17 Configuring Oracle Privileged Account Manager for Integrated Solutions
This chapter describes how to configure Oracle Privileged Account Manager for integration with commonly used directory and identity management technologies.
This chapter includes the following sections:
-
Section 17.2, "Integrating with Oracle Access Management Access Manager"
-
Section 17.3, "Integrating with the Credential Store Framework"
17.1 Integrating with Oracle Identity Manager
This section provides information about the Oracle Privileged Account Manager - Oracle Identity Manager integration process.
The topics include:
Note:
If you are using Oracle Privileged Account Manager on IBM WebSphere, refer to "Differences When Integrating with Oracle Identity Manager" in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management for information about this topic.
17.1.1 Overview
The integration of Oracle Privileged Account Manager and Oracle Identity Manager enables you to manage access to the LDAP groups that are also Oracle Privileged Account Manager grantees. Specifically, integrating these two products enables you to
-
Manage the identity lifecycle from hiring to retirement
-
Provide a native ability to automate adding and removing users to the proper LDAP groups based on their HR system updates
-
Provide the ability to manually request access to accounts
-
Support the ability to get approvals for requests
-
Support reporting that you can use for attestation reporting; either to augment or in-lieu of Oracle Privileged Account Manager's own reporting.
In addition, Oracle Privileged Account Manager leverages Oracle Identity Manager for workflow support. The integration points include:
-
Access to privileged accounts granted to roles in Oracle Privileged Account Manager by an Oracle Privileged Account Manager administrator
-
End users can request membership in these roles through Oracle Identity Manager
-
Standard Oracle Identity Manager workflow are used to approve these requests
-
Membership in the requested role results in end users getting access to the corresponding privileged accounts in Oracle Privileged Account Manager
To support this integration, Oracle Identity Manager
-
Populates the resource catalog with the proper enterprise roles and entitlements.
Oracle Privileged Account Manager target-accounts are entitlements because Oracle Identity Manager is not actually granting direct access to the actual account only a representation of that account.
Note:
If you are using Oracle Privileged Account Manager on IBM WebSphere, refer to "Differences in How Oracle Privileged Account Manager is Deployed in Oracle Fusion Middleware"in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management for information.
17.1.2 Before You Begin
This section describes some tasks you must complete before starting the actual integration process. These tasks include:
17.1.2.1 Installing Oracle Identity Manager
The instructions in this chapter assume you have already installed Oracle Identity Manager. If you have not yet installed Oracle Identity Manager, refer to the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management for instructions.
17.1.2.2 Configuring an Oracle Identity Manager Administrator
When you configure an Oracle Identity Manager administrator for this integration, that administrator must be able to perform these tasks:
-
Configure an Oracle Identity Manager rule that assigns new users to the proper LDAP groups based on a business rule. The rule should apply whether you assign the new users manually through the user screen or automatically by using an HR/text feed.
-
Use Oracle Identity Manager's native functionality to build requests for items in the Oracle Identity Manager resource catalog to ensure that the catalog is properly populated. Oracle Identity Manager enables users to request access to entitlements contained in the Oracle Identity Manager catalog.
-
Set approver fields to the proper values. For example, in situations where one employee requests access to the email account of another employee who will be away from the office for an extended period of time.
-
Handle "firecall" requests, where an Oracle Privileged Account Manager user must access a system that is outside the normal business process.
Firecall requests are handled based upon your business requirements and business rules. For example, if the Oracle Privileged Account Manager user is authorized for a target, but the access policy prevents that user from getting the password, then the Oracle Privileged Account Manager administrator can temporarily change the access policy for that target-account.
If the user cannot wait for Oracle Identity Manager, the Oracle Privileged Account Manager administrator can manually direct access (for example, add a specific grantee to the account) instead.
To review the steps for configuring an Oracle Identity Manager administrator, refer to "Managing Admin Roles" in the Oracle Fusion Middleware User's Guide for Oracle Identity Manager.
17.1.2.3 Configuring the External Identity Stores
You must configure an external identity store as the main authentication source for Oracle Privileged Account Manager. Refer to Section 3.3.2, "Configuring an External Identity Store for Oracle Privileged Account Manager" for more information.
