54.3 Deploying the Access Portal Service
The following topics describes how to configure the environment and deploy Access Portal:
-
Preparing and Enabling the Access Portal Service on an Oracle Repository
-
Preparing and Enabling the Access Portal Service on Microsoft Active Directory
-
(Active Directory Only) Deploying the OAMAgent Web Application
-
Protecting the Oracle Traffic Director Instance with the Webgate Plugin
-
(Optional) Enabling the Detached Credential Collector for the Target Webgate
54.3.1 Deploying Java Cryptography Extension Policy Files
If you want to enable unlimited strength jurisdiction policy encryption on your Oracle Access Manager server, you must download the appropriate policy files and place them in the server's Java Runtime Environment.
To deploy Java Cryptography extension policy files:
54.3.2 Identity Store Configuration File
You can apply guidelines to create the idstore.props file that configures the identity keystore for the Access Portal Service.
You pass this file to the IDM Configuration Tool.
See Preparing and Enabling the Access Portal Service on an Oracle Repository.
Oracle Unified Directory Example
# Common IDSTORE_HOST: IDMHOST1.mycompany.com IDSTORE_PORT: 1389 IDSTORE_ADMIN_PORT: 4444 IDSTORE_KEYSTORE_FILE: OUD_ORACLE_INSTANCE/OUD/config/admin-keystore IDSTORE_KEYSTORE_PASSWORD: Password key IDSTORE_BINDDN: cn=oudadmin IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com IDSTORE_SEARCHBASE: dc=mycompany,dc=com IDSTORE_USERNAMEATTRIBUTE: cn IDSTORE_LOGINATTRIBUTE: uid IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com IDSTORE_NEW_SETUP: true POLICYSTORE_SHARES_IDSTORE: true # OAM IDSTORE_OAMADMINUSER:oamadmin IDSTORE_OAMSOFTWAREUSER:oamLDAP OAM11G_IDSTORE_ROLE_SECURITY_ADMIN:OAMAdministrators # OAM and OIM IDSTORE_SYSTEMIDBASE: cn=systemids,dc=mycompany,dc=com # OIM IDSTORE_OIMADMINGROUP: OIMAdministrators IDSTORE_OIMADMINUSER: oimLDAP # WebLogic IDSTORE_WLSADMINUSER : weblogic_idm IDSTORE_WLSADMINGROUP : WLSAdmins
Oracle Internet Directory Example
# Common IDSTORE_HOST: OIDHOST1.mycompany.com IDSTORE_PORT: 3060 IDSTORE_BINDDN: cn=orcladmin IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com IDSTORE_SEARCHBASE: dc=mycompany,dc=com IDSTORE_USERNAMEATTRIBUTE: cn IDSTORE_LOGINATTRIBUTE: uid IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com POLICYSTORE_SHARES_IDSTORE: true IDSTORE_NEW_SETUP: true # OAM IDSTORE_OAMADMINUSER:oamadmin IDSTORE_OAMSOFTWAREUSER:oamLDAP OAM11G_IDSTORE_ROLE_SECURITY_ADMIN:OAMAdministrators # OAM and OIM IDSTORE_SYSTEMIDBASE: cn=systemids,dc=mycompany,dc=com # OIM IDSTORE_OIMADMINGROUP: OIMAdministrators IDSTORE_OIMADMINUSER: oimLDAP # WebLogic IDSTORE_WLSADMINUSER : weblogic_idm IDSTORE_WLSADMINGROUP : WLSAdmins
Microsoft Active Directory Example
# Common IDSTORE_HOST: <AD-server-hostname>IDSTORE_PORT: <AD-server-port>IDSTORE_DIRECTORYTYPE: adIDSTORE_BINDDN: <domain>\AdministratorIDSTORE_PASSWD: <password>IDSTORE_USERNAMEATTRIBUTE: cnIDSTORE_LOGINATTRIBUTE: cn (or another login attribute)>IDSTORE_USERSEARCHBASE: CN=Users,DC=essodev,DC=idc,DC=localIDSTORE_SEARCHBASE: DC=essodev,DC=idc,DC=localIDSTORE_GROUPSEARCHBASE: CN=Users,DC=essodev,DC=idc,DC=localIDSTORE_SYSTEMIDBASE: CN=Users,DC=essodev,DC=idc,DC=localIDSTORE_OAMSOFTWAREUSER: oamSoftwareUserIDSTORE_OAMADMINUSER: oamAdminUserOAM11G_CREATE_IDSTORE: trueESSO_IDSTORE_HOST : <AD-server-hostame>ESSO_IDSTORE_PORT : <AD-server-port>ESSO_IDSTORE_BINDDN : <domain>\AdministratorESSO_IDSTORE_TYPE : adIS_ESSO_PRESENT : trueESSO_IDSTORE_PASSWD : <password>
Where:
-
IDSTORE_HOSTandIDSTORE_PORTare, respectively, the host and port of your Identity Store directory. Specify the back end directory here, rather than OVD. In the case of OID and OUD, specify, respectively, one of the Oracle Internet Directory or Oracle Unified Directory instances, for example:OID:
OIDHOST1and3060OUD:
IDMHOST1and1389 -
IDSTORE_ADMIN_PORT(LDAP_DIR_ADMIN_PORT) is the administration port of your Oracle Unified Directory instance. If you are not using Oracle Unified Directory, you can leave out this parameter. -
IDSTORE_KEYSTORE_FILEis the location of the Oracle Unified Directory Keystore file. It is used to enable communication with Oracle Unified Directory using the Oracle Unified Directory administration port. It is calledadmin-keystoreand is located inOUD_ORACLE_INSTANCE/OUD/config. If you are not using Oracle Unified Directory, you can leave out this parameter. This file must be located on the same host that theidmConfigToolcommand is running on. The command uses this file to authenticate itself with OUD. -
IDSTORE_KEYSTORE_PASSWORDis the encrypted password of the Oracle Unified Directory keystore. This value can be found in the fileOUD_ORACLE_INSTANCE/OUD/config/admin-keystore.pin. If you are not using Oracle Unified Directory, you can leave out this parameter. This file must be located on the same host that theidmConfigToolcommand is running on. The command uses this file to authenticate itself with OUD. -
IDSTORE_BINDDNis an administrative user in the Identity Store Directory -
IDSTORE_GROUPSEARCHBASEis the location in the directory where Groups are Stored. -
IDSTORE_SEARCHBASEis the location in the directory where Users and Groups are stored. -
