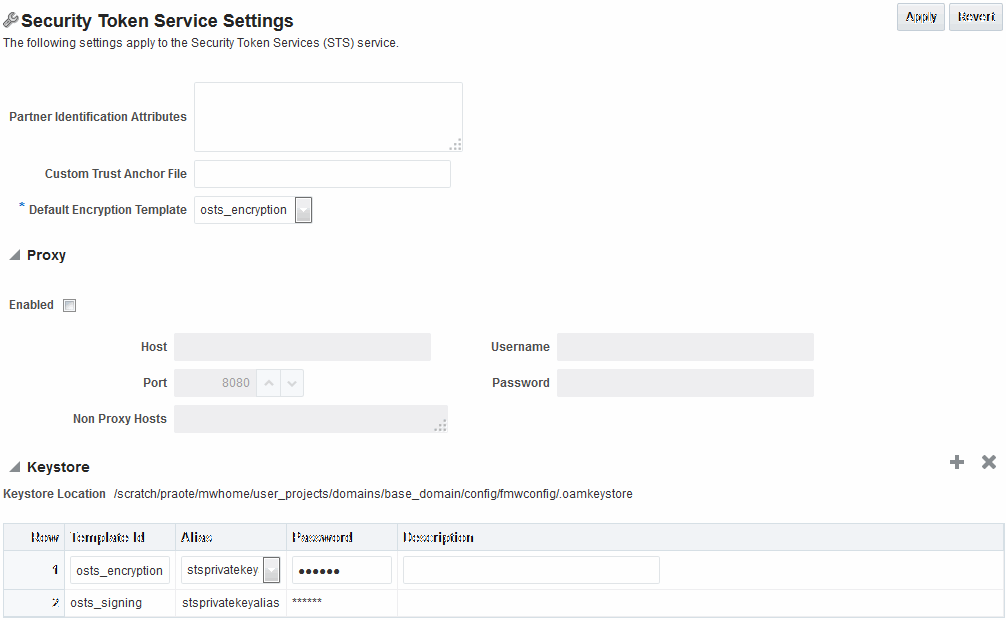
43.4 Defining Security Token Service Settings
The following topics introduce:
43.4.1 About Security Token Service Settings
Security Token Service can be viewed or altered from the Security Token Service section of the System Configuration tab.
These settings are show in Figure 43-3.
Table 43-1 describes the elements on the Security Token Service Settings page.
Table 43-1 Security Token Service Settings
| Element | Description |
|---|---|
|
Partner Identification Attributes |
A field where you list attributes, other than the standard ones available by default, that should be available in "Identity Attributes" Table in the Partner page. These attributes can be used to identify a partner by matching their values against those in the incoming request. When a Requester sends a WS-Trust request to Security Token Service, the server might map the incoming token containing the requester's identity to a partner entry in the Security Token Service partner store. To do so, Security Token Service will use the mapping settings configured in a validation template and will attempt to map the token data to a partner entry by performing a lookup by matching the token data to a Partner Identification Attribute. By default, each requester partner contains three identification attributes that can be set: username, HTTP Basic Username, SSL Client Certificate DN. It is possible to define additional Identification Attributes that could be set for each requester partner entry. This section allows new attributes to be set. After defining a new attribute, it becomes available in the Requester Partner entry section, and it can be used in mapping rules in the WSS Validation Templates. |
|
Custom Trust Anchor File |
By default, Access Manager and Security Token Service use the default It is possible to configure Security Token Service to use a specific trust anchor file if necessary, that will contain trust anchors only used for Security Token Service operations and validations. In this case, this field should contain the location of the JKS keystore to use. Note the following:
See Also: Managing Security Token Service Certificates and Keys |
|
Default Encryption Template |
A list from which you choose the default template for Security Token Service encryption:
See Also: Setting the Default Encryption Key. |
|
Proxy |
Outbound Connection Properties, HTTP Proxy Settings Use this section to configure Security Token Service to use a proxy for outgoing HTTP connections when optionally retrieving the WS-Sec Policy of Relying Parties at runtime:
|
|
Keystore |
Location: Path of the active keystore that was set up during Security Token Service installation. The Keystore table includes the following information for each of the templates in the table, which are available for use as the Default Encryption Template:
The keystore section defines key entries that exist in the Security Token Service keystore: After an entry is defined an entry, it can be used in other Security Token Service templates (like SAML Issuance Templates). |
43.4.2 Managing Security Token Service Settings
Users with valid Administrator credentials can use the following procedure to confirm or modify Security Token Service settings:
43.4.2.1 Prerequisites for Managing Security Token Service Settings
Both the Access Manager Service and the Security Token Service must be enabled.