6 Organizing Content
Oracle WebCenter Content provides several ways to organize content. The Folders component (also called Framework Folders) provides a hierarchical folder interface, similar to a conventional file system, for organizing and locating some or all of the content in the repository. Contribution Folders provides similar functionality, however, Folders is a scalable, enterprise solution and is meant to be a replacement for Contribution Folders. WebDAV (Web-Based Distributed Authoring and Versioning) provides a way to remotely author and manage Oracle content using clients that support the WebDAV protocol. And Content Folios is an optional component that when enabled, provides a quick and effective way to assemble, track, and access logical groupings of multiple content items from within the secure environment of Content Server.
This chapter discusses the following methods of organizing content:
6.1 Managing Folders
The folder hierarchy provided by the Folders component is accessible through both the standard content management Web interface and through the WebDAV interface. With the standard interface, folders and content items (files) are accessed with a browser and specially designed Web pages. With the WebDAV interface, a network connection is made to Content Server and then folders and files are accessed through Windows Explorer, just as shared folders are accessed.
Do not enable both Contribution Folders and Folders unless content must be migrated from Contribution Folders to the Folders interface. To migrate the folders and files from Contribution Folders to the Folders interface, use the Folders Migration utility to replicate the folder hierarchy and selectively migrate folder content. For more information, see Oracle Fusion Middleware Administering Oracle WebCenter Content.
This section discusses the following topics:
6.1.1 Folder Overview
The familiar folder and file model provides a framework for organizing and accessing content stored in the repository. Functionally, folders and files are very similar to those in a conventional file system. Folders and files can be copied, moved, renamed, and deleted. Shortcuts can be created in order to access a content item from multiple locations in the hierarchy.
Files in the Folders interface are similar to symbolic links or pointers to content items in the repository. The operations performed in the Folders interface, such as searching or propagating metadata, effectively operate on the associated content items.
Users can create and edit folders, shortcuts to folders, and links to documents as allowed by Content Server's standard security model. Folders are assigned security attributes in the same way they are assigned to content items, including security group, account, and Access Control List attributes, if enabled.
By default, folders inherit the security settings and other default metadata defined for the parent folder. Security and metadata values can be set for a given folder and those values propagated to folders and content items within the folder.
This section discusses the following topics:
6.1.1.1 Folders and Files
Users can easily view the relationship between folders and subfolders and can browse to a group of content items. Using Folders, users can perform the following actions with the privileges defined by Content Server's standard security model:
-
Browse to locate content items for check-in, check-out, and to view and change folder and item information.
-
Create new folders and subfolders.
-
Create new content items in a folder or add existing repository content to a folder.
-
Add shortcuts to folders or content items in one or more locations. Shortcuts act as placeholders for the referenced content item.
-
Move or copy folders or files to other locations.
-
Rename a folder or file.
-
Remove a file from the folders hierarchy. This does not affect the associated content item.
-
Delete a folder or file. When deleted, the folder or file and any shortcuts to it are removed from the folders hierarchy. Any content items associated with the files are set to expired in the repository.
-
Create a query folder that contains content items returned by the query associated with the folder. For more information about query folders, see Section 6.1.1.3.
-
Create a retention query folder and assign retention rules for the content items returned by the query. For more information about query folders and retention scheduling, see Section 6.1.1.4.
-
Assign folder security and default metadata values for content items created in the folder. Specified metadata values can be propagated to the contents of a folder or propagation can be blocked for a given folder. For more information, see Section 6.1.1.7.
The Folders interface follows several conventions familiar to users of file systems:
-
Use standard Windows naming conventions when creating folders. Do not use special characters such as the forward or backward slash characters or the double quote character.
-
Content Server can store multiple files of the same name as separate content items. However, in the Folders interface, file names in a given folder must be unique (in the same way that a folder in Windows cannot contain two files with the same name).
6.1.1.2 Shortcuts and Links
With Folders, the same folder or content item can be referenced in multiple locations using shortcuts that act as placeholders for the referenced folder or file. Shortcuts to folders or files can help locate and manage the target content items within the folder hierarchy.
Folders and folder shortcuts are identified with different icons.
| Icon | Description |
|---|---|
|
Folder: Folders can contain other folders, content items, and shortcuts to other folders and content items. Folders are identified by a standard folder icon. |
|
|
Folder Shortcut: A folder shortcut includes the contents of the associated folder in the hierarchy at the point where the shortcut is stored. Folder shortcuts are identified by a folder icon with an arrow and can reference either a folder or a query folder. Folder shortcuts are excluded from metadata propagation actions. |
|
|
Query Folder: The contents of a query folder are the repository content items returned by the query associated with the folder. Query folders are identified by a folder icon with a magnifying glass. |
|
|
Retention Query Folder: Similar to a query folder, the contents of a retention query folder are the repository content items returned by the query associated with the folder. Retention rules can also be set for the content items returned by the query. Retention query folders are identified by a folder icon with a magnifying glass and a clock. |
Content items in the Folders interface are similar to links to items in the repository. There are two types of links for content items.
| Icon | Description |
|---|---|
|
File (primary link): There can be only one primary link to a content item in the Folders interface. The primary link represents the content item in the repository and is identified by a standard document icon. In most respects, working with a file (or primary link) is the same as working directly with the content item in the repository. For example, the status of the associated content item for a deleted file is set to "expired." |
|
|
Shortcut (secondary link): There can be any number of file shortcuts in the Folders interface to an associated content item. A file shortcut is identified by a document icon with an arrow indicating that it is a reference to the actual content item. Shortcuts are excluded from metadata propagation actions. Changes made by means of the shortcut (such as metadata changes) are made to the underlying content item. Changes made to the shortcut itself (such as deleting the shortcut) do not affect the underlying content item. |
|
|
Query result: The contents of a query folder are the repository content items returned by the query associated with the folder. Query content items are identified by a document icon with a magnifying glass. |
6.1.1.3 Query Folders and Searches
A query folder functions much like a saved search. Each time is it accessed, the query associated with the folder is initiated. The contents of a query folder are the content items returned by the query. The contents of query folders can change dynamically as the contents of the repository change.
Query folders contain the actual repository content items returned by the query, not the folders and shortcuts. Query folder contents can be copied, viewed, and updated for individual items, or metadata changes can be propagated through all items in the query folder.
Folders also expands the standard search results options to include the Create Query Folder option to save a search query as a query folder. To search for folders or files from within a folder, use the options in the Search menu in a given folder. You can search any or all folder metadata fields.
6.1.1.4 Folders Retention
Basic content retention scheduling can be done by creating a retention query folder, assigning retention attributes to the folder, and then configuring the retention schedule. Retention rules can be assigned based on the age of the content item or on the number of revisions. If you have a license for Records, retention rules based on categories defined in Records can be established.
Administrative privileges are needed to specify retention rules or schedules. For information about specifying retention scheduling, see Section 6.1.3.1. For information about specifying retention scheduling, see Section 6.1.3.2.
The following considerations apply to retention query folders:
-
Retention rules are associated with the retention query folder but are stored separately from the standard folder metadata. For this reason, you cannot search for a query folder based on the folder's retention attributes.
-
Unlike standard query folders, retention query folders search only database values and cannot perform full-text searches even if full-text search is supported.
