1 Introduction to Identity and Access Management Deployment
This chapter provides an introduction to Oracle Identity and Access Management Deployment.
This chapter also describes and illustrates the deployment reference topologies employed in this guide.
The Oracle Identity and Access Management Deployment Wizard and related lifecycle tools were developed to automate Oracle Identity and Access Management Deployment and reduce the time required to install and configure Oracle Identity and Access Management components.
Note:
This guide describes how to install Oracle Identity and Access Management with High Availability (HA) in two scenarios, such as the following:-
Oracle Identity Manager (OIM) Only
-
Oracle Access Management Suite Only.
The key to a successful deployment is planning and preparation. The road map for installation and configuration at the end of this chapter directs you to the appropriate chapters for the tasks you need to perform. Use this chapter to help you map the examples used in this guide to your own deployment.
This chapter contains the following sections:
-
Section 1.2, "Understanding Oracle Identity and Access Management Deployment Topologies"
-
Section 1.3, "Products Deployed Using the Oracle Identity and Access Management Deployment Wizard"
-
Section 1.4, "Reference Topologies Documented in This Version of the Guide"
1.1 Planning Your Deployment
A deployment for Oracle Identity and Access Management consists of the following parts:
-
A database for storing policy information and information specific to the identity and access management components being deployed.
-
Identity and Access Management components can be divided into three categories:
-
Directory Services: one or more highly available directories for storing identity information
-
Identity Management Provisioning: Oracle Identity Manager
-
Access Control: Oracle Access Management Access Manager
-
-
A highly available web tier which is used to access Identity and Access Management components.
-
A highly available load balancer, which is used to distribute load between the web servers. The load balancer is also used to off load SSL encryption to ensure that communication between user sessions and Oracle Identity and Access Management are encrypted, but without the overhead of having to enable SSL between the individual Identity and Access Management components.
This guide explains in detail how to deploy two topologies supported in this early release of Oracle Identity and Access Management (11.1.2.2). This topology is not the only one supported by Oracle, but it is deemed to be the most common.
1.2 Understanding Oracle Identity and Access Management Deployment Topologies
Each topology is divided into tiers for increased security and protection. The tiers are separated by firewalls that control access from one tier to the next. The goal is to prevent unauthorized traffic. In an Internet-facing topology, for instance, it should not be possible to directly access a database from the Internet zone. Only applications deployed in the application zone should have access to the database.
The diagram shows three tiers:
-
Web Tier
-
Application Tier
-
Database Tier
Although it is not shown on the figures, there can also be a directory tier (which is often included in the database tier). If a dedicated directory tier is introduced, LDAP directories can be placed alongside the database tier. Note that the common practice is to use an existing directory on the network.
This section contains the following topics:
1.2.1 About the Web Tier
The web tier is in the DMZ Public Zone. The HTTP Servers are deployed in the web tier.
Most of the Identity and Access Management components can function without the web tier, but to properly support high availability and SSO between IAM components out of the box, the web tier is required. All topologies created using the Deployment Tool come with a configured web tier.
In the web tier:
-
WEBHOST1 and WEBHOST2 have Oracle HTTP Server, WebGate (an Access Manager component), and the
mod_wl_ohsplug-in module installed. Themod_wl_ohsplug-in module enables requests to be proxied from Oracle HTTP Server to a WebLogic Server running in the application tier. -
In the OAM-Only deployment scenario, WebGate in Oracle HTTP Server uses Oracle Access Protocol (OAP) to communicate with Oracle Access Manager running on OAMHOST1 and OAMHOST2, in the Identity Management zone. WebGate and Access Manager are used to perform operations such as user authentication.
On the firewall protecting the web tier, the HTTP ports are 443 (HTTP_SSL_PORT) for HTTPS and 80 (HTTP_PORT) for HTTP.
1.2.1.1 High Availability Provisions
If the Oracle HTTP server fails on the WEBHOST1, Oracle Process Management and Notification (OPMN) server attempts to restart it.