IDSTORE_USERNAMEATTRIBUTEis the name of the directory attribute containing the user's name. Note that this is different from the login name. -
IDSTORE_LOGINATTRIBUTEis the LDAP attribute which contains the users Login name. -
IDSTORE_USERSEARCHBASEis the location in the directory where Users are Stored. -
IDSTORE_NEW_SETUPis always set to true for Oracle Unified Directory. If you are not using OUD, you do not need to specify this attribute. -
POLICYSTORE_SHARES_IDSTOREis set totruefor IDM 11g. -
IDSTORE_OAMADMINUSERis the name of the user you want to create as your Access Manager Administrator. -
IDSTORE_OAMSOFTWAREUSERis a user that gets created in LDAP that is used when Access Manager is running to connect to the LDAP server. -
OAM11G_IDSTORE_ROLE_SECURITY_ADMINis the name of the group which is used to allow access to the OAM console. -
IDSTORE_SYSTEMIDBASEis the location of a container in the directory where users can be placed when you do not want them in the main user container. This happens rarely but one example is the Oracle Identity Manager reconciliation user which is also used for the bind DN user in Oracle Virtual Directory adapters. -
IDSTORE_OIMADMINGROUPIs the name of the group you want to create to hold your Oracle Identity Manager administrative users. -
IDSTORE_OIMADMINUSERis the user that Oracle Identity Manager uses to connect to the Identity store. -
IDSTORE_WLSADMINUSER: The username to be used for logging in to the web logic domain once it is enabled by SSO. -
IDSTORE_WLSADMINGROUP: is the name of the group to which users who are allowed to log in to the WebLogic system components, such as the WLS Console and EM, belong.
Use OIM entries only if your topology includes Oracle Identity Manager. Use OAM entries only if your topology includes Access Manager.
54.3.3 Oracle Access Manager Configuration File
You can apply guidelines to create the config-oam.props file that configures the Oracle Access Manager instance.
You will pass this file to the IDM Configuration Tool in Preparing and Enabling the Access Portal Service on an Oracle Repository. Note that the Access Portal Service requires the Simple mode security posture. To enable this posture, set the parameters below as follows:
OAM11G_OAM_SERVER_TRANSFER_MODE: simple
OAM_TRANSFER_MODE: simple
The file will have the following structure:
Create a properties file called config_oam.props with the following contents:
WLSHOST: ADMINVHN.mycompany.com
WLSPORT: 7001
WLSADMIN: weblogic
WLSPASSWD: Admin Password
IDSTORE_DIRECTORYTYPE: OUD
IDSTORE_HOST: IDSTORE.mycompany.com
IDSTORE_PORT: 389
IDSTORE_BINDDN: cn=oudadmin
IDSTORE_USERNAMEATTRIBUTE: cn
IDSTORE_LOGINATTRIBUTE: uid
OAM11G_SERVER_LOGIN_ATTRIBUTE: uid
IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com
IDSTORE_SEARCHBASE: dc=mycompany,dc=com
IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com
IDSTORE_SYSTEMIDBASE: cn=systemids,dc=mycompany,dc=com
IDSTORE_OAMSOFTWAREUSER: oamLDAP
IDSTORE_OAMADMINUSER: oamadmin
PRIMARY_OAM_SERVERS: IDMHOST1.mycompany.com:5575,IDMHOST2.mycompany.com:5575
WEBGATE_TYPE: ohsWebgate11g
ACCESS_GATE_ID: Webgate_IDM
OAM11G_OIM_WEBGATE_PASSWD: password to be assigned to WebGate
COOKIE_DOMAIN: .mycompany.com
OAM11G_WG_DENY_ON_NOT_PROTECTED: true
OAM11G_IDM_DOMAIN_OHS_HOST: SSO.mycompany.com
OAM11G_IDM_DOMAIN_OHS_PORT: 443
OAM11G_IDM_DOMAIN_OHS_PROTOCOL: https
OAM11G_SERVER_LBR_HOST: SSO.mycompany.com
OAM11G_SERVER_LBR_PORT: 443
OAM11G_SERVER_LBR_PROTOCOL: https
OAM11G_OAM_SERVER_TRANSFER_MODE: simple
OAM_TRANSFER_MODE: simple
OAM11G_IDM_DOMAIN_LOGOUT_URLS: /console/jsp/common/logout.jsp,/em/targetauth/emaslogout.jsp
OAM11G_IDSTORE_ROLE_SECURITY_ADMIN: OAMAdministrators
OAM11G_SSO_ONLY_FLAG: false
COOKIE_EXPIRY_INTERVAL: 120
OAM11G_IMPERSONATION_FLAG: false
OAM11G_OIM_INTEGRATION_REQ: false
OAM11G_OIM_OHS_URL:https://SSO.mycompany.com:443
SPLIT_DOMAIN:true
Where:
-
WLSHOST(ADMINVHN) is the host of your administration server. This is the virtual name. -
WLSPORTis the port of your administration server. -
WLSADMINis the WebLogic administrative user you use to log in to the WebLogic console. -
WLSPASSWDis the WebLogic administrator password. -
IDSTORE_DIRECTORYTYPEisOUD,OIDorOVD. -
IDSTORE_HOSTandIDSTORE_PORTare the host and port of the Identity Store directory when accessed through the load balancer. -
IDSTORE_BINDDNis an administrative user in the Identity Store directory. -
IDSTORE_USERSEARCHBASEis the location in the directory where Users are stored. -
IDSTORE_GROUPSEARCHBASEis the location in the directory where Groups are stored. -
IDSTORE_SEARCHBASEis the location in the directory where Users and Groups are stored. -
IDSTORE_SYSTEMIDBASEis the location of a container in the directory where the user oamLDAP is stored. -
IDSTORE_OAMSOFTWAREUSERis the name of the user account to be used to interact with LDAP. -
IDSTORE_OAMADMINUSERis the name of the user account that can access your OAM Console. -
PRIMARY_OAM_SERVERSis a comma separated list of your OAM Servers and the proxy ports they use, for example: IDMHOST1:OAM_PROXY_PORTNote:
To determine the proxy ports your OAM Servers use:
-
Log in to the Oracle Access Management Console.