-
If multiple retention rules are specified for a particular retention query folder, all the rules must be satisfied for the disposition to occur. For example, if you specify the age as 1 calendar year and the number of revisions to keep as 3, only those items that are more than 1 year old and that are older than the last three revisions are deleted.
-
Different queries can include the same content item in their results. In this case, the retention rules for each retention query folder are applied independently from one another. For example, if one query folder specifies the number of revisions to keep as 2 and another specifies the revisions to keep as 3, only two revisions of the item are retained.
-
Folders retention is treated differently than that in Records. When using Records, if multiple delete actions are called, the retention with the longest interval is used. In Folders, the shortest interval always runs first.
-
Folders retention processes items based on the values in the dCreateDate row in the Revisions table in the database.
Considerations with Records Usage
If both Folders and Records are used on the same system, the following additional considerations apply:
-
If Records is installed, it is possible to have two retention schedules (as well as multiple rules) for the same item. If a content item has retention rules defined in both Content Server and in Records, only the retention and schedule defined by the Records system are used.
-
If Records is installed with a level of DoD Baseline or higher, retention query folder options are not available in the Content Server interface. Any existing retention query folders retain their icon and (inactive) retention attributes, but function as a standard query folder.
If the level is then set to Standard or lower, then retention query folder options are enabled in Content Server and the rules for any existing retention query folders become active.
6.1.1.5 Personal Folders
In the root folder of the Folders hierarchy is a Users folder that contains a folder defined for you as an authenticated user. You can create subfolders and content items in the same way you do with other folders in the hierarchy. Every authenticated user can have a personal folder.
Folders provides menu options to quickly add folders, files, and shortcuts to your personal folder, referred to as Add to My Folder in menus. Although your personal folder is visible only to you, the items in the folder are governed by the security settings for the item itself and not necessarily those of the enclosing folder. Some items may be accessible to other users, for example, in search results.
To access your personal folder, choose My Content Server then My Folders from the Main menu.
6.1.1.6 Folders Metadata
Every folder has a set of metadata values that can be applied to content items added to the folder. Folders can be configured to enforce metadata rules on their content items or to allow any or all values to be modified. For example, a folder could be configured to enforce 'Secure' as the value for the Security Group metadata field. Then, when a content item is added to that folder, the Security Group value automatically updates to Secure.
Folders inherit the default metadata assigned to their parent folders unless the folder is explicitly configured otherwise. Subsequent changes to a parent folder's metadata do not affect the metadata for existing subfolders unless explicitly propagated down through the hierarchy.
Folder metadata inheritance and propagation make it easy to apply metadata to content items. Whether you are an administrator managing all folders and files or a user managing your own folders and files, it is a good idea to plan a metadata strategy before creating folders and adding content items. The strategy should include the following basic steps:
-
Determine whether specific folders or branches in the hierarchy have unique metadata requirements and how best to identify and manage those requirements.
-
Determine which metadata fields (if any) a user should specify when adding or checking in a content item through a particular folder.
-
Determine which metadata fields (if any) should have a default value or an enforced value for a particular folder.
-
Determine which subfolders (if any) are eligible to be changed when propagating metadata through a folder.
-
Determine whether to use profiles to manage metadata requirements. An administrator can create one or more profiles to organize, selectively display, and control access to metadata fields based on rules associated with the profile.
Default metadata values are automatically applied to new content items created in or checked in to a folder. To modify the default metadata values for a folder, Delete permission to the folder is required or you must be the author and have Write permission.
Default metadata values are also used as the default values when propagating metadata.
If Oracle WebCenter Content: Desktop is used and the folder has the Prompt for Metadata option selected, you are prompted to provide metadata values for the item rather than relying on the folder's default metadata settings.
Content items in a folder do not necessarily have the same security settings. To propagate metadata to content items, you must also have Write permission for the content item. To restrict changes to folders only, select the Propagate To Folders Only option.
When propagating metadata, select the metadata fields and specify the values to propagate from the metadata available for the current folder. Any metadata value that can be changed can be propagated. For example, you can propagate the Security Group or Owner values, but you cannot propagate the Content ID. Blank field, such as the Comment or Expiration Date fields, can be propagated to clear the associated values from content items.
To prevent propagation, select Inhibit Propagation in the folder information for a folder or override a folder's inhibit setting using the Force Propagation setting on the Propagate page.
An administrator can create sets of metadata as one or more profiles that the administrator or other users can easily apply to folders when specifying folder defaults or when propagating metadata.
6.1.1.7 Versioning
Content items can be checked in and out through the Folders interface in much the same way as through the standard content management pages. When a particular content item is viewed or edited, options are available to check out the item and then check in a new version of that item.
Folders provides two modes for viewing content item versions:
-
Published Items (consumption mode): The latest released revisions of documents are displayed. These are the same revisions that are returned in search result listings.
-
All Items (contribution mode): The latest revision of each document is displayed. These can include the revisions of documents that are still in workflow or have otherwise not finished with the search indexing process.
Users can switch between the two modes to see released content items only or to see content items that require work before being released. The selection remains in effect until changed.
6.1.2 Configuring Folders
Different types of configuration variables can be set to configure the Framework Folders component:
6.1.2.1 Folder Variables
These variables configure optional settings in the Folders interface.
| Variable | Description |
|---|---|
|
|
If set to true, the owner/author of an item can delete the item as long a they have Write privileges, otherwise, they require Delete permission. The default value is true. |
|
|
If set to true, allows browsing of the Users folder (FLD_USERS), otherwise when a user tries to access the Users folder, they are redirected to their personal folder (FLD_USER:<username>). The default value is false. If explicitly set to true in the config.cfg file, all users can see the contents of the Users folder. An administrator can temporarily set the value as a binder variable in the URL when browsing the Users folder. |
|
|
Set to true to disable personal folder naming specified by FldPersonalFolderFormat. The default is false. If the name format for personal folders is changed or disabled after personal folders are created, the existing folders must be manually renamed, or recreated. For example, if the personal folder for user abc.def@example.com is formatted with the name abc.def and then DisablePersonalFolderFormat is set, the database retains the existing folder name, but the user interface expects it to be named abc.def@example.com. You must rename the folder to match the disabled formatting or delete the row from the database and recreate the folder when the user logs in. |
|
|
Number of files to display in the folder explorer. The default is 50. |
|
|
Number of folders to display in the folder explorer. The default is 50. |
|
|
If set to true, enables the Process Indicator shown during copy, move, delete, and propagate operations. The default value is false. |
|
|
Specify the regular expression used to construct the name of the personal folder from the user's name. By default, the regular expression is (.+)@(.+):$1 (two groups of one or more characters separated by "@" and using the first group as the folder name. For example, the user name abc.def@example.com results in a personal folder is named abc.def. For information about regular expressions, see |
|
|
By default, moved items retain the metadata defined for the item and do not inherit metadata values in the new location. If set to true, the Auto propagate destination's metadata to folder option is added to the Choose a Destination window for mover operations. If the user selects this option, moved items inherit the metadata defined by the enclosing folder in the same way that copied items do. The default value is false. |
|
|
Specify a document type to use if the document type cannot be determined when creating a content item. The default document type is Document. |
|
|
If set to true and Oracle Text Search is in use, subfolder searching is enabled. The default is false. When enabled, the system adds all paths to all documents to the search index. Documents are re-indexed whenever they are added to or removed from a folder. In addition, the document is re-indexed if its full path changes in any way (for example, when the parent folder is moved). |
6.1.2.2 Folders Migration Variables
These variables configure optional settings in the Folders Migration utility. The Folders Migration utility migrates folder content and structure from Contribution Folders (Folders_g component) to Folders (FrameworkFolders component). The utility is available the tables associated with Contribution Folders are present in the database schema.
