11 Managing Users
The user management feature in Oracle Identity Manager includes creating, updating, deleting, enabling and disabling, locking, and unlocking of user accounts. This feature is described in the following sections:
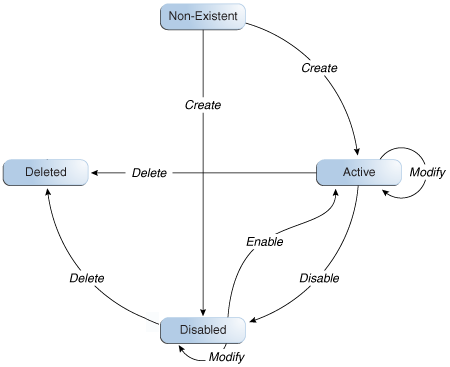
11.1 User Lifecycle
User lifecycle is a term to describe the process flow of how a user entity is created, managed, and terminated in the system based on certain events or time factors.
A user entity goes through various stages in the lifecycle. The stages are non-existent, disabled, active, and deleted. Figure 11-1 depicts the different lifecycle stages, all possible transitions, and the operations that set up those transitions:
There is a possibility of process rules or business requirements being defined for each transition of the user lifecycle. You can use the sample scenarios listed in Table 11-1 to establish the link between user lifecycle transitions and business objectives.
Table 11-1 User Life Cycle and Business Objectives Sample Scenarios
| Current State | Operation | Sample Scenario | Process Description |
|---|---|---|---|
|
Non-existent |
Create |
HR enters user profile information for a new hire. If the new hire is not introduced to the system immediately, then HR sets a future start date for the user. |
If the start is not a future date then the user is introduced into the system in an Active state.If the Start Date is in future then the create process creates the user in a disabled state. |
|
Disabled |
Enable |
User's start date is in effect. The system initiates provisioning for the new hire. |
User is marked enabled in the system and the user is now able to login and use the system. By default, all necessary memberships and accounts are established as part of the workflow. |
|
Active |
Modify |
User is promoted to a new position. As a result, HR changes the job title of the user. |
New resources are provisioned to the user, and old irrelevant resources are deprovisioned from the user. |
|
Active |
Disable |
User takes one year sabbatical from the company. HR manually disables the user on the last working day of the user. The user re-joins the company after some period. HR can make the user Active again. |
User is marked disabled in the system, and the user is no longer able to login to the system. The disabled users can be made Active again. |
|
Active |
Deleted |
User retires from the company. HR manually deletes the user on the last working day of the user. |
User is marked deleted in the system, and the user is no longer able to login to the system. By default, all users' accounts are deprovisioned as part of the workflow. |
The following concepts are integral to user lifecycle management:
11.1.1 OIM Account
OIM Account is an abstraction representing a means to be authenticated to access Oracle Identity Manager. In Oracle Identity Manager, the cardinality of relationship between user and OIM account is one-to-one. By default, users are associated with OIM accounts that allow users to access Oracle Identity Manager. However, there may be users who do not need to access Oracle Identity Manager, and therefore, may not be provisioned with an OIM account.
Some user operations, such as lock and unlock, are explicitly account operations. When locking or unlocking a user, you lock or unlock the user's OIM account.
In Oracle Identity Manager, each user has a Design Console Access attribute that controls the OIM account of the user. If the Design Console Access option for a user is selected in the UI, then the user is End-User Administrator. If this option is not selected, then the user is an End-User.
11.1.2 Organization
Organization is a logical container for authorization and permission data. A user in Oracle Identity Manager must belong to one organization only. For detailed information about organizations in Oracle Identity Manager, see Chapter 13, "Managing Organizations".
11.1.3 Role
Oracle Identity Manager provides easy and controlled privilege management through roles. Roles are named groups of related privileges that you grant to users or other roles. Roles are designed to ease the administration of end-user system and schema object privileges. For detailed information about roles, see Chapter 12, "Managing Roles".
11.2 User Entity Definition
Attributes are defined for the user entity in Oracle Identity Manager. These attributes are the same for all entities. You can add your own attributes to the user entity.
For each attribute of an entity, the following properties are defined in Oracle Identity Manager:
-
Attribute Name: The name of the attribute.
-
Type: Indicates the type of data in the attribute. Supported types are string, number, date, and boolean.
-
Properties: For each attribute, the properties such as Use in bulk (specifies whether the attribute is available in bulk operations), Encrypt (determines whether the attribute must be encrypted), Searchable (determines whether the attribute can be searched by a user), and so on can be defined.
See Also:
"Configuring Custom Attributes" in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for more information about adding custom attributes and their properties
Table 11-2 lists the attributes defined for the user entity in Oracle Identity Manager:
Table 11-2 Attributes Defined for User Entity
| Attribute Name | Category | Description | Data Type | Properties | Lookup Code and its Entries |
|---|---|---|---|---|---|
|
usr_key |
Account Settings |
The GUID of the user. It is autogenerated when the user is created. |
number |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: Yes Max-Size: 19 Visible: No Display-Type: ENTITY |
N/A |
|
act_key |
Basic User Information |
The GUID of the organization to which the user belongs. This is a mandatory field. |
number |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 19 Visible: Yes Display-Type: ENTITY |
N/A |
|
Last Name |
Basic User Information |
The last name of the user. This is a mandatory field. |
string |
Required: Yes System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
First Name |
Basic User Information |
The first name of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Middle Name |
Basic User Information |
The middle name of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Display Name |
Basic User Information |
The display name of the user. If not specified, then it is autogenerated while creating the user. |
string |
Required: No MLS: No Multi-represented: Yes System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 382 Visible: Yes Display-Type: TEXT |
N/A |
|
Xellerate Type |
Basic User Information |
The type of end-user or administrator. |
string |
Required: Yes System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 30 Visible: Yes Display-Type: CHECKBOX |
Lookup.Users.XellerateType End-User End-User Administrator |
|
usr_password |
Account Settings |
The password of the user. It is stored as an encrypted value. |
string |
Required: Yes System-Controlled: No Encryption: Encrypt User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 128 Visible: Yes Display-Type: SECRET |
N/A |
|
usr_disabled |
Account Settings |
Indicates whether the user is disabled or enabled. 0 indicates that the user is enabled. 1 Indicates that the user is disabled. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: Yes Read-Only: Yes Max-Size: 1 Visible: Yes Display-Type: CHECKBOX |
N/A |
|
Status |
Account Settings |
The status of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: Yes Max-Size: 25 Visible: Yes Display-Type: LOV |
Lookup.WebClient.Users.Status Active Disabled Deleted Disabled Until Start Date |
|
Role |
Basic User Information |
The type of user in the system. |
string |
Required: Yes System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 255 Visible: Yes Display-Type: LOV |
Lookup.Users.Role Full-Time Part-Time Temp Intern Consultant EMP CWK NONW OTHER Contractor |
|
User Login |
Account Settings |
The login ID of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 256 Visible: Yes Display-Type: TEXT |
N/A |
|
usr_manager_key |
Basic User Information |
The GUID of the user's manager. |
number |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 19 Visible: Yes Display-Type: ENTITY |
N/A |
|
Start Date |
Account Effective Dates |
The start date of the user. |
date |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: - Visible: Yes Display-Type: DATE_ONLY |
N/A |
|
End Date |
Account Effective Dates |
The end date of the user. |
date |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: - Visible: Yes Display-Type: DATE_ONLY |
N/A |
|
usr_provisioning_date |
Provisioning Dates |
The date on which the user profile has been created in Oracle Identity Manager. |
date |
Required: No System-Controlled: No Encryption: Clear Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: - Visible: Yes Display-Type: DATE_ONLY |
N/A |
|
usr_deprovisioning_date |
Provisioning Dates |
The date when the resources will be deprovisioned from the user. |
date |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: - Visible: Yes Display-Type: DATE_ONLY |
N/A |
|
usr_provisioned_date |
System |
The date when the resources have been provisioned to the user. |
date |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
usr_deprovisioned_date |
System |
The date when the resources are deprovisioned from the user. |
date |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
|
Basic User Information |
The e-mail address of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 256 Visible: Yes Display-Type: TEXT |
N/A |
|
usr_locked |
Account Settings |
