2 Deploying Logon Manager
with Microsoft AD LDS (ADAM)
This chapter describes best practices for deploying Logon Manager with Microsoft AD LDS (ADAM). It contains the following sections:
2.1 Logon Manager and AD LDS (ADAM) Environments
You have the choice to deploy Logon Manager in a directory environment, such as AD LDS (ADAM) or AD LDS, which enables the delivery of single sign-on capability to any machine on the network through central storage of application credentials, templates, and policies. Users synchronize with the directory to download these items and update their credential stores with new or changed credentials.
Adding Logon Manager to your existing directory environment provides the following benefits:
-
Logon Manager leverages the existing user accounts, groups, and native directory permissions (ACLs) without the need to manage these items separately or synchronize them with another directory or database.
-
Logon Manager data is automatically protected by your existing backup and disaster recovery plans.
-
No dedicated servers or server-side processes are required; Logon Manager's scalability and performance depend solely on the capacity and robustness of your existing directory infrastructure.
-
Administrators are not burdened with additional administrative tasks or the need to learn new tools or concepts. Delegated administration of Logon Manager is achieved through the native capabilities of the directory.
A directory also enables the organization of Logon Manager templates and policies into a highly visual hierarchy. While you can use a flat model if your environment calls for it, a properly set-up hierarchy can help maintain top directory, Agent, and network performance, as well as simplify Logon Manager administration by permitting more efficient access control.
2.1.1 Benefits of AD LDS (ADAM)-Based Deployments
AD LDS (ADAM) provides data storage and retrieval for directory-enabled applications, without the dependencies that are required by Active Directory. AD LDS (ADAM) provides much of the same functionality as Active Directory, but it does not require the deployment of domains or domain controllers, and the directory schema for AD LDS (ADAM) is completely independent of the enterprise schema you may be using in an Active Directory domain. You can run multiple instances of AD LDS (ADAM) concurrently on a single server, with an independently managed schema for each AD LDS (ADAM) instance. The following are the benefits of deploying Logon Manager with AD LDS (ADAM):
-
Ideal for pilot and proof-of-concept deployments. A fully functional AD LDS (ADAM) instance that very closely mimics a full-scale Active Directory environment can be set up in minutes and is entirely self-contained (requiring only the Active Directory host on which it runs).
-
Simplified deployment. AD LDS (ADAM) is available free of charge from Microsoft. Deployment within existing Active Directory environments is easy and allows the reuse of existing user accounts and groups.
-
Efficient scaling and fault tolerance. Since AD LDS (ADAM) is based on Active Directory code, its scalability characteristics are similar to those of Active Directory. Just two servers, capable of supporting approximately 5,000 Logon Manager users, are enough to ensure basic fault tolerance. If your organization consists of more than 5,000 members, consult a Microsoft expert for more information on scalability and fault tolerance.
Additionally, deploying Logon Manager with AD LDS (ADAM) in an existing Active Directory environment provides the following benefits:
-
Retraining is minimized. Administrative procedures for AD LDS (ADAM) are very similar to those for Active Directory. Administrators skilled with Active Directory will be able to deploy and maintain AD LDS (ADAM) instances with little additional effort; management tools for both platforms mirror management tools for Active Directory.
-
Existing Active Directory accounts and policies can be leveraged. Active Directory user accounts, groups, and policies are instantly available in AD LDS (ADAM). You do not need to import, re-create or synchronize your existing configuration and user account data.
2.1.2 Active Directory vs. AD LDS (ADAM)
The table below highlights the key differences between Active Directory and AD LDS (ADAM):
| Feature | Active Directory | AD LDS (ADAM) |
| Server Discovery and Failover | Fully automatic. Client broadcasts request and listens for reply from the nearest server. Failover is simplified as fallback from server to server is automatic. | Automatic when using a load balancer; otherwise requires an explicit server list.
For the benefits of load balancing, see Benefits of Load-Balancing an Logon Manager Deployment. If not using a load balancer, client must be explicitly provided with a list of servers to connect to, ordered by geographic proximity. |
| Schema Extension | Global. You must perform a schema extension to add the required Logon Manager object classes to your Active Directory schema. Existing classes and attributes are not modified in any way. Administrators must understand the impact (usually negligible) of the extension on the directory as a whole. Detailed information on the schema extension is available in Appendix B: Logon Manager Repository Object Classes and Attributes. | Local. When deploying Logon Manager on AD LDS (ADAM), you must perform a schema extension against the target AD LDS (ADAM) instance only. The extension consists of the same four object classes as the Active Directory schema extension. |
| Credential Storage Under User Objects | Yes. You have the option to store Logon Manager application credentials under respective user objects. | No. All user credentials are stored under a dedicated OU within the AD LDS (ADAM) instance. This OU contains an object for each Logon Manager user. |
| Usage Reporting | Yes. When Logon Manager is deployed on Active Directory, you can obtain point-in-time information on user credentials stored in the directory. | No. AD LDS (ADAM) environments do not support point-in-time information reporting for Logon Manager. (Available on AD LDS (ADAM) when Provisioning Gateway is installed.) |
For more in-depth information about AD LDS (ADAM) and its applications, please see:
-
ADAM FAQ: http://www.microsoft.com/windowsserver2003/ADAM/ADAMfaq.mspx
-
AD LDS FAQ: http://technet.microsoft.com/en-us/library/cc755080%28WS.10%29.aspx
2.1.3 How Logon Manager Extends the AD LDS (ADAM) Schema
Before Logon Manager can store data in AD LDS (ADAM), you must extend the schema of the selected AD LDS (ADAM) instance (the Active Directory host's schema is not affected) using the Administrative Console. The schema extension consists of adding four object classes and setting the appropriate permissions so that objects of those types can be created, read, modified, and deleted. Existing classes and attributes are not modified in any way.