After configuring the Oracle Privileged Account Manager external identity store, you must configure Oracle Identity Manager to use that same identity store. Refer to Oracle Identity Manager Connector Guide for Oracle Internet Directory for more information about setting up and configuring the LDAP connector you need for the server.
17.1.2.4 Creating LDAP Groups
Oracle Privileged Account Manager is optimized for managing shared and privileged accounts, such as root on an UNIX system.
Oracle Privileged Account Manager determines which users can check out passwords for accounts on a target, based on the grants those users have received. Grants can be made directly or through membership in groups. The groups themselves can be static or dynamic.
Ideally, these LDAP groups should match your enterprise roles. For example, if you have a "Data Center Product UNIX Administrators" enterprise role, you should have a corresponding LDAP group. The benefit of this match is that you can use these groups to control access to other applications besides Oracle Privileged Account Manager target-accounts.
Note:
To create an LDAP group, contact your LDAP administrator.
17.1.2.5 Adding the Oracle Privileged Account Manager CA Certificate
You must configure Oracle Privileged Account Manager's Catalog Synchronization task to include the Oracle Privileged Account Manager server's web service Certificate authority (CA) certificate or HTTPS web service calls to the Oracle Privileged Account Manager server cannot succeed.
This process is done in two steps:
Note:
If you are using Oracle Privileged Account Manager on an IBM WebSphere server, these steps are slightly different. Refer to "Differences When Integrating with Oracle Identity Manager" in the Oracle Fusion Middleware Third-Party Application Server Guide for Oracle Identity and Access Management for instructions.
To retrieve the Oracle Privileged Account Manager server's CA certificate:
-
From your browser, connect to the Oracle Privileged Account Manager server web service:
https://hostname:sslport/opam
-
Locate and save the CA certificate (
.pem) file to the truststore.
For example, from a Firefox browser-
Click the lock icon in the browser's address bar.

-
When the information dialog displays, click More information.
-
On the Page Info dialog, click View certificate.
-
On the Certificate Viewer dialog, select the Details tab to view the Certificate Hierarchy.
-
Select the first (root) certificate in the Certificate Hierarchy list, and then click Export.
-
When the Save Certificate to File dialog displays, navigate to the directory where you want to save the file. For example,
/tmp/opam.pem. -
Select X.509 Certificate (PEM) from the Save as type menu, enter
opam.pemas the file name, and click Save.
-
Run the following command to import the CA certificate file, opam.pem, into the WebLogic truststore on the server where you are running Oracle Identity Manager:
keytool -import -file FILE_LOCATION -keystore TRUSTSTORE_LOCATION -storepass TRUSTSTORE_PASSWORD -trustcacerts -alias ALIAS
Where
-
FILE_LOCATION is the full path and name of the certificate file.
-
ALIAS with an alias for the certificate.
-
TRUSTSTORE_PASSWORD is a password for the truststore.
-
TRUSTSTORE_LOCATION is one of the following truststore paths:
If You Are Using Then Import the Certificate to the Keystore in this Directory: Oracle
jrockit_R27.3.1-jdkJROCKIT_HOME/jre/lib/securityDefault Oracle WebLogic Server JDK
WEBLOGIC_HOME/java/jre/lib/security/cacertsJDK other than
Oraclejrockit_R27.3.1-jdk
or Oracle WebLogic Server JDKJAVA_HOME/jre/lib/security/cacerts
17.1.3 Setting Up Oracle Identity Manager for the Integration
Note:
These instructions assume that you have already installed Oracle Identity Manager and that you are an Oracle Identity Manager administrator who can perform the different configuration tasks described in this section.
To prepare Oracle Identity Manager for the integration you must perform the tasks described in the following topics:
17.1.3.1 Installing and Configuring the Generic LDAP Connector
You must download and install a generic LDAP connector file that works with your LDAP identity store as a target.
For installation instructions, refer to "Installing Connectors" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
17.1.3.2 Creating an Application Instance
After installing the connector, you must create an application instance and make it available to Catalog.