Indicates whether the user account is locked or unlocked. The value 0 indicates that the account is unlocked. The value 1 indicates that the account is locked. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Update: No Read-Only: Yes Max-Size: 1 Visible: Yes Display-Type: LOV |
Users.Lock User 0 1 |
|
Locked On |
Lifecycle |
The date on which the user account has been locked. |
date |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
Automatically Delete On |
Lifecycle |
The date on which the user account will be automatically deleted. |
date |
Required: No System-Controlled: No Encryption: Clear Searchable: Yes Bulk-Updatable: Yes Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
Manually Locked |
Lifecycle |
Indicates whether the user account has been automatically or manually locked. 1 indicates that the account has been manually locked by an administrator. 0 indicates that the account has been automatically locked, for instance, on exceeding the maximum number of login attempts with incorrect password. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: TEXT |
N/A |
|
usr_login_attempts_ctr |
System |
The number of times the user has tried logging in with incorrect password. It is set to 0 at every successful login. |
number |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 19 Visible: No Display-Type: NUMBER |
N/A |
|
usr_create |
System |
The date on which the user has been created. |
date |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
usr_update |
System |
The date on which the user has been last updated. |
date |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
usr_timezone |
Preferences |
The timezone preference of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 100 Visible: Yes Display-Type: TIME_ZONE |
N/A |
|
usr_locale |
Preferences |
The locale preference of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 100 Visible: Yes Display-Type: LOV |
Notification.Languages English French German Italian Spanish Brazilian Portuguese Japanese Korean Simplified Chinese Traditional Chinese Arabic Czech Danish Dutch Finnish Greek Hebrew Hungarian Norwegian Polish Portuguese Romanian Russian Slovak Swedish Thai Turkish |
|
usr_pwd_cant_change |
System |
This field is currently not used. |
string |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: CHECKBOX |
N/A |
|
usr_pwd_must_change |
System |
This field is currently not used. The value 0 indicates that the password is not required to be changed. The value 1 mandates that the user changes the password. |
string |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: CHECKBOX |
N/A |
|
usr_pwd_never_expires |
System |
This field is currently not used. The value 0 indicates that the password will expire. The value 1 indicates that password never expires. |
string |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 1 Visible: Yes Display-Type: CHECKBOX |
N/A |
|
usr_pwd_expire_date |
System |
The date on which the password will expire. Valid if Password Never Expires is 0. |
date |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
usr_pwd_warn_date |
System |
The date after which the user will be warned to change the password. |
date |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Update: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
usr_pwd_expired |
System |
Indicates whether the user password has expired. If so, then the password must be reset. The value 0 indicates that password has not expired. The value 1 indicates that password has expired. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Update: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: CHECKBOX |
N/A |
|
usr_pwd_warned |
System |
Indicates whether the user has been warned to change the password. 0 indicates that the user has not been warned to change the password yet. 1 indicates that the user has been warned to change the password. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: CHECKBOX |
N/A |
|
usr_pwd_reset_attempts_ctr |
System |
The number of times the user has tried resetting the password with incorrect answers to challenge questions. It is set to 0 at every successful reset password. |
number |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 19 Visible: No Display-Type: NUMBER |
N/A |
|
usr_change_pwd_at_next_logon |
System |
Indicates whether the user must change his password at next login. The value 1 indicates that the user must reset password at next login. The value 0 indicates that user does not need to reset password at next login. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Update: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: CHECKBOX |
N/A |
|
usr_data_level |
System |
Indicates the kind of operation, such as add, modify, or delete, supported on this record. The possible values for this column are: 0: Indicates that this row can be updated or deleted 1: Indicates that this row cannot be updated and deleted 2: Indicates that the row can only be modified and cannot be deleted 3: Indicates that the row can only be deleted and cannot be modified |
string |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: TEXT |
N/A |
|
usr_pwd_min_age_date |
System |
If set, then it indicates the date before which the user password cannot be changed. |
date |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: - Visible: No Display-Type: DATE_ONLY |
N/A |
|
usr_createby |
System |
The GUID of the user who created this user. |
number |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 19 Visible: No Display-Type: ENTITY |
N/A |
|
usr_updateby |
System |
The GUID of the user who updated this user. |
number |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 19 Visible: No Display-Type: ENTITY |
N/A |
|
usr_created |
System |
This is not currently used in Oracle Identity Manager. |
date |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 19 Visible: No Display-Type: DATE_ONLY |
N/A |
|
usr_policy_update |
System |
This is used to re-evaluate the user's policies. To re-evaluate object policies for any user to whom the current policy applies, evaluate the UPP and UPD tables to get list of users for the current policy. For each user found, set the policy_update flag. Attach as a post-insert, post-update and post_delete event handler to tcPOP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: Yes Read-Only: Yes Max-Size: 1 Visible: No Display-Type: TEXT |
N/A |
|
Country |
Other User Attributes |
The country of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 100 Visible: Yes Display-Type: TEXT |
N/A |
|
Department Number |
Other User Attributes |
The department number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Description |
Other User Attributes |
The description of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 2000 Visible: Yes Display-Type: TEXT |
N/A |
|
Common Name |
Other User Attributes |
The common name of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 240 Visible: Yes Display-Type: TEXT |
N/A |
|
Employee Number |
Other User Attributes |
The employee number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Fax |
Other User Attributes |
The FAX number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: Yes Display-Type: TEXT |
N/A |
|
Generation Qualifier |
Other User Attributes |
The Generation Qualifier for the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: Yes Display-Type: TEXT |
N/A |
|
Hire Date |
Other User Attributes |
The hire date of the user. |
date |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: - Visible: Yes Display-Type: DATE_ONLY |
N/A |
|
Home Phone |
Other User Attributes |
The home phone number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: Yes Display-Type: TEXT |
N/A |
|
Locality Name |
Other User Attributes |
The locality name of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Mobile |
Other User Attributes |
The mobile number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: Yes Display-Type: TEXT |
N/A |
|
Pager |
Other User Attributes |
The pager number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: Yes Display-Type: TEXT |
N/A |
|
Home Postal Address |
Other User Attributes |
The home postal address of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 256 Visible: Yes Display-Type: TEXT |
N/A |
|
Postal Address |
Other User Attributes |
The postal address of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 256 Visible: Yes Display-Type: TEXT |
N/A |
|
Postal Code |
Other User Attributes |
The postal code of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 230 Visible: Yes Display-Type: TEXT |
N/A |
|
PO Box |
Other User Attributes |
The PO box number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: Yes Display-Type: TEXT |
N/A |
|
State |
Other User Attributes |
The state of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Street |
Other User Attributes |
The street name in the user's address. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Telephone Number |
Other User Attributes |
The telephone number of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: Yes Display-Type: TEXT |
N/A |
|
Title |
Other User Attributes |
The title of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
Initials |
Other User Attributes |
The initials of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 10 Visible: Yes Display-Type: TEXT |
N/A |
|
Password Generated |
System |
This flag indicates whether the password has been autogenerated for the user. |
string |
Required: No System-Controlled: Yes Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: Yes Max-Size: 1 Visible: No Display-Type: TEXT |
N/A |
|
LDAP Organization |
Other User Attributes |
User organization name in LDAP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
