optional
-
Provider:
DefaultAuthenticator -
Password/Confirmation
-
-
Click the newly created user,
user1. -
Click the Groups tab.
-
Assign all the groups with the
OAAMkeyword to the user,user1.Move those groups from the left (available) to the right (chosen).
-
Click Save to save the changes.
8.4.5 Importing Oracle Adaptive Access Manager Snapshot
A full snapshot of policies, rules, challenge questions, dependent components, and configurations is shipped with Oracle Adaptive Access Manager. This snapshot is required for the minimum configuration of OAAM. Import the snapshot into the system by following these instructions:
-
Log in to the OAAM Administration Console with the newly created user.
http://oaam_managed_server_host:oaam_admin_managed_server_port/oaam_admin
-
Open System Snapshot under Environment in the Navigation tree.
The System Snapshots Search page is displayed.
-
Click the Load from File button in the upper right.
A Load and Restore Snapshot screen appears.
-
Deselect Back up current system now and click Continue.
-
When the dialog appears with the message that you have not chosen to back up the current system, and do you want to continue, click Continue.
-
Click the Choose File button.
-
Now that you are ready to load the snapshot, click the Browse button on the dialog in which you can enter the filename of the snapshot you want to load. A screen appears for you to navigate to the directory where the snapshot file is located. Click Open. Then, click the Load button to load the snapshot into the system.
The snapshot file,
oaam_base_snapshot.zipis located in theOracle_IDM1/oaam/initdirectory where the OAAM base content is shipped. -
Click OK.
So far, you have loaded the snapshot into memory. The items in the snapshot are not effective yet. Unless you click the Restore button, the items in the snapshot have not been applied.
-
To apply the snapshot, click Restore.
Once you have applied the snapshot, make sure it appears in the System Snapshots page.
To ensure correct operation, make sure that the default base policies and challenge questions shipped with Oracle Adaptive Access Manager have been imported into your system. For details, see Setting Up the Oracle Adaptive Access Manager Environment in the Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager.
You may encounter a non-working URL if policies and challenge questions are not available as expected in your Oracle Adaptive Access Manager environment.
8.4.6 Validating Initial Configuration of Access Manager
Verify that Access Manager is set up correctly by accessing the Welcome to Oracle Access Management page.
-
Log in to the Oracle Access Management Console:
http://oam_adminserver_host:oam_adminserver_port/oamconsole
You should be redirected to the OAM Server for login.
-
Provide the WebLogic administrator user name and password.
If the login is successful, the Welcome to Oracle Access Management page is displayed.
8.4.7 Validating Initial Configuration of Oracle Adaptive Access Manager
Verify that Oracle Adaptive Access Manager is set up correctly by accessing the OAAM Server.
-
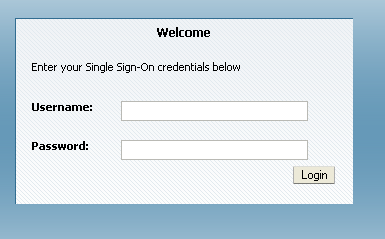
Log in to the OAAM Server.
http://host:port/oaam_server
-
Provide any user name and click Continue.
-
Provide the password as "test" because the Access Manager and Oracle Adaptive Access Manager integration has not yet been performed. You must change the password immediately after the integration.
-
Click the Enter button on the virtual authentication device.
-
Click Continue to register the new user.
-
Click Continue to accept the security device.
-
Choose questions and provide answers to register for Knowledge Based Authentication (KBA).
A successful login indicates that you have configured the initial configuration correctly.
8.4.8 Registering WebGate Using the Oracle Access Management Console
This section describes how to create and register the 11g WebGate. Oracle HTTP Server WebGate is a Web server extension that is available with Oracle Access Manager. The Oracle HTTP Server WebGate intercepts HTTP requests from users for Web resources and forwards them to the Access Server for authentication and authorization. Oracle HTTP Server WebGate installation packages are found on media and virtual media that is separate from the core components. For information on installing the Oracle HTTP Server WebGate, see "Installing and Configuring Oracle HTTP Server 11g Webgate for Oracle Access Manager" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
8.4.8.1 Pre-requisites for WebGate Registration
Ensure that the following are installed before configuring and registering the Oracle Web Gate:
-
WebLogic Server for Oracle HTTP Server (
WLS_FOR_OHS) -
Oracle HTTP Server (
WLS_FOR_OHS/Oracle_WT1, call thisOHS_HOME) -
WebGate (
WLS_FOR_OHS/Oracle_OAMWebGate1, call thisWG_HOME)
For information, see "Preparing to Install Oracle HTTP Server 11g Webgate for Oracle Access Manager" in Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management
8.4.8.2 Configure the 11g WebGate
After installing WebGate, perform the post-installation steps. For information, see Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
8.4.8.3 Register the 11g WebGate as a Partner Using the Oracle Access Management Console
You must register the Access Manager Agent that resides on the computer hosting the application to be protected.
Registering an agent sets up the required trust mechanism between the agent and the Access Manager engine. Registered agents delegate authentication tasks to the OAM Server.
For information, see Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
-
Go to the Oracle Access Management Console.
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
Register the 11g WebGate partner using the Oracle Access Management Console.
-
Click the Edit button in the tool bar to display the configuration page.
-
Set the Access Client Password and click Apply to save the changes. Note the Artifacts Location in the confirmation message.
-
In the Artifacts Location, locate the
ObAccessClient.xmlconfiguration file andcwallet.ssoand copy them to the OHS_HOME/instances/instance/config/OHS/component/webgate/configdirectory.
8.4.8.4 Restarting the OHS WebGate
Restart the Web server (OHS) for the changes to take effect.