-
Click Configuration in the upper right corner.
-
Click Server Instances.
-
Search for the OAM Server, such as WLS_OAM1, and select Open from the Actions menu.
-
Proxy port is the value shown as Port.
-
-
ACCESS_GATE_IDis the name you want to assign to the WebGate. -
OAM11G_OIM_WEBGATE_PASSWDis the password to be assign to the WebGate. -
OAM11G_IDM_DOMAIN_OHS_HOSTis the name of the load balancer which is in front of the OHS's. -
OAM11G_IDM_DOMAIN_OHS_PORTis the port that the load balancer listens on (HTTP_SSL_PORT). -
OAM11G_IDM_DOMAIN_OHS_PROTOCOLis the protocol to use when directing requests at the load balancer. -
OAM11G_WG_DENY_ON_NOT_PROTECTED, when set tofalse, allows login pages to be displayed. It should be set totruewhen using webgate11g. -
OAM_TRANSFER_MODEis the security model that the Oracle Access Manager Servers function in. Valid values aresimpleandopen. If you use thesimplemode, you must define a global passphrase. -
OAM11G_OAM_SERVER_TRANSFER_MODEis the security model that the OAM Servers function in. -
OAM11G_IDM_DOMAIN_LOGOUT_URLSis set to the various logout URLs. -
OAM11G_SSO_ONLY_FLAGconfgures Access Manager as authentication only mode or normal mode, which supports authentication and authorization.If
OAM11G_SSO_ONLY_FLAGistrue, the OAM Server operates in authentication only mode, where all authorizations return true by default without any policy validations. In this mode, the server does not have the overhead of authorization handling. This is recommended for applications which do not depend on authorization policies and need only the authentication feature of the OAM Server.If the value is
false, the server runs in default mode, where each authentication is followed by one or more authorization requests to the OAM Server. WebGate allows the access to the requested resources or not, based on the responses from the OAM Server. -
OAM11G_IMPERSONATION_FLAGis set totrueif you are configuring OAM Impersonation. -
OAM11G_SERVER_LBR_HOSTis the name of the load balancer fronting your site. This and the following two parameters are used to construct your login URL. -
OAM11G_SERVER_LBR_PORTis the port that the load balancer is listening on (HTTP_SSL_PORT). -
OAM11G_SERVER_LBR_PROTOCOLis the URL prefix to use. -
OAM11G_OIM_INTEGRATION_REQshould be set totrueif you are building a topology which contains both OAM and OIM. Otherwise set tofalseat this point. This value is only set to true when performing Access Manager/Oracle Identity Manager integration and is set during the integration phase. -
OAM11G_OIM_OHS_URLshould be set to the URL of your load balancer. This parameter is only required if your topology contains OAM and OIM. -
COOKIE_DOMAINis the domain in which the WebGate functions. -
WEBGATE_TYPEis the type of WebGate agent you want to create. -
OAM11G_IDSTORE_NAMEis the Identity Store name. If you already have an Identity Store in place which you wish to reuse (rather than allowing the tool to create a new one for you), then set the value of this parameter to the name of the Identity Store you wish to reuse. -
OAM11G_SERVER_LOGIN_ATTRIBUTEwhen set touid, ensures that when users log in, their username is validated against theuidattribute in LDAP. -
SPLIT_DOMAINshould be set totrueIf you are creating a domain with just OAM or OAM located in a different domain from OIM (Split Domain). Otherwise, it is not necessary to specify this parameter.
54.3.4 Understanding the Access Portal Service Repository Objects
The vGoLocator object is required for all repositories and the value of its vGOLocatorAttribute attribute specifies the path to the People container in which the Access Portal Service stores application credentials for each user.
The vGOLocator object must point to the same data store instance as the Oracle Access Manager instance on which the Access Portal Service is deployed.
For Oracle LDAP directories, the following applies:
-
If there is a single object under the
vGOLocatorcontainer, thevGoLocatorAttributevalue is parsed regardless of the object's name. -
If there are multiple objects under the
vGOLocatorcontainer, the object named default is parsed. If no object nameddefaultexists, the request will fail. -
If
thevGOLocatorAttributeattribute has no value or does not exist, or if thevGOLocatorcontainer does not exist, the request will fail.
When using Microsoft Active Directory, the Access Portal Service stores application credentials under the Users container as described below:
-
If there is a single object under the
vGOLocatorcontainer, thevGoLocatorAttributevalue is parsed regardless of the object's name. -
If there are multiple objects under the
vGOLocatorcontainer, the object named default is parsed. If no object nameddefaultexists, the data will be within theUSERScontainer. -
If
thevGOLocatorAttributeattribute has no value or does not exist, or if thevGOLocatorcontainer does not exist, the data will be stored within theUserscontainer.
You must explicitly enable the storage of user credentials under respective user objects using the Oracle Enterprise Single Sign-On Suite Administrative Console. This makes the following changes to the repository:
-
The User class is added as a possible superior to the vGOUserData class.
-
All users are granted the right to create vGOUserData objects. These rights are granted at the directory root and are recursively inherited down to the user objects.
54.3.5 Preparing and Enabling the Access Portal Service on an Oracle Repository
You can prepare and enable the Access Portal Service on an Oracle Repository.