LDAP Organization Unit |
Other User Attributes |
User organization unit in LDAP, such as department or any subentity of a larger entity. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 80 Visible: Yes Display-Type: TEXT |
N/A |
|
LDAP GUID |
Other User Attributes |
User global unique identifier in LDAP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 256 Visible: Yes Display-Type: TEXT |
N/A |
|
LDAP DN |
Other User Attributes |
User distinguished name in LDAP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 256 Visible: Yes Display-Type: TEXT |
N/A |
|
FA Language |
Preferences |
Language of the user for LDAP environment. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 100 Visible: No Display-Type: TEXT |
NA |
|
Embedded Help |
Other User Attributes |
Indicates whether to suppress the help popups on rollover. This attribute is not interpreted by Oracle Identity Manager and is used to persist values in LDAP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 10 Visible: No Display-Type: LOV |
Lookup.Users.EmbeddedHelp true false |
|
Number Format |
Other User Attributes |
The number format preference of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 30 Visible: No Display-Type: LOV |
Lookup.Users.NumberFormat #,##0.##[.,] #,##0.###[\u00A0,] #,##0.### #,##0.###;#,##0.###- #,##0.###[.,] #,##0.###;(#,##0.###)[.,] #,##0.##[\u00A0,] #,##0.###['.] #,##0.###[',] |
|
Date Format |
Other User Attributes |
The date format preference of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: No Display-Type: LOV |
Lookup.Users.DateFormat MM-dd-yyyy MM-dd-yy MM.dd.yyyy MM.dd.yy MM/dd/yyyy MM/dd/yy M-d-yyyy M-d-yy M.d.yyyy M.d.yy M/d/yyyy M/d/yy dd-MM-yyyy dd-MM-yy d-M-yyyy d-M-yy dd.MM.yyyy dd.MM.yy d.M.yyyy d.M.yy dd/MM/yyyy dd/MM/yy d/M/yyyy d/M/yy yyyy-MM-dd yy-MM-dd yyyy-M-d yy-M-d yyyy.MM.dd yy.MM.dd yyyy.M.d yy.M.d yy. M. d yyyy/MM/dd yy/MM/dd yyyy/M/d yy/M/d |
|
Time Format |
Other User Attributes |
The time format preference of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: No Display-Type: LOV |
Lookup.Users.TimeFormat HH.mm HH.mm.ss HH:mm HH:mm:ss H:mm H:mm:ss H.mm H.mm.ss a hh.mm a hh.mm.ss a hh:mm a hh:mm:ss ah:mm ah:mm:ss hh.mm a hh.mm.ss a hh:mm a hh:mm:ss a |
|
Currency |
Other User Attributes |
The preferred currency code of the user. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: No Display-Type: LOV |
Lookup.Users.Currency |
|
Font Size |
Other User Attributes |
The preferred font size of the user, such as large or medium. This is related to the Accessibility feature. This attribute is not interpreted by Oracle Identity Manager and is used to persist values in LDAP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 10 Visible: No Display-Type: LOV |
Lookup.Users.FontSize LARGE MEDIUM |
|
Color Contrast |
Other User Attributes |
The preferred color contrast of the user, such as standard or high. This is related to the Accessibility feature. This attribute is not interpreted by Oracle Identity Manager and is used to persist values in LDAP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 10 Visible: No Display-Type: LOV |
Lookup.Users.ColorContrast STANDARD HIGH |
|
Accessibility Mode |
Other User Attributes |
The preferred accessibility feature of the user, such as Screen Reader Optimized or Standard Accessibility. This attribute is not interpreted by Oracle Identity Manager and is used to persist values in LDAP. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: No Bulk-Updatable: No Read-Only: No Max-Size: 20 Visible: No Display-Type: Text |
Lookup.Users.AccessibilityMode screenReader inaccessible default |
|
FA Territory |
Preferences |
Region of the user for LDAP environment. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: No Read-Only: No Max-Size: 100 Visible: No Display-Type: LOV |
NA |
|
User Name Preferred Language |
Preferences |
The preference language of the user used to show only the display name of the user in that language. Note: The preference can be stored in Oracle Identity Manager, but it is not honored on Oracle Identity Manager UI. |
string |
Required: No System-Controlled: No Encryption: Clear User-Searchable: Yes Bulk-Updatable: Yes Read-Only: No Max-Size: 20 Visible: No Display-Type: LOV |
Select MLS_LOCALE_CODE as USR_NAME_PREFERRED_LANG from mls_locale where locale_flag=0 OR locale_flag 1 order by mls_locale_code asc |
11.3 Default User Accounts
Table 11-3 lists the default user accounts that are created in Oracle Identity Manager.
Table 11-3 Default User Accounts
| Account | Description |
|---|---|
|
XELSYSADM |
This account is the Oracle Identity Manager administrator (super-user) and is created during installation. You create a password for this account during installation. To change the password at any later point in time after installation, see "Changing Oracle Identity Manager Administrator Password" in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager. |
|
WEBLOGIC |
This account is used for integrating SOA and Oracle Identity Manager by using the 'User Role Provider' implementation. When SOA is reconfigured to use LDAP-based user-role provider, Oracle Identity Manager does not require this account. This account is created during installation. You create a password for this account during installation. To change the user name of this account at any later point in time after installation, see "Enabling Oracle Identity Manager to Connect to SOA Using the Administrative Users Provisioned in LDAP" in Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management. |
|
OIMINTERNAL |
This account is set to a'run as' user for Message Driven Beans (MDBs) executing JMS messages. This account is created during installation and is used internally by Oracle Identity Manager. The password of this account is set to a single space character in Oracle Identity Manager database to prevent user login through Oracle Identity Manager Design console or Oracle Identity Manager System Administration Console. Do not change the user name or password of this account. |
11.4 User Management Tasks
You can perform the following user management tasks by using Oracle Identity Self Service:
Note:
For more information about the tasks listed in this section, see "Security Architecture" in Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
11.4.1 Searching Users
The search operation lets you search user entities based on the search criteria that you specify. Each search criterion consists of:
-
The attribute to search against
-
The search operators, such as Equals and Starts with
-
The values to search for
To search for users:
-
Log in to Identity Self Service.
-
On the left pane, under Administration, select Users. The Manage Users page is displayed.
-
Select any one of the following options:
-
All: On selecting this option, the search is performed with the AND condition. This means that the search operation is successful only when all the search criteria specified are matched.
-
Any: On selecting this option, the search is performed with the OR condition. This means that the search operation is successful when any search criterion specified is matched.
-
-
In the searchable user attribute fields, such as User Login, specify a value. You can include wildcard characters (*) in the attribute value.
For some attributes, select the attribute value from the list. For example, to search all users with locked accounts, select Locked from the Account Status list.
-
For each attribute value that you specify, select a search operator from the list. The following search operators are available:
-
Starts with
-
Ends with
-
Equals
-
Does not equal
-
Contains
-
Does not contain
The search operator can be combined with wildcard characters to specify a search condition. The asterisk (*) character is used as a wildcard character. For example, you can specify the value of the User Login attribute to be Jo* as the search criteria, and select Equals as the search operator. The users with login names that begins with Jo are displayed.
-
-
To add a searchable user attribute to the Manage Users page, click Add Fields, and select the attribute from the list of attributes.
For example, if you want to search all users with the Country attribute as US, then you can add the Country attribute as a searchable field and specify a search condition.
Note:
You can configure the attributes that are searchable. The attributes available for search must be a subset of the attributes defined for the user entity that are marked with the Searchable = Yes property.
-
Optionally click Reset to reset the search conditions that you specified. Typically, you perform this step to remove the specified search conditions and specify a new search condition.
-
Click Search. The search results is displayed in a tabular format, as shown in Figure:
-
If you want to hide columns in the search results table, then perform the following steps:
-
Click View on the toolbar, select Columns, Manage Columns. The Manage Columns dialog box is displayed.
-
From the Visible Columns list, select the columns that you want to hide.
-
Click the left arrow icon to add the columns in the Hidden Columns list.
-
Click OK. The selected columns are not displayed in the search results. A status message displays along the bottom of the search table to identify how many columns are currently hidden. Figure shows that three columns are hidden:
-
11.4.1.1 Operations on Search Results
This section describes the operations that you can perform based on selection of row(s) in the search results table. It is divided into single selection operations and bulk or multiple selection operations.