1.2.1.2 Security Provisions
The Oracle HTTP Servers process requests received using the URLs igdadmin.mycompany.com, sso.mycompany.com, and iadadmin.mycompany.com. The names igdadmin.mycompany.com, sso.mycompany.com, and iadadmin.mycompany.com are only resolvable inside the firewall. This prevents access to sensitive resources such as the Oracle WebLogic Server console and Oracle Enterprise Manager Fusion Middleware Control console from the public domain.
1.2.2 About the Application Tier
The application tier is the tier where Java EE applications are deployed. Products such as Oracle Identity Manager, Oracle Access Manager and Oracle Enterprise Manager Fusion Middleware Control are the key Java EE components that are deployed in this tier. Applications in this tier benefit from the High Availability support of Oracle WebLogic Server.
If a directory tier exists in the deployment topology, the Identity and Access Management applications in the application tier interact with the directory tier as follows:
-
They leverage the directory tier for enterprise identity information.
-
In some cases, they leverage the directory tier (and sometimes the database in the data tier) for application metadata.
-
Oracle Enterprise Manager Fusion Middleware Control is an administration tool that provides administrative functionalities to the components in the application tier as well as the directory tier.
-
WebLogic Server has built-in web server support. If enabled, the HTTP listener exists in the application tier as well.
The application tier includes the following components:
-
Oracle Access Management Suite. However, only Oracle Access Manager (OAM) is configured and activated by the Identity and Access Management Deployment Wizard. (OAM). If necessary, other components of the Oracle Access Management Suite, such as Oracle Identity Federation and Secure Token Service, can be configured manually.
-
The governance components, which are Oracle Identity Manager (OIM) and Oracle SOA Suite (SOA).
-
The administrative components of Identity and Access Management, including Oracle Identity Manager, which is used for user provisioning. These servers also run Oracle SOA, which is used exclusively by Oracle Identity Manager.
In addition:
-
OAMHOST1 hosts an Oracle WebLogic Administration Server for IAMAccessDomain. Inside the administration server are managerial and navigational components for the domain including: Oracle WebLogic Console, Oracle Enterprise Manager Fusion Middleware Control, and Access Manager Console.
-
OIMHOST1 hosts an Oracle WebLogic Administration Server for IAMGovernanceDomain. Inside the administration server are managerial and navigational components for the domain including: Oracle WebLogic Console, Oracle Enterprise Manager Fusion Middleware Control, and Oracle Authorization Policy Manager.
-
The WebLogic Administration server is a singleton process. That is, it can only be started on one server at a time. In the event that the host running the administration server fails, the Administration server can be manually started on a different host.
1.2.2.1 About WebLogic Domains
A domain is the basic administration unit for WebLogic Server instances. A domain consists of one or more WebLogic Server instances (and their associated resources) that you manage with a single Administration Server. You can define multiple domains based on different system administrators' responsibilities, application boundaries, or geographical locations of servers.
In the topology used in this version of the guide, products are deployed to two separate Middleware Home directories and to two separate WebLogic domains:
-
IAMAccessDomain - Hosts Oracle Access Management suite components.
-
IAMGovernanceDomain - Hosts Oracle Identity Manager, SOA, and other governance components.
1.2.3 About the Database Tier
Starting with 11g Release 2 (11.1.2), policy information is stored in the database. The database is also used for storing information specific to the Identity and Access Management components being deployed.
In some cases, the directory tier and database tier might be managed by the same group of administrators. In many enterprises, however, database administrators own the data tier while directory administrators own the directory tier.
