| Oracle® Communications Service Broker Online Mediation Controller Implementation Guide Release 6.1 E29452-02 |
|
|
PDF · Mobi · ePub |
| Oracle® Communications Service Broker Online Mediation Controller Implementation Guide Release 6.1 E29452-02 |
|
|
PDF · Mobi · ePub |
This chapter describes the steps required to configure Oracle Communications Online Mediation Controller as a Remote Authentication Dial In Service (RADIUS) Manager. Online Mediation Controller supports RADIUS authentication and authorization integration with Oracle Communications Billing and Revenue Management (BRM). Network requests can also be routed to Oracle Communications Elastic Charging Engine (ECE) for authorization.
See "Setting Up RADIUS Mediation for Accounting", for information on setting up Online Mediation Controller for use with BRM or ECE RADIUS accounting.
Online Mediation Controller translates RADIUS authentication and authorization requests to requests that BRM and ECE understands. The Portal Connection Protocol (PCP) is used for communication with BRM while the ECE Authentication API is used for ECE.
Figure 9-1 shows the Online Mediation Controller components that you need to set up and configure to apply the BRM or ECE authentication and authorization services in a network supporting authentication and authorization with RADIUS.
Figure 9-1 Online Mediation Controller Components for Authentication and Authorization
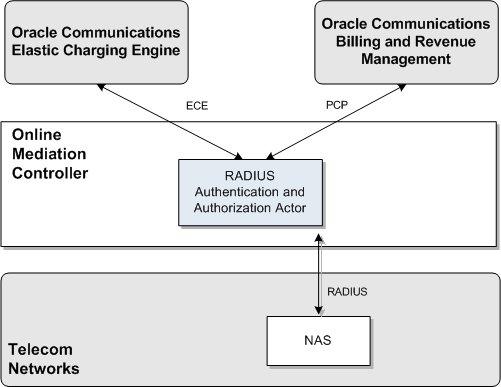
To set up Online Mediation Controller to perform RADIUS Authentication and Authorization mediation to BRM or ECE, you need to configure the following Online Mediation Controller components:
SSU RADIUS
SSU PCP or SSU ECE
RADIUS Authentication module
See BRM documentation for information on how authentication and authorization is done in BRM.
See the documentation for oracle.communication.brm.charging messages.query in Oracle Communications ECE Java API Reference for information on the ECE Charging API.
To create an end-to-end configuration for RADIUS authentication and authorization:
Configure the SSU RADIUS. See "Configuring the SSU RADIUS" for more information.
Create a set of client profiles and AVP filters for requests and responses. See "Configuring a Client Profile and AVP Filters" for more information.
Create a set of Proxy Realms. See "Adding Proxy Realms" for more information.
Configure the SSU PCP or SSU ECE to connect to BRM or ECE, respectively. See "Connecting to BRM Through PCP" or "Connecting to ECE Using the ECE API" for more information.
Configure RADIUS Mediation. See "Configuring RADIUS Mediation", for more information.
Configure the SSU RADIUS for accounting requests as described in ”Configuring the SSU RADIUS” in Oracle Communications Service Broker Signaling Server Units Configuration Guide. Use the following configuration data, specifically:
Create a new incoming routing rule.
Set the parameter Name to the rule name to use.
Set Local Realm to any. This is a case-sensitive field.
Set Alias to the instance name that you are going to use for the RIMOFCFRADIUS instance.
The complete string to enter in the Alias fields is:
ssu:rimofcfradius.RIMOCFRADIUS@ocsb.com
Click Apply.
To create a client profile:
In the SSU RADIUS Configuration screen, click the RADIUS tab.
Click the Client Profile tab. Click the ClientProfile sub tab to define the RADIUS client profile properties.
Click New.
In the New window enter the following information:
In the Client Address field, enter the address or address range for the RADIUS Network Authentication Server (NAS) client(s) to configure. You can define a single IP address or host name, or a group of RADIUS clients, if entered as a regular expression.
In the Client NAS Identifier field, enter the ID of the client NAS. This can be a fully qualified domain name.
In the Authentication Shared Secret Key field, enter the key in the Credential Store that maps to the secret in the Credential Store used to identify authentication requests from the NAS client.
For more information about the Credential Store, see Service Broker Security Guide.
In the accountingSharedSecretKey field, enter the key in the Credential Store that maps to the secret in the Credential Store used to identify accounting requests from the NAS client.
Click OK.
Click the Avps to copy from Request to Response tab.
Choose the client profile to apply the filter to from the Parent drop-down list. The index of the client profile correlates to the keyId assigned to the client profile.
To add additional AVPs in incoming requests needed in the response:
Click New.
In the New: window enter:
In the Attribute Name field, enter the name of an AVP included in the request and shall be included in the response.
Click Apply.
To a add a proxy realm to proxy requests to:
In the SSU RADIUS Configuration node, click the RADIUS tab.
Click the Proxy Realm tab.
Click New.
In the New window enter:
In the Name of the proxy realm field, enter a name for the RADIUS server to proxy requests to.
In the Username Match Criteria field, enter the username matching criteria. Use a regular expression matching the realm part of the username attribute in the request. For example, enter isp1.net for any user that belongs to isp1.net.
In the Authentication Shared Secret Key field, enter the key in the Credential Store that maps to the secret in the Credential Store used to identify authentication requests from the NAS client. For more information about the Credential Store, see Oracle Communications Service Broker Security Guide.
In the Accounting Shared Secret Key field, enter the key in the Credential Store that maps to the secret in the Credential Store used to identify accounting requests from the NAS client.
In the Request Timeout field, enter the number of seconds to wait for a response before a request times out and is retried.