You can perform the following single selection operations by selecting a user from the search results table:
-
View detail
-
Modify, only if the user status is active
-
Enable, only if the user status is disabled
-
Disable, only if the user status is enabled
-
Lock, only if the selected user's account is unlocked
-
Unlock, only if the selected user's account is locked
-
Reset password
-
Delete
You can perform the following bulk or multiple selection operations by selecting multiple users from the search results table:
-
Modify
-
Enable, only if the user status is disabled
-
Disable, only if the user status is enabled
-
Lock, only if the selected user's account is unlocked
-
Unlock, only if the selected user's account is locked
-
Delete
Note:
All bulk operations and single operations can be a direct operation or generate a request which is subject to approval, based on the authorization privileges you have determined by the admin roles of the user.
11.4.2 Creating a User
You can create a new user in Oracle Identity Manager by using the Create User page. You can open this page only if you are authorized to create users as determined by the authorization policy on the Create User privilege on any organization in Oracle Identity Manager.
Note:
The create user operation can be a direct operation or generate a request, which is subject to approval, based on the authorization privileges you have.
To create a user:
-
In Identity Self Service, under Administration, click Users. The Search Users page is displayed.
-
From the Actions menu, select Create. Alternatively, you can click Create on the toolbar. The Create User page is displayed with input fields for user profile attributes.
-
Enter details of the user in the Create User page. Table 11-4 describes the fields in the Create User page:
Table 11-4 Fields in the Create User Page
Section Field Description Justification and Effective Date
Justification
Justification for creating the user.
Effective Date
Date on which the user must be created.
Basic User Information
First Name
First name of the user.
Middle Name
Middle name of the user.
Last Name
Last name of the user.
Email
E-mail address of the user.
Manager
The reporting manager of the user.
Organization
The organization to which the user belongs. This is also known as the home organization.
User Type
The type of employee, such as consultant, contractor, contingent worker, employee, full-time employee, intern, non-worker, other, part-time employee, or temporary.
Display Name
It can have localized values, which can be added by clicking Manage Localizations, and selecting from a list of languages. Display Name is available in 33 languages.
Account Settings
User Login
The user name to be specified for logging in to the Administration Console.
Password
The password to be specified for logging in to the Administration console.
Confirm Password
Re-enter the password to be specified for logging in to the Administration console.
Account Effective Dates
Start Date
The date when the user will be activated in the system.
End Date
The date when the user will be deactivated in the system.
Provisioning Dates
Provisioning Date
Date when user is getting provisioned into the system.
Deprovisioning Date
Date when the user is getting deprovisioned from the system.
Contact Information
Telephone Number
The telephone number of the user.
Home Phone
The telephone number of the user's residence.
Home Postal Address
The postal address of the user's residence.
Fax
The fax number of the user.
Mobile
The mobile number of the user.
Pager
The pager number of the user.
Postal Address
The postal address of the user.
Postal Code
The postal code number of the user's address.
PO Box
The post box number of the user's address.
State
The state name of the user.
Street
The street name where the user resides.
Country
The country where user resides.
Preferences
Locale
The locale code of the user.
Timezone
The timezone of the user.
Other Attributes
Common Name
The common name of the user.
Department Number
The department number of the user.
Employee Number
The employee number of the user.
Generation Qualifier
Whether the user qualifies the generation.
Hire Date
The hiring date of the user.
Locality Name
The name of the locality where user resides.
Initials
The initials of the user.
Title
The title for the user.
-
Click Submit. A message is displayed stating that the user is created successfully.
Tip:
Users can be created by any one of the following methods:
-
By using Oracle Identity Administration
-
By self registration
-
By using SPML Web service or APIs
For all the above methods, Oracle Identity Manager uses the default password policy or Password Policy against Default Rule. If you want to use a different password policy, then you must attach the new password policy to the default rule by using Oracle Identity System Administration. To do so, see "Managing Password Policies" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
11.4.3 Viewing User Details
The view user operation allows you to view detailed user profile information in the User Details page. You can open this page if you are authorized to view the user's profile as determined by the authorization policy through the View User Details privilege.
To display user details:
-
In Identity Self Service, under Administration, click Users. The Search Users page is displayed.
-
Search for the user for which you want to display the details.
-
In the search results table, click the user login name in the User Login column. The User Details page is displayed.
The user details are displayed in the following tabs:
-
The Attributes Tab: Displays the attribute profile that includes details about basic user information, account effective dates, and provisioning dates. For more details, see "Editing User Attributes".
-
The Roles Tab: Displays a list of roles to which the user belongs. You can click each role to display summary information about the role.
In the Roles tab, you can assign roles to the user and remove roles from the user. For more details, see "Adding and Removing Roles".
-
The Entitlements Tab: Displays a list of entitlements for the user. You can click each entitlement to display a summary of the entitlement.
In the Entitlements tab, you can request for entitlements and remove entitlements from the user. For more details, see "Adding and Removing Entitlements".
-
The Accounts Tab: Displays a list of accounts for the user. You can click each account to display a summary of the account.
Typical tasks you perform in this tab are request for an account, modify and remove accounts, mark an account as primary, and disable and enable accounts. For more details, see "Modifying Accounts".
-
The Direct Reports Tab: Displays a read-only table of users for whom the user is set as the manager. In other words, this tab lists the direct reportees of the user. For each user in the table, it displays the following:
-
Display Name
-
User Login
-
Status
-
Organization
If you select a row in the table, then summary information about the direct reportee is displayed at the bottom.
Direct reports allows you to open the user details of the direct reportees. To do so, select a row in the table of direct reportees, and click the open icon on the toolbar.
-
-
The Admin Roles Tab: Displays a list of admin roles assigned to the user. You can select an admin role to display a summary of the admin role.
Using the admin role detail information, you can select or deselect the include sub-orgs option. When this option is selected, it specifies that the admin role is applicable to the users of the organization and all the suborganizations of the organization. When this option is not selected, it specifies that the admin role is applicable to the users of the organization only. See "Managing Admin Roles" for more information.
11.4.4 Modifying Users
You can perform administrative user modification tasks from the user details. The modification is broken up across the different tabs in the page that displays user details, which means that modifications done in each tab are independent of each other and must be saved individually. The modifications you can perform in each tab is outlined in the following sections:
Note:
The modify user operation can be a direct operation or generate a request, which is subject to approval, based on the authorization privileges you have.
11.4.4.1 Editing User Attributes
To edit the attributes of a user:
-
In the Users section under Administration, search for the user for which you want to modify the attributes.
-
Select the user in the search results table.
-
Modify the user in one of the following ways:
-
Click Edit on the toolbar.
-
From the Actions menu, select Edit.
-
Click the user login of the user record that you want to disable. On the User Details page, click Modify User on the toolbar.
-
-
In the Modify User page, change values of the attributes in the respective fields as required.
-
Click Submit. The modify attribute operation is completed successfully.
11.4.4.2 Adding and Removing Roles
In the Roles tab of the User Details page, you can add and remove roles. To assign roles for a user:
-
In the User Details page, click the Roles tab. The Roles tab is displayed with the list of roles assigned to the user.
-
From the Actions menu, select Request. Alternatively, you can click Request Roles on the toolbar. The Catalog page is displayed.
-
Click the search icon next to the Catalog field. A list of catalog items available for requesting is displayed.
Note:
The catalog items that are available for requesting by a user is governed by authorization privileges defined for the admin roles of the user.
-
Select the catalog item for the role that you want to request.
-
Click Add Selected to Cart. The selected role catalog item is added to the request cart.
-
Click Checkout. The role will be assigned to the user when an approver approves the request.
You can edit the catalog item by clicking View & Edit.
To remove roles from a user:
-
In the User Details page, click the Roles tab. The Roles tab is displayed with the list of roles assigned to the user.
-
Select the role that you want to remove.
-
From the Actions menu, select Remove. Alternatively, you can click Remove Roles on the toolbar. The Catalog page is displayed.