1.3 Products Deployed Using the Oracle Identity and Access Management Deployment Wizard
The following products can be installed, configured, and integrated using the Oracle Identity and Access Management Deployment Wizard:
-
Oracle WebLogic Server
-
Oracle SOA Suite (required for Oracle Identity Manager only)
-
Oracle Identity Manager
-
Oracle Access Management
-
Oracle Unified Directory
-
Oracle HTTP Server
-
Webgate
The products that are installed and configured depend on the option that you select on the Select IAM Products screen of the Oracle Identity and Access Management Deployment Wizard, when you create the deployment response file. For more information, see Section 4.4.1.6, "Select IAM Products"
1.4 Reference Topologies Documented in This Version of the Guide
In this version of the Identity and Access Management deployment guide, the following reference HA topologies are documented:
1.4.1 Only Oracle Identity Manager in an HA Environment
This section illustrates and describes the Oracle Identity Manager Only (OIM-Only) installation scenario.
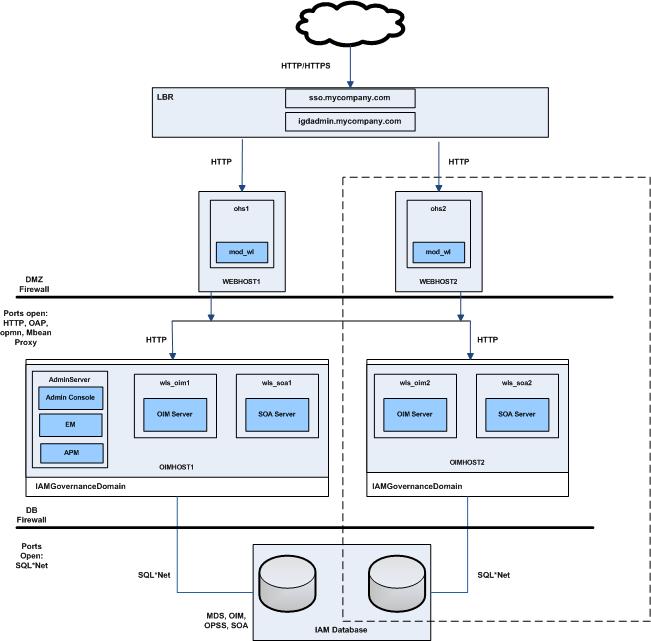
Description of the illustration r2ps2-oim-only.jpg
Oracle Identity Governance/Manager empowers user self-service, simplifies account administration, and streamlines audit tasks resulting in a lower overall total cost of ownership for managing identities. The Oracle Identity Manager Only (OIM-Only) topology diagram includes icons and symbols that represent the hardware load balancer, host computers, firewalls, and other elements of the topology. At a high level, it shows the main components of the topology, including the following:
-
The Load Balancer: The load balancer can be configured to receive user requests on either Port 80 (HTTP) and Port 443 (HTTPS). If HTTPS is chosen, SSL is terminated (where appropriate), and the request are passed onto the Oracle HTTP servers using Port 7777.
-
The Web Tier: Each host in the web tier hosts an Oracle HTTP Server instance and the mod_wl_ohs module.
-
The Application Tier: There are two hosts, OIMHOST1 and OIMHOST2. A single WebLogic administration domain, IAMGovernanceDomain, spans these hosts. Managed Servers run on both OIMHOST1 and OIMHOST2 in a WebLogic clustered setup. For example,
wls_oim1andwls_soa1run on OIMHOST1. Similarly, wls_oim2 and wls_soa2 run on OIMHOST2. Requests are received from the Web Tier. Each host contains Managed Servers for the following products:-
Oracle Identity Manager (OIM)
-
SOA that hosts a SOA Server and corresponding JRF/OPSS processes (exclusively used by Oracle Identity Manager)
OIMHOST1 also contains the WebLogic Administration Server, which hosts the WebLogic Console, Enterprise Manager Fusion Middleware Control, and Authorization Policy Manager (APM). Oracle Identity Manager Administration Console (/sysadmin) and SOA Console are hosted on the OIM Managed Server. In the event of the failure of OIMHOST1, the WebLogic Administration Server can be started on OIMHOST2 manually.
-
-
Firewalls: These are used to separate the Web, Application, and Database tiers into different zones. WEBHOST1 and WEBHOST2 reside in the DMZ.