Note:
Schema extension is a post-installation procedure. For instructions, see Preparing the AD LDS (ADAM) Instance for Logon Manager. Oracle highly recommends that you perform a schema health check (as described by Microsoft best practices) before performing the schema extension.For detailed information on the schema extensions made by Logon Manager, see the following appendices:
2.1.4 How Logon Manager Synchronizes with AD LDS (ADAM)
The Logon Manager Agent uses the AD LDS (ADAM) synchronizer plug-in to communicate with AD LDS (ADAM). When properly configured, synchronization occurs whenever one of the following events takes place:
-
The Logon Manager Agent starts
-
Application credentials are added, modified, or deleted by the end-user
-
The machine running the Agent acquires an IP address or its existing IP address changes (if Logon Manager is configured to respond to these events)
-
The auto-synchronize interval elapses (if configured)
-
The user initiates synchronization via the Agent's "Refresh" function
During synchronization, the Logon Manager Agent traverses the Logon Manager sub-tree and loads the contents of the sub-containers to which the current user has been granted access; it also synchronizes any credentials that have been added, modified, or deleted since the last synchronization.
2.1.5 How Logon Manager Handles and Stores Application Credentials
Logon Manager encrypts application credentials using a unique key generated when the user completes the First-Time Use (FTU) wizard. The credentials remain encrypted at all times, including in the Agent's local cache, the directory, and while in transit over the network. Logon Manager only decrypts credentials (to memory, never to disk) when a configured application requests logon, and wipes the target memory location as soon as the logon request completes. The amount of data Logon Manager stores per enabled application and per user is trivial (measurable in bytes and small kilobytes).
2.1.6 Benefits of Load-Balancing an Logon Manager Deployment
When a directory server fails, Logon Manager will attempt to contact the next one on its server list. If no servers on the list can be reached, synchronization becomes unavailable until the problem is remedied. If your environment calls for more than one physical AD LDS (ADAM) server, Oracle highly recommends using a load balancer that will evenly and automatically distribute the requests coming from the network among the AD LDS (ADAM) servers behind it. If a server goes offline, the rest can temporarily absorb the workload of the failed machine, providing failover transparency to the end-user and adequate time to bring the faulty server back online.
2.2 Designing the AD LDS (ADAM) Directory Sub-Tree
Logon Manager gives you the freedom to set up the directory structure to best fit the needs of your organization. Specifically, you have the choice to store your data in a flat model, or create a hierarchy. While a flat model works fine for small deployments, growing and large deployments should utilize a hierarchy from the very beginning. The exact structure of your sub-tree will depend on the following factors:
-
Number of users
-
Number of applications that Logon Manager will support
-
Robustness of the existing infrastructure
-
Structure of your organization.
2.2.1 Guidelines for Structuring the AD LDS (ADAM) Sub-Tree for Logon Manager
Oracle recommends that you set up your sub-tree as a hierarchy by following the guidelines below:
-
Use OUs to group templates, policies, and credentials by category, such as department or division, according to the structure of your organization.
-
Control access at the OU level.
-
Disable inheritance and grant no user rights at the Logon Manager root container, unless your environment dictates otherwise.
When set up this way, a hierarchy provides the following benefits:
-
Highly visual and self-documenting tree structure. When you view your sub-tree in a directory browser, the sub-tree structure is self-descriptive and easy to follow.
-
No unwanted inheritance of rights. Users will not natively inherit rights to sub-OUs that you do not want them to access. This eliminates the need to explicitly deny unwanted access rights that are being passed down the tree.
-
Robust network, Agent, and directory performance. Typically, users who download large numbers of templates and policies generate more network traffic and a higher load on the directory than users who only download items relevant to their jobs. Grouping conserves your environment's resources and improves Agent response time.
-
Distributed administrative tasks. Your templates are organized into easily controllable sets, and access rights determine who can manage which templates. You also have the ability to implement rights-based version control of your templates.
-
Low administrative overhead. Controlling access at the template level requires setting permissions for each individual template via the Logon Manager Administrative Console; controlling access at the OU level is achieved via delegated administration using Microsoft and third-party management tools.
The following figure depicts a sample Logon Manager sub-tree whose design reflects the above best practices.
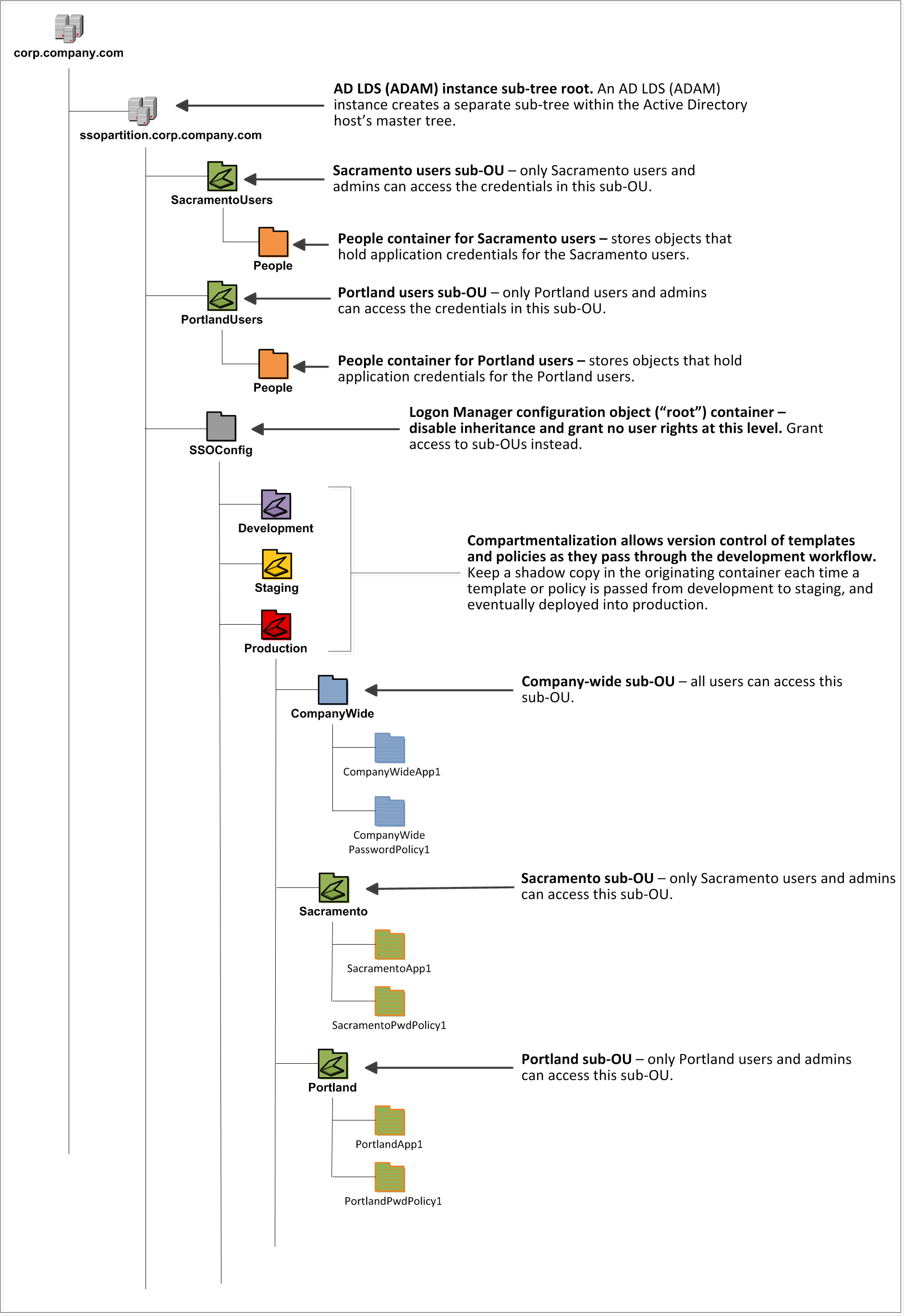
In our sample scenario, users from the Portland division do not need access to applications used by the Sacramento division, and vice versa; therefore, each division's templates and policies live in dedicated sub-OUs under the root and one division cannot access another division's sub-OU. In the end, your environment will dictate the specifics of your implementation.