-
Click the search icon next to the Catalog field. A list of catalog items available for requesting is displayed.
Note:
The catalog items that are available for requesting by a user is governed by authorization privileges defined for the admin roles of the user.
-
Select the catalog item for the role that you want to remove.
-
Click Add Selected to Cart. The selected role catalog item is added to the request cart.
-
Click Checkout. The role is either removed immediately or a request is raised depending on authorization privileges granted to the user.
You can edit the catalog item by clicking View & Edit.
11.4.4.3 Adding and Removing Entitlements
To request entitlements for a user:
-
In the User Details page, click Entitlements. The Entitlements tab is displayed with the list of entitlements assigned to the user.
-
From the Actions menu, select Request. Alternatively, you can click Request Entitlements on the toolbar. The Catalog page is displayed.
-
Click the search icon next to the Catalog field. A list of catalog items available for requesting is displayed.
Note:
The catalog items that are available for requesting by a user is governed by authorization privileges defined for the admin roles of the user.
-
Select the catalog item for the entitlement that you want to request.
-
Click Add Selected to Cart. The selected entitlement catalog item is added to the request cart.
-
Click Checkout. The entitlement will be assigned to the user when an approver approves the request.
You can edit the catalog item by clicking View & Edit.
To remove entitlements from a user:
-
In the User Details page, click Entitlements. The Entitlements tab is displayed with the list of entitlements assigned to the user.
-
Select the entitlement that you want to remove.
-
From the Actions menu, select Remove. Alternatively, you can click Remove Entitlements on the toolbar. The Catalog page is displayed.
-
Click the search icon next to the Catalog field. A list of catalog items available for requesting is displayed.
Note:
The catalog items that are available for requesting by a user is governed by authorization privileges defined for the admin roles of the user.
-
Select the catalog item for the entitlement that you want to remove.
-
Click Add Selected to Cart. The selected entitlement catalog item is added to the request cart.
-
Click Checkout. The entitlement will be removed from the user when an approver approves the request.
You can edit the catalog item by clicking View & Edit.
11.4.4.4 Modifying Accounts
You can perform the following account modification operations from the Accounts tab of the User Details page:
11.4.4.4.1 Requesting for an Account
You can request accounts by requesting an application instance. You can request for the following types of accounts (application instances):
-
Primary account: A primary account is the first account created for a user in a target application. In other words, a primary account is the first application instance that is being requested. Oracle Identity Manager supports multiple accounts for a single application instance. The first account that is created is tagged as primary account, and there can be only one primary account for a user. The other accounts (non-primary accounts) are associated with the primary account. When the user requests entitlements, the entitlements are appended to the primary account.
-
Non-primary account: If a user already has a primary account and requests for another account in the same target application, then that account is a non-primary account. A user can have multiple non-primary accounts, but only one primary account.
See Also:
"Marking an Account as Primary" for more information on marking an account as primary
To request for an account:
-
In the User Details page, click the Accounts tab. This tab lists the accounts of the user.
-
From the Actions menu, select Request. Alternatively, click Request Accounts on the toolbar. The Catalog page is displayed.
-
Click the search icon next to the Catalog field. A list of catalog items available for requesting is displayed.
Note:
The catalog items that are available for requesting by a user is governed by authorization privileges defined for the admin roles of the user.
-
Select the catalog item for the account that you want to request. In other words, select the application instance that you want to request.
-
Click Add Selected to Cart. The selected account catalog item is added to the request cart.
-
Click Checkout. The account will be granted to the user when an approver approves the request.
You can edit the catalog item by clicking View & Edit.
11.4.4.4.2 Modifying an Account
To modify an account for the user:
-
In the Accounts tab, select the account that you want to modify.
-
From the Actions menu, select Modify. Alternatively, click Modify Accounts on the toolbar. The account details is displayed which is available for editing.
-
Edit the fields that you want to modify.
-
Click OK.
11.4.4.4.3 Removing an Account
To remove an account from the user:
-
In the Accounts tab, from the Actions menu, select Remove. Alternatively, click Remove Accounts on the toolbar. The Catalog page is displayed.
-
Click the search icon next to the Catalog field. A list of catalog items available for requesting is displayed.
Note:
The catalog items that are available for requesting by a user is governed by authorization privileges defined for the admin roles of the user.
-
Select the catalog item for the account that you want to remove.
-
Click Add Selected to Cart. The selected account catalog item is added to the request cart.
-
Click Checkout. The account will be removed from the user when an approver approves the request.
You can edit the catalog item by clicking View & Edit.
11.4.4.4.4 Marking an Account as Primary
Oracle Identity Manager supports multiple accounts in a single application instance. The first account that is created is tagged as the primary account, and there can be only one primary account for a user. The other accounts (non-primary accounts) are associated with the primary account.
All types of entitlements are available for request in the request catalog. If the request for an entitlement is approved, it is associated with the primary account and not the non-primary account.
When the user gets provisioned to an application instance, Oracle Identity Manager checks if it is the first account provisioned for the user in that application instance. If so, the account is marked as primary. When existing user accounts are reconciled from application instances, the first account that gets reconciled is marked as primary.
A user can have only one primary account. However, Oracle Identity Manager supports multiple accounts for a single application instance. If the account marked as primary is not supposed to be the actual primary account, you can manually change the primary tag for the account and mark another account as primary. By doing so, you can ensure that when the user requests entitlements, the entitlements are appended to the primary account.
To mark an account as a primary account:
-
In the Accounts tab, select the account that you want to mark as primary.
-
From the Actions menu, select Make Primary. Alternatively, click Make Primary on the toolbar.
A message is displayed asking for confirmation.
-
Click Yes to confirm. The account is marked as primary.
11.4.4.4.5 Disabling an Account
You can disable an account that is in enabled state. To disable an account:
-
In the Accounts tab, select the account that you want to disable.
-
From the Actions menu, select Disable. Alternatively, click Disable on the toolbar.
A message is displayed asking for confirmation.
-
Click Yes to confirm. The account is disabled.
11.4.4.4.6 Enabling an Account
You can enable an account that is in disabled state. To enable an account:
-
In the Accounts tab, select the account that you want to enable.
-
From the Actions menu, select Enable. Alternatively, click Enable on the toolbar.
A message is displayed asking for confirmation.
-
Click Yes to confirm. The account is enabled.
11.4.4.5 Modifying Details of Direct Reports
The modify the details of direct reports:
-
In the User Details page, click the Direct Reports tab. This tab lists the direct reports of the open user.
-
Select the user or direct report you want to modify.
-
Click the edit icon on the toolbar. The User details page of the selected direct report is displayed. Use the toolbar and tabs to modify the details of the direct report.
11.4.5 Disabling a User
To disable a user that is in enabled state:
-
In the Users section under Administration, search for and select the user you want to disable.
-
Disable the user in one of the following ways:
-
Click Disable on the toolbar.
-
From the Actions menu, select Disable.
-
Click the user login of the user record that you want to disable. On the User Details page, click Disable User on the toolbar.
-
-
In the Target Users section, click the plus icon to search for more target users and add to the list of users that you want to disable. You can also view the user details by clicking the User Details link for each user.
-
In the Justification and Effective Date section, specify a justification and effective date for disabling the selected user.Click Submit. A message is displayed stating that the user is successfully disabled.
11.4.6 Enabling a User
To enable a disabled user:
-
In the Users section under Administration, search for and select the user you want to enable.
-
Enable the user in one of the following ways:
-
Click Enable on the toolbar.
-
From the Actions menu, select Enable.
-
Click the user login of the user record that you want to enable. On the User Details page, click Enable User on the toolbar.
-
-
In the Target Users section, click the plus icon to search for more target users and add to the list of users that you want to enable. You can also view the user details by clicking the User Details link for each user.
-
In the Justification and Effective Date section, specify a justification and effective date for enabling the selected user.Click Submit. A message is displayed stating that the user is successfully enabled.