-
Navigate to the OHS_HOME
/instances/instance/bindirectory. -
Restart the OHS instance by using the following command:
opmnctl stopall opmnctl startall
8.4.8.5 Validating the WebGate Setup
Once the setup of WebGate is complete, validate the registration:
-
Verify the WebGate configuration by accessing the protected URL.
http://ohs_host:ohs_port/
You should be redirected to Access Manager SSO login page for authentication.
-
Enter user name and password.
The Oracle HTTP Server Welcome page should be displayed.
This is the partner that will be protected using Oracle Adaptive Access Manager.
8.4.9 Registering the OAAM Server as a Partner Application to Access Manager
A partner application is any application that delegates the authentication function to Access Manager 11g. If OAAM is registered with Access Manager as a partner application, OAAM will then be able to communicate with Access Manager via the Trusted Authentication Protocol (TAP) to communicate the authenticated user name to the OAM Server after it performs strong authentication, risk, and fraud analysis, and the OAM Server owns the responsibility for redirecting to the protected resource.
If authentication is successful and the user has the appropriate profile registered, Oracle Adaptive Access Manager constructs the TAP token with the user name and sends it back to Access Manager. Access Manager asserts the token sent back. After asserting the token, Access Manager creates its cookie and continues the normal single-sign on flow in which it redirects the user to the protected resource.
To register the OAAM Server as a trusted partner application to Access Manager, follow these steps:
-
Ensure that the Access Manager Administration Server is running.
-
Set up the environment for WLST.
-
Go to IAM_ORACLE_HOME
/common/bin.cd IAM_ORACLE_HOME/common/bin -
Execute the
wlst.shto enter the WLST shell../wlst.sh
-
Type
Connectto connect to the WebLogic Administration Server. -
Enter username. For example,
admin_username. -
Enter password. For example,
admin_password. -
Enter t3://hostname:port
For example
t3://AdminHostname:7001 -
In another terminal window, create the
keystoredirectory by executing the following:mkdir IAM_ORACLE_HOME/TAP/TapKeyStore -
Using the WLST shell, run the
registerThirdPartyTAPPartnercommand:registerThirdPartyTAPPartner(partnerName = "partnerName", keystoreLocation= "path to keystore", password="keystore password", tapTokenVersion="v2.0", tapScheme="TAPScheme", tapRedirectUrl="OAAM login URL")
The command registers any third party as a Trusted Authentication Protocol (TAP) Partner.
An example is provided below.
registerThirdPartyTAPPartner(partnerName = "OAAMTAPPartner", keystoreLocation= "IAM_ORACLE_HOME/TAP/TapKeyStore/mykeystore.jks" , password="password", tapTokenVersion="v2.0", tapScheme="TAPScheme", tapRedirectUrl="http://OAAM_ Managed_server_host:14300/oaam_server/oamLoginPage.jsp")
Parameter Details partnerName
The name of the partner should be unique. It can be any name used for identifying the third party partner. If the partner exists in Access Manager, the configuration will be overwritten.
keystoreLocation
The keystore location is an existing location. If the directory path specified is not present, an error occurs. You must provide the complete path including the keystore file name. In the example shown earlier, the keystore location was
IAM_ORACLE_HOME/TAP/TapKeyStore/mykeystore.jks. Another example iskeystoreLocation= "/scratch/jsmith/dwps1tap/TapKeyStore/mykeystore.jks". When you run the commandregisterThirdPartyTAPPartner, the keystore file is created in that location specified. On Windows, the path must be escaped. For example:"C:\\oam-oaam\\tap\\tapkeystore\\mykeystore.jks"
password
The keystore password used to encrypt the keystore. The keystore is created by running command "registerThirdPartyTAPPartner" in the location as specified for parameter "keystoreLocation". Make a note of the password as you will need it later.
tapTokenVersion
Version of the Trusted Authentication Protocol.
tapTokenVersionis alwaysv2.0for 11.1.1.5.0 and 11.1.2.0. If using IDContext Claims, it isv2.1.tapScheme
Trusted Authentication Protocol Authentication Scheme (TAPScheme out of the box.) This is the authentication scheme that will be updated. If you want two tap partners with different tapRedirectUrls, create a new authentication scheme using the Oracle Access Management Console and use that scheme here.
The authentication scheme will be created automatically while you are running the
registerThirdPartyTAPPartnercommand in the instructions above. The name ofTAPSchemewill be passed as parameter to that command. The example command hastapScheme="TAPScheme".tapRedirectUrl
Third party access URL. The TAP redirect URL should be accessible. If it is not, registration of the partner fails with the message:
Error! Hyperlink reference not valid.tapRedirectUrlis constructed as follows:http://oaamserver_host:oaamserver_port/oaam_server/oamLoginPage.jspEnsure that the OAAM server is running; otherwise registration will fail. The credential collector page will be served by the OAAM Server. The authentication scheme created by
registerThirdPartyTAPPartner(TAPScheme) points to the OAAM Server credential collector page as the redirectURL. -
Type
exit ()to quit the WebLogic shell.
8.4.10 Setting the Agent Password
You will need to specify the Agent password in multiple places. OAAM needs this agent password in order to use the agent profile for integration.
8.4.10.1 Adding a Password to the IAMSuiteAgent Profile in the Oracle Access Management Console
When Access Manager is installed, a default agent profile called IAMSuiteAgent is created. This profile is used by OAAM when integrating with Access Manager. When the IAMSuiteAgent profile is first created, it has no password. You must set a password before the profile can be used by OAAM for integration. To do this, proceed as follows:
-
Log in to the Oracle Access Management Console.
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
Enter username and password.
-
Select the System Configuration tab.
-
Expand Access Manager Settings, and then SSO Agents.
-
Double-click OAM Agent.
The WebGate page opens in the right hand pane.
-
Click Search to list all WebGate agents including IAMSuiteAgent.
-
Double-click IAMSuiteAgent to edit the properties.
-
Specify the password in the Access Client Password field and click Apply to save the changes.
This is a required step.