| Variable | Description |
|---|---|
|
|
Specify the default Security Group to assign to migrated folders if one is not already associated with the folder. If not set explicitly, the default value is Public. Contribution Folders do not need and may not have a Security Group setting. Migrated folders require a security setting. |
|
|
Specify the base name for the root folder created during migration. The folder name has the form: If not set, the base value defaults to "Migrate". |
|
|
Specify the list of folders to exclude from the migration. The list may include folder IDs and folder marks. If not set explicitly, only the TRASH folder is excluded. |
|
|
Set to 0 (zero) to prevent the Folder Migration option from showing in the Administration menu. If set to 1 or if not set explicitly, and migration is possible, the option is displayed. |
6.1.2.3 Folders WebDAV Variables
These variables configure optional settings in the Folders WebDAV interface.
| Variable | Description |
|---|---|
|
|
Set to false to prevent a WebDAV copy from writing over items with the same name. The default value is true |
6.1.3 Working with Retention Scheduling
Content revisions can be disposed of based on the age of the content item or on the number of revisions. If Records is installed, retention rules based on Records categories can also be defined. For additional retention query folder considerations, see Section 6.1.1.4.
To define retention scheduling for the contents of a retention query folder, first specify the retention rules associated with the folder then specify the retention schedule for each of the rules used with one or more retention query folder. This section discusses those tasks:
6.1.3.1 Specify Retention Rules
Retention rules are specified when you create a retention query folder and can be modified at a later time. Retention rules can be specified for retention query folders only if you are an administrator. Retention query folders that do not include retention rules act like standard query folders.
Note:
If Records is installed with a level of DoD Baseline or higher, retention query folder options are not available in the Content Server interface. Any existing retention query folders retain their icon and (inactive) retention attributes, but function as a standard query folder.
The following procedure shows how to specify retention rules. For more information about creating folders and specifying queries, see Oracle Fusion Middleware Using Oracle WebCenter Content.
Query folders with retention rules apply the rules on a specified schedule. For more information about how to create a retention schedule for query folders, see Section 6.1.3.2. For details about setting up a Record retention schedule, see Chapter 13.
-
Navigate to the folder where the retention query folder is stored.
-
To change metadata values, including the retention rules, choose Update Folder Information from the Actions menu for the associated folder.
To change metadata values for the folder when you are viewing the contents of the folder, choose Folder Information from the Edit menu on the page.
-
Click show advanced retention options.
-
Choose one or more retention options. For example, to keep only the most recent 3 revisions of a content item, choose Revisions and specify 3. Older revisions are expired on the retention schedule specified for Revisions.
-
Revisions: Specify how many revisions of the content items in the query folder to keep and click Update.
-
Age: Specify how long to keep the content items in the query folder and click Update.
If you have the full Records product, the units list includes fiscal units as well as calendar units.
-
Category: Assign a category to the query folder and use the retention defined for the category to determine how to dispose of the content items.
This option is available only with the full Records system.
-
-
Make any additional changes to the folder metadata or query and click Save.
6.1.3.2 Configuring a Query Retention Schedule
Query folders with assigned retention rules apply the rules on a specified schedule. A different schedule can be set for each type of retention rule. Content items that are included in multiple query folders can have multiple retention rules, and therefore have multiple schedules applied to them.
Folders retention rules are treated differently than those in the Records system. When using Records, if multiple delete actions are called, the retention with the longest interval is used. In Folders, the shortest interval always runs first.
If a content item has retention rules defined in both Content Server and in Records, only the retention and schedule defined by the Records system is used.
To configure a query retention schedule:
-
From the Administration menu, choose Folders Retention Administration then Configure Scheduled Jobs.
-
On the Folder Retention Scheduled Jobs page, specify schedules for retention rules governed by age or revision.
Age-based rules process items based on the values in the dCreateDate row in the Revisions table in the database.
-
Weeks/Days: Select a Start Time and an End Time. This schedules the retention for query folders with Weekly retention rules. To run the scheduled disposition immediately, click Run Now.
-
Calendar Months: Select a day of the month, a Start Time and an End Time. This schedules the retention for query folders with Monthly or Quarterly retention rules. To run the scheduled disposition immediately, click Run Now.
-
Calendar Years: Select a month, a day of the month, a Start Time and an End Time. This schedules the retention for query folders with Yearly retention rules. To run the scheduled disposition immediately, click Run Now.
-
Fiscal Months/Fiscal Years: If Records is installed, you can schedule the retention for query folders with Fiscal Month and Fiscal Year retention rules. To run the scheduled disposition immediately, click Run Now.
-
Retention Revisions: Select a day of the month, a Start Time and an End Time. This schedules the retention for query folders with Revisions retention rules. To run the scheduled disposition immediately, click Run Now.
Important:
If Records is installed and category retention rules are used, the categories are scheduled by their associated age or revision rules. For example, a category with a retention specified in months is governed by the value you specify here for Calendar Months. Likewise, to immediately apply the retention rules for all items with retention rules or categories specified in months, click the Run Now button associated with Calendar Months on this page.
-
-
Click Update.
6.2 Managing Contribution Folders
Contribution Folders is an optional component that. when enabled, provides a hierarchical folder interface in the form of contribution folders (also called hierarchical folders), enabling the creation of a multilevel folder structure.
Note:
The newer, Folders component is a scalable, enterprise solution and is meant to be a replacement for Contribution Folders.
This chapter includes the following topics:
6.2.1 Understanding Contribution Folders
This sections provides an overview of Contribution Folder functionality and discusses the following topics:
-
Section 6.2.1.5, "Latest Version versus Latest Released Version"
-
Section 6.2.1.7, "Contribution Folder Archiving and Searching"
6.2.1.1 Advantages of Using Contribution Folders
There are several advantages when using Contribution Folders:
-
Browsing: Users can browse through folders to find subfolders and content items using a simple mechanism to retrieve additional information about a folder, and to traverse the tree structure. In a folder with a large number of subfolders, the user can easily view and browse through content items in that folder.
-
Creating folders: Users can create new folders in any folders easily, by naming the folders. Additional information such as folder metadata and default metadata is accessible only if needed.
-
Assigning folder metadata: Users can assign metadata to folders when creating a folder or to existing folders using the same process.
-
Assigning default metadata for items: Users can specify metadata to be assigned to content created in or added to a folder. Set the metadata at folder creation time or later. The steps and process are the same.
-
Assigning a Content Profile to a folder: Content profiles can be assigned to a folder when it is created or later to determine what metadata fields are available to be set as defaults for content items added to that folder.
-
Creating new content in a folder: Users can browse through a folder and check in a new item. If the folder specifies default metadata for new content, or a content profile, then the content check-in form reflects that.
-
Adding existing content to a folder: Users can browse into a folder and add a link to an existing content item. If the destination folder contains items with the same name, the user is asked to rename the new link.
-
Moving or copying items: Users can browse to a folder, select one or more subfolders and content items, and move them or copy them into another folder.
