11 Configuring High Availability for Mobile and Social
This chapter describes the Oracle Access Management Mobile and Social high availability framework. Topics include the following:
-
Section 11.1, "Oracle Access Management Mobile and Social Component Architecture"
-
Section 11.3, "Mobile and Social High Availability Concepts"
-
Section 11.4, "Configuring Mobile and Social High Availability"
11.1 Oracle Access Management Mobile and Social Component Architecture
Oracle Access Management Mobile and Social (Mobile and Social) is a lightweight security and identity solution that opens your existing Identity Management infrastructure to mobile and social networks. Mobile and Social integrates with existing IDM products including OAM and IGF. See Oracle Access Management Mobile and Social in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management for more information on Mobile and Social.
Figure 11-1 shows the Mobile and Social component architecture.
Figure 11-1 Mobile and Social Component Architecture
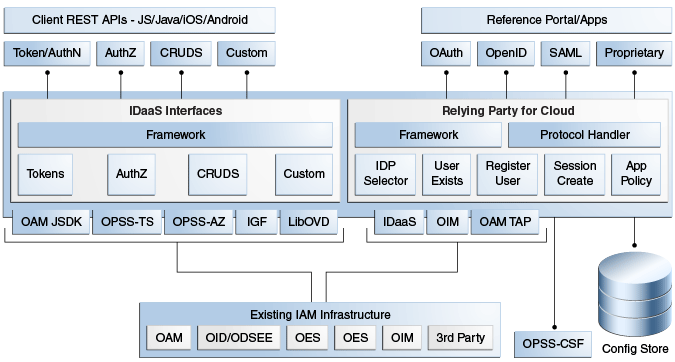
Description of "Figure 11-1 Mobile and Social Component Architecture"
The Oracle Access Management Mobile and Social service acts as an intermediary between a user who wants to access protected resources, and the back-end Access Management and Identity Management services that protect the resources. Mobile and Social provides simplified client libraries that allow developers to quickly add feature-rich authentication, authorization, and Identity capabilities to registered applications. On the back-end, the Mobile and Social server's pluggable architecture lets system administrators add, modify, and remove Identity and Access Management services without having to update user installed software.
11.1.1 Session State Information
No session state is recorded for the Mobile Services component. For Internet Identity Services, short-lived tokens are kept in memory and discarded as soon as they expire.
11.1.2 Component Lifecycle
Mobile and Social is a component in Access Suite J2EE application. You deploy and configure Mobile and Social as part of the Access Suite; the install, configuration, server instances are associated with the Access Suite.
As part of Mobile Services and Internet Identity Services, Mobile and Social provides HTTP interfaces for the clients to invoke. Mobile and Social processes those requests and returns a response, which the client may use to make additional requests. Mobile and Social is stateless, it can handle all requests sent by the client independently. Mobile and Social provides mobile device registration service and user authentication services using products like OAM, or by using social networks authentication and user profile services using Directory Servers.
Mobile and Social starts up as part of Access Suite server startup. MBean Server loads the Mobile and Social configuration.
11.1.3 Component Configuration Artifacts
Use the Administration Console or WLST commands to edit configuration files. Table 11-1 shows Mobile and Social configuration files and their location.
11.1.4 Mobile and Social Deployment Artifacts
A Mobile and Social installation deploys the following components as part of oam-server.ear:
-
oic_rest.war -
oic_rp.war
Table 11-2 shows Mobile and Social services deployment locations:
Table 11-2 Mobile and Social Product Deployment Locations
| Mobile and Social Product | Deployment Location |
|---|---|
|
Administration Server |
Administration Server user interface deploys as part of the OAM Admin .ear, |
|
Managed Server, REST, and Internet Identity Services runtime |
Deploy as part of the OAM Server .ear file, |
11.2 Mobile and Social Component Characteristics
Mobile and Social services consists of two subcomponents, Mobile Services and Internet Identity Services. Mobile Services provide Representational state transfer (REST) interfaces for authentication, user profile, and authorization services. Internet Identity Services provides integration with social network authentication.
See Introduction to Mobile Services in Oracle Fusion Middleware Administrator's Guide for Oracle Access Management for more information on Mobile and Social.
11.3 Mobile and Social High Availability Concepts
This section describes the Mobile and Social high availability architecture and its elements. Topics include the following:
-
Section 11.3.1, "Mobile and Social High Availability Architecture"
-
Section 11.3.2, "Mobile and Social High Availability and Node Failover"
11.3.1 Mobile and Social High Availability Architecture
Figure 11-1 shows Mobile and Social deployed in a high availability architecture in an active-active configuration.
Figure 11-2 Mobile and Social High Availability Architecture
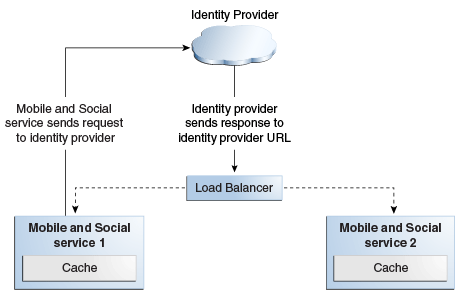
Description of "Figure 11-2 Mobile and Social High Availability Architecture"
Figure 11-2 shows a typical client server architecture that supports multi-instance deployments. In most cases, requests are stateless, requiring no persistence. Mobile and Social services relies on other products, such as OAM/OID, that may have their own high availability capability. For the cases where state is maintained (Internet Identity authentication requests), high availability is achieved through sticky load balancing.