Before completing this procedure, make sure you have created the required configuration files as described in Identity Store Configuration File and Oracle Access Manager Configuration File.
The idmConfigTool is located at:
IAM_ORACLE_HOME/idmtools/bin
Note:
When you run the idmConfigTool, it creates or appends to the file idmDomainConfig.param. This file is generated in the same directory that the idmConfigTool is run from. To ensure that each time the tool is run, the same file is appended to, always run the idmConfigTool from the directory:
IAM_ORACLE_HOME/idmtools/bin
The syntax of the command on Linux is:
idmConfigTool.sh -configOAM input_file=configfile
For example:
idmConfigTool.sh -configOAM input_file=config_oam1.props
When the command runs you are prompted to enter the password of the account you are connecting to the Identity Store with. You are also asked to specify the passwords you want to assign to these accounts:
-
IDSTORE_PWD_OAMSOFTWAREUSER -
IDSTORE_PWD_OAMADMINUSER
-
On the machine running your target Oracle Access Manager instance, change into the following directory:
/Oracle/Middleware/Oracle_IDM1/idmtools/bin -
Set the following environment variables:
setenv ORACLE_HOME /Oracle/Middleware/Oracle_IDM1setenv MW_HOME /Oracle/Middlewaresetenv JAVA_HOMEJDKPath(where JDKPath is the full path to the Java Development Kit used by the Oracle Access Manager instance)
-
Pre-configure the identity store to extend the directory schema with the required object classes by running the following command:
./idmConfigTool.sh -preConfigIDStore input_file=idstore.propswhere
idstore.propsis a property file containing configuration parameters specific to your environment. For information on assembling this file, see Identity Store Configuration File. -
Create the required users and groups by running the following command:
./idmConfigTool.sh -prepareIDStore mode=all input_file=idstore.propswhere
idstore.propsis a property file containing configuration parameters specific to your environment. For information on assembling this file, see Identity Store Configuration File.This command does the following:
-
Adds the Access Portal Service object classes and attributes to the schema
-
Creates the
CO,People, andvGoLocatorcontainers (with create permissions only, including children). For more information on these containers, see Understanding the Access Portal Service Repository Objects.
-
-
Create and configure the required Webgate profile by running the following command:
./idmConfigTool.sh -configOAM input_file=config_oam.propswhere
config_oam.propsis a property file containing configuration parameters specific to your environment. For information on assembling this file, see Oracle Access Manager Configuration File. -
Add conditions to the Admin role in the Security Realm as follows:
-
Log in to the Weblogic Administration Server Console.
-
In the left pane of the console, click Security Realms.
-
On the "Summary of Security Realms" page, click myrealm under the Realms table.
-
On the "Settings" page for myrealm, click the Roles & Policies tab.
-
On the "Realm Roles" page, expand the Global Roles entry under the Roles table. This brings up the entry for Roles.
-
Click the Roles link to go to the Global Roles page.
-
On the "Global Roles" page, click the Admin role to go to the Edit Global Role page:
-
On the "Edit Global Roles" page, under Role Conditions, click Add Conditions.
-
On the "Choose a Predicate" page, select Group from the predicates list and click Next.
-
On the Edit Arguments Page, specify
OAMAdministratorsin the Group Argument field and click Add. -
Click Finish to return to the "Edit Global Rule" page.
The Role Conditions now show the
OAMAdministratorsGroup as an entry. -
Click Save to finish adding the Admin role to the
OAMAdministratorsGroup.
-
-
Check the log file for any errors or warnings and correct them. A file named
automation.logis created in the directory where you run the tool. -
Restart the WebLogic Administration Server.
-
Enable the Access Portal Service:
-
Log on to the Oracle Access Manager Console.
-
Select the Launch Pad tab.
-
In the Configuration section, click Available Services.
-
In the screen that appears, click Enable next to Access Portal Service.
-
Note:
After you run idmConfigTool, several files are created that you need for subsequent tasks. Keep these in a safe location.
Two 11g WebGate profiles are created: Webgate_IDM, which is used for intercomponent communication and Webgate_IDM_11g, which is used by 11g Webgates.
The following files exist in the directory ASERVER_HOME/output/Webgate_IDM_11g. You need these when you install the WebGate software.
-
cwallet.sso -
ObAccessClient.xml -
password.xml
Additionally, you need the files aaa_cert.pem and aaa_key.pem, which are located in the directory ASERVER_HOME/output/Webgate_IDM.
54.3.6 Preparing and Enabling the Access Portal Service on Microsoft Active Directory
You can prepare and enable the Access Portal Service on Microsoft Active Directory.
The following LDIF file is required to extend the Active Directory schema with Access Portal Service classes and attributes:
<ORACLE_HOME>/idmtools/templates/ad/esso_schema_extn.ldif
The file is a template file. Before you can proceed, you need to modify the values, such as domain names and paths to match the target environment.
To prepare and enable the Access Portal Service with Microsoft Active Directory:
-
Extend the Active Directory schema by running the following command on the server machine hosting the repository:
ldifde –i –f esso_schema_extn.ldifUpon completion, a message will confirm that importing data was successful:
-
Use the
ADSIEdittool to create containers namedCO,People, andvGoLocatorunder the repository root. -
Under the
vGoLocatorcontainer, create an object nameddefaultof classvGoLocatorClassand set its attribute value to the DN of the container that holds thePeoplecontainer. For more information, see Understanding the Access Portal Service Repository Objects. -
Enable the storage of user credentials under user objects:
-
Launch the Oracle Enterprise Single Sign-On Suite Administrative Console and connect to the target repository.
-
In the Console, select Enable Storing Credentials Under User Object (AD Only) from the Repository menu.
-
The Console displays a dialog informing you of the changes about to be made to your Active Directory schema. Click OK.
-
Wait for a dialog confirming the changes to appear, then click OK to dismiss it.