For instructions, refer to Part IV, "Application Management," in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
17.1.4 Running the opamSetup Script
For the Oracle Privileged Account Manager-Oracle Identity Manager integration to become operational, you must run the Oracle Privileged Account Manager-Oracle Identity Manager integration setup script (opamSetup), which is available in the following directory:
<OIM Oracle Home>/server/bin
Run one of the following commands to start the script:
-
For UNIX, use
opamSetup.sh -
For Windows, use
opamSetup.bat
opamSetup -oimUrl <OIM URL> -oimUser <OIM username> -oimPassword <OIM user password> -opamItResource <OPAM IT resource name> -opamServer <OPAM server name> -opamPort <OPAM server port> -opamUser <OPAM user> -opamPassword <OPAM user password> -idStoreItResource <ID Store IT resource name> [-ctxFactory <Initial context factory>] [-help]
where:
| Option | Description |
|---|---|
|
-oimUrl <OIM URL> |
Provide the URL address for the Oracle Identity Manager server. |
|
-oimUser <OIM username> |
Provide a Oracle Identity Manager log-in user name. |
|
-oimPassword <OIM user password> |
Provide the Oracle Identity Manager log-in password. |
|
-opamItResource <OPAM IT resource name> |
Provide the Oracle Privileged Account Manager IT resource name. |
|
-opamServer <OPAM server name> |
Provide the path and directory name for the Oracle Privileged Account Manager server. |
|
-opamPort <OPAM server port> |
Provide the Oracle Privileged Account Manager server port. |
|
-opamUser <OPAM user> |
Provide a Oracle Privileged Account Manager log-in user name. Note: You must be an administrator with the User Manager Admin Role and the Security Administrator Admin Role to run this command. |
|
-opamPassword <OPAM user password> |
Provide the Oracle Privileged Account Manager log-in password. |
|
-idStoreItResource <ID Store IT resource name> |
Provide the name of the IT resource in the identity store. |
|
-ctxFactory <Initial context factory> |
Provide the name of the context factory (usually |
|
-help |
Optional. Display usage options for this command |
Note:
If you inadvertently omit a parameter, you will be prompted to provide it.
The opamSetup script performs the following tasks:
-
Creates the Oracle Privileged Account Manager IT resource with the
opamServer,opamPort,opamUser, andopamPasswordset-up script parameters. -
Creates a UDF column named
OPAM_TAGSin the Oracle Identity Manager catalog. -
Creates an Oracle Privileged Account Manager synchronization scheduled job with the following characteristics:
-
Name: Oracle Privileged Account Manager Catalog Synchronization Job. If a job with this name already exists, the job appends
a -1to the name, thena -2, and so on. -
Schedule type: Periodic, runs every 15 minutes.
-
OPAMServerIdStoreItResource: The
idStoreItResourceparameter of the set-up script. -
OpamServerItResource: The
opamItResourceparameter of the set-up script.
-
-
Creates the
OIM.OPAM.Integrationsystem property (if it does not yet exist) and sets it totrue.
If any of these tasks fail, the script automatically executes the next task.
17.1.5 Creating the OPAM_TAGS UDF
After setting up the Oracle Privileged Account Manager-Oracle Identity Manager integration environment, you must manually create an OPAM_TAGS user-defined field (UDF) in the Oracle Identity Manager catalog. The OPAM_TAGS UDF enables Oracle Privileged Account Manager to search the Oracle Identity Manager catalog.
To manually create the OPAM_TAGS UDF, perform the following steps:
-
Open the Oracle Identity Manager Admin Console and log in to Oracle Identity System Administration.
-
Create and activate a sandbox.
Note:
For detailed instructions about creating and activating a sandbox, refer to the "Managing Sandboxes" section in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
-
In the left pane, under System Entities, click Catalog to open the manage Catalog page.
-
Click the Create a custom field icon.
-
When the Select Field Type dialog box displays, select the Text field type to create a text field. Click OK.
-
When the page to create a custom field displays, specify the following settings:
-
Appearance section: Type
OPAM tagsin the Display Label field. -
Name section: Type
OPAM_TAGSin the Name field and typeOPAM metadata tagsin the Description field. -
Constraints section: Check the Searchable box.
