35.2 Working with the Adaptive Authentication Service
The following options are available:
-
OTP from Oracle Mobile Authenticator
-
OTP through SMS
-
OTP through Email
-
Access Request Notification from Oracle Mobile Authenticator
Figure 35-1 shows the Second Factor Authentication page in which the user has selected the OTP Through Email option.
In this case, the user receives the OTP via a configured Email address.
Figure 35-1 Second Factor Authentication Preferred Method Page
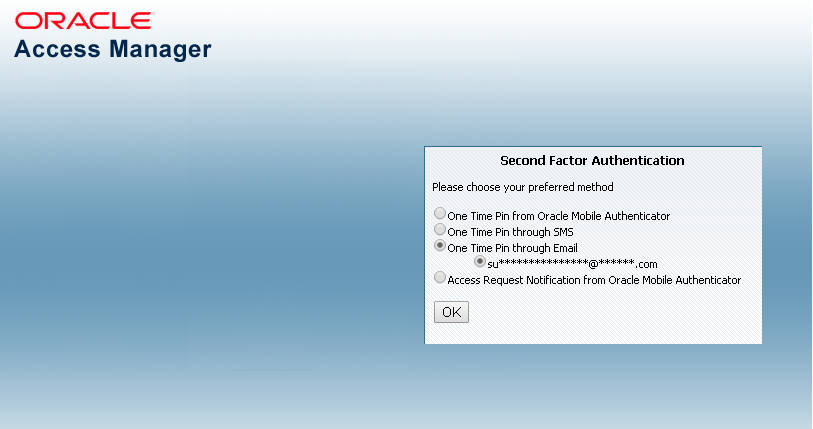
Description of "Figure 35-1 Second Factor Authentication Preferred Method Page"
If the selected option is either OTP From Oracle Mobile Authenticator or Access Request Notification from Oracle Mobile Authenticator, the Adaptive Authentication Service works in tandem with the Oracle Mobile Authenticator (OMA), a mobile device app that uses Time-based One Time Password and push notifications to authenticate users within the second factor authentication scheme.
In advance of using the OTP from OMA or Access Request Notification from OMA options, a user must download a supported authenticator app to a mobile device (for example, Oracle Mobile Authenticator to an Apple iPhone) and configure it by clicking a link provided by the Access Manager administrator. (The OMA app is not needed if using the OTP through Email or OTP through SMS options.)
Note:
You must configure the Oracle Mobile Authenticator mobile device app to retrieve a secret key required to generate a OTP.
See Generating a Secret Key for the Oracle Mobile Authenticator for information about the secret key.
See Understanding Oracle Mobile Authenticator Configuration for information on how to configure the OMA.
The following topics describe each option and how the Oracle Mobile Authenticator works:
35.2.1 Understanding the One Time Password Option
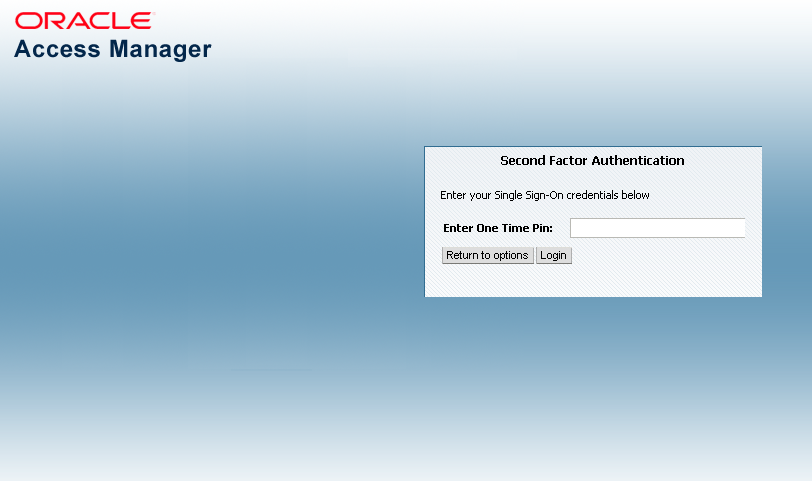
After the successful authentication of initial credentials, the user needs to choose one of the OTP options as a second-factor authentication. Access to the protected resource is provided when the OTP received by the user is entered in the OTP login page.