Note:
Oracle highly recommends that you store templates, policies, and application credentials in individual OUs. To do this, you must Use Configuration Objects.Unlike Active Directory, AD LDS (ADAM) does not permit Logon Manager to store application credentials under user objects. Instead, when deployed on AD LDS (ADAM), Logon Manager stores application credentials in a flat format inside a special OU called People. The People container, by default, resides in the root of your AD LDS (ADAM) partition; however, if you require more granular access control, you can create multiple People containers (each must have a unique path) for different departments or regions within your organization, just like you would for templates and policies, as shown in Figure 3. You would then configure each department's Logon Manger instances to seek application credentials in that department's People OU. You must create the People OU and provide its full path to the AD LDS (ADAM) synchronizer as described in Creating the People OU.
Note:
A container object is automatically created inside the People OU at first use for each Logon Manager user in order to keep user data private and separate.If you are using Provisioning Gateway and want to take advantage of multiple People OUs, the following limitations apply:
Note:
It is not possible to use multiple People OUs with Provisioning Gateway with a single domain.-
The People OU must reside inside a parent container at the root of the AD LDS (ADAM) partition,
-
The parent container's name must be the name of the domain (NT-style) of the users whose application credentials are stored in the corresponding People OU. If necessary, create a separate domain for each department or region that requires a separate People OU and move the corresponding users to that domain.
If you are starting out with a flat model, but expect the number of users and provisioned applications to grow, create a sub-container under the root and use it to store your templates and policies as a flat file until you are ready to transition to a hierarchy. Monitor the performance of your environment as you add more users and provision more applications, and transition to a hierarchy sooner rather than later to minimize the required effort. When transitioning to a hierarchy, use the existing container as your new Logon Manager root container and create sub-OUs underneath it.
2.2.2 Version Control and Pre-Flight Testing of Templates and Policies
Oracle recommends that you create dedicated sub-OUs for each stage of your workflow: development, staging, and production, as shown in Figure 3. This way you will be able to:
-
Track changes made to templates and policies as they pass through the workflow and enter production by keeping shadow copies each time templates and policies move from one workflow stage to the next.
-
Roll back to a previous version of a template or policy if need arises.
-
Control who can work on which templates and policies at each workflow stage. In particular, you should strictly enforce rules governing who can put a template or a policy into production.
Always test every application template and administrative override in a contained environment before you deploy it to end-users. Testing helps you stage your changes and resolve any potential issues that would be much more costly to resolve were they to occur in production. Testing is particularly critical in large deployments: if you push out a misconfigured template or an incorrect administrative override network-wide, access to mission-critical applications may be lost enterprise-wide.
When setting up a contained test environment, create a dedicated test container to which only members of your development group will have access. Then, point the test Logon Manager Agent(s) at this container and place your templates and administrative overrides in it. Once you confirm that the templates and policies are functioning as intended, move them to the target production container.
If you decide not to keep shadow copies of your templates after you test them, move them from the test container to target production containers as follows:
-
Retrieve the template from the directory.
-
Create a local backup of the template.
-
Push the duplicate into the new location within the directory.
-
Delete the template from its original location.
2.2.3 Precautions for Configuring Object Access Control Lists Using the Console
When you modify an object's Access Control List (ACL) using the Console, the connection string (repository host name or IP) used to connect to the repository is treated by the Console as a unique repository identifier and recorded in the object. The Console is thus unable to distinguish between two unique repositories and two methods to connect to the same repository.
Because of this, if you use different connection strings for the same repository, e.g. an IP address and host name, the changes made to an object from one session to the next will be lost. To work around this issue in an AD LDS (ADAM) environment, always use the same connection string (IP address or host name) when modifying object ACLs through the Console.
2.2.4 Precautions for Upgrading the Agent and Console
To maintain template and settings compatibility throughout your environment, you should always use a version of the Console matching the oldest version of the Agent still deployed in production. Due to template schema changes between releases, older Agents may exhibit unexpected behavior when supplied a template created or modified by a newer version of the Console. For this reason, if you are upgrading to a newer release of Logon Manager, Oracle highly recommends that you do not upgrade your Console until all deployed Agent installations have been upgraded.
