Firewall Port Requirements
The specifics of the Oracle cloud services network requirement depend on the customer network topology relative to the Oracle Services Support centers, Oracle Advanced Support Gateway, and the monitored systems. The customer networks must be configured to permit traffic flow between Oracle Advanced Support Gateway and Oracle Services Support centers. This is referred to as the external connection.
Note - A web proxy can be used to proxy the HTTPS traffic across the external connection. However, Oracle Advanced Support Gateway does not support NTLM or Kerberos proxy authentication. The Transport Layer Security (TLS) VPN traffic cannot be routed through a proxy server.
Caution - To defend against security attacks, you should never connect Oracle Advanced Support Gateway interfaces or the Oracle ILOM Service Processor to a public network, such as the Internet. The Gateway should never be exposed directly to the Internet without the protection of a customer firewall or Access Control List (ACL.) |
Oracle Advanced Support Gateway comes with multiple network interfaces. Of these interfaces, two are utilized to support connectivity requirements. The first interface is used primarily for external connectivity while the second interface is connected directly to the PCC Infrastructure management network. This provides, in effect, the required isolation between the PCC infrastructure and the customer internal network.
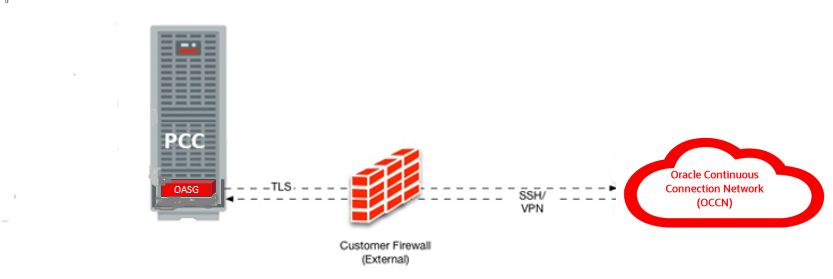
The diagram below depicts an example of the traffic flow between monitored systems and Oracle. (Detailed firewall rules and templates are provided to the customer during the implementation process.)
Figure 1 High Level Traffic Flow and Firewall Requirement