Let's assume the Adaptive Authentication Service is enabled and configured for second factor authentication. When the user accesses a resource protected by Access Manager, a page is displayed that requests a user name and password. If these initial credentials are authenticated successfully, a Second Factor Authentication Preferred Method Page page is displayed and the user selects from one of the options. In this use case, the user selects one of the OTP options and receives a OTP through SMS/Email or generated and displayed by the OMA app. The user enters the OTP in the OTP login page.
Figure 35-2 shows the OTP login page.
Once the OTP is successfully validated by Access Manager, the user is directed to the protected resource. On failure of any of the OTP options, an error message will be displayed, and the user will be returned to the same OTP page.
Note:
Access Manager validates the OTP using the Time-based One Time Password (TOTP) algorithm. TOTP is a two-factor authentication scheme specified by the Internet Engineering Task Force (IETF) under RFC 6238 and used by the Adaptive Authentication Service. TOTP is an extension of the HMAC-based One Time Password algorithm and supports a time-based moving factor (a value that must be changed each time a new password is generated).
The following topics describe how the user may receive the OTP:
35.2.1.1 About using OTP through Email or SMS
The user receives the OTP through an email or SMS and enters it in the OTP login page.
In cases where OTP through email or SMS is chosen, Access Manager will send a OTP to the configured email address or phone number respectively. The user then enters the received OTP and Access Manager will validate it. On a successful validation, the user will be directed to the protected resource.
The Adaptive Authentication Service expects that the required email address or phone number is configured in the appropriate field.
See Configuring the Adaptive Authentication Plug-in in the Oracle Access Management Console.
When you use the OTP with Email or SMS option, the OTP is accessible from any device on which the email address can be accessed or from the SMS app that is associated with the specified phone number, respectively.
Note:
The OMA mobile app is not used for the OTP through Email or OTP through SMS options.
35.2.1.2 About using OTP from Oracle Mobile Authenticator
In the use case where a OTP will be generated and displayed by the OMA app on a mobile device, the app must be configured with the Access Manager server details.
Following this configuration, the user authenticates with Access Manager using the proper credentials and Access Manager will return a secret key. This secret key is unique to each user and known only to Access Manager and the OMA. The secret key is used to generate the OTP.
See Generating a Secret Key for the Oracle Mobile Authenticator on how to populate the secret key with the required data.
After Access Manager generates a OTP for the user using the secret key, the OTP is pushed to the OMA. The user then enters the OTP in the One Time Pin Login Page. If the OTP generated by Access Manager matches the OTP entered by the user, access to the protected resource is allowed. If the OTP entries do not match, access is not allowed.
See Using the Oracle Mobile Authenticator with OTP And Access Request.
Note:
The OMA refreshes the OTP every 30 seconds so the OTP entered by a user is valid only for that period of time.
35.2.2 Understanding the Access Request (Push) Notification Option
The Access Manager sends an Access Request Notification to the notification server which is then pushed to the user’s configured device.
Let's assume the Adaptive Authentication Service is enabled and configured for second factor authentication. When the user accesses a resource protected by Access Manager, a page is displayed that requests a user name and password. If these initial credentials are authenticated successfully, a Second Factor Authentication Preferred Method page is displayed and the user selects from one of the options. In this use case, the user selects Access Request Notification from Oracle Mobile Authenticator.
Note:
This is a push notification option which works in tandem with the OMA.
See Using the Oracle Mobile Authenticator with OTP And Access Request.
Figure 35-3 shows the Second Factor Authentication Preferred Method Page with Access Request Notification that has been selected.