Note:
Even if you do not make any changes to a template, it is still rewritten using the currently installed Console's data schema when you push the template back to the repository.2.3 Global Agent Settings vs. Administrative Overrides
The behavior of the Logon Manager Agent, including its interaction with the directory, is governed by settings configured and deployed to the end-user machine by the Logon Manager administrator using the Logon Manager Administrative Console. The settings fall into one of the following categories:
-
Global Agent settings are the "local policy" for the Agent; they are stored in the Windows registry on the end-user machine and are included in the Logon Manager MSI package to provide the Agent with an initial configuration during deployment. Global Agent settings are stored in
HKEY_LOCAL_MACHINE\Software\Passlogix(32-bit systems) orHKEY_LOCAL_MACHINE\Wow6432Node\Software\Passlogix(64-bit systems).Caution:
Users able to modify the HKLM hive can alter their global Agent settings and thus change the behavior of the Agent from the one originally intended. To ensure that a setting will not be changed by the end-user, deploy it through an administrative override. -
Administrative overrides take precedence over the global Agent settings stored in the Windows registry and constitute the "domain" policy for the Agent. Overrides are downloaded from the central repository by the Agent during synchronization and stored in the Agent's encrypted and tamper-proof local cache, which makes them immune to end-user alterations. When role/group security is enabled, administrative overrides can be applied on a per-user or per-group basis; they can also be applied enterprise-wide to enforce configuration consistency for all users.
Note:
Be conservative when planning your administrative overrides. Fewer overrides mean less data to store and transfer, and thus more efficient synchronization with the central repository. Reducing the number of overrides also simplifies troubleshooting by eliminating unknowns, as administrative overrides cannot be viewed on the end-user machine.
Global Agent settings together with administrative overrides constitute the complete configuration policy for the Agent. The rest of this guide describes the recommended optimal configuration and complements the information found in the other Enterprise Single Sign-On Suite Administrator's Guide.
WARNING:
Settings such as domain names and user object paths should always be thoroughly tested before deployment and not deployed as administrative overrides unless absolutely necessary. A simple mistake, such as a mistyped domain name, can render end-user workstations unable to synchronize with the directory, in which case you will not be able to propagate a correction through the Console - changes will have to be made to user machines using other tools.
The figure below depicts a typical view of the Logon Manager Administrative Console set up for synchronization with AD LDS (ADAM).
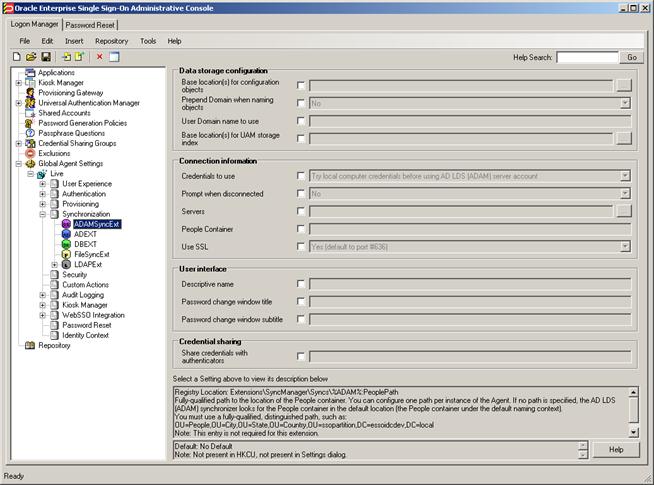
The next section describes best practices for configuring Logon Manager for synchronization with AD LDS (ADAM). If you need additional information on settings described in this guide, see the online help included with the Console.
Note:
Before you begin, make sure that the Logon Manager Agent and the AD LDS (ADAM) synchronizer plug-in are installed on your machine; otherwise, AD LDS (ADAM)-related settings will not be displayed in the Console. For installation instructions, see the installation guide for your version of Logon Manager.Tip:
In a development or staging environment, disable the option Check for publisher's certificate revocation in Internet Explorer to eliminate a delay when the Console starts and your machine is not connected to the Internet. (The delay is caused by Internet Explorer attempting to look up the server's certificate and timing out when a certificate authority cannot be reached.) Do not disable this option on production machines.The best practice for settings not described in this and other guides is to leave them at their default values, unless your environment dictates otherwise. The default value is automatically in effect whenever the check box for the setting in the Administrative Console is not checked. The value is visible in the inactive field next to the check box.
2.4 Recommended Global Agent Settings
This section lists Oracle-recommended best-practice global Agent settings. Configure the settings as described below and include them in the customized Logon Manager MSI package. For instructions on creating the package, see the "Packaging Logon Manager for Mass Deployment" section in the guide Enterprise Single Sign-On Suite Installation Guide.
2.4.1 Use Configuration Objects
On AD LDS (ADAM) deployments Oracle highly recommends that you use directory objects for storing user and configuration data, allowing hierarchical storage, as well as role/group-based access control for individual containers, templates, and policies as described in Designing the AD LDS (ADAM) Directory Sub-Tree. If you disable this feature, Logon Manager will store all template and configuration data as a single flat file under the tree root.
![]()
Located in: Global Agent Settings > Live > Synchronization
To enable: Select the check box, then select Yes from the drop-down list.
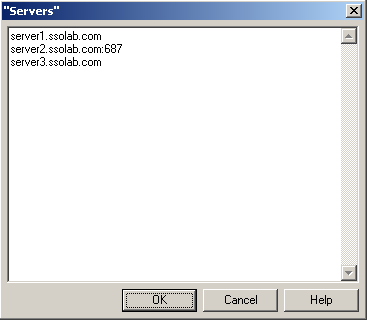
2.4.2 Configure a Server List with Desired Failover Order
In AD LDS (ADAM) environments, server URLs must be explicitly provided to Logon Manager. Oracle highly recommends using at least two physical AD LDS (ADAM) servers and placing them behind a load balancer for automatic, transparent failover. If you choose not to use a load balancer, arrange the server URLs in order of geographic proximity to the end-user so that the performance hit due to physical distance between the end-user and the next available server is minimized. For more information on load balancing, see Benefits of Load-Balancing an Logon Manager Deployment.
![]()
Located in: Global Agent Settings > Live > Synchronization > ADAMSyncExt
To set: Select the check box, click the (…) button, and enter the desired values (one per line) as shown below. When you are finished, click OK.
2.4.3 Specify the Path to the Logon Manager Configuration Objects
You must specify the location of the Logon Manager root container (which stores Logon Manager configuration objects) for Logon Manager to store data in AD LDS (ADAM).