Note:
Members of protected groups (i.e., users whose ACLs are governed by the AdminSDHolder object) will not be able to store credentials under their user objects until the AdminSDHolder ACL is updated with permissions required by this feature. See the guide Deploying Logon Manager with a Directory-Based Repository for instructions on how to remedy this issue.
-
-
Create the users in Active Directory if necessary.
-
Create a user data store:
-
Log on to the Oracle Access Manager console and click Configuration at the top of the page.
-
Click User Identity Stores.
-
In the screen that appears, click Create under OAM ID Stores.
-
In the dialog that appears, fill in the following required values, leaving the rest at their defaults:
Field Value Store Name
ESSOAuthnStoreStore Type
Microsoft Active Directory
Location
ad-server-hostname:port
Bind DN
domain\username
Password
password
Login ID Attribute
cnUser Search Base
Fully qualified DN of the Users container
Object Search Base
Fully qualified DN of the Groups container
-
-
Test the connection and correct any errors if necessary, then click Apply.
-
Update the LDAP authentication module:
-
Log on to the Oracle Access Manager console.
-
In the Plugins section, click Authentication Plug-ins.
-
In the Access Manager section, click Authentication Modules.
-
In the screen that appears, click Search.
-
In the list of search results, select the LDAPPlugin module.
-
In the Steps tab, select the stepUI step.
-
In the KEY_IDENTITY_STORE_REF field, enter the name of the user data store you created in step 5 of this procedure.
-
Repeat the above for the stepUA step.
-
Click Save to save your changes.
-
-
Create the identity data store (IDS) profile in Oracle Access Manager:
-
Log on to the Oracle Access Manager console.
-
Click Configuration at the top of the page.
-
Click User Identity Stores.
-
In the IDS Profile section, click Create Form Fill Application IDS Profile.
-
In the form that appears, fill in the fields as follows:
Field Value Name
meaningful profile name
Description
meaningful profile description
Repository Options
Create New
Repository Name
meaningful repository name
Directory Type
Microsoft Active Directory
Host name
Active Directory server host name
Port
Active Directory server port
Bind DN
domain/user name of repository account
Bind password
password of repository account
Base DN
fully qualified DN of the repository root
User search base
fully qualified DN of the Users container
App template search base
fully qualified DN of the CO (ESSO policy data) container
Top search base
fully qualified DN of the repository root
-
Test the connection, then click Apply.
-
-
Configure the relational mapping of users and groups:
-
Edit the IDS profile you just created.
-
Select the Entity Attributes tab.
-
Add the following new attributes, one at a time (adding multiple attributes at once is not supported):
member,memberOf,distinguishedName -
Select the Entities tab.
-
Under Users, enable the
member,memberOf, anddistinguishedNameentity attributes. -
Set the User Base, Group Base, Search Base, and Create Base entities to the fully qualified DNs of the respective containers in the repository.
-
Repeat steps e and f in the Groups section of the form.
-
Select the Relationships tab.
-
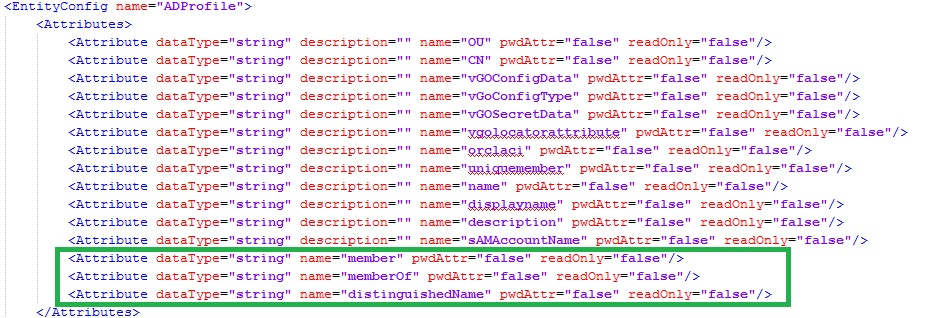
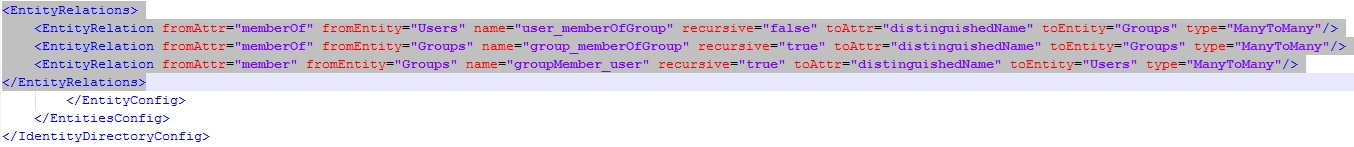
Configure the entity relationships as shown in the following illustration:
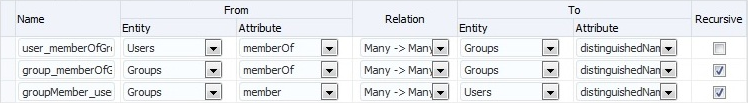 This makes the following changes in the file DOMAIN_HOME
This makes the following changes in the file DOMAIN_HOME/config/fmwconfig/ids-config.xml: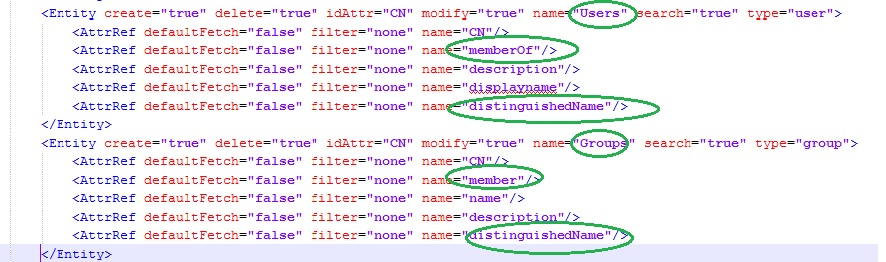
-
-
Enable the IDS profile:
-
Select the Launch Pad tab in the Admin console window.