8.4.10.2 Updating the IAMSuiteAgent in the WebLogic Administration Console
Note: The IAMSuiteAgent is now in Open Mode with password authentication. If you are using the domain agent in the IDM Domain for another console, update the domain agent definition so that you can continue using the domain agent.
-
Log in to WebLogic Administration Console.
http:oam_adminserver_host:port/console
-
Enter credentials.
-
Select Security Realms from the Domain Structure menu.
-
Click myrealm.
-
Click the Providers tab.
-
Select IAMSuiteAgent from the list of authentication providers.
-
Click Provider Specific.
-
Enter the agent password and confirm the password.
This is a required step.
-
Click Save.
-
Click Activate Change on the top left corner.
-
Restart the WebLogic Administration Server, OAAM Admin and managed servers, and OAM Server.
8.4.11 Verifying TAP Partner Registration
To verify the TAP partner registration, follow the instructions below.
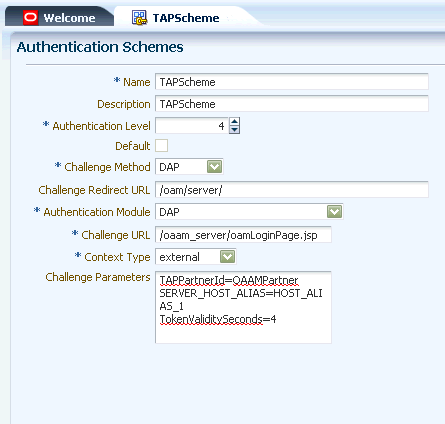
8.4.11.1 Verifying the Challenge URL
To validate the Access Manager configuration, perform the following steps:
-
Log in to the Oracle Access Management Console.
-
Enter credentials.
-
Click the Policy Configuration tab in the left pane of the console.
-
In the left pane, expand the Authentication Schemes node.
-
Double-click the TAPScheme authentication scheme.
-
Verify that the Challenge Method is
DAPand the Authentication Module isDAP. -
Verify that Challenge URL shows part of the value of the tapRedirectUrl that had been specified when OAAM was registered with Access Manager as a partner application. For example, if the
tapRedirectUrlishttp://OAAM_Managed_server_host:14300/oaam_server/oamLoginPage.jsp, then Challenge URL should show/oaam_server/oamLoginPage.jsp. The host and port part of the URL is parameterized in Challenge Parameter. In the Challenge Parameters field, you will see bothTAPPartnerId=OAAMPartnerandSERVER_HOST_ALIAS=HOST_ALIAS_1. -
Check the challenge parameters are set correctly.
8.4.11.2 Adding the MatchLDAPAttribute Challenge Parameter in the TAPScheme
You must add the MatchLDAPAttribute challenge parameter and set it to the User Name Attribute as specified in the LDAP Identity Store.
-
Log in to the Oracle Access Management Console.
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
Enter credentials.
-
Click the Policy Configuration tab to the left of the screen.
-
Expand the Authentication Schemes node.
-
Double-click TAPScheme authentication scheme.
-
To add another parameter to an existing parameter, position your cursor in the Challenge Parameter field and press Enter using your keyboard.
-
In the new line, add an entry for the challenge parameter.
For example,
MatchLDAPAttribute=uidMatchLDAPAttributemust be set to theUser Name Attributeas specified in the LDAP Identity Store. For example,uid,mail,cn, and so on.Note:
The challenge parameter is case-sensitive.
For information, see "Managing User Identity Stores" in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
-
Click Apply to submit the change.
-
Dismiss the Confirmation window.
8.4.11.3 Validating the IAMSuiteAgent Setup
To validate the IAMSuiteAgent setup, proceed as follows:
-
Restart the managed server hosting the OAM Server.
-
Stop the managed server hosting the OAM Server.
OAM_DOMAIN_HOME/bin/stopManagedWeblogic.sh oam_server1
-
Start the managed server hosting the OAM Server.
OAM_DOMAIN_HOME/bin/startManagedWeblogic.sh oam_server1
-
-
Launch Oracle Access Management tester.
IAM_ORACLE_HOME/../jdk_version/bin/java -jar IAM_ORACLE_ HOME/oam/server/tester/oamtest.jar
The Oracle Access Management Tester Console appears.
-
In the Server Connection section provide server connection details:
-
IP Address: Access Manager Managed Server Host
-
Port: Oracle Access Management Oracle Access Protocol (OAP) Port
-
Agent ID:
IAMSuiteAgent -
Agent Password:
Passwordprovided in Adding a Password to the IAMSuiteAgent Profile in the Oracle Access Management Console
The Server Connection section provides fields for the information required to establish a connection to the OAM Server.
-
-
Click Connect.
If you can connect to the server, the next section, Protected Resource URI, will be enabled.
-
The Protected Resource URI section provides information about a resource whose protected status needs to be validated.
In this section, provide the protected resource URI as follows:
-
Host:
IAMSuiteAgent -
Port:
80 -
Resource:
/oamTAPAuthenticateNote:
You can test any other resource protected using TAPScheme other than
oamTAPAuthenticate.
-
-
Click Validate
The Validate button is used to submit the Validate Resource server request. If the validation is successful, the next section for User Identity will be enabled.
-
In the User Identity section, provide
User Identityand click Authenticate. If the authentication is successful, the setup is successful.This section provides information about a user whose credentials need to be authenticated. The Authenticate button is used to submit the Authenticate User server request.
8.4.12 Setting Up Access Manager TAP Integration Properties in OAAM
To run setupOAMTapIntegration.sh to configure Access Manager for TAP Integration, proceed as follows:
Note:
If the OAAM command line script fails to run, then execute it as follows:
bash script_name
-
Ensure that the OAAM managed server is running.
-
Create a working directory.
mkdir temp cd temp mkdir oaam_cli cd..