11.4.7 Deleting a User
To delete a user:
-
In the Users section under Administration, search for and select the user you want to delete.
-
Delete the user in one of the following ways:
-
Click Delete on the toolbar.
-
From the Actions menu, select Delete.
-
Click the user login of the user record that you want to delete. On the User Details page, click Delete User on the toolbar.
-
-
Verify that the selected user is displayed in the Target Users section.
-
If required, in the Target Users section, click the plus icon to search for more target users and add to the list of users that you want to delete. You can also view the user details by clicking the User Details link for each user.
-
In the Justification field, enter a justification for deleting the user.
-
In the Effective Date field, specify a date from which the user account must be removed.
-
Click Submit. A request to delete the user is created, which is subject to approval.
11.4.8 Locking an Account
To lock the account of a user:
-
In the Users section under Administration, search for and select the user you want to lock.
-
Lock the user in one of the following ways:
-
Click Lock Account on the toolbar.
-
From the Actions menu, select Lock Account.
-
Click the user login of the user record that you want to lock. On the User Details page, click Lock Account on the toolbar.
-
-
In the confirmation message that is displayed, click Lock. The account of the selected user is locked.
11.4.9 Unlocking an Account
To unlock the account of a user:
-
In the Users section under Administration, search for and select the user you want to unlock.
-
Unlock the user in one of the following ways:
-
Click Unlock Account on the toolbar.
-
From the Actions menu, select Unlock Account.
-
Click the user login of the user record that you want to unlock. On the User Details page, click Unlock Account on the toolbar.
-
-
In the confirmation message that is displayed, click Unlock. The account of the selected user is unlocked.
11.5 Username Reservation
When the request for user creation is submitted, the following scenarios are possible:
-
While the request is pending, another create user request is submitted with the same username. If the second request is approved and the user is created, then the first request, when approved, fails because the username already exists in Oracle Identity Manager.
-
While the request is pending, another user with the same username is directly created in the LDAP identity store. When the create user request is approved, it fails while provisioning the user entity to LDAP because an entry already exists in LDAP with the same username.
To avoid these problems, you can reserve the username in both Oracle Identity Manager and LDAP while the create user request is pending for approval. If a request is created to create a user with the same username, then an error message is displayed and the create user request is not created.
See Also:
"Creating Requests" for information about creating requests to create a user
For reserving the username:
-
The USER ATTRIBUTE RESERVATION ENABLED system property must be set to TRUE for the functionality to be enabled. For information about searching and modifying system properties, see "Managing System Properties" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
-
Reservation in LDAP is done only if reservation functionality is enabled, and LDAP is in sync with Oracle Identity Manager database. For information about synchronization between Oracle identity Manager and LDAP identity store, see "Integration Between LDAP Identity Store and Oracle Identity Manager" in Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
Note:
-
If LDAP provider is not configured, then the reservation is done only in Oracle Identity Manager.
-
When LDAP synchronization and user attribute reservation features are enabled, it is recommended to enable UID uniqueness in the directory server. Without this, user reservation in the directory does not work properly because while the user is reserved in the reservation container, the user with the same user ID can be created in the user container. This results is user creation failure when Oracle Identity Manager tries to move the user from the reservation container to the user container.
-
If user attribute reservation is enabled, the reservation happens in two phases:
In the first phase, an entry is created in Oracle Identity Manager database and a user is created in reservation container. This entry in Oracle Identity Manager database is removed after successful creation of user, rejection by approver, or request failure.
In the second phase, in LDAP, on successful creation, the user is moved to the reservation container. In other cases such as rejection by approver or request failure, the user is removed from the reservation container.
After the request-level and operation-level approvals are obtained for the create user request, the username is no longer reserved in the username container in LDAP. The username is moved to the container in which the existing users are stored. The user is also created in Oracle Identity Manager.
This section consists of the following topics:
11.5.1 Enabling and Disabling Username Reservation
The username reservation functionality is enabled by default in Oracle Identity Manager. This is done by keeping the value of the USER ATTRIBUTE RESERVATION ENABLED system property to TRUE. You can verify the value of this system property in the System Configuration section of the Oracle Identity Manager System Administration Console.
To disable username reservation:
-
Log in to Oracle Identity System Administration.
-
In the left pane, under System Management, click System Configuration. The Advanced Administration opens in a new window.
-
In the left pane, click the search icon to search for all existing system properties. A list of system properties are displayed in the search results table.
-
Click User Attribute Reservation Enabled. The System Property Detail page for the selected system property is displayed, as shown in Figure 11-2:
Figure 11-2 The System Property Detail Page
Description of "Figure 11-2 The System Property Detail Page"
-
In the Value field, enter False.
-
Click Save. The username reservation functionality is disabled.
11.5.2 Configuring the Username Policy
Username Policy is a plugin implementation for username operations such as username generation and username validation. You can change the default policies from the System Configuration section in Oracle Identity System Administration.
In case of a Create User usecase, the plugins are invoked only if the user login is not provided. In such a case, the plugin to be invoked is picked up from the system property, "Default policy for username generation".
Table 11-5 lists the predefined username policies provided by Oracle Identity Manager. In this table, the dollar ($) sign in the username generation indicates random alphabet:
Table 11-5 Predefined Username Policies
| Policy Name | Expected Information | Username Generated |
|---|---|---|
|
oracle.iam.identity.usermgmt.impl.plugins.EmailIDPolicy |
|
E-mail value is used as the auto-generated user name |
|
oracle.iam.identity.usermgmt.impl.plugins.LastNameFirstInitialLocalePolicy |
First name, last name, and locale |
last name + first initial_locale, last name + middle initial + first initial_locale, last name + $ + first initial_locale (all possibilities of single random alphabets), last name + $$ + first initial_locale |
|
oracle.iam.identity.usermgmt.impl.plugins.FirstInitialLastNameLocalePolicy |
Firstname, Lastname, Locale |
first initial + lastname_locale, first initial + middle initial + first name_locale, first initial + $ + lastname_locale, first initial + $$ + lastname_locale |
|
oracle.iam.identity.usermgmt.impl.plugins.LastNameFirstInitialPolicy |
Firstname, Lastname |
lastname+firstInitial, lastname+middleinitial+firstInitial, lastname+$+firstInitial ( all possibilities of single random alphabets) , lastname+$$+firstInitial |
|
oracle.iam.identity.usermgmt.impl.plugins.FirstInitialLastNamePolicy |
Firstname, Lastname |
firstInitial+lastname, firstInitial+middleInitial+firstname, firstInitial+$+lastname, firstInitial+$$+lastname |
|
oracle.iam.identity.usermgmt.impl.plugins.LastNameFirstNamePolicy |
Firstname, Lastname |
lastname.firstname, lastname.middleinitial.firstname, lastname.$.firstname ( all possibilities of single random alphabets) , lastname.$$.firstname |
|
oracle.iam.identity.usermgmt.impl.plugins.FirstNameLastNamePolicy |
Firstname, Lastname |
firstname.lastname, firstname.middleinitial.lastname, firstname.$.lastname (all possibilities of single random alphabets) , firstname.$$.lastname |
|
oracle.iam.identity.usermgmt.impl.plugins.DefaultComboPolicy |
Any one of the following: - Firstname, Last Name - Last name. |
If e-mail is provided, then username is generated based on the e-mail. If e-mail is not available, then it generates username based on firstname and lastname by appending a user domain to it. If first name is not available, then it generates the username based of the last name only by appending a user domain to it. The user domain is configured as the Default user name domain system property, and the default value is @oracle.com |
|
oracle.iam.identity.usermgmt.impl.plugins.LastNamePolicy, |
Lastname |
lastname, middle initial + lastname , $ + lastname, $$ + lastname |
|
oracle.iam.identity.usermgmt.impl.plugins.LastNameLocalePolicy |
Lastname, Locale |
lastname_locale, middle initial + lastname_locale , $ + lastname_locale, $$ + lastname_locale |
|
oracle.iam.identity.usermgmt.impl.plugins.FirstNameLastNamePolicyForAD |
Firstname, Lastname |
firstname+lastname, substring of firstname+lastname+$, substring of firstname+ substring of lastname+$ |
|
oracle.iam.identity.usermgmt.impl.plugins.LastNameFirstNamePolicyForAD |
Lastname, Firstname |
lastname+firstname, lastname+substring of firstname+$, substring of lastname+ substring of firstname+$ |
The policy implementations generate the username, check for its availability, and if the username is not available, then generate other username based on the policy in the order mentioned in Table 11-5, and repeat the procedure. The dollar ($) sign in the username generation indicates random alphabet. If any of the expected information is missing, then the policies generate errors.