1.4.2 Only Oracle Access Management in an HA Environment
This section illustrates and describes the Oracle Access Management Only (OAM-Only) installation scenario.
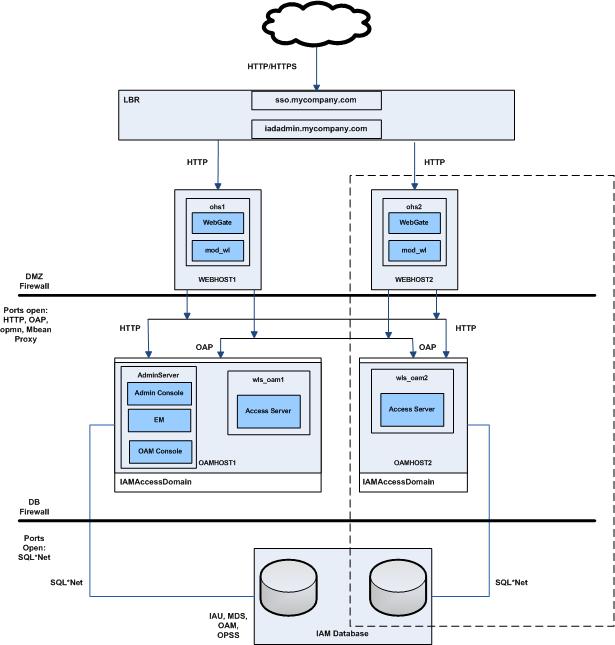
Description of the illustration rsps2-oam-only.jpg
Oracle Access Management suite gives customers the flexibility to deploy a comprehensive solution delivering authentication, single sign-on, authorization, mobile and social sign-on, identity propagation, and risk-based authentication and authorization at the network perimeter.
Oracle Access Manager (OAM) enables your users to seamlessly gain access to web applications and other IT resources across your enterprise. It provides a centralized and automated single sign-on (SSO) solution, which includes an extensible set of authentication methods and the ability to define workflows around them. It also contains an authorization engine, which grants or denies access to particular resources based on properties of the user requesting access as well as based on the environment from which the request is made. Comprehensive policy management, auditing, and integration with other components of your IT infrastructure enrich this core functionality.
This topology will not service federated requests out of the box.
The topology diagram includes icons and symbols that represent the hardware load balancer, host computers, firewalls, and other elements of the topology. At a high level, it shows the main components of the topology, including the following:
-
The Load Balancer: The load balancer receives user requests on Port 80 (HTTP) and Port 443 (HTTPS), strips out the SSL (where appropriate) and passes the requests onto the Oracle HTTP servers using Port 7777.
-
The Web Tier: Each host in the web tier hosts an Oracle HTTP Server instance and the mod_wl_ohs module.
-
The Application Tier: There are two hosts, OAMHOST1 and OAMHOST2. A single WebLogic administration domain,
IAMAccessDomain, spans these hosts. Managed Servers run on both OAMHOST1 and OAMHOST2 in a WebLogic clustered setup. For example,wls_oam1runs on OAMHOST1. Similarly,wls_oam2runs on OAMHOST2. Requests are received from the Web Tier. Each host contains Managed Servers for Oracle Access Manager.OAMHOST1 also contains the WebLogic Administration Server, which hosts the WebLogic Console, Enterprise Manager Fusion Middleware Control, and Oracle Access Manager Administration Console. In the event of the failure of OAMHOST1, the WebLogic Administration Server can be started on OAMHOST2 manually.
-
Firewalls: These are used to separate the Web, Application, and Database tiers into different zones. WEBHOST1 and WEBHOST2 reside in the DMZ.
Note:
When you configure Oracle Access Management using the Oracle Identity and Access Management Deployment Wizard, only Oracle Access Manager is enabled, by default. For enabling other services including Security Token Service, Identity Federation, and Oracle Access Management Mobile and Social, refer to "Enabling or Disabling Available Services" in the Oracle Fusion Middleware Administrator's Guide for Oracle Access Management.