-
Copy the OAAM
clifolder to the working directory.cp -r OAAM_HOME/oaam/cli/. temp/oaam_cli -
Open
oaam_cli.propertieslocated intemp/oaam_cli/conf/bharosa_properties witha text editor.gedit temp/oaam_cli/conf/bharosa_properties/oaam_cli.properties
-
Set the properties described in Table 8-7.
Parameter Details oaam.adminserver.hostname
This is the Admin Server host of the WebLogic Server Domain where OAAM is installed.
oaam.adminserver.port
This is the Admin Server port of the WebLogic Server Domain where OAAM is installed.
oaam.db.url
This is the valid JDBC URL of the OAAM database in the format:
jdbc:oracle:thin:@db_host:db_port:db_sid
oaam.uio.oam.tap.keystoreFile
This is the location of keystore file generated by
registerThirdPartyTAPPartnerWLST.Copy the file from the location specified in the above WLST for parameter "
keystoreLocation". If Access Manager and OAAM are on different machines, you will need to manually copy the keystore file created in the OAM Server to the OAAM Server and provide the location on the OAAM server here.On Windows, the file path value must be escaped. For example: "
C:\\oam-oaam\\tap\\keystore\\store.jks"oaam.uio.oam.tap.partnername
This is the "partnerName" used in the WLST registerThirdPartyTAPPartner command. For example, OAAMPartner.
oaam.uio.oam.host
This is the Access Manager Primary Host.
oaam.uio.oam.port
This is the Access Manager Primary Oracle Access Protocol (OAP) Port. This is the OAM Server port, with the default port number 5575.
oaam.uio.oam.webgate_id
This is the
IAMSuiteAgentvalue. Do not change this.oaam.uio.oam.secondary.host
Name of the secondary OAM Server Host machine. This property is used for high availability. You could specify the fail-over hostname using this property.
oaam.uio.oam.secondary.host.port
This is the Access Manager Secondary OAP Port. This property is used for high availability. You could specify the fail-over port using this property.
oaam.uio.oam.security.mode
This depends on the Access Manager security transport mode in use. The value can be 1 (for Open), 2 (for Simple), or 3 (for Cert). The default, if not specified, is 1 (Open).
oam.uio.oam.rootcertificate.keystore.filepath
The location of the Keystore file generated for the root certificate: DOMAIN_HOME/output/webgate-ssl/oamclient-truststore.jks.
This is required only for security modes 2 (Simple) and 3 (Cert).
oam.uio.oam.privatekeycertificate.keystore.filepath
The location of the Keystore file generated for private key: DOMAIN_HOME/output/webgate-ssl/oamclient-keystore.jks.
Private key is only required if you set up Access Manager and OAAM in Simple and Cert mode.
oaam.csf.useMBeans
For a multiple domain installation, the oaam.csf.useMBeans property must be set to true. For information on setting this parameter, see "Oracle Adaptive Access Manager Command-Line Interface Scripts" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager.
-
Save the changes and quit the editor.
-
Set Middleware and Java Home environment variables.
For bash:
export ORACLE_MW_HOME=Location_of_WebLogic_installation_where_Oracle_Adaptive_ Access_Manager_is_installed export JAVA_HOME=Location_of_JDK_used_for_the_WebLogic_installation
or
For csh:
setenv ORACLE_MW_HOME Location_of_WebLogic_installation_where_Oracle_Adaptive_ Access_Manager_is_installed setenv JAVA_HOME Location_of_JDK_used_for_the_WebLogic_installation
-
Change directory to
temp/oaam_cli/. -
Enable execute permissions.
chmod 777 setupOAMTapIntegration.sh
-
Run the OAAM setup integration script using the following command:
./setupOAMTapIntegration.sh conf/bharosa_properties/oaam_cli.properties
This script sets the properties required for the integration in OAAM.
-
When the command runs, it prompts you for the following information:
-
Weblogic Server Home Directory: Usually
$ORACLE_MW_HOME/wlserver_10.3 -
OAAM Admin server username: This is the Admin Server user name of the WebLogic Server Domain (usually weblogic).
-
OAAM Admin server password: This is the password for the Admin Server user.
-
OAAM database username: OAAM database user.
-
OAAM database password: Password for the OAAM database user.
-
Access Manager WebGate Credentials to be stored in CSF: Enter WebGate password.
-
Access Manager TAP Key store file password: The password you assigned when you registered the TAP partner. For information, see Registering the OAAM Server as a Partner Application to Access Manager.
When you set up Access Manager and Oracle Adaptive Access Manager integration in simple or Cert mode, the additional inputs you will have to provide are as follows:
-
Access Manager Private Key certificate Keystore file password: The Simple Mode Pass Phrase. You can obtain it by executing the WLST command
displaySimpleModeGlobalPassphrase. -
Oracle Access Management Global Pass phrase: The Simple Mode Pass Phrase. You can obtain it by executing the WLST command
displaySimpleModeGlobalPassphrase.
For information, refer to "Retrieving the Global Passphrase for Simple Mode" in the Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
-
8.4.13 Configuring a Resource to be Protected with TAPScheme
To protect a resource with the OAAM TAPScheme, proceed as follows:
8.4.13.1 Creating a New Resource under the Application Domain
To create a new resource to protect, proceed as follows:
-
Log in to the Oracle Access Management Console.
http://oam_host:port/oamconsole
-
Click the Policy Configuration tab in the Oracle Access Management Console.
-
Double-click Application Domains in the left panel.
-
In the Application Domains page, click Search, and in the search results, click IAM Suite
-
Click Resources tab.
-
Click the New Resource button to create a resource.
Type:
http. The HTTP type is the default; it covers resources that are accessed using either the HTTP or HTTPS protocol. Policies that govern a particular resource apply to all operations.Description: An optional unique description for this resource.
Host identifier:
IAMSuiteAgentResource URL: The URL value must be expressed as a single relative URL string that represents a path component of a full URL composed of a series of hierarchical levels separated by the '/' character. The URL value of a resource must begin with / and must match a resource value for the chosen host identifier.