![]()
Located in: Global Agent Settings > Live > Synchronization > ADAMSyncExt
To set: Select the check box, click the (…) button, and enter the desired value. When you are finished, click OK.
2.4.4 SSL Support
Logon Manager repository synchronizers ship with SSL support enabled and Oracle highly recommends that you do not disable it. Your environment should always utilize SSL for all connections to the Logon Manager and other repositories for maximum security.
Note:
Note: You must configure your domain controllers to use SSL before deploying Logon Manager. For instructions, see the following MSDN article: http://msdn.microsoft.com/en-us/library/aa364671(VS.85).aspx
![]()
Located in: Global Agent Settings > Live > Synchronization > ADAMSyncExt
To re-enable (if disabled): Deselect the check box.
2.4.5 Select the Credentials to Use when Authenticating to the Repository
Use the Credentials to use option to select the credentials Logon Manager should use when authenticating to the repository. Oracle recommends that you set this to Local computer credentials so that the user will not be prompted to reauthenticate if Logon Manager is unable to authenticate to the repository.
Note:
Do not leave this at the default setting, Try local computer credentials before using AD LDS (ADAM) server account. Doing so will cause an authentication failure (and the re-authentication prompt to appear, unless disabled) if the repository and the end-user machine are not part of the same domain.If you are using Smart Cards to authenticate to Logon Manager, you can also use the card's certificate to authenticate to the repository by selecting Use card's certificate from the drop-down menu. For more information, see the Oracle Enterprise Single Sign-On Suite Plus Administrator's Guide.
![]()
Located in: Global Agent Settings > Live > Synchronization > ADAMSyncExt
To set: Select the check box, then select the appropriate option from the drop-down list.
2.4.6 Configure Logon Manager to Use a Specific People OU
If you created a People OU in a location other than default (root of the AD LDS (ADAM) partition), or you have created multiple People OUs for more granular control of access to application credentials, you must configure the target Logon Manager instances to use the corresponding People OUs, as explained in Designing the AD LDS (ADAM) Directory Sub-Tree.
![]()
Located in: Global Agent Settings > Live > Synchronization > ADAMSyncExt
To set: select the check box next to the People container option and enter the fully qualified path to the specific People OU you want Logon Manager to use into the field. For example:
OU=People,OU=City,OU=State,OU=Country,OU=ssopartition,DC=company,DC=com
2.4.7 Choose Whether to Prompt the User when Disconnected from the Repository
Use the Prompt when disconnected option to decide whether Logon Manager should prompt the user to re-authenticate to the repository upon authentication failure or disconnection. Oracle recommends that you set this to No; doing so will avoid unnecessary confusion and helpdesk calls.
![]()
Located in: Global Agent Settings > Live > Synchronization > ADAMSyncExt
To set: Select the check box, then select the appropriate option from the drop-down list.
This option is directly related to the Credentials to use option described above and has no effect if Allow disconnected operation is set to No.
2.4.8 Add the AD LDS (ADAM) Synchronizer to the Synchronizer Order List
Ensure that the AD LDS (ADAM) (ADAMSyncExt) synchronizer plug-in is present and enabled in the Synchronizer order list if at least one of the following is true for your environment:
-
Logon Manager is synchronizing with more than one repository,
-
Logon Manager is using roaming synchronization,
-
Kiosk Manager is installed in your environment.
Note:
Instructions for configuring Logon Manager for multi-repository and roaming synchronization, as well as installing and configuring Kiosk Manager, are beyond the scope of this guide. For more information, see the documentation for your version of Logon Manager and/or Kiosk Manager.![]()
Located in: Global Agent Settings > Synchronization
To set: Select the check box, then click the (…) button. In the list that appears, select the checkbox next to ADAMSyncExt and click OK. Use the up/down arrows to set synchronization order as necessary.
2.4.9 Make the Logon Manager Agent Wait for Synchronization on Startup
To ensure that users always have the most recent credentials, application templates, password policies, and administrative overrides, configure the Agent to wait for synchronization on startup. When this option is enabled, the Agent checks whether the directory is online. If the directory is online, the Agent does not respond to application logon requests until it successfully synchronizes with the directory. If the directory is offline, the Agent does not attempt to synchronize and starts immediately.
![]()
Located in: Global Agent Settings > Live > Synchronization
Use the default value (Yes) unless your environment requires otherwise.
2.4.10 Use Optimized Synchronization
Optimized synchronization instructs the Logon Manager Agent to synchronize only credentials that have changed since the last synchronization. Do one of the following, depending on your environment:
-
Enable this option to improve synchronization performance on deployments with large numbers of credentials per user.
-
Disable this option to improve synchronization performance on deployments with fewer than five credentials per user and a large number of templates downloaded per user.
![]()
Located in: Global Agent Settings > Live > Synchronization
Use the default value (Yes) unless your environment requires otherwise.
2.4.11 Restrict Disconnected Operation
During deployment, configure the Logon Manager Agent not to run if a connection to the directory cannot be established. This will prevent users from completing the First-Time Use (FTU) wizard when the Agent is not connected to the directory and no local cache is present. By not allowing the Agent to run when the directory is not available, you avoid a common situation in which a second set of encryption keys is created when a user completes the FTU wizard while disconnected from the directory.
Note:
See the guide Logon Manager Best Practices: Configuring the Logon Manager Agent for more information on this required best practice.![]()
Located in: Global Agent Settings > Live > Synchronization
To set: Select the check box, then select No from the drop-down list.
2.5 Recommended Administrative Overrides
Directory synchronization settings, such as domain names and object paths, should not be deployed as administrative overrides. (See Global Agent Settings vs. Administrative Overrides for an explanation.) The recommended best-practice overrides are described in the section "Configuring Logon Manager" in the guide Logon Enterprise Single Sign-On Suite Administrator's Guide.
2.6 Overview of the Deployment Process
This section provides a brief high-level overview of the Logon Manager deployment process on AD LDS (ADAM). Make sure you have read all of the preceding sections of this document before proceeding with deployment. Deploying Logon Manager with MS AD LDS (ADAM) requires you to:
-
1. Obtain the following documents:
-
The latest version of this document
-
Installing Oracle Enterprise Single Sign-On Suite
-
Oracle Enterprise Single Sign-On Suite Administrator's Guide
-
-
If you have not already done so, install AD LDS (ADAM) on the target server. The AD LDS (ADAM) installer and installation instructions are available on the Microsoft Web site.