Requests can go to either server because there is no database persistence for sessions or runtime data. The load balancer returns requests to either Mobile and Social service 1 or 2 based on the policy set, such as Round Robin.
When an application invokes Internet Identity Services, control goes to a social network site such as Google, Facebook, or an Internet identity provider to process the request. When the response returns from the identity provider, it must return to the same server that initiates the request. With multiple Mobile and Social node deployments and when access is through the load balancer, requests to Mobile and Social must be pinned to the same server using the load balancer sticky sessions feature. Mobile and Social can further process the request after the Mobile and Social server that initiates the request to an IDP receives the IDP response.
You deploy Mobile and Social applications to all members in a cluster. The Mobile and Social application does not notify other cluster members when it successfully deploys on a cluster.
11.3.2 Mobile and Social High Availability and Node Failover
This section describes elements of the Mobile and Social architecture that provide protection from node failure.
Note that if a node failover occurs, Mobile and Social follows standard WebLogic Server failover procedures. If node failure occurs before Mobile and Social completes a request that it receives from a client, the client receives an error through HTTP connections timeouts.
This section includes the following topics:
11.3.2.1 Load Balancing Requirements and Characteristics
Mobile and Social components are standard J2EE applications deployed on WebLogic Server 10.3, and conform to the standard for load balancing. Note the following:
-
You must use sticky session routing for Mobile and Social/RP requests, however, external load balancers are supported.
-
There is no intra-component load balancing.
-
There are no timeout requirements because there are no persistent connections.
11.3.2.2 Session State Replication and Failover
The Mobile and Social high availability architecture relies on standard WebLogic Server clustering support for failover requirements. This architecture does not replicate the session state.
11.3.2.3 Client Application Startup
When an Mobile and Social instance starts up, it does not affect the running system state. The Mobile and Social instance does not affect other running components or cluster members other than becoming a participant in WebLogic Server clustering scenarios.
11.3.2.3.1 Death Detection / Restart
Use the Node Manager for Java EE components and OPMN for system components for death detection and component restart.
11.4 Configuring Mobile and Social High Availability
Mobile and Social is part of the same managed server as Oracle Access Manager.
You can deploy Mobile and Social independently or with other components such as OAM, STS, and Identity Federation.
This section describes how to configure Mobile and Social high availability and includes the following topics:
-
Section 11.4.1, "Mobile and Social High Availability Requirements"
-
Section 11.4.2, "Modifying the WebGate Profile Configuration"
-
Section 11.4.3, "Modifying Token Service Provider Configuration in Mobile Security"
-
Section 11.4.4, "Modifying OAuth Service Provider Configuration in Federation"
11.4.1 Mobile and Social High Availability Requirements
Note the following Mobile and Social configuration prerequisites:
-
To configure Mobile and Social for high availability, you must install and configure OAM on multiple hosts in a high availability set up. See Chapter 6, "Configuring High Availability for Oracle Access Management Access Manager Components."
-
You must enable Mobile and Social if it is not enabled. Log into the Oracle Access Management Console, select the System configuration tab, open Available Services, and verify that the Mobile and Social status shows a green check.
-
You must configure OHS for
oic_restandoic_rpby adding the following mapping to theoam.conffile in ORACLE_INSTANCE/config/OHS/ohs1/moduleconf:<Location /oic_rest> SetHandler weblogic-handler WebLogicCluster oamhost1.example.com:14100,oamhost2.example.com:14100 </Location> <Location /oic_rp> SetHandler weblogic-handler WebLogicCluster oamhost1.example.com:14100,oamhost2.example.com:14100 </Location>
11.4.2 Modifying the WebGate Profile Configuration
You must modify the WebGate profile configuration to set up Mobile and Social high availability.
To modify the WebGate profile configuration:
-
Log into the OAM Console.
-
Go to the Launch Pad. Click Agents then click Search.
-
Select accessgate-oic to edit it.
Note:
There must be multiple Primary Server List entries if you install multiple instances for this cluster. -
Delete all entries in the Primary Server List.
-
Add the entry
Otherfor Access Server andlocalhostas Host Name. The port number must match the existing port number. -
Click Apply then save your changes.
11.4.3 Modifying Token Service Provider Configuration in Mobile Security
You must modify the Token Service Provider configuration to set up Mobile and Social high availability.
-
Log into the OAM Console.
-
Select the Mobile Security tab
-
Go to the Launch Pad. Select Mobile Authentication.
-
Click any Service Provider that depends on OAM, such as the following:
-
OAMAuthentication
-
OAMAuthorization
-
MobileOAMAuthentication
-
JWTOAMAuthentication
-
MobileJWTOAMAuthentication
-
-
Change
oam.OAM_SERVER_1andoam.OAM_SERVER_2tolocalhost. The port number must be identical to the existing port number.
11.4.4 Modifying OAuth Service Provider Configuration in Federation
You must modify the OAuth Service Provider configuration in Federation.
-
Log into the OAM Console.
-
Select the Federation tab.
-
Go to Launch Pad. Select OAuth, Identity Domains, then Default Domain. Select Service Providers then OAuthServiceProvider.
-
Change
oam.OAM_SERVER_1andoam.OAM_SERVER_2tolocalhost. The port number must be identical to the existing port number.