-
Deleting an item/folder: A user can browse to a folder, select one or more subfolders and content items, and delete them. The user is prompted for confirmation of delete action. For items with multiple revisions, the user is asked whether all revisions are deleted or only the latest revision. The user should have an option to apply their answer to all selected files.
-
Renaming an item/folder: A user selects a link/shortcut or subfolder within a folder and renames it. The rename action is allowed only on single items. If the new name is same as that of an existing item or folder, the user is warned and required to change the name to be unique.
The Contribution Folders component mimics the Windows file system. The use of double quotes in the name is not allowed (for example, "doublequotedfolder"). Use the standard naming conventions for Windows when creating folders.
Note:
The newer Folders component is a scalable enterprise solution and is meant to be a replacement for Contribution Folders.
The following structure is used for Contribution Folders:
-
Each Content Server instance has a common set of contribution folders. Any change to the folders is applied system-wide.
-
There is one default system-level folder, called Contribution Folders. The Trash Bin function is enabled during installation with a system-level folder called Trash created.
-
The system administrator can change the name of a system-level folder, but cannot delete it or add a custom system-level folder except through changes to the database. Deleting a system-level folder disables it, but does not remove it from the system.
-
Each folder in the hierarchy contains content items that have the same numeric Folder value, which is assigned automatically upon creation of the folder. Changing the value of the Folder field for a content item places it in a different folder.
-
The maximum number of folders and content items in each folder can be limited so browsing through contribution folders does not affect system performance.
6.2.1.2 Contribution Folders Component Security
The Contribution Folders component applies security at two levels:
-
Content item security: The user logins and security controls in Content Server also apply to content that is managed through contribution folders. For example, if you have Read permission for a content item, you can view the file, but you cannot check in a revision to the file.
To allow users with Read permission to access content through a contribution folder, the
GetCopyAccessenvironment variable must be set, as follows:-
Choose Admin Server then Content Security from the Main menu.
-
Select Allow get copy for user with read privilege.
-
-
Folder security: Security is also applied at the folder level:
-
Each contribution folder has an owner, a user who has permission to manage the folder. The owner can change a folder's metadata and delete the folder, even if they do not have Write or Delete permission to the folder's security group. However, the owner does not have additional permissions to content items in the folder.
-
Users can see only the contribution folders assigned no security group or a security group for which they have at least Read permission.
-
To delete a folder, a user must have Delete permission to the folder or be the owner of the folder. The user must also have permission to delete all of the content items and subfolders in that folder.
-
To change a folder's default metadata, a user must have Read and Write permissions. If the
FoldersModifyWithRWvariable is set to false, a user must also have Delete permission to the folder or be the owner of the folder.
-
Caution:
Be careful when changing the security group of a folder. If a folder is changed to a more restrictive security group, authors may no longer have permission to manage their own content items.
When creating a new folder, the metadata from the parent folder populates the fields for the new folder. The folder initially "inherits" the metadata, but can change its values without affecting the parent folder. Later changes to a parent folder's metadata do not affect the metadata for existing subfolders. To apply a parent folder's metadata to subfolders and content items, use the Metadata Propagation and Default Values feature.
6.2.1.3 Trash Bin
The Trash Bin is an optional feature that sends deleted items to a Trash folder, rather than permanently deleting the items. Items in the Trash Bin can then be permanently deleted or restored to their original location in the folder hierarchy.
Please note the following information regarding the trash bin:
-
Deleting a revision from the Repository Manager bypasses the Trash Bin and permanently deletes the revision.
-
Enable or disable the Trash Bin function using System Folder Configuration after installation.
-
If using folders to contribute content to a Site Studio website, it consider disabling the Trash Bin feature. Otherwise, any deleted content items, such as those moved to Trash Bin, still appear in the tables of content (dynamic lists) on the website. To get rid of the content items, go into the Trash Bin in WebDAV and explicitly delete the documents from there, too.
6.2.1.4 Metadata Propagation and Default Values
The metadata propagation function enables contributors to copy specified metadata values from a folder to its subfolders and content items. Propagation is useful when moving a large number of content items to a new folder structure, or after revising the default metadata for a folder. This feature allows the application of metadata to all items in the structure.
The following list explains this function in more detail:
-
The propagation function applies each folder's metadata to all uninhibited subfolders and content items within those folders. Each uninhibited subfolder and content item inherits the metadata of the launched folder.
-
When inhibiting a folder, it is not affected by metadata propagation from a higher-level folder. However, metadata propagation can still be launched from an inhibited folder.
-
The system administrator selects which metadata fields are included in propagation. This setting applies system wide. By default, no metadata fields are included until they are selected.
-
If a folder metadata field does not have a value defined, subfolders and content items within that folder cannot inherit the blank value during propagation and any existing metadata values can remain intact for these items. The
CollectionPropagateEmptyValuesconfiguration variable controls if empty field values are propagated. -
When metadata propagation is launched, only folders and content items for which you have Write permission to the security group are affected.
When a file is checked in through a contribution folder, default metadata values are entered on the content check-in form. The default values are evaluated in the following order:
-
Contribution folder default values: When checking in a new content item from an Exploring page, default metadata values for that contribution folder are entered on the content check-in form.
-
User default metadata values: If any metadata defaults are not defined for the contribution folder, the user's default metadata values are applied. User default metadata values are only applicable when creating new content items using WebDAV. They are not applicable when using the Web interface.
-
System default metadata values: The system default values are applied to any fields not defined by the contribution folder or the user's default metadata. These values are defined by the system administrator. System default metadata values are only applicable when creating new content items using WebDAV. They are not applicable when using the Content Server Web interface.
-
None: A metadata field can be blank if it is not a required field. If a required field is blank, an error occurs and the content item is not checked in.
6.2.1.5 Latest Version versus Latest Released Version
When documents are edited and checked in, the revised document is processed, indexed, then released. Before the process is complete, the revised document is considered the latest version. After the process is complete, the revised document is considered the latest released version.
Depending on the setting of the CollectionReleasedOnly configuration variable, users with read access to the content item see either the latest version or nothing if the item is not released. Authors, however, always see the latest version. By default, this variable is enabled and displays the latest version to all users with read access.
For information about the CollectionReleasedOnly configuration variable, see Oracle Fusion Middleware Configuration Reference for Oracle WebCenter Content.
6.2.1.6 Local Contribution Folders
The local folders function enables the mapping of a contribution folder structure to a local file system on the host system (not the user's system). Changes to the folder, its subfolders, and content items are reflected in the local directory. To allow users to access and modify files in the local directory, map the local folder to a shared drive and allow access using standard folder permissions.
Use local folders to manage content, such as the files on a website, which contain links to other files in the same folder hierarchy. In Content Server, individual content items are stored according to security groups and content types, not folder locations. Hyperlinks between Web pages do not work if accessed directly from Content Server. Local folders lets you place content items in a folder hierarchy to preserve the link relationships between content items.
The following outline describes how this function could be used for website management:
-
A Web designer creates a website that contains several Web pages with internal hyperlinking in a multilevel directory structure.
-
Through a WebDAV client, the designer copies the entire website structure to a contribution folder called
WebSite. -
On the Local Folders page, the
WebSitefolder is mapped to a directory on a shared drive,Z:\Intranet. -
The
\Intranetdirectory is set up as a Web server virtual directory. -
Users can access the website from the
Z:\Intranetdirectory without logging in to Content Server. Web pages can be updated in Content Server, and they are replicated to the local directory automatically.