-
Create groups for Logon Manager administrators and Logon Manager users. Basic instructions are provided in Appendix E: Creating the Required User Groups on AD LDS (ADAM).
-
Create a new AD LDS (ADAM) instance that will be used by Logon Manager, as described in Creating an AD LDS (ADAM) Instance.
-
Install the Logon Manager Agent and the Logon Manager Administrative Console on a machine within your domain, as described in the installation guide for your version of Logon Manager. Make sure you select the AD LDS (ADAM) Synchronizer when installing the Agent.
-
Complete the steps in Preparing the AD LDS (ADAM) Instance for Logon Manager:
-
Extend the AD LDS (ADAM) instance schema with Logon Manager classes and attributes.
-
Create the People OU, which will store each user's application credentials.
-
Create the Logon Manager configuration object container and desired tree structure.
-
Grant the required permissions.
-
-
Configure Logon Manager as follows:
-
Complete the steps in Configuring the AD LDS (ADAM) Synchronizer.
-
Configure the options described in Recommended Global Agent Settings in this guide.
-
Configure the options described in the "Configuring the Logon Manager Agent" section of the Enterprise Single Sign-On Suite Administrator's Guide.
Note:
For detailed descriptions of the settings in question, see the Console's online help.
-
-
On a test machine, do the following:
-
Create a pilot set of core templates and policies.
-
Finalize the end-user experience by testing each core template, global Agent setting, and administrative override that will be deployed into production.
-
-
Create a custom MSI package and deploy it to end-user machines by completing the steps in the "Packaging Oracle Enterprise Single Sign-On Suite for Mass Deployment" section of the Installing Oracle Enterprise Single Sign-On Suite.
-
Create, test, and deploy the remaining application templates. See the guide Configuring and Diagnosing Application Templates for in-depth information on provisioning different types of applications.
2.7 Creating an AD LDS (ADAM) Instance
This section describes how to create an AD LDS (ADAM) instance on which you will deploy Logon Manager. If you have not already done so, install AD LDS (ADAM) on the target server. The AD LDS (ADAM) installer and installation instructions are available on the Microsoft web site. Before you begin, note the following:
-
Oracle recommends deploying on Windows Server 2008 and later versions of the Windows Server operating system family. Deployment on Windows XP or Windows 7 is discouraged. Deployment on Windows Server versions prior to 2008 is not supported.
-
To simplify deployment, Oracle highly recommends creating an AD LDS (ADAM) instance that runs on the default port (636 for SSL connections; non-SSL connections to AD LDS (ADAM) are supported but not recommended). If you use a custom port, it must be open between all clients and the target servers.
Note:
Regardless of the type of connection to the repository, user credential data remains encrypted at all times. -
If you are installing AD LDS (ADAM) on a domain controller or another server on which a directory is already running, you will not be able to use the default ports; therefore, Oracle highly recommends deploying Logon Manager on a member server instead of a domain controller.
To create the target AD LDS (ADAM) instance:
Note:
The AD LDS (ADAM) setup wizard screens depicted in this guide may differ visually across the supported versions of the Windows Server operating system family; however, the procedure is identical for all supported versions.-
Launch the AD LDS (ADAM) Setup Wizard.
-
On Windows Server 2008: Click Start > Programs> Administrative Tools> Active Directory Lightweight Directory Services Setup Wizard.
-
On Windows Server 2008 R2:
Note:
: Make sure you have added the "Active Directory Lightweight Directory Services" role to your server before starting this procedure.In Server Manager, expand the Roles node and select the Active Directory Lightweight Directory Services role. In the right-hand pane, expand the Advanced Tools>AD LDS Tools section and click AD LDS Setup Wizard.
-
-
In the "Welcome" screen, click Next.
-
In the "Setup Options" screen, select A unique instance and click Next.
-
Name your AD LDS (ADAM) instance and click Next. The recommended name is ssopartition.
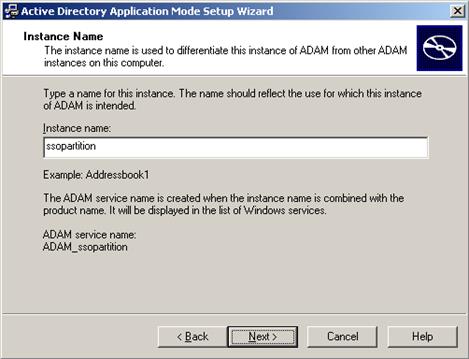
-
Enter the desired port numbers for this AD LDS (ADAM) instance. If you are not using the default ports (389/636), note the custom port numbers you enter here - you will need them later to configure Logon Manager.
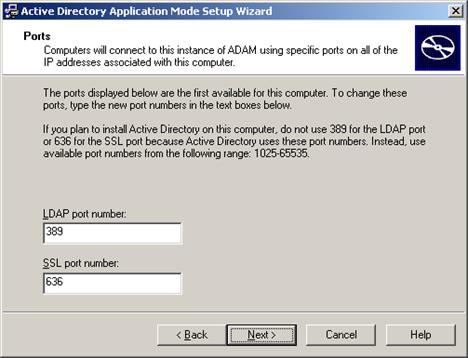
-
Select Yes, create an application directory partition and give the partition a fully-qualified DN. This is the root of your AD LDS (ADAM) instance's sub-tree. The DN must start with ou= and not cn= as the dialog box suggests; otherwise, the Logon Manager deployment will fail.
-
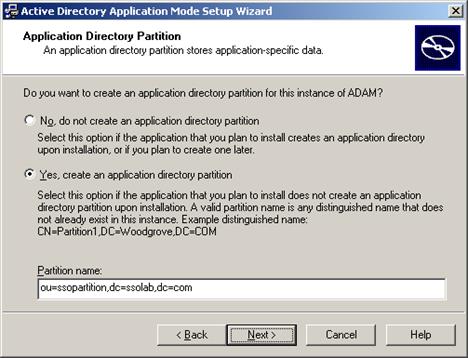
-
Specify the locations in which you want AD LDS (ADAM) to store its files. In most cases, it is safe to accept the default values.