Values must be provided for all the parameters of the username generation format. If any of the parameters are not provided, then Oracle Identity Manager generates an error. For example, If the firstname.lastname policy is configured and the firstname is not provided, then the error would be "An error occurred while generating the Username. Please provide firstname as expected by the firstname.lastname policy".
The username generation is exposed as public APIs in User Manager. Oracle Identity Manager provides an utility class for accessing the functionality of generating user names. The class that contains utility methods is as shown:
oracle.iam.identity.usermgmt.api.UserManager
The UserManager class exposes the following public API for username generation and validation:
//Method that will generate username based on default policy
public String generateUserNameFromDefaultPolicy(Map<String, Object> attrMap)
throws UserNameGenerationException, UserManagerException;
//Method that will generate username based on policy
public String generateUserNameFromPolicy(String policyId, Map<String, Object>
attrMap) throws UserNameGenerationException, UserManagerException;
//Method that will check whether username is valid against default policy
public boolean isUserNameValidForDefaultPolicy(String userName, Map<String,
Object> attrMap) throws UserManagerException;
//Method that will check whether username is valid against given policy
public boolean isUserNameValidForPolicy(String userName, String policyId,
Map<String, Object> attrMap) throws UserManagerException;
//Method to return all policies (including customer written)
public List<Map<String, String>> getAllUserNamePolicies(Locale locale)
//Method that will return policy description in given locale
public String getPolicyDescription(String policyID, Locale locale)
Table 11-6 lists the constants defined in the UserManager class to represent the policy ID of the default username policies:
Table 11-6 Constants Representing Policy IDs
| Policy Name | Constant |
|---|---|
|
EmailUserNamePolicy |
EMAIL_ID_POLICY |
|
LastNameFirstInitialLocalePolicy |
FIRSTNAME_LASTNAME_POLICY |
|
FirstInitialLastNameLocalePolicy |
LASTNAME_FIRSTNAME_POLICY |
|
LastNameFirstInitialPolicy |
FIRSTINITIAL_LASTNAME_POLICY |
|
FirstInitialLastNamePolicy |
LASTNAME_FIRSTINITIAL_POLICY |
|
LastNameFirstNamePolicy |
FIRSTINITIAL_LASTNAME_LOCALE_POLICY |
|
FirstNameLastNamePolicy |
LASTNAME_FIRSTINITIAL_LOCALE_POLICY |
|
DefaultComboPolicy |
DEFAULT_COMBO_POLICY |
|
LastNamePolicy |
LASTNAME_POLICY |
|
LastNameLocalePolicy |
LASTNAME_LOCALE_POLICY |
|
FirstNameLastNamePolicyForAD |
FIRSTNAME_LASTNAME_POLICY_FOR_AD |
|
LastNameFirstNamePolicyForAD |
LASTNAME_FIRSTNAME_POLICY_FOR_AD |
When called to generate username, the policy classes expect the attribute values to be set in a map by using the key constants defined in the oracle.iam.identity.utils class.Constants. This means that a proper parameter value must be passed to call the method by using the appropriate constant defined for it, for example, the FirstName parameter has a constant defined for it.
The default username policy can be configured by using the Oracle Identity System Administration. To do so:
-
Navigate to the System Configuration section.
-
Search for all the system properties.
-
Click Default policy for username generation. The System Property Detail page for the selected property is displayed, as shown in Figure 11-3:
Figure 11-3 The Default Username Policy Configuration

Description of "Figure 11-3 The Default Username Policy Configuration"
The XL.DefaultUserNameImpl system property is provided for picking up the default policy implementation. By default, it points to the default username policy, which is oracle.iam.identity.usermgmt.impl.plugins.DefaultComboPolicy displayed in the Value field.
-
In the Value field, enter oracle.iam.identity.usermgmt.impl.plugins.POLICY. Here, POLICY is one of the policy implementations.
Note:
All the plug-ins must be registered with Oracle Identity Manager by using the /identity/metadata/plugin.xml file. A sample plugin.xml file is as shown:
<plugins pluginpoint="oracle.iam.identity.usermgmt.api.UserNamePolicy"> <plugin pluginclass="oracle.iam.identity.usermgmt.impl.plugins.LastNameFirstNamePolicy" version="1.0" name="LastNameFirstNamePolicy"/> </plugins>
-
Click Save.
11.5.3 Writing Custom User Name Policy
You can write your own policies by adding new plug-ins and changing the default policies from the System Configuration section in Oracle Identity System Administration.
See Also:
"Developing Plug-ins" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information about the plug-in framework
The UserManager exposes APIs for username operations. The APIs take the user data as input and return a generated username. The APIs make a call to plug-ins that return the username. This allows you to replace the default policies with custom plug-ins with your implementation for username operations.
Note:
-
For user name generation and validation, public APIs are exposed in UserManager.
-
While creating the policy, ensure that the attributes used in generating the username are defined in the request data set. For information about request data set, see the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
You can write your own username policies by implementing the plug-in interface, as shown:
package oracle.iam.identity.usermgmt.api;
public interface UserNameGenerationPolicy extends
oracle.iam.identity.usermgmt.api.UserNamePolicy {
public String getUserName(Map<String, Object> reqData) throws UserNameGenerationException;
public boolean isGivenUserNameValid(String userName, Map<String, Object> reqData);
//methods inherited from old user name policy interface
//oracle.iam.identity.usermgmt.api.UserNamePolicy
public String getUserNameFromPolicy(HashMap<String, String> reqData) throws UserNameGenerationException;
public boolean isUserNameValid(String userName, HashMap<String, String> reqData);
public String getDescription(Locale locale);
}
This plug-in point is exposed as a kernel plug-in that takes request data as input and returns the username. Each plug-in expects some information and generates username based on that information provided.
Note:
Oracle Identity Manager provides an abstract implementation of the oracle.iam.identity.usermgmt.api.UserNameGenerationPolicy interface as the oracle.iam.identity.usermgmt.api.AbstractUserNameGenerationPolicy class name. Therefore, you need not implement the following two methods:
public String getUserNameFromPolicy(HashMap<String, String> reqData) throws UserNameGenerationException; public boolean isUserNameValid(String userName, HashMap<String, String> reqData);
All the plug-ins must be registered with Oracle Identity Manager by using the /identity/metadata/plugin.xml file. A sample plugin.xml file is mentioned below:
<plugins pluginpoint="oracle.iam.identity.usermgmt.api.UserNamePolicy"> <pluginpluginclass="oracle.iam.identity.usermgmt.impl.plugins.CustomDepartmentNumberEmployeeNumberPolicy " version="1.0" name="CustomDepartmentNumberEmployeeNumberPolicy"/> </plugins>
The following are the guidelines on while writing custom user name policies:
-
Policies should implement the new interface oracle.iam.identity.usermgmt.api.UserNameGenerationPolicy.
-
Custom user name policies must be re-entrant. This means that the custom code in the policy should return the same user login if approver has updated an attribute that does not contribute in generating the user login.