Consider the following information when using local folders:
-
Content Server security does not apply to folders or content items in the local directory.
-
Only content items with a status of "Released" appear in the local directory. Items that fail conversion, are still being indexed, are in a workflow, or have a future release date are not available in the local directory.
-
Only the latest revision of a content item is available in the local directory.
-
Modifying directories or files directly in the local file system can cause problems with the local folder mapping. All changes must be made through the Content Server Contribution Folders interface.
-
To restrict access for specific files to only users who belong to a specific security group, point local directories to
/weblayoutsecured directories.
6.2.1.7 Contribution Folder Archiving and Searching
The steps used to export the folder hierarchy structure are different from the steps used to archive folder content. The following considerations apply to exporting and archiving folder information:. Content can be archived in a separate step using Archiver.
-
You can export and import the folder hierarchy structure from the Contribution Folders administration interface.
-
You can import and export content items with Archiver.
-
When you export the folder hierarchy, the entire structure is exported. You cannot specify a particular folder.
-
The folder hierarchy is exported to a text file in HDA format, which Content Server can import.
Caution:
When you import a folder archive file, all content items are removed from the repository and replaced by the imported folder hierarchy.
If the CollectionSearchRecursiveContent configuration variable is set to true, when users click Search on the interface, a Browse button and field are displayed in the Results Options section of the Search page. Click Browse to find and select a folder, including its subfolders, to be searched.
6.2.1.8 Optimizing Performance
This section provides guidelines for improving performance with Contribution Folders and WebDAV enabled:
-
Limit the number of contribution folders, especially unused ones. The more folders used, the more RAM is required by the folder cache. If a large number of folders is needed, increase the memory available. To allocate more memory, set the
-Xmx JAVA_OPTIONSparameter to a high enough value to accommodate the memory requirements and avoid getting errors. -
Limit the number of folders and content items in contribution folders. If the number of folders, content items or both in a contribution folder is too high, it can affect performance. When browsing through folders, each item in a folder is processed by the server, the network, and the client browser. Each item takes time and resources at each of these steps. The amount of time is dependent on many factors. A rule of thumb is that each item adds a few milliseconds to browsing response time and a few kilobytes to the size of the page displayed in the browser. The number of items in a folder only affects browsing, not searching.
High numbers of folders, content items or both in a contribution folder can affect the user experience. Users can have a harder time finding things in folders that contain a large number of items.
Therefore, limit the number of folders and content items per contribution folder. The recommended maximum number for both folders and content items per folder is 1,000. Specify these limits during the Contribution Folders/WebDAV software installation or modify the limits later. For more information on setting folder and file limits, see Section 6.2.2.1.
-
Perform regular database maintenance. When a system has a large number of content items and folders, Contribution Folders performance is affected by database performance. Perform periodic (for example, monthly) database maintenance to verify there is enough RAM, the indexes are optimized, and the database is not too fragmented.
-
Relax security to allow users without the appropriate access privileges to see (not access) secure content or folders. The
CollectionContentSecurityandCollectionFolderSecurityvariables control if users can see secure content or folders on Exploring pages if they have no access privileges to the content. If these variables are set to 'false' (not the default), users with no access privileges to secure content items or folders see them on Exploring pages. However, if they try to view the content, an access-denied error is displayed. This setting speeds up browsing performance because it simplifies the queries (less filtering), but it does allow users to see some information about secure content which they cannot access. -
Limit the number of items and folders displayed on Exploring pages. Set the
CollectionDisplayResultSetSizeconfiguration variable to control the maximum number of items displayed on Exploring pages. If the number of items in the result set exceeds the specified number, the results are truncated and spread over multiple pages. Navigation links allow movement between pages. Use this setting to prevent extremely large pages from being generated. -
Remove selected options from the Actions menu for items on Exploring pages. The following configuration variables remove certain menu options from the Actions menu next to the Info icons on Exploring pages:
-
CollectionInfoEnabled: Folder Information and Content Information options -
CollectionLinkEnabled: Create Shortcut option -
CollectionMoveEnabled: Move option -
CollectionDeleteEnabled: Delete option
-
6.2.1.9 Metadata Inheritance
When creating a new folder or checking in new content into a folder, the metadata from the parent folder automatically populates the fields for the new folder or the new content item. The folder initially inherits the metadata, but can change its values without affecting the parent folder. Later changes to a parent folder's metadata do not affect the metadata for existing subfolders or content checked in to a folder.
There are times when items checked in to a folder should not inherit the parent folder's metadata values. For example, you can create a folder with the metadata field of ReadOnly set to true to prevent renaming, moving, or deleting the folder but allow content to be checked in to the folder.
If content checked in to the folder inherits the folder's metadata value of true for the ReadOnly field, that content cannot be deleted, even by its author. You may want to have a folder set to ReadOnly, but you may want content checked in to the folder to not inherit the value of true for ReadOnly so deletions are allowed.
The value of the ReadOnly field can be set to false for content checked in to the folder on the check-in page through the browser interface. If content is checked in through WebDAV, the value of this field cannot be changed at check-in time.
Follow these steps to prevent inheriting value from the parent folder. This example uses the ReadOnly field, but any metadata field can be used.
-
Locate the
/custom/Folders/resourcesdirectory. -
Copy the existing
folders_forcemeta_resource.hdafile to another name as backup. -
Open the
folders_forcemeta_resource.hdafile in a text editor. -
Edit the file as follows. The ResultSet is similar to the following:
@ResultSet METADATA_OVERRIDE 2 name value xReadOnly 0 @end
-
Save the file.
-
Restart Content Server.
6.2.2 Configuring Contribution Folders
Folder performance can be optimized in the following ways:
6.2.2.1 Setting Folder and File Limits
To modify the maximum number of folders and content items in a contribution folder:
-
Choose Administration then Folder Configuration from the Main menu.
-
On the Virtual Folder Administration Configuration page, enter a number in the Maximum Folders Per Virtual Folder field. If a user attempts to define more than this number of contribution folders, an error message is displayed.
-
Enter a number in the Maximum Content Per Virtual Folder field. If a user attempts to check in more than this number of content items, an error message is displayed.
-
Click Update.
6.2.2.2 Enabling and Disabling System Folders
To enable a system-level hierarchical folder that was disabled:
-
Choose Administration then Folder Configuration from the Main menu. Choose System Folder Configuration.
-
On the System Folder Configuration page, click the gray icon next to the folder to enable it.
The folder is enabled and the folder Exploring page for the folder opens. Users can see the enabled folder.
To disable a folder, follow the same procedure. Click the green icon next to a folder to disable it.
6.2.2.3 Disabling the Trash Bin
To disable the Trash Bin after the initial Contribution Folders setup:
-
Choose Administration then Folder Configuration from the Main menu. Choose System Folder Configuration.
-
On the System Folder Configuration page, click the green dot next to Trash to disable the Trash Bin.
Any content deleted from folders is permanently deleted rather than being moved to the Trash Bin. Content, after it is deleted, can no longer be restored.
Note:
Disabling the Trash Bin can be particularly useful when using Site Studio.