-
At the top of the page, click Configuration.
-
In the Settings section, select Access Portal Service from the View drop-down list.
-
In the screen that appears, select the IDS profile you created earlier from the IDS Profile drop-down list.
-
Click Apply.
-
-
Add the Active Directory schema XML definition file to the IDS server configuration file:
-
Open the following file in a text editor:
DOMAIN_HOME/config/fmwconfig/ovd/ids/server.os_xml -
Locate the
<schema check="true">section and add the following line inside it:<location>schema.ms.xml</location> -
Save and close the file.
-
Restart the managed server instance to apply your changes.
-
54.3.7 (Active Directory Only) Deploying the OAMAgent Web Application
The OAMAgent web application provides the means to configure Access Control Lists within an Active Directory-based Access Portal Service repository via a web interface running on Microsoft Internet Information Server.
To deploy th OAMAgent web application, do the following:
-
Extract the
OAMAgent.zipfile (available in the Logon Manager folder of the Enterprise Single Sign-On Suite ZIP archive) into a directory. -
Using the IIS Manager application, create a new IIS web site; when prompted, in the Physical Path field, enter the full path to the directory into which you extracted the
OAMAgent.ziparchive. -
Edit the newly created web application's
Web.configfile as follows:-
Add the following to the
system.webServersection:<configuration><system.webServer><httpHandlers><add type="ColumbiaWindowsAgent.Rest.AgentAcl, OAMAgent" path="ColumbiaWindowsAgent/V1/AgentAcl" verb="POST"/></httpHandlers> </system.webServer></configuration>
-
Add the following to the
system.websection:<compilation targetFramework="4.0"><assemblies><add assembly="Interop.ActiveDs, Version=1.0.0.0, Culture=neutral"/></assemblies></compilation>
-
Save and close the file.
-
-
In the IIS Manager application, navigate to IIS Manager > Target Site > .NET Compilation > Assemblies and ensure that the new assembly appears in the list of assemblies (i.e., that the
Interop.ActiveDs.dllfile appears in the web root directory). -
Create a new handler mapping:
-
In the IIS Manager application, navigate to IIS Manager > Target Site > Handler Mappings and click Add Managed Handler in the right-hand pane.
-
In the dialog that appears, fill in the fields as follows and save your changes:
Field Value Path
ColumbiaWindowsAgent/V1/AgentAclType
ColumbiaWindowsAgent.Rest.AgentAcl, OAMAgentName
OAMAgent
-
-
Enable 32-bit application support:
-
In the IIS Manager application, navigate to IIS Manager > Application Pools.
-
Right-click the target site and select Advanced Settings from the context menu.
-
Set the Enable 32-bit Applications option to True and save your changes.
-
-
Make the following site configuration changes:
-
In the IIS Manager application, navigate to IIS Manager > Application Pools.
-
Select the target site.
-
Set the .NET Version to 4.0.
-
Set the Identity option to LocalSystem.
-
Save your changes.
-
-
In the IIS Manager application, select the host machine, click Server Certificates, and click Import a Certificate, and provide the path to a root CA certificate trusted by both the IIS server running the
OAMAgentweb application as well as the server running the target Access Portal Service instance.Additionally, the Access Portal Service server must have a certificate signed by that CA in its keystore. That CA must also be present in the server's
cacertfile (trust store). -
Create a https binding using the newly installed certificate:
-
In the IIS Manager application, right-click the target site and select Edit Bindings from the context menu.
-
Click Add New Site Binding.
-
Select https from the Type drop-down list.
-
Select the certificate you imported in step 8.
-
Click Close.
-
-
Enable SSL for the target site:
-
In the IIS Manager application, select the target site.
-
Click SSL Settings.
-
Select the Require SSL check box.
-
Select the Require client certificates check box.
-
Click Apply in the right-hand pane.
-
-
Add the following to the
oam-config.xmlfile on the Access Portal Service server instance, then restart the instance to apply your changes:<Setting Name="RestServicePath" Type="xsd:string">ColumbiaWindowsAgent/V1/AgentAcl</Setting><Setting Name="IPAddress" Type="xsd:string">iis-server-hostname</Setting><Setting Name="Protocol" Type="xsd:string">https</Setting><Setting Name="Port" Type="xsd:string">iis-server-port</Setting><Setting Name="Version" Type="xsd:string">1</Setting><Setting Name="ADPath" Type="xsd:string">AD-server-hostname:port</Setting>
-
Add the following keystore parameters to the managed server's startup script
JAVA_OPTIONSline:-Djavax.net.ssl.keyStore=keystore-location-Djavax.net.ssl.keyStorePassword=keystore-password
54.3.8 Setting the Policy Cache Refresh Interval
-1 (never refresh).A value of 0 disables the policy cache and causes every request to retrieve the corresponding policy from the repository.
To set a custom policy cache refresh interval:
54.3.9 About Integrating with Oracle Privileged Account Manager
When you integrate with Oracle Privileged Account Manager, you need to be aware of the Privileged Account Manager templates and the Privileged Account Manager server URL.
Following are the issues:
-
Only Oracle Privileged Account Manager templates of type "Privileged" are supported. Templates of type "Delegated" are not supported when created on the server side; creating such a template will result in unpredictable behavior.
-
You must specify the Oracle Privileged Account Manager server URL in the Access Portal Service settings in the target Oracle Access Manager server instance.
54.3.9.1 Installing Oracle Privileged Account Manager Certificates
You must import the certificates into the identity keystore of the application server running the Oracle Access Manager instance.
This procedure is currently only available for WebLogic; do not perform it on other application servers.
Note:
The listCred command in OPSS has been deprecated in this release; keystore passwords must now be retrieved programmatically.
To install Oracle Privileged Account Manager:
54.3.9.2 Configuring the Oracle Privileged Account Manager Server
You can configure the Oracle Privileged Account Manager server.
Before completing the steps below, make sure you have created a provider on the target Oracle Access Manager instance for the desired Oracle Privileged ccount Manager instance and placed it as the first provider in the provider list.
