23.2 Overview of the SSO Login Process with OAM Agents and ECC
Access Manager authenticates each user with a customer-specified authentication method to determine the identity and leverages information stored in the user identity store.
This topic is based on using the default Embedded Credential Collector with OAM Agents (Resource WebGates) protecting resources.
Access Manager authentication supports several authentication methods and a number of authentication levels. Resources with varying degrees of sensitivity can be protected by requiring higher levels of authentication that correspond to more stringent authentication methods.
When a user tries to access a protected application, the request is received by Access Manager which checks for the existence of the SSO cookie.
After authenticating the user and setting up the user context and token, Access Manager sets the SSO cookie and encrypts the cookie with the SSO Server key (which can be decrypted only by the SSO Engine).
Depending on the actions (responses in Access Manager 11g) specified for authentication success and authentication failure, the user may be redirected to a specific URL, or user information might be passed on to other applications through a header variable or a cookie value.
Based on the authorization policy and results of the check, the user is allowed or denied access to the requested content. If the user is denied access, she is redirected to another URL (specified by the Administrator in WebGate registration).
Figure 23-1 shows the processes involved in evaluating policies, validating a user's identity, authorizing the user for a protected resource, and serving the protected resource. This example shows the OAM Agent flow. There are slight variations with 11g WebGates/Access Clients.
Figure 23-1 SSO Log-in with Embedded Credential Collector and OAM Agents
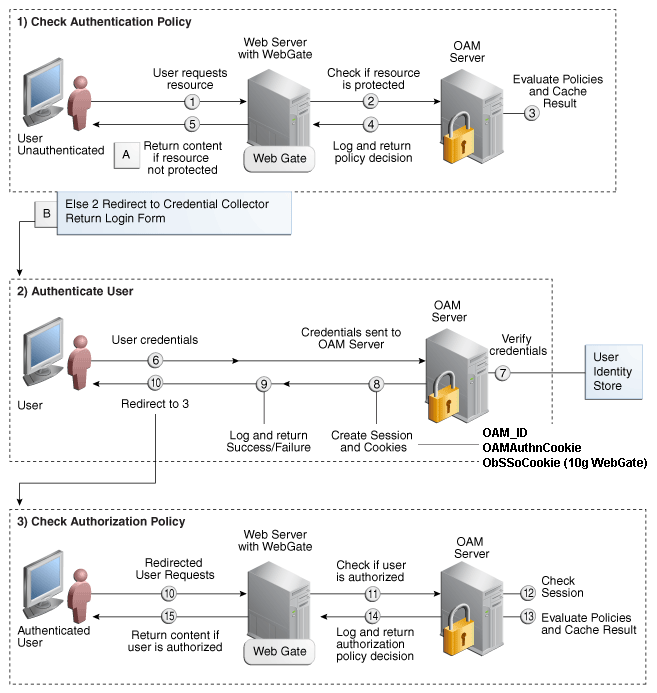
Description of "Figure 23-1 SSO Log-in with Embedded Credential Collector and OAM Agents"
Process overview: SSO Login Processing with Embedded Credential Collector and OAM Agents
-
The user requests a resource.
-
WebGate forwards the request to Access Manager for policy evaluation.
-
Access Manager:
-
Checks for the existence of an SSO cookie.
-
Checks policies to determine if the resource protected and if so, how?
-
-
Access Manager Server logs and returns decisions.
-
WebGate responds as follows:
-
Unprotected Resource: Resource is served to the user.
-
Protected Resource:
Request is redirected to the credential collector.
The login form is served based on the authentication policy.
Authentication processing begins
-
-
User sends credentials.
-
Access Manager verifies credentials.
-
Access Manager starts the session and creates the following host-based cookies:
-
One per Agent: OAMAuthnCookie set by 11g WebGates (ObSSOCookie set by 10g Webgate) using the authentication token received from the OAM Server after successful authentication.
Note: A valid cookie is required for a session.
-
One for OAM Server: OAM_ID
-
-
Access Manager logs Success or Failure.
-
Credential collector redirects to WebGate and authorization processing begins.
-
Webgate prompts Access Manager to look up policies, compare the user's identity, and determine the user's level of authorization.
-
Access Manager logs policy decision and checks the session cookie.
-
OAM Server evaluates authorization policies and cache the result.
-
OAM Server logs and returns decisions
-
WebGate responds as follows:
-
If the authorization policy allows access, the desired content or applications are served to the user.
-
If the authorization policy denies access, the user is redirected to another URL determined by the Administrator.
-