6.2.2.4 Defining System Default Metadata
To define the system default metadata to be applied on initial check-in:
-
Choose Administration then Folder Configuration from the Main menu. Choose Folder Configuration then System Default Information Field Configuration.
-
On the System Default Information Field Configuration page, specify the default values to be applied to content upon check-in. Idoc Script can be used in any information field.
-
Click Update.
These defaults are applied to any content checked in through a contribution folder only if a value is not defined for the folder or by the user.
6.2.2.5 Configuring Metadata Propagation
To configure metadata propagation:
-
Choose Administration then Folder Configuration from the Main menu. Choose Folder Configuration then Information Field Inherit Configuration.
-
On the Information Field Inherit Configuration page, select check boxes for the metadata fields to be propagated.
-
Click Update.
When a contributor clicks Propagate on a Hierarchical Folder Information page, only the selected metadata values are propagated.
To propagate the inhibit setting itself, select the check box for the Inhibit Metadata Update field on the Information Field Inherit Configuration page. However, the inhibit setting only propagates from false to true or false to blank, and not from true to false or blank to false. Any folders and content items set to true or blank are not included in the propagation process.
6.2.2.6 Hiding Metadata Fields Globally Except for Specific Folders
To hide one or more metadata fields globally for all folders and for new check-ins, but allow those metadata fields to be visible for checking in content using specific WebDAV contribution folders:
-
Choose Administration then Admin Applets from the Main menu. Choose Configuration Manager then the Rules tab.
-
On the Configuration Manager: Rules tab, click Add to add a rule. Enter information for the rule name and description.
-
In the General tab, select is Global rule with Priority and Use rule activation condition.
-
Click Edit next to the User rule activation condition check box.
-
Click Add to add a condition.
-
Highlight the condition and select the Clause tab.
-
In the Field menu, select Folder.
-
In the Operator menu, select Not Equals.
-
In the Value menu, enter the
xcollectionIDof the folder where the metadata field appears. The xcollectionID is located in the database Collections table under dCollectionID. -
Click Add to add the clause to the Clause section.
-
Click OK.
-
-
Select the Fields tab from the Edit Rule page.
-
Click Add and select the field to hide.
-
Click OK.
-
On the Type menu of the Add Rule Field page, select Hidden.
-
Click OK.
-
In the main Edit Rule page, click OK.
-
Test the configuration by adding content to a non-specified folder. The field is hidden. Try adding content to the folder specified in the rule. The field is visible. If multiple folders are required to display the fields, more conditions are required within the clause of the same rule.
6.2.3 Working with Contribution Folders
This section discusses common tasks involved in managing contribution folders:
6.2.3.1 Managing Local Folders
This section discusses the following topics in the management of local folders:
6.2.3.1.1 Specifying Local Folders
To map a contribution folder structure to a local file system on the host system:
-
Choose Administration then Folder Configuration from the Main menu. Choose Folder Configuration then Local Folders.
-
On the Local Folders page, click Browse.
-
Click the folder to be mapped to the file system. Navigate to a higher-level folder to display its subfolders. The target folder is the open folder.
-
Click OK.
The target folder is entered in the Folder field.
-
Enter a directory name in the Local Directory field.
For example, c:/my_website.
-
Click Add.
If necessary, the directory is created on the file system and the specified folder structure is replicated to the specified directory.
6.2.3.1.2 Rebuilding Local Folders
To rebuild the directory structure for a folder that is mapped to a local file system:
-
Choose Administration then Folder Configuration from the Main menu. Choose Folder Configuration then Local Folders.
-
On the Local Folders page, click Rebuild for the
folder/directorymapping to rebuild.The directory (and all subdirectories and files) is deleted from the local file system, and the folder structure is re-copied to the directory.
6.2.3.1.3 Removing Local Folders
To delete a local folder mapping:
-
Choose Administration then Folder Configuration from the Main menu. Choose Folder Configuration then Local Folders.
-
On the Local Folders page, click Remove for the folder/directory mapping to delete.
The directory (and all subdirectories and files) is deleted from the local file system, and the mapping is removed from the Local Folders page. A mapped contribution folder cannot be deleted until local folder mapping is removed.
6.2.3.2 Archiving Contribution Folders
This section discusses the following topics regarding archiving folders:
6.2.3.2.1 Exporting an Archive
Depending on the size of the folder hierarchy that is being exported as an archive file, the default heap size value for the JVM may not be adequate. If memory errors are issued during the export procedure, increase the heap size.
To export the folder hierarchy as an archive file:
-
Choose Administration then Folder Configuration from the Main menu.
-
On the Virtual Folder Administration Configuration page, click Export Archive.
-
Click Save.
-
Navigate to the directory to save the folder archive file.
-
Specify a new file name to easily identify the archive file (for example,
101127_CollectionArchive).In Windows, the file type is left as Text Document and a .txt extension is appended to the file name (for example, CollectionArchive.hda.txt). To save the file with just the .hda extension, select the All Files file type.
-
Click Save.
The folder hierarchy is exported to the specified file.
6.2.3.2.2 Importing an Archive
To import an archived folder structure:
Caution:
This procedure removes all content items in the current folders and replaces them with the imported folder hierarchy. Typically, perform this procedure only on an Content Server that has no content items in the repository.
-
Choose Administration then Folder Configuration from the Main menu.
-
On the Virtual Folder Administration Configuration page, click Browse and navigate to the archive file to import.
-
Click Open.
The path and file name appear in the field.
-
Click Import Archive.
-
Click OK.
The archived folder is imported and re-created.
6.2.3.3 URL-Mapped Folders
To map a URL to a folder, choose Administration then Folder Configuration from the Main menu. Select the Web Url Mapped Folders option. Select a folder and URL for it from the provided list. For more information about mapping Web URLs, see Administering Oracle WebCenter Content.
6.3 Managing WebDAV
WebDAV is automatically installed and enabled with Content Server. It provides a way to remotely author and manage Oracle content using clients that support the WebDAV protocol.
For example, you can use Windows Explorer to manage folders and files or use Microsoft Office products to check in, check out, and modify content in the Oracle repository rather than using Oracle's Web browser interface. The WebDAV protocol is specified by RFC 2518.0. For more information, see the WebDAV Resources page at http://www.webdav.org.
Important:
WebDAV does not support the use of non-ASCII characters in user names.
For information about using the WebDAV interface, see Using Oracle WebCenter Content.
This section discusses the following topics:
6.3.1 Understanding WebDav
WebDAV provides support for the following authoring and versioning functions:
-
Version management
-
Locking for overwrite protection
-
Web page properties
-
Collections of Web resources
-
Name space management (copy/move pages on a Web server)
-
Access control
When WebDAV is used with a content management system, the WebDAV client provides as an alternate user interface to the native files in the content repository. The same versioning and security controls apply, whether an author uses the Oracle Web browser interface or a WebDAV client.
In Content Server, the WebDAV interface is based on the folder interface provided by either the Folders (FrameworkFolders) component or by the Contribution Folders (Folders_g) component. Except where noted, WebDAV functions similarly for both components.
This section discusses the following topics:
6.3.1.1 WebDAV Clients
A WebDAV client is any application that can send requests and receive responses using the WebDAV protocol. Typically, a WebDAV client requires no additional setup.