To configure the Oracle Privileged Account Manager server:
54.3.9.3 Creating the Required Template Mapping on the Provisioning Gateway Server
You can create the required template mapping on the Provisioning Gateway server machine using Provisioning Gateway Administrative Console.
To create:
-
Run the following command on the Provisioning Gateway server machine:
certutil -setreg chain\minRSAPubKeyBitLength 512 -
Restart the Provisioning Gateway server machine.
-
Log on to the Provisioning Gateway Administrative Console.
-
Select the Settings tab, then the Template Mapping section.
-
Click Edit and select the privileged template associated with your Oracle Privileged Account Manager target, then save your changes. This will create the required
cn=OpamTemplateMapmapping in the repository. -
Test the configuration:
-
Log on to Web Logon Manager as one of the grantees assigned to the target privileged account.
-
Click Add next to the target privileged template. The privileged account details will appear in a separate tab.
-
54.3.10 Deploying the Oracle Traffic Director Administration Server
The Oracle Traffic Director Administration Server deploys and manages Oracle Traffic Director proxy instance(s).
Linux security restricts the opening of ports under 1024 to the root user. If you wish to run Oracle Traffic Director proxies on ports 80 or 443, follow the configuration gudielines for running as the root user.
See "Creating an Administration Server and Administration Node" in the Oracle Traffic Director Installation Guide.
WARNING:
Oracle highly recommends against running Oracle Traffic Director as the root user due to increased security risk; you should limit the use of the root user to development environments only.
To deploy the Oracle Traffic Director Administration Server:
See the Oracle Traffic Director Installation Guide.
54.3.11 Deploying Webgate Binaries and Secure Trust Artifacts
You must have already created a Webgate profile in the Oracle Access Manager server before you start to deploy Webgate binaries and secure trust artifacts.
The secure trust artifacts that is generated during the procedure are required to complete the deployment of Webgate binaries and secure trust artifacts.
See Preparing and Enabling the Access Portal Service on an Oracle Repository.
To deploy Webgate binaries and secure trust artifacts:
-
Decompress the Webgate binaries installer into a local directory on the Oracle Traffic Director host and launch the installer with the following command:
./runInstaller -
When prompted, specify the full path to your Java runtime environment. For example:
/usr/local/packages/jdk16 -
In the installer's "Prerequisite Checks" screen, click Next.
-
Specify the installation path and click Next:
/MW_HOME/OAM_OTD_WebGate_HOME -
Click Install and wait for the installation to complete.
-
Change into the following directory:
/MW_HOME/OAM_OTD_WebGate_HOME/webgate/iplanet/tools/deployWebGate -
Deploy the Webgate binaries using the following command:
./deployWebGateInstance.sh -w /MW_HOME/wginst1 -oh /MW_HOME/OAM_OTD_WebGate_HOME -ws otd -
Copy the Oracle Access Manager artifact files (generated while completing the following steps:
See Preparing and Enabling the Access Portal Service on an Oracle Repository:
-
Copy the
ObAccessClient.xml,cwallet.sso, andpassword.xmlartifact files to:/MW_HOME/wginst1/webgate/config -
Copy the
aaa_key.pemandaaa_cert.pemartifact files to:/MW_HOME/wginst1/webgate/config/simple
-
-
(Optional) If you deployed your Oracle Traffic Director administration server instance as the root user, grant that instance permissions to the Webgate (otherwise, skip this step).
WARNING:
Oracle highly recommends against running Oracle Traffic Director instances as the
rootuser due to increased security risk; you should limit the use of therootuser to development environments only.-
Change into
/MW_HOME/wginst1 -
Execute
chmod -R 777 .
-
54.3.12 (Optional) Configuring the ESSOProvisioning Plugin
When you successfully log on to Oracle Access Manager, the ESSOProvisioning plugin will provision your directory credentials to a specific application in your Access Portal Service (ESSO) wallet.
It will also update the target application credentials if your directory credentials change. If you want to enable the plugin, you must assign the ESSOProvAuthnScheme to the ESSOAuthnPolicy authentication policy in the IAM Suite application domain profile.
To optionally configure the ESSOProvisioning plugin:
- Log into the Oracle Access Manager Console.
- At the top of the page, click Application Security.
- In the Plug-ins section, click Authentication Modules.
- In the screen that appears, click Search.
- In the list of search results, click the ESSOProvisioningModule module.
- In the screen that appears, select the Steps tab.
- Edit the
ESSO_PROV_Stepstep and enter the name of the target application for which you want to provision directory credentials. - Edit the
ESSO_UI_StepandESSO_UA_Stepsteps and add a User Identity Store value ofKEY_IDENTITY_STORE_REFto each. - Click Save to save the steps, then click Apply to apply your changes to the module.
- Select the Launch Pad tab; in the Access Manager section, click Application Domains.
- In the screen that appears, click Search.
- From the list of search results, locate and double-click the IAM Suite profile.
- Select the Authentication Policies tab.
- In the list of policies, select ESSOAuthnPolicy.
- From the Authentication Scheme drop-down menu, select the ESSOProvAuthnScheme authentication scheme.
- Click Apply to save your changes.
54.3.13 Creating an Oracle Traffic Director Configuration
You can create an Oracle Traffic Director Configuration
To create an Oracle Traffic Director configuration:
54.3.14 Protecting the Oracle Traffic Director Instance with the Webgate Plugin
To protect your Oracle Traffic Director instance with the Webgate plugin:
54.3.14.1 Generating Secure Trust Artifacts
You can generate secure trust artifacts.
To generate:
Note:
Only include the -enableWLM flag if you have deployed the Access Portal reference application. Otherwise, the flag is not necessary.
If you do not include the -enableWLM flag and wish to deploy the Access Portal reference application later, you must manually modify the appropriate Oracle Traffic Director configuration file as described in the Access Portal reference application deployment instructions.