In the Number of Retries field, enter the number of times to retry a request before it is considered failed.
Click Apply to save your configuration.
To connect Online Mediation Controller to BRM:
Create BRM connection pools in the SSU PCP. See the discussion on connection pools in the chapter on configuring the PCP signaling server unit in Oracle Communications Service Broker Signaling Server Units Configuration Guide for more information.
For additional information on BRM connection pools, consult the chapter on connection pools in Oracle Communications Billing and Revenue Management System Administrator's Guide.
Secure the BRM connection pools created in step 1, as described in the PCP signaling server configuration chapter in Oracle Communications Service Broker Signaling Server Units Configuration Guide.
In the Administration Console:
Expand OCSB.
Expand Signaling Tier.
Select SSU PCP.
Select the PCP tab.
Select the Credential Store tab.
In the Password area, enter the ID of the connection pool that you want to secure in the Key field. This should be the Pool ID you assigned to the connection pool created in step 1.
In the Password area, enter the password of the BRM client application account used by the connection pool to access the BRM in the Password field. This should be the password of the account you configured in the BRM CM Login ID field when you initially defined the connection pool.
In the Password area, uncheck the One-way check box.
In the Password area, click Set.
Repeat the Administration Console steps for each connection pool you want to secure.
Define destination BRM applications, as described in "Defining PCP Network Entities" in the chapter "Configuring the PCP Signaling Server Unit" in Oracle Communications Service Broker Signaling Server Units Configuration Guide.
Click Commit to save your configuration.
To connect Online Mediation Controller to ECE:
In the Administration Console:
In the navigation tree, expand OCSB.
Expand Signaling Tier.
Select SSU ECE.
Select the ECE tab.
Click the Coherence tab.
Populate the ECE Protocol Adapter values used to connect to ECE using the information below. Consult your ECE administrator for specific information about the ECE implementation in your environment.
In the Coherence cluster name field, enter the name of the Coherence cluster on which ECE runs. A default value of BRM is entered.
In the JMX management read-only field, set whether Mbeans exposed by the ECE Coherence node allow operations that modify run-time attributes. The default value is set to FALSE.
In the Coherence log file name field, provide a string used when logging is enabled. By default, the log is located in the same directory as where the managed server is started.
In the Coherence log level field, enter the log level for the ECE Coherence cluster. The possible numeric values range from -1 to 9. There is no default value. See Oracle Coherence User Guide, for more information on setting Coherence logging levels.
In the Use ECE well known address field, select the boolean indicating whether a well known address (WKA) for ECE will be used. Multicast address is not supported when WKA is used.
In the Well know address 1 (ip:port) field, provide the first WKA IP address and port number of the ECE Coherence cluster.
In the Well know address 2 (ip:port) field, provide the second WKA IP address and port number of the ECE Coherence cluster.
In the Multicast address (ip:port) field, provide the IP address and port number of the ECE Coherence cluster when using multicast.
In the Multicast TTL field, enter in a value for the multicast time-to-live setting. This value determines the maximum number of hops a packet may traverse. Legal values are from 0 to 255.
In the Use SSL connection field, select the boolean indicating whether to use a secure connection to ECE. The default value is FALSE. See the discussion on securing SSU ECE in Oracle Communications Service Broker Signaling Server Units Configuration Guide, for more information on setting up the SSL connection to ECE.
See Oracle Communications Elastic Charging Engine Administration Guide, for additional information on configuring ECE.
Select the General tab to set the general parameters listed in Table 9-1:
Table 9-1 ECE OCS General Parameters
| Name | Type | Description |
|---|---|---|
|
Request Default Timeout |
Integer |
Specifies the default request timeout in milliseconds when no value is supplied by the outbound request. The default value is 2000 milliseconds. |
|
ECE Request Batch Size |
Integer |
Specifies the number of ECE requests to send per request. The default value is 1. |
|
ECE Request Batch Timeout |
Integer |
Specifies the ECE batch request timeout in milliseconds. |
|
ECE Thread Pool Size |
Integer |
Specifies the number of ECE threads to use in the connection pool. |
This section describes how to configure RADUIS Mediation using the Online Mediation Controller Administration Console.
To access the RADIUS Mediation Configuration screen:
In the domain navigation pane, expand OCSB.
Expand Processing Tier.
Click RADIUS Mediation.
The Radius Mediation configuration pane contains the General described in Table 9-2.
Table 9-2 RadiusAthentication Configuration Subtabs
| Subtab | Description |
|---|---|
|
General |
Enables you to define time out value for authentication requests and how to treat accounting requests when Online Mediation Controller operates in degraded mode. See "Configuring General Parameters" |
The General tab enables you to set up how the Authentication application treats authentication requests that time out. Table 9-3 describes configuration parameters in the General subtab.
Table 9-3 Authentication Application General Parameters
| Name | Type | Description |
|---|---|---|
|
auth-timeout |
Integer |
The time to allow for an authentication requests to execute before it is considered to have timed out. Given in seconds. |
|
degraded-mode-behavior |
Enumeration, drop-down menu |
Defines how authentication requests that times out are handled. Choose:
|
By default, the authentication and authorization service type parameter configuration is the same as that for RADIUS accounting. See "Creating and Configuring an IMOFCFPCP or IMOFCFECE Instance", for information on viewing and customizing service type mapping.
You can extend the authentication and authorization functionality by adding support for custom RADIUS AVPs. You do that by adding custom AVPs to the RADIUS dictionary in the RADIUS SSU. See ”Configuring the RADIUS SSU” in Oracle Communications Service Broker Signaling Server Units Configuration Guide for more information.