Although there are many applications that support the WebDAV protocol to some degree, Content Server is tested with, and supports the following:
-
Microsoft Windows Explorer
-
Microsoft Word 2002 (XP) through 2010
-
Microsoft PowerPoint 2002 (XP) through 2010
-
Microsoft Excel 2002 (XP) through 2010
Windows Explorer can be used to manage files created in a non-WebDAV client, but the native application cannot be used to check content in to and out of the repository.
Note:
Do not confuse the term WebDAV client with Oracle WebDAV Client, which is a separate Oracle product that enhances the WebDAV interface.
Oracle also offers Oracle WebCenter Content: Desktop, which can enhance the WebDAV client environment by more closely integrating with Windows Explorer, Microsoft Outlook, Lotus Notes, and other applications. For more information, see the Oracle Fusion Middleware Using Oracle WebCenter Content: Desktop.
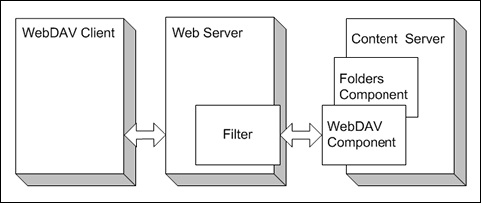
6.3.1.2 WebDAV Architecture
WebDAV support is implemented through a component which handles WebDAV requests directly. A WebDAV request follows this process (as illustrated in Figure 6-1):
-
The WebDAV client makes a request to Content Server.
-
The message is processed by the Web server through a custom filter.
-
On the Content Server, the WebDAV component performs the following functions:
-
It recognizes the client request as WebDAV.
-
It maps the client request to the appropriate WebDAV service call.
-
It converts the client request from a WebDAV request to the appropriate request.
-
It connects to the core Content Server and executes the request.
-
-
The WebDAV component converts the response into a WebDAV response and returns it to the WebDAV client.
Important:
WebDAV uses several nonstandard HTTP methods, including PROPFIND, PROPPATCH, MKCOL, DELETE, COPY, MOVE, LOCK, and UNLOCK. Many third-party applications-such as firewalls, proxy servers, load balancers, and single sign-on applications, do not allow these methods by default. If your network includes any of these applications, you may have to reconfigure them to allow the WebDAV methods.
6.3.1.3 WebDAV Folders
You connect to a WebDAV folder as you would a networked location. The credentials used are the same as those for the standard browser interface for Content Server. Folders and folder content can be used as defined by your user permissions. For example, if you have Read permission for a content item, you can view the file, but you cannot check in a revision to the file.
The WebDAV interface provides a subset of the options available through the browser interface. In general, users can create, delete, move, and copy content items and folders and modify and check in content items. To check out content items through the WebDAV interface, use a WebDAV client that can open the file. To perform other management tasks, such as specifying or propagating metadata values, use the standard browser interface.
For more information about creating a connection to a WebDAV folder and using WebDAV folders to manage content, see Using Oracle WebCenter Content.
6.3.1.4 Multiple Concurrent Language Support
To support multiple concurrent languages, certain WebDAV properties (metadata fields) should only contain characters that are displayable in all of the languages you intend to support. For example, in a multiple language environment that supports both English and Japanese, an English desktop would have trouble displaying Japanese (double-byte) characters.
In addition, different WebDAV clients provide different levels of support for characters within the ASCII character set. To ensure that WebDAV property fields are displayable in your WebDAV client, the values in those fields must contain only characters that are supported by your client. For more information about character support for your WebDAV client, see the product documentation for your WebDAV client.
Note:
To ensure compatibility between languages and WebDAV clients in a multiple language environment, folder names and certain Content Server fields should only contain characters that are displayable in all languages and in all WebDAV clients you intend to support. This is not a limitation of the Content Server fields themselves, but of the language mix and the WebDAV client environment.
Folder and File Names
It is recommended that you limit folder and file names to the printable ASCII character set (ASCII characters 32 to 128). In addition, folder and file names cannot contain the following characters:
? # & ? \ * " | < > :
Microsoft Web Folders WebDAV Client
The following fields must conform to the compatibility standard you establish for your multiple language environment:
-
the content name (dDocName)
-
the original content name (dOriginalName)
-
the content title (dDocTitle)
-
the folder names
Oracle WebCenter Content Desktop WebDAV Client
The following fields must conform to the compatibility standard you establish for your multiple language environment:
-
the content name (dDocName)
-
the original content name (dOriginalName)
-
the content title (dDocTitle)
-
the content type (dDocType)
-
the content item author (dDocAuthor)
-
the security group (dSecurityGroup)
-
the folder names
6.3.2 Configuring WebDAV
After installing WebDAV, most of the WebDAV system administration tasks can be done from folders Web pages.
This section discusses the following topics:
6.3.2.1 WebDAV Connection Strings
When creating a Content Server connection, the user must provide the WebDAV URL for that server. Each defined connection must have its own, unique WebDAV URL. Do not have two server connections on the computer that use the exact same WebDAV URL. The WebDAV URL typically has the following form:
http[s]://host-name:[port]/web-root/idcplg/webdav
For example:
http://server:7044/idc/idcplg/webdav http://server.example.com:16200/cs/idcplg/webdav https://server/cs/idcplg/webdav
With the use of a form-based login, WebDAV connection strings now require the _dav root before the web root. For example:
http://host_name:16200/_dav/cs/idcplg/webdav/
6.3.2.2 Default Content Item Naming
When users check new content in through a WebDAV folder, they cannot explicitly set metadata values such as the title for the content item. As a general rule, content items inherit any metadata defaults specified for the folder.
In the case of the content item title (dDocTitle), it is always set to the original file name (dDocOriginalName) except as noted below:
-
Folders Default: For Folders (FrameworkFolders component), if the folder specifies a title as part of its default metadata, the title specified by the folder is used as the document's title.
-
Contribution Folders Default: For Contribution Folders (Folders_g component), if the folder specifies a title as part of its default metadata, and the
CollectionDocTitleOverrideconfiguration variable is set to 1, the title specified by the folder is used as the document's title. Modify the variable setting in theIntradocDir/config/config.cfgfile.
6.3.2.3 Security and WebDAV
The following security features are included in WebDAV:
-
Access: The user logins and security controls in the folders component and Content Server also apply to content that is managed using WebDAV clients. For example, if you have Read permission for a content item, you can view the file, but you cannot check in a new revision to the file.
-
Login Cookie: When a user logs in to Content Server through a WebDAV application, the WebDAV component sets a cookie in the client. The cookie remains set if a WebDAV request is made within the time specified by the
WebDAVMaxInactiveIntervalconfiguration parameter. The default is 3600 seconds, or one hour. The cookie remains set even if the WebDAV client application closes. If the cookie expires, the user must log in to Content Server again to perform WebDAV transactions through Microsoft Word, Excel, and PowerPoint.The cookie includes a cryptographic key that prevents unauthorized users from generating counterfeit cookies. The
WebDAVSecretKeyparameter is used to generate the key. To prevent WebDAV login cookies from being used on other Content Servers, change theWebDAVSecretKeysetting to a new, unique value for each instance that is accessed through WebDAV. -
Windows Explorer: If a user logs in to Content Server through Windows Explorer, the client retains the user login authentication within the shell. Even if the login cookie expires, Windows Explorer sends the user name and password to Content Server automatically, so the user is not prompted to log in. The only way to clear this is for the user to log out of Windows.