Figure 35-3 Access Request Notification Preferred Method Page
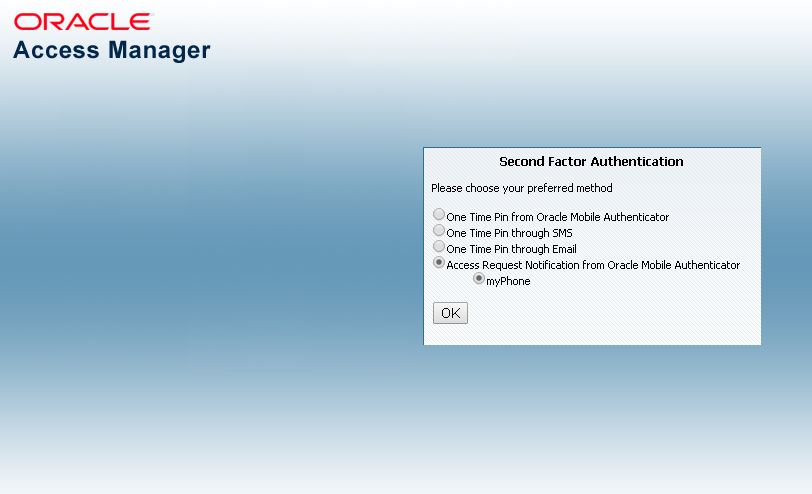
Description of "Figure 35-3 Access Request Notification Preferred Method Page"
When the user selects Access Request Notification from the Second Factor Authentication Preferred Method Page, Access Manager sends an Access Request Notification to either the Apple Push Notification Server or the Google Notification Server depending upon the user's configured device. The notification server then pushes a notification to the mobile device and the user will approve or deny it. Based on a successful response, the user will be directed to the protected resource. On failure, an error message will be displayed and the user will be returned to the same OTP page.
Figure 35-4 shows the Access Request Notification message that is displayed during this process.
Figure 35-4 Access Request Notification Wait Screen
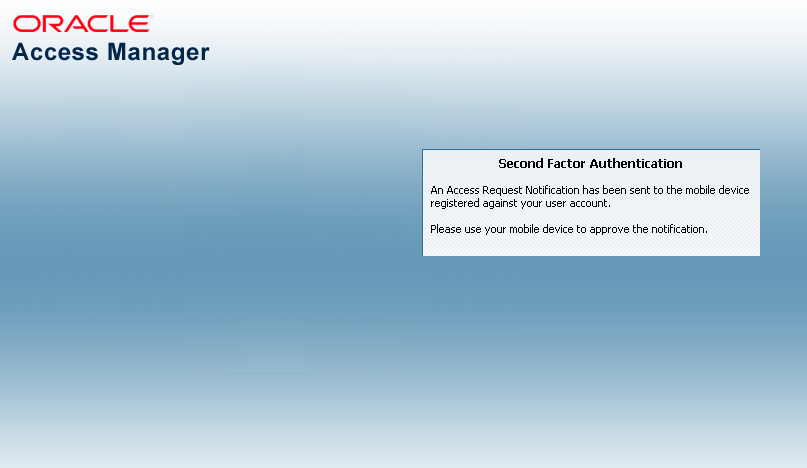
Description of "Figure 35-4 Access Request Notification Wait Screen"
35.2.3 Using the Oracle Mobile Authenticator with OTP And Access Request
The user downloads the OMA app to the mobile device and configures it to receive the access request notification.
Depending on the selected option, the Adaptive Authentication Service will need to work in tandem with the Oracle Mobile Authenticator (OMA), a mobile device app that uses Time-based One Time Password and push notifications to authenticate users with the second factor authentication scheme. To receive the OTP or Access Request Notification using the OMA, a user downloads it to an Apple or Android mobile device and configures it by clicking a link provided by the Access Manager administrator. Access Manager and OMA must share a secret key.
See Generating a Secret Key for the Oracle Mobile Authenticator about the secret key.
See Understanding Oracle Mobile Authenticator Configuration on how to configure OMA.
Note:
The OMA app is not needed if using the OTP through Email or OTP through SMS options.