For sample implementation please refer below:
package oracle.iam.identity.usermgmt.impl.plugins;
import java.util.Locale;
import java.util.Map;
import oracle.iam.identity.exception.UserNameGenerationException;
import oracle.iam.identity.usermgmt.api.AbstractUserNameGenerationPolicy;
import oracle.iam.identity.usermgmt.api.UserManagerConstants;
import oracle.iam.identity.usermgmt.api.UserNameGenerationPolicy;
public class CustomDepartmentNumberEmployeeNumberPolicy extends AbstractUserNameGenerationPolicy implements UserNameGenerationPolicy {
private String departmentNumberKey = UserManagerConstants.AttributeName.DEPARTMENT_NUMBER.getId();
private String employeeNumberKey = UserManagerConstants.AttributeName.EMPLOYEE_NUMBER.getId();
@Override
public String getUserName(Map<String, Object> reqData)
throws UserNameGenerationException {
String departmentnumber = reqData.get(departmentNumberKey) == null ? null : reqData.get(departmentNumberKey).toString();
String employeeNumber = reqData.get(employeeNumberKey) == null ? null : reqData.get(employeeNumberKey).toString();
// Required in case of approver edit. If approver has not modified any attribute which contributes in user name generation , then return same old user login
//Check if user data is not changed using checkForSameUserLogin method present in AbstractUserNameGenerationPolicy, then return same user login
//OR use Map<String, Object> existingData = (Map<String, Object>) reqData.get(oracle.iam.identity.usermgmt.api.UserManagerConstants.EXISTING_DATA ) to implement your own comparison logic
// If existingData is NULL, it means generate a new user login. If it is not NULL, then it means policy is invoked during approver edit.
// If it is NOT NULL, Compare value of participating attributes from existingData and reqData. If same, return same user login as present in existingData ; otherwise generate a new user login.
String oldUserLogin = checkForSameUserLogin(reqData , new String[]{departmentNumberKey , employeeNumberKey});
if(oldUserLogin!=null)
return oldUserLogin;
// TODO: DO basic validations. Also, Ensure newly generated user name is unique and not reserved. You may use utility methods in oracle.iam.identity.usermgmt.utils.UserNamePolicyUtil for preforming validations.
return departmentnumber + "-" + employeeNumber;
}
@Override
public boolean isGivenUserNameValid(String userName, Map<String, Object> reqData) {
// TODO : custom implementation
return true;
}
@Override
public String getDescription(Locale locale) {
return "User Name Generation Policy using department number and employee number";
}
}
11.5.4 Releasing the Username
The username is released in the following scenarios:
-
When the request is approved, and the user is successfully created in Oracle Identity Manager and provisioned to LDAP, and the username from the reserved table is removed. The reserved username is removed after successful user creation after the approvals. The reserved entry in LDAP is removed and the actual user is created.
-
If the request is rejected, then the reserved entry of username in LDAP and Oracle Identity Manager is removed.
-
If the request fails while or before creating a user in Oracle Identity Manager or LDAP, then the reserved username is deleted.
11.5.5 Configuring Username Generation to Support Microsoft Active Directory
In Oracle Identity Manager deployment with LDAP synchronization is enabled, where Microsoft Active Directory (AD) is the data store, the User Login attribute in Oracle Identity Manager is mapped to the uid attribute in LDAP, which in turn is mapped to the sAMAccountName attribute. The sAMAccountName attribute is used as login for all AD-based applications. There is a limitation on the maximum length supported for value contained in the sAMAccountName attribute in AD. It cannot exceed 20 characters.
Oracle Identity Manager accepts user name as an input at the time of user creation and it can be more than 20 characters. Because AD does not support user name of more than 20 characters, Oracle Identity Manager can be configured to generate the user name, which consists of less than 20 characters.
When AD is used as data store, you can configure the autogeneration of user name by setting the value of the XL.DefaultUserNamePolicyImpl system property to any one of the following:
-
FirstNameLastNamePolicyForAD: Generates the user login by prefixing a substring from the first name to that of the last name
-
LastNameFirstNamePolicyForAD: Generates the user login by prefixing a substring from last name to that of the first name
See "Administering System Properties" for information about the XL.DefaultUserNamePolicyImpl system property and setting values of system properties.
Note:
If AD is the data store, then any one of the FirstNameLastNamePolicyForAD or LastNameFirstNamePolicyForAD policies must be used. Any other user name generation policy will fail to generate the user name.
11.6 Common Name Generation
The generation of the Common Name user attribute value in Oracle Identity Manager is described in the following sections:
11.6.1 Common Name Generation for Create User Operation
In an LDAP-enabled deployment of Oracle Identity Manager, Fusion applications such as Human Capability Management (HCM) does not pass the common name via SPML request. Given that the common name is a mandatory attribute in LDAP and Oracle Identity Manager is setup to use it as the RDN, Oracle Identity Manager must generate a unique common name.
Based on the description on Common Name, it is the user's display name consisting of first name and last name. Therefore, Oracle Identity Manager generates the Common Name with the help of a common name generation policy that specifies the Common Name in the "firstname lastname" format.
To configure common name generation in Oracle Identity Manager, set the value of the XL.DefaultCommonNamePolicyImpl system property to oracle.iam.identity.usermgmt.impl.plugins.FirstNameLastNamePolicy. For information about the XL.DefaultCommonNamePolicyImpl system property and setting the value of a system property, see "Managing System Properties" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
The following are the details of the FirstNameLastNamePolicy:
-
Expected information: Firstname, Lastname
-
Common Name generated: firstname.lastname, firstname.$.lastname (all possibilities of single random alphabets), firstname.$$.lastname and so on until a unique common name is generated
Note:
The common name must be reserved until the user is created by the request so that multiple requests generated simultaneously having same first and last names do not generate the same common name.
11.6.2 Common Name Generation for Modify User Operation
When the user profile is modified, one or more attributes can change. HCM cannot filter out and send only the modified data to Oracle Identity Manager because it does not have the old user attributes and cannot determine which ones are modified. Therefore, all attributes including the common name (CN) are passed to Oracle Identity Manager by the SPML request. Because the CN changed, Oracle Identity Manager attempts a modify operation (modrdn) in the directory resulting in DN change. Because of this unintended DN change, the group membership DN becomes stale resulting in the user loosing membership in that group. This subsequently results in authorization failure. This happens when referential integrity is turned off in the LDAP server, and therefore, the referenced groups are not updated when the RDN of the user changes. Therefore, referential integrity must be turned on in the target LDAP server. Otherwise, the group memberships become stale. The referential integrity issue is also applicable to roles. Groups are also members of other groups and any RDN changes must be reflected as well.
You can turn on the referential integrity by setting the value of the XL.IsReferentialIntegrityEnabled system property to TRUE. For information about this system property, see "Managing System Properties" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
Table 11-7 lists the possible scenarios when RDN is modified:
Table 11-7 RDN Modification Scenarios
| Referential Integrity in LDAP | XL.IsReferentialIntegrityEnabled | Result of Modify Operation (modrdn) |
|---|---|---|
|
Disabled |
FALSE |
Oracle Identity Manager generates an error and operation fails. |
|
Disabled |
TRUE |
Modify operation passes from Oracle Identity Manager and RDN is changed in LDAP. However, the group references are not updated and are stale. This configuration is not recommended. |
|
Enabled |
FALSE |
Oracle Identity Manager generates an error and modify operation fails. This property must be set to TRUE in Oracle Identity Manager because referential integrity is enabled in LDAP. |
|
Enabled |
TRUE |
Modify operation passes and RDN is updated. In addition, the references for the DN are updated in LDAP. |
|
Multiple directories with roles and users stored in separate directories. Referential integrity property is not relevant here. |
FALSE |
Modify operation fails from Oracle Identity Manager. This is not supported by LDAP. Therefore, FALSE is the recommended value in Oracle Identity Manager for the property. |
|
Multiple directories with roles and users stored in separate directories. Referential integrity property is not relevant here. |
TRUE |
Modify operation passes and RDN is modified. However, because LDAP does not support referential integrity in multiple directories, the group references are stale and must be manually updated. |