40.4 Managing Access Manager Policies for Use with Identity Federation
The following topics explain how to use policy responses in Access Manager in the context of federation policies:
40.4.1 About Policy Responses with Assertion Attributes for Identity Federation
A policy can optionally include one or more authentication responses, or authorization responses, or both. You can configure the use of assertion attributes when setting up Access Manager policy responses with Identity Federation.
You use assertion attributes as follows:
-
Authorization policy conditions
-
Response attributes as HTTP headers
-
Response attributes for identity context
Figure 40-7 shows the Response configuration tab for an authorization policy:
Figure 40-7 Authorization Policy Response Tab
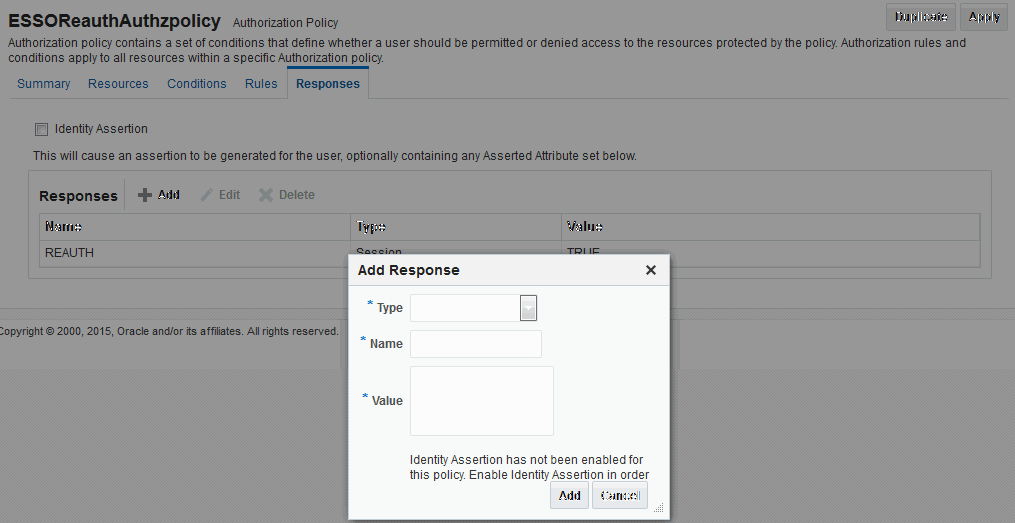
Description of "Figure 40-7 Authorization Policy Response Tab"
Table 40-6 describes the elements for a policy response.
Table 40-6 Policy Response Elements
| Element | Description |
|---|---|
|
Name |
This is a unique name to distinguish this response from other responses that use the same mechanism (type). |
|
Type |
This is the mechanism used to convey the response form of the action to be taken with the value string. Select Assertion Attribute. |
|
Value |
This is the response expression, set as a variable. To provide the federation data as response attributes in the authentication or authorization policy, the values can reference:
|
40.4.2 Defining Policy Responses with Assertion Attributes for Identity Federation
You can use the Oracle Access Management Console to configure policy responses with assertion attributes.
40.4.2.1 Background on Conditions and Responses for Identity Federation
Identity Federation conditions and responses must be specified separately because they are used for different tasks.
For example, if the identity provider sends a role assertion and the service provider wanted to only allow people who had a role of sales to gain access to the resource, you add a condition as follows:
-
The Condition Namespace is "Session".
-
The Name is "fed.attr.role".
-
The Operator is set to EQUALS.
-
Value is "sales".
A condition is used to control access to a resource within Access Manager.
Note:
-
Replace the role in this example to the actual SAML asserted attribute.
-
If you want to use the standard SAML NameID value as the condition, then the value is "attr.fed.nameidvalue".
A response, on the other hand, enables you to pass an asserted attribute to the application.For example, if you wanted to pass the asserted attribute role to a back-end application in an HTTP header, you would:
-
Go to the Response tab.
-
Add a Header, name
Role(this is the name of the HTTP header). -
The value would be
$session.attr.fed.attr.role.
Then replace the role in this example to correspond to the SAML asserted attribute.
40.4.2.3 Viewing or Configuring Responses with Assertion Attributes
To view or configure responses with assertion attributes:
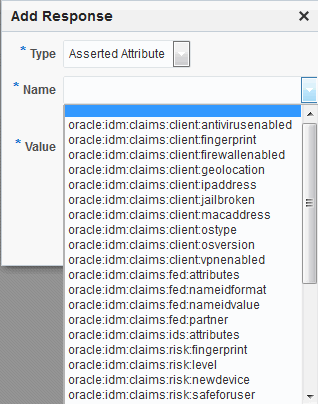
Figure 40-8 shows an example of federation response attribute configuration.
Figure 40-8 Adding a Federation Response Attribute to an AuthZ Policy
Description of "Figure 40-8 Adding a Federation Response Attribute to an AuthZ Policy"