54.3.14.2 Loading Required WebGate Libraries into an OTD Instance
You can load the required WebGate libraries into an OTD instance
To load:
54.3.14.3 Deploying Configuration Changes
You can deploy configuration changes from the Oracle Traffic Director Admin Console.
To deploy:
- Log into the Oracle Traffic Director Admin Console.
- Select your configuration and click the Instance Modified notification at the top of the page.
- Pull and deploy the changes.
- When prompted to restart the instance, click OK, then click Finish.
54.3.15 (Optional) Enabling the Detached Credential Collector for the Target Webgate
You can enable the Detached Credential Collector for the target Webgate and deploy the Detached Credential Collector pages on Oracle HTTP Server.
The following topics describe how to enable and deploy the Detached Credential Collector:
54.3.15.1 Enabling Detached Credential Collector Operations
You can enable detached credential collector operations from the Application Security launch pad.
To enable:
- Login to the Oracle Access Management Console.
- Select Application Security and in the Launch Pad, click Agents icon.
- In the screen that appears, click Search.
- From the list of search results, locate and click the agent that is protecting your OTD Proxy Instance.
- Check the box Allow Credential Collector Operations.
- Click Apply to save your changes.
- Restart the OTD Proxy Instance.
54.3.15.2 Creating and Applying a Detached Credential Collector Authentication Scheme
You can create and apply a detached credential collector authentication scheme from the Application Security launch pad.
To create:
- Login to the Oracle Access Management Console.
- Select Application Security and in the Launch Pad, click Authentication Schemes under Access Manager.
- In the screen that appears, click Search.
- From the list of search results, locate and click the ESSOProvAuthnScheme authentication scheme.
- In the screen that appears, click Duplicate.
- Give the new scheme a descriptive name - for example
DCC-ESSOAuthnScheme. - In the Challenge Method drop-down list, select FORM.
- In the Challenge Redirect URL field, enter the Oracle Traffic Director host name and port in the format
http://otd.hostname:port/(including the trailing slash). - In the Challenge URL field, enter
/oamsso-bin/login.pl - In the Context Type drop-down list, select external.
- Click Apply to save your changes.
- Select the Launch Pad tab.
- In the Access Manager section, click Application Domains.
- In the screen that appears, click Search.
- From the list of search results, locate and click the IAM Suite profile.
- Select the Authentication Policies tab.
- Click ESSOAuthnPolicy.
- In the Authentication Scheme drop-down list of ESSOAuthnPolicy, select the DCC authentication scheme you just created.
- Click Apply to save your changes.
54.3.15.3 Deploying Detached Credential Collector Pages on an Oracle HTTP Server
You can deploy Detached Credential Collector pages on an Oracle HTTP server.
To deploy:
54.3.16 Configuring Logon Manager for Compatibility with the Access Portal Service
You can enable interoperability between Logon Manager and the Access Portal Service.
If you have not already done so, install the Authentication Manager component of the Logon Manager on each target end-user machine to enable the MultiAuth authenticator in Logon Manager.
For more information on configuring Logon Manager repository settings, see the guide Deploying Logon Manager with a Directory-Based Repository.
Note:
For an Application Policy to be compatible, enable the "User Visible" setting in the Application profile in the Oracle Access Management Console. You must perform this task in addition to the modifications that are described in the following topics:
54.3.16.1 Modifying the Access Portal Service Configuration
You can modify the Access Portal service configuration.
To modify:
-
In the IDS profile you have configured for the Access Portal Service, ensure that you are connecting with a user who possesses root privileges (e.g.,
orcladmin). -
If you are using Oracle Internet Directory as your repository, set the following permissions to permit Logon Manager to its First Time Use wizard:
-
For the
vGoLocatorobject and itsdefaultchild object:orclaci = access to attr=(*) by * BindMode="Simple" (read,search,compare)orclaci = access to entry by * BindMode="Simple" (browse) -
For the
Peoplecontainer:orclaci = access to attr=(*) by * BindMode="Simple" (read,write,search,compare)orclaci: access to entry by * BindMode="Simple" (browse,add,delete)
-
-
Ensure that the PolicyCache TTL is set to a positive, non-zero value.
54.3.16.2 Modifying the Logon Manager Configuration
You can modify the Logon Manager configuration by connecting to your repository.
To modify:
-
Launch the Enterprise Single Sign-On Suite Administrative Console and connect to the Access Portal Service repository.
-
If you are using Active Directory as your repository, do the following (otherwise, skip this step):
-
Navigate to Global Agent Settings > Live > Synchronization > ADEXT.
-
Select the check box next to the Use secure location for storing user settings option and select Yes from the drop-down menu.
-
-
Navigate to Global Agent Settings > Live > Authentication > Authentication Manager and configure the graded authenticators as required by your environment. For more information, refer to the Enterprise Single Sign-On Suite Administrator's Guide.
-
Navigate to Global Agent Settings > Live > Authentication and configure each authenticator as required by your environment, noting the following:
-
If using Oracle Internet Directory as your repository, there are two Recovery Method options Passphrase suppression using entryUUID and Passphrase suppression using secure key. Select Passphrase suppression using secure key if displayed; otherwise select Passphrase suppression using entryUUID.
-
If using Active Directory as your repository, set the Recovery Method option to Passphrase suppression using user's SID.
For more information, see the guide Deploying Logon Manager with a Directory-Based Repository.
-
-
Navigate to Global Agent Settings > Live > Synchronization and configure the appropriate synchronizer as required by your environment, noting the following:
-
Enable the Use aggressive synchronization option.
-
Enable the Resynchronize when network or connection status changes option.
-
Set the Interval for automatic resynchronization option to
1.
-
-
Publish your settings to the repository:
-
In the tree on the left-hand side right-click Live and select Publish from the context menu.
-
Click Browse and select the target path within the repository. (If prompted, enter the appropriate connection parameters and click OK to connect.)
-
In the Available configuration objects list, double-click Live to move it to the list of objects selected for publishing.
-
Click Publish and wait for the operation to complete.
-