For example:
/higherriskresourceProtection Level:
Protected -
Click Apply to add this resource to the application domain.
8.4.13.2 Create a New Authentication Policy that Uses TAPScheme to Protect the Resource
To create a new authentication policy that uses the TAPScheme authentication to protect the resource, proceed as follows:
-
Double-click Application Domains in the left panel.
-
In the Application Domains page, click Search, and in the search results, click IAM Suite
-
Click the Authentication Policies tab and then the Create Authentication Policy button.
-
Add general policy details:
Name: A unique name used as an identifier in the left pane. For example, HighPolicy.
Authentication Scheme: TAPScheme
-
Add global policy elements and specifications:
Description (optional): Optional unique text that describes this authentication policy.
Success URL: The redirect URL to be used upon successful authentication.
Failure URL: The redirect URL to be used if authentication fails.
-
Add Resources:
Choose the URL of a resource from those listed. The listed URLs were added to this application domain earlier. You can add one or more resources to protect with this authentication policy. The resource definition must exist within the application domain before you can include it in a policy.
-
Click the Resources tab on the Authentication Policy page.
-
Click the Add button on the tab.
-
Choose the URL from the list. For example,
/higherriskresource.
-
-
Click Apply to save changes and close the Confirmation window.
-
Add policy responses.
Responses are the obligations (post authentication actions) to be carried out by the Web agent. After a successful authentication, the application server hosting the protected application should be able to assert the User Identity based on these responses.After a failed authentication, the browser redirects the request to a pre-configured URL
-
Close the page when you finish.
8.4.14 Validating the Access Manager and Oracle Adaptive Access Manager Integration
Try to access the protected resource. You should be redirected to OAAM for registration and challenge. The OAAM login page is shown instead of the Access Manager login page.
8.5 Other Access Manager and OAAM Integration Configuration Tasks
This section describes other configuration procedures that you may need depending on your deployment.
8.5.1 Configuring Integration to Use TAPScheme to Protect IDM Product Resources in the IAM Suite Application Domain
Note:
The instructions in this section should only be performed if you want to use TAPscheme in the IAMSuiteAgent application domain.
To use TAPscheme for Identity Management product resources in the IAM Suite domain, Protected HigherLevel Policy, the following configuration must be performed:
-
Log in to the Oracle Access Management Console.
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
In the navigation tree, double-click Application Domains, then click Search, and in the search results, click IAM Suite.
-
Click the Authentication Policies tab.
-
Click Protected Higher Level Policy.
-
In the Resources window click /oamTAPAuthenticate.
-
Click Delete, and then Apply.
-
Create a new Authentication Policy in the IAMSuite application domain.
-
For authentication scheme, choose LDAP Scheme.
-
In the Resources window, click Add.
-
Select the resource /oamTAPAuthenticate.
-
Click Apply.
8.5.2 Changing the Authentication Level of the TAPScheme Authentication Scheme
To change the authentication level of the TAPScheme authentication scheme, proceed as follows:
-
Select the Policy Configuration tab in the Oracle Access Management Console.
-
Expand the Shared Components node.
-
Expand the Authentication Schemes node.
-
Double-click TAPScheme.
-
On the Authentication Scheme page, change the authentication level.
-
Click Apply to submit the changes.
-
Dismiss the Confirmation window.
-
Close the page when you finish.
8.5.3 Setting Up Oracle Adaptive Access Manager and Access Manager Integration When Access Manager is in Simple Mode
To set up Oracle Adaptive Access Manager and Access Manager integration in Simple mode, proceed as follows.
8.5.3.1 Configuring Simple Mode Communication with Access Manager
Securing communication between OAM Servers and clients (WebGates) means defining the transport security mode for the OAP channel within the component registration page. The transport security communication mode is chosen during Access Manager installation. In Simple mode, the installer generates a random global passphrase initially, which can be edited as required later.
Simple mode is used if you have some security concerns, such as not wanting to transmit passwords as plain text, but you do not manage your own Certificate Authority (CA). In this case, Access Manager 11g Servers and WebGates use the same certificates, issued and signed by Oracle CA.
For information on configuring Access Manager for Simple mode communication, see Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
8.5.3.2 Setting OAAM Properties for Access Manager for Simple Mode
Follow the steps in Section 8.4.12, "Setting Up Access Manager TAP Integration Properties in OAAM." When you edit the oaam_cli.properties file, set the following properties in addition to ones specified in Table 8-7.
Table 8-8 Properties for Security Mode
| Parameters | Details |
|---|---|
|
oaam.uio.oam.security.mode |
This depends on the Access Manager security transport mode in use. The value can be 1 (for Open), 2 (for Simple), or 3 (for Cert). The default, if not specified, is 1 (Open). |
|
oam.uio.oam.rootcertificate.keystore.filepath |
The location of the Keystore file generated for the root certificate: DOMAIN_HOME/output/webgate-ssl/oamclient-truststore.jks. This is required only for security modes 2 (Simple) and 3 (Cert). |
|
oam.uio.oam.privatekeycertificate.keystore.filepath |
The location of the Keystore file generated for private key: DOMAIN_HOME/output/webgate-ssl/oamclient-keystore.jks. This is required for security modes 2 (Simple) and 3 (Cert) |
8.5.4 Configuring Identity Context Claims in the Access Manager and OAAM TAP Integration
Identity Context allows organizations to meet growing security threats by leveraging the context-aware policy management and authorization capabilities built into the Oracle Access Management platform. Identity Context secures access to resources using traditional security controls (such as roles and groups) as well as dynamic data established during authentication and authorization (such as authentication strength, risk levels, device trust and the like).