-
Personal Folders: Content Server creates a personal folder for each user (
/Users/username/). The Web interface prevents users from creating folders in the/Usersdirectory. To prevent users from having write access to the/Usersdirectory through the WebDAV interface, however, you must explicitly set permissions for the/Usersfolder. For example, you can give most users Read access to the folder, and allow only administrators to write to the folder. -
Session timeout: If a WebDAV client does not specify a session timeout value, the default timeout specified by the
WebDAVDefaultTimeoutsetting is used. If a file remains locked (checked out) for this amount of time with no activity in the session, an "undo check-out" is applied to any checked out content.
6.4 Managing Content Folios
Content Folios is an optional component that is automatically installed with Content Server. When enabled, it provides a quick and effective way to assemble, track, and access logical groupings of multiple content items from within the secure environment of Content Server. For example, you can assemble all items relevant to an upcoming brochure, such as images, logos, legal disclosures, and ad copy, and send them through a workflow process. After approval, you can download all associated content and send it for print.
This section discusses the following topics:
6.4.1 About Content Folios
A content folio is an XML file checked in to the repository that uses elements to define a hierarchical structure of nodes, slots, and specified content items. In practice, a content folio is a logical grouping, or a framework in which to structure content. Simple folios are a flat container, while advanced folios can nest content in a hierarchy within folders. With an advanced folio, the hierarchy can be set before, during, or after content items are assembled.
Content can be added to existing folios or the folios can be locked so changes cannot be made. Items can be added by searching the repository. You can add content items to an advanced folio by checking new items into the repository or by searching for existing content. An advanced folio can also contain hyperlinks to outside resources such as websites or shared network drives.
Content Folios adds the following functionality:
-
Organize content into a simple, flat folio structure
-
Organize content into an advanced hierarchical folio structure
-
Create pre-structured templates for selection when creating folios
-
Modify folio structure dynamically
-
Lock folio structure to prevent it from being modified dynamically
-
Lock content folios to prevent additions
-
Unlock folios to allow additions
-
Modify folios without tracking revisions
-
Take a snapshot of a folio to track revisions
-
Download renditions of folio content in .zip, .ppt, .pdf, or XML format
-
Create multiple unstructured content baskets for use in collecting content items
Several changes are made to Content Server during installation of Content Folios:
-
Additional metadata fields: The following metadata fields are added to record the current state of a folio or template:
-
CpdIsTemplateEnabled
-
CpdIsLocked
-
-
Additional views: The following views are added and are used on the Folio Edit page to communicate Content Folios tables to JavaScript:
-
NodPropertyView
-
LinkPropertyView
-
NodeRemovalTypeView
-
CpdTreeDisplayFunctionMapView
-
CpdPopupEditActionsView
-
ItemPropertyView
-
PneDocProfileView
-
-
Additional Relations: The GenericUserProfileRelation is used by PneDocProfileView.
-
Additional Tables: The following tables record the links that folios and content baskets have against content in the system:
-
CpdLinks
-
CpdArchiveLinks
-
CpdBasketLinks
-
CpdEditHistory
-
Changes made to Content Server remain even if Folios is disabled.
6.4.2 Creating and Using Content Folios
The structure of a folio can be based on a pre-defined template when it is created. The structure can also be modified when creating or editing the folio, as discussed in the following sections:
6.4.2.1 Creating and Editing Folio Templates
Folio templates are a predefined organization of nodes, subnodes, slots, and any content items required when creating a folio. The templates are XML files checked in to and are managed by Content Server. A template is selected for use when creating an advanced folio. A template can be edited or revised at any time. Revisions to a template are not applied retroactively to existing folios based on that template, but only apply to new folios created based on the template's new revision.
To create folio templates, you must have administration rights.
To create a folio template:
-
Choose Administration then Folio Administration from the Main menu. Choose Create Folio Template.
-
Save the folio template and check in the folio:
-
From the page Actions menu, select Save template.
-
Choose the profile to use with the template and click Next.
-
Enter the necessary check-in information, including a descriptive title for the template. Click Check In.
-
-
Add structure or content to the template on the Create/Edit Folio Template page and define the template properties.
The Structure tab of the Create/Edit Folio Template page is divided into three sections:
-
Folio Structure Pane: Shows the nodes, slots, and items that comprise the folio hierarchy. Right click within the folio structure area to display the following options on a contextual menu. Unless noted otherwise, the options are available for nodes, items, and slots:
-
Insert Selected Source Item: Inserts a selected item from the Source Items Pane in a slot. If the slot contains an item, it is replaced.
-
Insert Item by Search: Opens a search page to find an item to add to the folio in the selected node or slot. If the slot contains an item, it is replaced.
-
Insert Item by Checkin: Opens a check-in form used to add an item to be used n the selected node or slot. If the slot contains an item, it is replaced.
-
Remove Content Item: Removes content from a slot. It does not remove the slot. (items only)
-
Insert hypertext: Creates a new item in the structure that can establish a hypertext link to the specified URL.
-
Create Node or Slot: Creates a node or slot at the specified location.
-
Cut, Copy, Paste: Cuts or copies an item for later pasting if needed.
-
Delete: Deletes an item from the structure.
-
-
Element Info Pane: When a node, slot, or item is selected in the Folio Structure Pane, information about the selection is displayed and optionally modified. Modified information is written back to the XML file that is checked in. Unless noted otherwise, the following fields are available for nodes, items, and slots:
-
Name: Name of the object.
-
Description: Description of the object.
-
Attributes (items and slots): The uses and limitations of the object. Default attributes include the following:
Allow empty: The object can be left empty.
Lock content: Items cannot be deleted from the slot.
Removable: The object can be deleted.
Allow external: External link can be specified.
Restrict formats: Limits allowable content item formats through a comma-delimited list that maps formats to file extensions.
Allow folio: A folio can be specified in the slot.
Content profile: The content profile used when adding an item by search or check in.
Clone item: The associated item is cloned. A cloned item is copied and checked in as a new item when a folio based on the template is created. If an item is not cloned, the original content item is associated with any folio created using the template.
-
Attributes (nodes): Default attributes include the following:
Removable: The node can be deleted.
Children movable: Items and slots can be moved within the hierarchy.
Allow item creation: Items can be created within the node.
Allow node creation: Subnodes can be created within the node.
Maximum items, Maximum nodes: Specifies the total number of items allowed in the node.
Content profile: The content profile used when adding an item by search or check in.
-
Content ID: (items and slots). The ID of the item.
-
Create Date: (items and slots). The date a content item was created.
-
Last modified: (items and slots). The last date changes were made.
-
Link: (hyperlinks only): The URL of a hyperlink.
-
-
Source Items Pane: Used to collect items to be used in the folio.
-
-
Click Finish when done.
6.4.2.2 Adding Custom Viewers and Renderers
Content Server ships with a default viewer that mimics the structure of the Create/Edit Folios page, and the following rendition options:
-
Zip
-
PDF
-
XML
Custom viewers and renderers can be created, but such development requires an understanding of the following:
-
the structure of the folio XML
-
the folio Idoc Script functions and their proper usage
-
the Iterator/Renderer architecture
-
the method for using a component to modify/add to the list of viewers and renderers
To add custom viewers and renderers, contact Oracle Consulting at http://www.oracle.com/consulting/index.html.