-
Maximum length: Type
256. -
Default Value section: Leave field blank.
-
Advanced section: Do not check any of the properties boxes.
-
-
Click Save and Close, then verify that the UDFs appear in the custom fields table.
-
Select the Manage Sandboxes tab and click Publish Sandbox.
Note:
For detailed instructions about publishing a sandbox, refer to the "Managing Sandboxes" section in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
17.1.6 Tagging Catalog Entries with Oracle Privileged Account Manager Metadata
The Oracle Privileged Account Manager Catalog Synchronization Job created by the opamSetup script tags the catalog entries with the Oracle Privileged Account Manager metadata. This job automatically runs every 15 minutes.
If you need to run the job immediately, instead of waiting for the next cycle to begin, you can manually perform the following steps from the Oracle Identity Manager Admin Console:
-
Click Scheduler.
-
When the new screen displays, search for and select the OPAM Catalog Synchronization job.
-
Click Run Now.
-
After the job finishes, click Refresh.
-
To verify that the job ran successfully, check the Job History view.
Note:
If you add new targets or accounts to Oracle Privileged Account Manager, you must run the Oracle Privileged Account Manager Catalog Synchronization Job again.
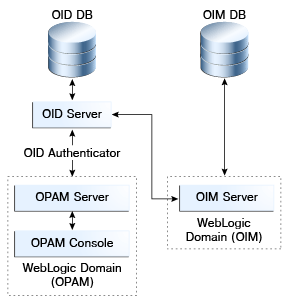
17.2 Integrating with Oracle Access Management Access Manager
This section explains how Oracle Access Management Access Manager (Access Manager) integrates with Oracle Privileged Account Manager. Using this integration scenario, you can protect Oracle Privileged Account Manager with Access Manager using a WebGate agent.
The topics in this section include:
17.2.1 Before You Begin
Before starting the procedure described in Section 17.2.2, "Enabling Single Sign-On," be aware of the following:
-
The instructions assume that you configured Oracle Internet Directory as the identity store; however, other component configurations are possible. Refer to the system requirements and certification documentation on Oracle Technology Network for more information about supported configurations.
-
In addition, the instructions describe a specific example of using Access Manager to protect URLs. Although they outline the general approach for this type of configuration, you are not limited to using the exact steps and components described here. For example, Oracle Internet Directory is one of several identity stores certified with Access Manager 11g.
-
You can use Oracle Adaptive Access Manager as an authentication option with Access Manager. Oracle Adaptive Access Manager provides strong-authentication and risk-based authorization that can be used to provide layered security for Oracle Privileged Account Manager.
To enable Oracle Adaptive Access Manager with Oracle Privileged Account Manager, select Access Manager as the authentication option for the WebGate that is protecting Oracle Privileged Account Manager.
-
If you deployed Oracle Identity Navigator with Oracle Privileged Account Manager, and you are using Oracle Identity Navigator as the user interface for Oracle Privileged Account Manager, you can also protect Oracle Identity Navigator with Access Manager while enabling Single Sign-On.
Refer to "Integrating with Oracle Identity Navigator" in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite for instructions.
-
Oracle Privileged Account Manager is protected by the domain agent out-of-the-box.
17.2.2 Enabling Single Sign-On
By default, the Access Manager 11g agent provides Single Sign On functionality for Oracle Privileged Account Manager and the following Identity Management consoles:
-
Oracle Identity Manager
-
Access Manager
-
Oracle Adaptive Access Manager
-
Oracle Authorization Policy Manager
-
Oracle Identity Navigator
The Access Manager agent can only protect consoles in a single domain. If your environment spans multiple domains, you can use Access Manager 11g WebGate for Oracle HTTP Server 11g. Configuring Oracle Privileged Account Manager for WebGate-based single sign-on is the same as configuring Oracle Identity Navigator. Refer to "Integrating with Oracle Identity Navigator" in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite.
You can use Access Manager to enable Single Sign On for the Oracle Privileged Account Manager's user interface by using any Access Manager authentication scheme as the challenge method.