To use identity context claims in the Access Manager and OAAM TAP integration, follow the below steps:
-
In Domain-home
/config/fmw-config/oam-config.xml, search for the setting with the TAP partner name. You would have specified the TAP Partner name while registering the TAP partner for Access Manager. For example,OAAMPartner. Change the OAAM partner's TapTokenVersion fromv2.0tov2.1. -
Change the version setting on the OAAM side from
v2.0tov2.1by adding/editing a property through the OAAM Administration Console. To do this, proceed as follows:-
Log in to the OAAM Administration Console.
http://oaam_managed_server_host:oaam_admin_managed_server_port/oaam_admin
-
In the left pane, click Environment and double-click Properties. The Properties search page is displayed.
-
Search for property with name
oaam.uio.oam.dap_token.versionand set its value tov2.1. -
In case the property does not exist, add a new property with the name
oaam.uio.oam.dap_token.versionand the value asv2.1.
-
-
In TAP Scheme of the Access Management policy, add the following challenge parameter:
TAPOverrideResource=http://IAMSuiteAgent:80/oamTAPAuthenticate. To do that, proceed as follows:-
Log in to the Oracle Access Management Console:
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
Click the Policy Configuration tab to the left of the screen.
-
Expand the Authentication Schemes node.
-
Double-click TAPScheme authentication scheme.
-
To add another parameter to an existing parameter, position your cursor in the Challenge Parameter field and press Enter using your keyboard.
-
In the new line, add
TAPOverrideResource=http://IAMSuiteAgent:80/oamTAPAuthenticatefor a challenge parameter of TAPScheme.
-
8.5.5 Disabling OAAM Administration Console Protection
You can disable OAAM Administration Console protection by disabling the IAMSuiteAgent that protects it.
To do so, either the WLSAGENT_DISABLED system property or environment variable must be set to true for the servers on which the agent should be disabled.
For instructions on disabling the IAMSuiteAgent, see Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.
8.5.6 Disabling Step Up Authentication
If you want to disable the Step Up Authentication scenario, the following property has to be set to false through the OAAM Properties Editor:
oaam.uio.oam.integration.stepup.enabled
By default this property is set to true. If set to false, the user is prompted for credentials when he tries to access a higher protected resource after he had been authenticated for the lower protected resource.
8.6 Resource Protection Use Case
This use case illustrates how to set up the login and step up authentication flows.
8.6.1 Changing Authentication Level of TAPScheme
To change the authentication level, proceed as follows:
-
Log in to the Oracle Access Management Console.
http://oam_host:port/oamconsole
-
Click the Policy Configuration tab.
-
Click TAPScheme in the left panel.
-
In the TAPScheme Authentication Schemes page, increase the value for the Authentication Level. For example if the value is
2, change it to4.TAPScheme will be protecting the higher protected resource.
-
Click Apply to save the changes.
-
In the left pane, click OAMAdminConsoleScheme.
-
Ensure that the Authentication Level value is lower than that of TAPScheme.
OAMAdminConsoleScheme will be protecting the lower protected resource.
8.6.2 Removing OAAM Administration Console from Protected Higher Level Policy
In this example, the OAAM Administration Console is moved from the Protected Higher Level Policy.
-
Click Application Domains in the left pane.
-
In the Application Domains page, click Search, and in the search results, click IAM Suite
-
Click the Authentication Policies tab.
-
Click Protected Higher Level Policy.
-
In the Resources tab, remove /oaam_admin/** and click Apply to apply the change.
8.6.3 Creating a New Policy that Uses TAPScheme to Protect the Resource
Create a new policy with TAPScheme and protect OAAM as a higher protected resource.
-
Click the Create Authentication Policy button in the Authentication Policies tab.
-
In the Authentication Policy page, specify a policy name in the name field. For example,
TestPolicy. -
In Authentication Scheme, select TAPScheme from the pulldown.
-
Click Resources tab.
-
Click the Add icon to create a new resource.
-
Click Search in the Search window.
-
Select /oaam_admin/** as the resource.
-
Click Apply to create the authentication policy.
Now the higher protected resource is the OAAM Administration Console protected by TAPScheme and the lower protected resource is Oracle Access Management Console protected by OAMAdminConsoleScheme.
8.6.4 Creating an New OAAM User
For information on creating a user, see Section 8.4.4, "Creating the OAAM Admin Users and OAAM Groups."
8.6.5 Login Flow Example
This section presents an example of a Login flow where the user registers his virtual authentication device and challenge questions. The example is based on the setup that was performed in Section 8.6.1, "Changing Authentication Level of TAPScheme" through Section 8.6.4, "Creating an New OAAM User."
The Login flow is as follows:
-
Access the protected resource, the OAAM Administration Console, by entering its URL in a web browser.
The Access Manager user name page appears.
You are redirected to OAAM Server.
-
In the Access Manager user name page, enter the user name and click Continue.
-
The Password page appears with the textpad for you to enter the password.
-
Enter the password and click Enter.
-
Click Continue to begin registering a profile for the user.
-
Select your security device and click Continue.
-
Register challenge questions.
-
You are allowed to access the protected resource, the OAAM Administration Console.
8.6.6 Step Up Authentication Flow
This section presents an example of the Step Up Authentication flow for the user who registered his profile and was allowed access to the higher protected resource in Section 8.6.5, "Login Flow Example." The example is based on the setup performed in Section 8.6.1, "Changing Authentication Level of TAPScheme" through Section 8.6.4, "Creating an New OAAM User."
The Step Up Authentication flow is as follows:
-
Access the lower protected resource, the Oracle Access Management Console, by entering the URL in a web browser.
When you access the lower risk resource, you are shown the Oracle Access Management login page, which has the username and password on the same page.
-
Enter the credentials of the user who has registered a profile (see Section 8.6.5, "Login Flow Example") and click Login.
-
After providing credentials and being successfully authenticated, you now have access to the lower protected resource, the Oracle Access Management Console.
-
Access the higher protected resource, the OAAM Administration Console, by entering the URL in a web browser.