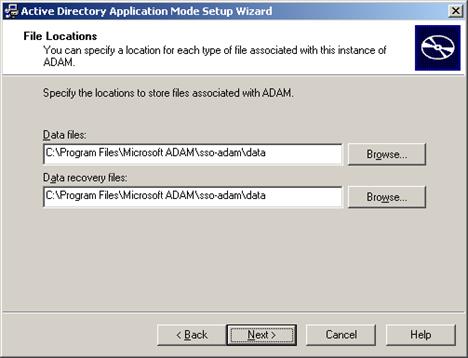
-
Specify the privileges that this instance of AD LDS (ADAM) will use to run.
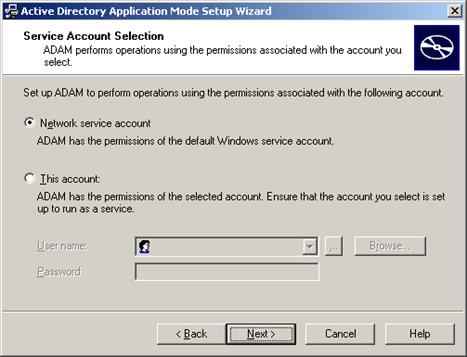
-
Select This Account, then click Browse to specify a user or group you want to have administrative privileges for this instance of AD LDS (ADAM). To prevent lockout from your entire Logon Manager deployment, Oracle highly recommends creating a dedicated group that contains two or more users with administrative privileges over the target AD LDS (ADAM) instance. For more information, see Appendix E: Creating the Required User Groups on AD LDS (ADAM).
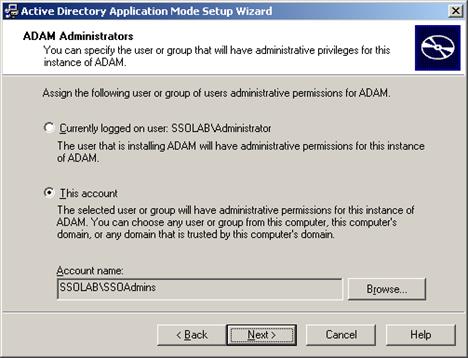
-
Select Do not import LDIF files for this instance of AD LDS (ADAM) and click Next.
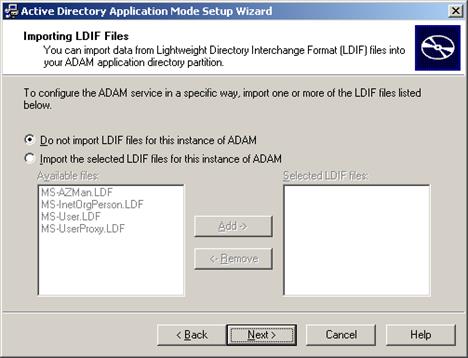
-
In the summary screen, review your configuration choices. If you need to make changes, click Back; otherwise, click Next and wait for AD LDS (ADAM) to create the instance.
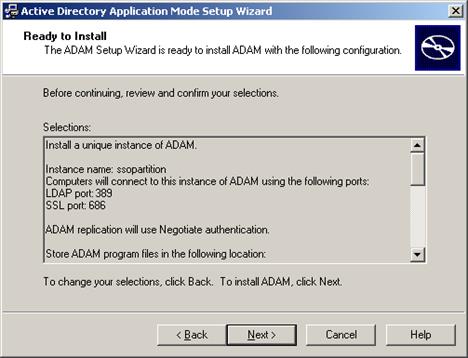
-
When the process is complete, click Finish to quit the wizard.
2.8 Preparing the AD LDS (ADAM) Instance for Logon Manager
This section describes the basic procedures for preparing AD LDS (ADAM) for use with Logon Manager. The preparation consists of extending your AD LDS (ADAM) schema with Logon Manager classes and attributes, allowing Logon Manager to store credentials under respective user objects, and creating the desired tree structure. Before starting this procedure, make sure that you have installed the Administrative Console.
2.8.1 Extending the Schema
-
Start the Logon Manager Administrative Console. By default, the shortcut to the console is located in Start> Programs> Oracle> ESSO Suite Administrative Console.
Note:
In a development or staging environment, disable the option Check for publisher's certificate revocation in Internet Explorer to eliminate a delay when the Console starts and your machine is not connected to the Internet. (The delay is caused by Internet Explorer attempting to look up the server's certificate and timing out when a certificate authority cannot be reached.) Do not disable this option on production machines. -
In the Console, select Extend Schema from the Repository menu. The Console displays the "Connect to Repository" dialog.
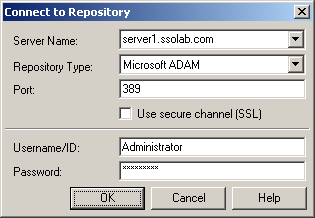
-
In the Server Name field, enter a fully qualified IP address, hostname, or NetBIOS name of your schema master domain controller.
-
In the Repository Type drop-down list, select Microsoft AD LDS (ADAM).
-
Enter the port number on which your directory is listening for connections. The default port is 636 for SSL connections and 389 for non-SSL connections.
-
(Optional) If you configured your domain controllers to use SSL, leave the Use secure channel (SSL) option selected; otherwise, deselect it. (See SSL Support for more information.)
-
In the Username/ID and Password fields, enter the credentials of the account you want Logon Manager to use to connect to AD LDS (ADAM). Depending on your environment, you may need to include the corresponding domain name as part of the user name, for example DOMAIN\user.
-
Click OK and wait for the Console to perform the schema extension. The Console displays a status dialog showing the progress. When the schema has been successfully extended, a confirmation message appears in the status dialog:
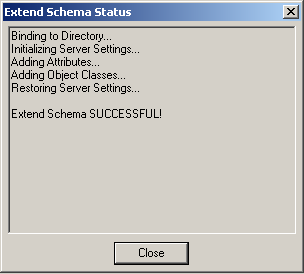
-
Click Close.
If the schema extension fails, check to make sure you have specified the AD LDS (ADAM) instance DN correctly, as described in step 6 on page 28. If the DN is incorrect, delete and re-create the AD LDS (ADAM) instance, then repeat this procedure.