The prerequisites are as follows:
-
Oracle HTTP Server has been installed.
When installing the Oracle HTTP Server, deselect Oracle WebCache and associated selected components with WebLogic domain (or WebSphere Cell).
-
Access Manager 11g has been installed and configured properly.
-
Oracle HTTP Server 11g has been installed and configured as a front-ending proxy web server for Oracle Privileged Account Manager.
-
Access Manager 11g WebGate for Oracle HTTP Server 11g has been installed on the Oracle HTTP Server 11g.
See Also:
Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management for details about installation of the listed components.
The high-level steps for enabling Single Sign On in Oracle Privileged Account Manager are as follows:
-
Use the Access Manager Administration Console to configure a new resource for the agent under which the Oracle Privileged Account Manager URL is to be protected. For information, refer to Section 17.2.2.1, "Configure a New Resource for the Agent."
-
Configure Oracle HTTP Server to point to the Access Manager domain which has the resources and policies configured. For information, refer to Section 17.2.2.2, "Configure Oracle HTTP Server for the Access Manager Domain."
-
Use the Administration Console to add the two new identity providers, namely the Access Manager Identity Asserter and the Oracle Internet Directory Authenticator. For information, refer to Section 17.2.2.3, "Add New Identity Providers.".
-
Use a WLST command to enable access to more than one application using multiple tabs in a browser session. For information, refer to Section 17.2.2.4, "Configure Access to Multiple Applications."
17.2.2.1 Configure a New Resource for the Agent
Perform these steps in the Access Manager administration console:
-
Select the Policy Configuration tab.
-
Under Application Domains, select the agent under which the Oracle Privileged Account Manager URL is to be protected (for example,
-OIMDomain). -
Choose Resources and click the create icon to add a new resource. Enter the type, host identifier and value, (
/oinav/…/*) and click the Apply button. -
Choose Protected Policy or the policy whose authentication schema is the LDAP schema. In the resources table, click the add icon and choose the Oracle Privileged Account Manager URL (
/oinav/…/*) from the drop-down list. -
Repeat the step for Authorization Policy.
17.2.2.2 Configure Oracle HTTP Server for the Access Manager Domain
Perform these steps to ensure that Oracle HTTP Server front ends the Oracle WebLogic Server container where Oracle Privileged Account Manager is installed.
-
Navigate to the Oracle HTTP Server server
configdirectory, for example,/scratch/mydir1/oracle/product/11.1.1/as_1/instances/instance1/config/OHS/ohs1), and find themod_wl_ohs.conffile. -
In the
<IfModule mod_weblogic.c>block, add the host and the port number of the Oracle Privileged Account Manager URL to be protected. For example:MatchExpression /oinav* WebLogicHost=host WebLogicPort=port
-
Restart the Oracle HTTP Server server in the OHS install
bindirectory, for example,/scratch/mydir1/oracle/product/11.1.1/as_1/instances/instance1/bin) by executing the following command:-./opmnctl restartproc ias=component=ohs1
17.2.2.3 Add New Identity Providers
Perform these steps to add two new identity providers:
-
Using the Administration Console, navigate to Security Realms, then myrealm, then Providers.
-
Add these two providers: Access Manager Identity Asserter and Oracle Internet Directory Authenticator.
-
Set the Control Flag of the Access Manager Identity Asserter to
Required. -
Update the following settings in the Oracle Internet Directory Authenticator:
-
Set the Control Flag to
Sufficient -
Select the Provider specific tab and make the necessary changes, supplying the host, port, and other credentials of the Oracle Internet Directory server. Configure the correct LDAP setting in the Oracle Internet Directory Authenticator.
The users and Groups in the LDAP will be reflected in the console.
-
-
Re-order the providers as follows:
-
Access Manager Identity Asserter
-
Authenticator
-
Default Authenticator
-
Default Identity Asserter
-
-
Restart Oracle WebLogic Server.
-
Enter the protected Oracle Privileged Account Manager URL, which will have the host and port from the Oracle HTTP Server install:
http://OHSHost:OHSPort/oinav/faces/idmNag.jspx
17.3 Integrating with the Credential Store Framework
This section explains how Oracle Privileged Account Manager integrates with Credential Store Framework (CSF).