OAM Server does not present the Login page since you are already authenticated. However, OAAM will run its fraud detection policies.
-
After OAAM determines that the risk is low, you now have access to the higher protected resource, the OAAM Administration Console.
8.7 Troubleshooting Common Problems
This section describes common problems you might encounter in an Oracle Adaptive Access Manager and Access Manager integrated environment and explains how to solve them. It is organized by common problem types and contains the following topics
In addition to this section, review the Oracle Fusion Middleware Error Messages Reference for information about the error messages you may encounter.
For information about additional troubleshooting resources, see Section 1.7, "Using My Oracle Support for Additional Troubleshooting Information."
8.7.1 OAAM Basic Integration with Access Manager
This provides solutions for integration issues pertaining to OAAM Basic integration with Access Manager.
8.7.1.1 Internet Explorer 7 and OAAM Basic Integration with Access Manager
In the OAAM Basic integration with Access Manager, you are forwarded to the OAAM page when you access a protected resource.
If you are using Microsoft Internet Explorer 7, when you enter a username and click Submit, you are stuck on the next page (/oam/pages/oaam/handleLogin.jsp) instead of being redirected to the password page automatically.
To resolve this problem, you can use the following workaround:
Click the Continue link to take you to /oam/pages/oaam/handleJump.jsp?clientOffset=-7.
8.7.1.2 Access Manager and OAAM Integration and Changes in the Console
A error occurs during the OAAM Basic integration with Access Manager flow.
The OAAMEnabled value is configured incorrectly.
In an environment where OAAM Basic integration with Access Manager is enabled, the following entry OAAMEnabled under oam-config.xml must be set to true:
<Setting Name="OAAM" Type="htf:map">
<Setting Name="OAAMEnabled" Type="xsd:boolean">true</Setting>
</Setting>
...
If an error occurs in OAAM Basic integration with Access Manager flows, check the value of this flag. In certain environments (Windows) or scenarios, such as creating a new Oracle Internet Directory and associating it with the OAAMBasic scheme, the original flows might be broken. OAAM Basic integration with Access Manager does not work because the OAAMEnabled flag is reset to false.
8.7.1.3 OTP Challenge Not Supported in OAAM Basic integration with Access Manager
In OAAM Basic integration with Access Manager, during registration with Access Manager after registering the challenge questions, you are forwarded to a contact page to enter a mobile number.
In this mode of integration, with OTP unsupported, this page is not significant. You complete the registration by entering a mobile number in the following form, and Submit.
:09900502139
The OAAM Challenge SMS policy has been configured to run instead of the OAAM Challenge policy.
To resolve this issue, replace the OAAM Challenge SMS policy with the OAAM Challenge policy, to prevent a challenge flow request to OTP:
-
Search for "OAAM Challenge Policy"
-
Under Action Group, replace "OAAM Challenge SMS" with "OAAM Challenge" every where you find it.
-
Save the policy.
8.7.1.4 Using ConfigureOAAM WLST to Create the Datasource in OAAM Basic Integration with Access Manager
You can use the configureOAAM WLST command to create the data source, associate it as a target with the OAM Server, and the OAAMEnabled property in the oam-config.xml file. The syntax is as follows:
configureOAAM(dataSourceName,paramNameValueList)
where:
-
dataSourceNameis the name of the datasource to be created -
paramNameValueListis a comma-separated list of parameter name-value pairs. The format of each name-value pair is as follows:paramName='paramValue'
The mandatory parameters are:
-
hostName—The name of the database host -
port- the database port -
sid- the database identifier (database sid) -
userName- the OAAM schema name -
passWord- the OAAM schema password
The optional parameters are:
-
maxConnectionSize- maximum connection reserve time out size -
maxPoolSize- maximum size of connection pool
-
For example:
configureOAAM(dataSourceName = "MyOAAMDS", hostName = "host.us.co.com", port = "1521", sid = "sid", userName = "username", passWord = "password", maxConnectionSize = None, maxPoolSize = None, serverName = "oam_server1")
Note:
SID = requires the service name.
8.7.2 Login Failure
This provides solutions for login issues.
8.7.2.1 Non-ASCII Credentials
When using a non-ASCII user name or password in the native authentication flow, a message similar to the following is displayed:
Sorry, the identification you entered was not recognized. Please try again.
The non-ASCII characters are in the credentials.
To resolve the problem:
-
Set the PRE_CLASSPATH variable to
${ORACLE_HOME}/common/lib/nap-api.jar.For C shell:
setenv ORACLE_HOME "IAMSUITE INSTALL DIR" setenv PRE_CLASSPATH "${ORACLE_HOME}/common/lib/nap-api.jar"For bash/ksh shell:
export ORACLE_HOME=IAMSUITE INSTALL DIR export PRE_CLASSPATH="${ORACLE_HOME}/common/lib/nap-api.jar" -
Start the managed server related to
OAAM_SERVER.
8.7.2.2 Mixed Case Logins
After successful authentication on Access Manager and Oracle Adaptive Access Manager, a registered user was asked to register his profile again after he entered his mixed-case user name in a different case combination than what he registered.
The user name is case-sensitive. By default, if a user enters a mixed-case user name in a case combination that is different from the registered user, the OAAM Server will consider the user to be unregistered. For example, if user userxy tries to log in by entering user name userXY, he will be asked to register his profile again.
To ensure that logins are successful on both OAM and OAAM servers, you must configure the OAAM Server to consider user names as case-insensitive. To achieve this set the following property:
bharosa.uio.default.username.case.sensitive=false
For information on setting properties in Oracle Adaptive Access Manager, see "Using the Property Editor" in Oracle Fusion Middleware Administrator's Guide for Oracle Adaptive Access Manager.
8.7.2.3 Cookie Domain Definition
Incorrect value of the cookie domain in your configuration can result in login failure.
For correct WebGate operation, ensure that the property oaam.uio.oam.obsso_cookie_domain is set to match the corresponding value in Access Manager.