2.8.2 Creating the People OU
After extending the AD LDS (ADAM) instance schema, you must create at least one People OU, which Logon Manager will use to store application credentials. By default, Logon Manager expects the People OU to reside at the root of the target AD LDS (ADAM) partition.
However, if you desire more granular control, you can create one or more People OUs anywhere in the directory and provide different instances of Logon Manager with the fully qualified paths to different People OUs, based on the requirements of your organization, as described in Configure Logon Manager to Use a Specific People OU.
To create the People OU:
-
In the ESSO Suite Administrative Console, select the Repository node in the tree.
-
Click the Click here to connect link in the right-hand pane. The Console displays the "Connect to Repository" dialog. Fill in the fields as explained in steps 3-7 on page 54 and click OK to connect.
-
In the tree, right-click the root of the target AD LDS (ADAM) instance, and selectCreate People Container from the context menu.
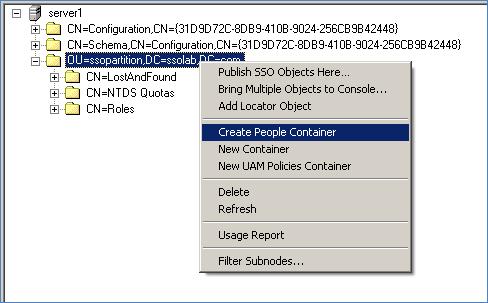
-
Verify that the People OU now exists at the root of the AD LDS (ADAM) instance's sub-tree.
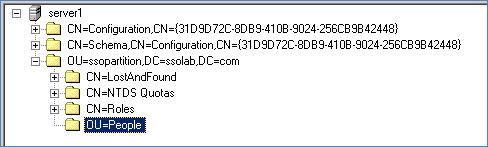
If the People OU does not appear after you complete the above steps, or if you receive errors indicating naming violations or other problems in the directory, consult the AD LDS (ADAM) documentation for possible causes and remedies.
2.8.3 Creating the Configuration Object Container and Sub-Tree Structure
Note:
While it is possible to use an existing container for storing Logon Manager objects, doing so may impair directory performance. Oracle highly recommends that you create a dedicated configuration object container.-
In the Logon Manager Administrative Console, select the Repository node in the tree.
-
Click the Click here to connect link in the right-hand pane. The Console displays the "Connect to Directory" dialog.
-
Fill in the fields as explained in steps 3-7 on page 32 and click OK to connect.
-
In the tree, right-click the desired parent container and select New Container from the context menu, as shown below:
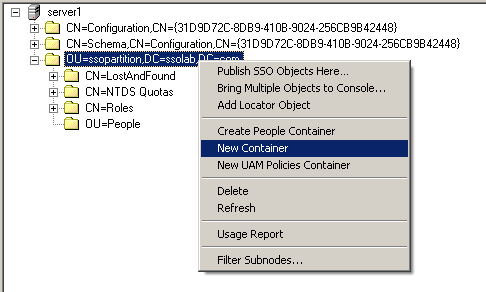
The Console displays the "New Container" dialog:
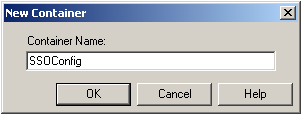
-
In the "New Container" dialog, enter the desired name and click OK.
Note:
Unless your environment calls for a specific name for this container, Oracle recommends that you use the default name, SSOConfig. -
Repeat steps 4 and 5 to create any additional containers you may need.
2.8.4 Granting Required Permissions to Logon Manager Users
You must grant Logon Manager users the following permissions in order to enable them to use Logon Manager:
-
Read access to the Logon Manager application partition. This permits users to read configuration objects and credentials during synchronization.
-
Write access to thePeople OU. This permits users to create credential objects during synchronization.
Note:
This procedure assumes you have already created the SSOUsers group and added the desired users to the group. You will grant the permissions listed above to the SSOUsers group, not individual users. For instructions on creating the group and assigning users to the group, see Appendix B: Logon Manager Repository Object Classes and Attributes.To grant these permissions:
-
Log on to the target server as an administrator and open a command prompt.
-
Use the following command to grant the SSOUsers group read access to the Logon Manager application partition (note that the command is a single line):
dsacls \\<hostname>:<port>\ <sso_partition_dn> /G "<domain>\SSOUsers":gr -
Use the following command to grant the SSOUsers group write access to the People OU (note that the command is a single line):
dsacls \\<hostname>:<port>\ OU=People,<sso_partition_dn> /G "<domain>\SSOUsers":CCWSSubstitute the variables in the above commands as follows:
-
<hostname>- the URL of the server running the target AD LDS (ADAM) instance. -
<domain>- target domain name. -
<port>- the port on which the target AD LDS (ADAM) instance is listening for connections. -
<sso_partition_dn>- the fully qualified DN of the Logon Manager application partition. Example:ou=ssopartition,dc=ssolab,dc=com
-
2.9 Configuring the AD LDS (ADAM) Synchronizer
After you have prepared AD LDS (ADAM) for Logon Manager, you must configure the AD LDS (ADAM) synchronizer for your environment. Configure these settings on your "template" client machine and include them in the MSI package you will use to deploy Logon Manager to end-users. Before starting this procedure, make sure that the Logon Manager Administrative Console and the Logon Manager Agent (including the AD LDS (ADAM) synchronizer plug-in) are installed.
Note:
Do not include application templates in the MSI package as they will not function in a directory-synchronized environment. The ability to include templates directly in the MSI package is for specialized use only. Instead, push them to the directory for automatic retrieval by the Logon Manager Agent.-
Launch the Logon Manager Administrative Console.
-
In the left-hand pane, right click the Global Agent Settings node, then selectImport > From Live HKLM from the context menu. The Console imports the current Agent settings from the Windows registry.
-
Configure the Agent as described in Recommended Global Agent Settings and Recommended Administrative Overrides.
Note:
When the check box next to a setting is unchecked, the default value for the setting (shown grayed-out to the right of the check box) is in effect. -
Save your configuration to an XML file for future reference. From the File menu, select Save, enter the desired file name, and click Save. If you change your settings, you can load this XML file into the Console to revert back to your original choices.
-
From the Tools menu, select Write Global Agent Settings to HKLM. The Console writes your changes to the registry and restarts the Agent.