The topics include:
17.3.1 Understanding Oracle Privileged Account Manager-Managed CSF Credentials
The Credential Store Framework (CSF) is an OPSS component that primarily provides secure storage for credentials. For example, many applications use CSF as a mechanism for storing application credentials.
Oracle Privileged Account Manager enables administrators to identify account credentials to be secured, shared, audited, and managed. In addition, Oracle Privileged Account Manager supports account lifecycle management activities such as periodic password modification.
Though many application developers use CSF to store application credentials for required targets (such as RDBMS and LDAP), there are certain aspects about how CSF is used that can potentially be improved, including:
-
Applications storing their credentials in CSF do not expect these credentials to be shared. Therefore, a given instance of CSF can have multiple references to the same credential. For example, multiple applications could be relying on the same physical credential and yet have multiple logical references.
-
Periodically modifying application credentials is necessary to satisfy compliance and internal IT policy requirements. However, modifying credentials (on the target and thereafter the CSF reference) remains a manual task, which is further complicated by the fact that there may be multiple references to the same credential in CSF. So, you must change the password or credential on the target and then manually update all references to that password in CSF.
Oracle Privileged Account Manager can automate this process, but automating the periodic modification of credentials is also complicated by the potential for multiple references that cannot be accurately traced.
Oracle Privileged Account Manager leverages its account lifecycle management feature to empower lifecycle management of application credentials stored in CSF.
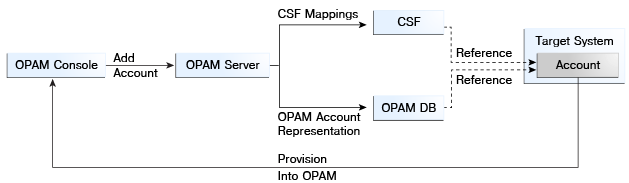
17.3.2 Provisioning
If you decide that Oracle Privileged Account Manager will manage a particular account credential, then that credential must be provisioned through Oracle Privileged Account Manager. The following figure illustrates this provisioning process.
The administrator
-
Adds an Oracle Privileged Account Manager target (if required).
-
Adds the Oracle Privileged Account Manager privileged account or credential to the target, which must include the necessary CSF mappings.
Note:
CSF mappings are the mechanism by which a specific credential instance is uniquely identified within CSF.
The Oracle Privileged Account Manager server stores the CSF mappings along with its representation of the privileged account. The Oracle Privileged Account Manager server creates instances of the credential in CSF that correspond to the provided mappings.
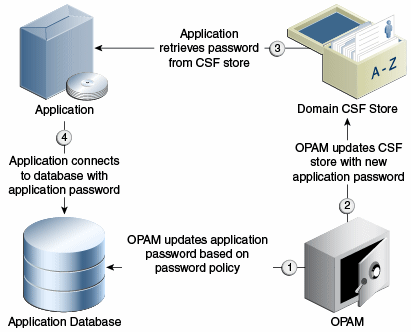
17.3.3 Lifecycle Management
An account provisioned as described in Section 17.3.2, "Provisioning" can have an associated Password Policy that governs password construction, periodic modification requirements, and so forth.
Oracle Privileged Account Manager normally honors and performs actions on the policy. However, whenever an administrator modifies an account credential that has associated CSF-mappings, Oracle Privileged Account Manager also updates the credential instances stored in CSF with those mappings (as shown in Figure 17-3). This update ensures that all relevant parties have access to the latest credential and allows the seamless management of password lifecycle events such as periodic modification.
17.3.4 Application Consumption
Using Oracle Privileged Account Manager to manage an application's credentials places no additional burden on that application. The only process change that occurs is that the credential must first be provisioned through Oracle Privileged Account Manager into Oracle Privileged Account Manager and CSF.
Oracle Privileged Account Manager pushes the credential to CSF with the administrator-provided mappings (as shown in Figure 17-3). If those mappings remain constant, the application can continue to access the credentials directly through CSF.