8.7.3 Identity Store
This provides solutions for identity store issues.
8.7.3.1 Username Attribute Incorrect Setting
The user experiences a login failure.
If the username attribute in the identity store is not cn, a login failure occurs.
To fix this problem, proceed as follows:
-
Log in to the Oracle Access Management Console:
http://oam_adminserver_host:oam_adminserver_port/oamconsole -
In the left panel, click TAPScheme.
-
Double-click TAPScheme authentication scheme.
-
In the TAPScheme page, add the challenge parameter
MatchLDAPAttributeand set the value to the username attribute specified in your identity store. The challenge parameter is case-sensitive so ensure that you have enter it correctly.For example, you could set it to
uid,mail,cn, and so onIf the username attribute is
uid, you would addMatchLDAPAttribute=uidNote:
To add another parameter to an existing parameter, you must position your cursor in the Challenge Parameter field and press Enter using your keyboard.
-
Click Apply to submit the change.
8.7.3.2 In the Access Manager and OAAM Integration TAP Could Not Modify User Attribute
Authentication succeeds but the final redirect fails with the following errors:
Module oracle.oam.user.identity.provider
Message Principal object is not serializable; getGroups call will result in
an extra LDAP call
Module oracle.oam.engine.authn
Message Cannot assert the username from DAP token
Module oracle.oam.user.identity.provider
Message Could not modify user attribute for user : cn, attribute :
userRuleAdmin, value : {2} .
In integration scenarios coupled with multiple identity stores, the user identity store that is set as the Default Store is used for authentication and assertion.
For the Access Manager and OAAM integration which uses the TAP, the assertion for the TAPScheme Authentication scheme is made against the Default Store. In this case the backend channel authentication made against the LDAP module uses a specific user identity store (OID, for example). When the user name is returned to Access Manager, the assertion occurs against the Default Store (not the same OID that was used for the authentication).
Note:
For Session Impersonation, the Oracle Internet Directory instance that is used for the user and grants must be the Default Store.
If you change the Default Store to point to a different store, ensure that TAPScheme also points to same store.
8.7.3.3 No Synchronization Between Database and LDAP
Registered status records remain in the OAAM database even if registered users are removed from LDAP. When the user is added to LDAP again, the old image, phrase, and challenge questions are used, because the OAAM database and LDAP are not synched.
8.7.4 Miscellaneous
This section provides solutions and tips for miscellaneous issues.
8.7.4.1 Integration Failure Due to Network Delay
Increase TokenValiditySeconds using Oracle Access Management Console if the integration fails.
-
Log in to the Oracle Access Management Console:
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
In the left panel, click TAPScheme.
-
In the TAPScheme page, add the challenge parameter
TotalValiditySecondsand set the value to the desired number. The default value is 1 second. The challenge parameter is case-sensitive so ensure that you have enter it correctly.For example,
TotalValiditySeconds=4Note:
To add a parameter when there are existing parameters, you must position your cursor in the Challenge Parameter field and press Enter using your keyboard, and then enter the new parameter.
-
Click Apply to apply the changes.
8.7.4.2 Changing the TAP Token Version to 2.1
The oam-config.xml file contains all Access Manager-related system configuration data and is located in the DOMAIN_HOME/config/fmwconfig directory.
-
Open the
oam-config.xmlfile in a text editor.vi DOMAIN_HOME/config/fmwconfig/oam-config.xml -
Search for
OAAMPartner. -
Change the value of the
TapTokenVersionfromv2.0tov2.1. -
Save the changes.
:wq!
-
Log in to the OAAM Administration Console.
http://oaam_managed_server_host:oaam_admin_managed_server_port/oaam_admin
-
In the left panel, click Properties under the Environment node.
-
Click the New Property button in the Properties page.
-
Specify the new property as:
Name:
oaam.uio.oam.dap_token.versionValue:
v2.1 -
Click Create.
-
Log in to the Oracle Access Management Console:
http://oam_adminserver_host:oam_adminserver_port/oamconsole
-
In the left pane, double-click the TAPScheme authentication scheme.
-
In the TAPScheme page, add the challenge parameter
TAPOverrideResource=http://IAMSuiteAgent:80/oamTAPAuthenticate. The challenge parameter is case-sensitive so ensure that you have enter it correctly.Note:
To add a parameter when there are existing parameters, you must position your cursor in the Challenge Parameter field and press Enter using your keyboard, and then enter the new parameter.
-
Click Apply to apply the changes.
8.7.4.3 Resource Protected by OAAMAdvanced Scheme Is Not Accessible in Access Manager 11.1.1.4.0 and OAAM 11.1.1.5.0 Integration
You cannot access a resource protected by the OAAMAdvanced authentication scheme in an Access Manager 11.1.1.4.0 and OAAM 11.1.1.5.0 integration.
In an Access Manager 11.1.1.4.0 and OAAM 11.1.1.5.0 integration, you must set the WebGate password for OAAM and several parameters in addition to those documented in this chapter in order for the integration to work properly.
To resolve this problem:
-
Set the WebGate password for OAAM.
-
Set
oaam.uio.oam.authenticate.withoutsessiontofalse. By default, this is set totrue.
8.7.4.4 Additional Properties to Set If Using OAAMAdvanced Scheme
If you are using the OAAMAdvanced scheme in OAAM Advanced integration with Access Manager, ensure that these properties are set:
-
For Access Management 11g Release 1 (11.1.1) and earlier:
oaam.uio.oam.authenticate.withoutsession = false
-
For Access Management 11g and 10g:
oracle.oaam.httputil.usecookieapi = true
8.7.4.5 Accessing LDAP Protected Resource as a Test
When setting up the environment, you may want to first verify that you can access a page protected by Access Manager using the LDAP authentication scheme. If you cannot access the page, try to resolve this issue before proceeding with the configuration.